#data privacy software
Explore tagged Tumblr posts
Text
What to Include in a GDPR-Compliant Tech Stack
Let’s face it—GDPR compliance can feel like alphabet soup mixed with legalese. But in reality, it’s all about trust, transparency, and protecting your users’ data. If your tech stack handles any kind of personal data from EU residents, then GDPR isn’t optional—it’s essential. Whether you’re building a website, launching a SaaS product, or managing digital marketing tools, here’s exactly what you…
#data privacy software#GDPR compliance tools#GDPR SaaS compliance#GDPR tech stack#GDPR website checklist
0 notes
Text
still confused how to make any of these LLMs useful to me.
while my daughter was napping, i downloaded lm studio and got a dozen of the most popular open source LLMs running on my PC, and they work great with very low latency, but i can't come up with anything to do with them but make boring toy scripts to do stupid shit.
as a test, i fed deepseek r1, llama 3.2, and mistral-small a big spreadsheet of data we've been collecting about my newborn daughter (all of this locally, not transmitting anything off my computer, because i don't want anybody with that data except, y'know, doctors) to see how it compared with several real doctors' advice and prognoses. all of the LLMs suggestions were between generically correct and hilariously wrong. alarmingly wrong in some cases, but usually ending with the suggestion to "consult a medical professional" -- yeah, duh. pretty much no better than old school unreliable WebMD.
then i tried doing some prompt engineering to punch up some of my writing, and everything ended up sounding like it was written by an LLM. i don't get why anybody wants this. i can tell that LLM feel, and i think a lot of people can now, given the horrible sales emails i get every day that sound like they were "punched up" by an LLM. it's got a stink to it. maybe we'll all get used to it; i bet most non-tech people have no clue.
i may write a small script to try to tag some of my blogs' posts for me, because i'm really bad at doing so, but i have very little faith in the open source vision LLMs' ability to classify images. it'll probably not work how i hope. that still feels like something you gotta pay for to get good results.
all of this keeps making me think of ffmpeg. a super cool, tiny, useful program that is very extensible and great at performing a certain task: transcoding media. it used to be horribly annoying to transcode media, and then ffmpeg came along and made it all stupidly simple overnight, but nobody noticed. there was no industry bubble around it.
LLMs feel like they're competing for a space that ubiquitous and useful that we'll take for granted today like ffmpeg. they just haven't fully grasped and appreciated that smallness yet. there isn't money to be made here.
#machine learning#parenting#ai critique#data privacy#medical advice#writing enhancement#blogging tools#ffmpeg#open source software#llm limitations#ai generated tags
61 notes
·
View notes
Text
How to install NewPipe on Android
NewPipe is a YouTube replacement client for Android devices. It's open-source (meaning, you can see all of their code as you please), privacy-oriented, lightweight, and supports features that are normally locked behind a YouTube Premium paywall.
Disclaimer: I am not affiliated with NewPipe, YouTube, Android, Google, Alphabet Inc, or any other brand or name mentioned here. I made this guide to help my friends who were curious.
NewPipe's Website: https://newpipe.net/
The GitHub Repository
Step 0. Compatibility check
Make sure you're running an Android device! This won't work on an Apple device of any kind! Also, for those more tech-savvy among you, if you have the F-Droid store installed, you can download NewPipe straight from there!
Step 1. Downloading
Go to NewPipe's Github repo (repository, the codebase or where all of the code is stored). Scroll to the bottom of the page until you see "Releases". Click on the one that says "Latest" next to it in a little green bubble:

Your version number (v#...) will be different if you're reading this in the future! That's okay. Scroll past the changelog (unless you want to read it!) until you find "Assets":

Click on the first one, the one with the little cube ending in .apk. APK files are Android Package (Kit) and are the main format for downloading apps. Once you click on the link, it should begin downloading or your browser will ask you to confirm that you want to download this file. You should always verify the filename matches what you expect it to be (namely, the file format) before attempting to install! It might take a few moments for the file to download depending on your internet connection.
Step 2. Installation
Once you have the file downloaded, you can click the download popup in your notification bar or find the file in your device's file system. One of 2 things will happen:
You will get a popup asking if you want to install an APK by the name of NewPipe - confirm that you do (and make sure the app is really NewPipe!) and it will install automatically. You can then click "Open" to open the app and begin using it.
You will get a popup warning you that you have the ability to install apps from unknown sources disabled and that you can't install this. This is normal and does not mean that you downloaded the wrong thing.
If you got the first popup, continue past this step. For those of you who got the second, let's go over what this means.
By default, most Androids have this setting disabled. This is for security purposes, so you can't accidentally install a malicious app from the whole internet. If you enable this setting (allow installations from unknown/unsigned sources), you are theoretically putting yourself at risk. Realistically, you're probably fine. But, after installing NewPipe, you can always re-disable the setting if it makes you more comfortable. That will prevent you from installing updates in the future, but it can always be re-enabled.
Ready to turn that setting on? It will vary by your individual device! Some devices will take you directly to the page with the setting upon failed installation, and some you will just have to find it yourself using the searchbar in settings.
Once you've allowed installations from unknown sources (wording may vary slightly), try to repeat the steps above of clicking the download popup or finding the APK in your files and trying to install it. It should work correctly this time!
Step 3. Updating NewPipe
Like most apps, NewPipe is in development currently and frequently has new versions released to improve it and fix bugs. Unlike most apps, NewPipe needs to be manually updated, since we haven't downloaded through the Google Play store.
To update NewPipe, all you have to do is follow the above steps for installing the app, except that when you get the popup asking to install it, it will instead say "Update". That's it! NewPipe and Android handle the rest.
NewPipe also has popup notifications for when the app has a new update, so you don't have to worry about checking the GitHub for a new release. Just click on the "A new version is available" popup and it should take you directly to the webpage.
That's it! Enjoy browsing videos in peace without ads and with the ability to download and so much more. Pro tip: you can copy paste YouTube links into the NewPipe search bar to go directly to that video/playlist/channel.
#newpipe#youtube#youtube client#youtube replacement#how to install newpipe#android#android apk#android app#images#text#links#image descriptions#privacy#data privacy#internet privacy#big tech#data security#github#software#database#opensource#open source#newpipe app
30 notes
·
View notes
Text
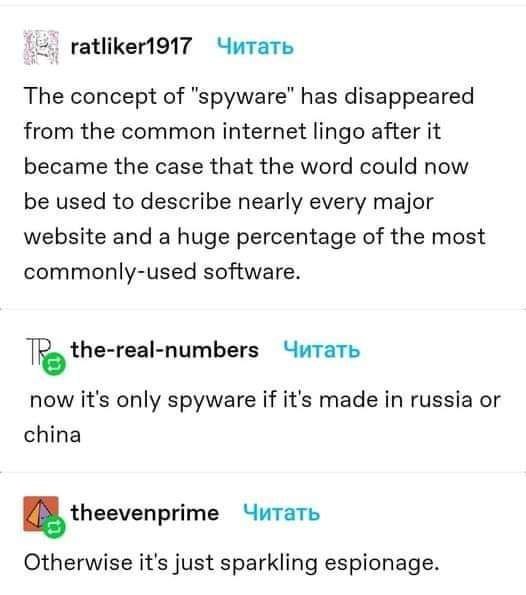
#spyware#internet#infotech#it#i.t.#information technology#software#firmware#espionage#online privacy#internet privacy#data privacy#invasion of privacy#privacy#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#class war#earth#oppression#repression#proxy war#eat the rich
25 notes
·
View notes
Text
hey maybe don’t talk to the qsmp datamine bot! i know it’s literally a thing that the federation is weird and invasive and definitely stealing the islanders data but bringing that out of the roleplay story world is…weird to say the least. especially in this era where internet privacy is basically nonexistent. it just sets a weird precedent
#to be clear i’m not saying the qsmp staff is actively trying to steal ur data#but like idk what exactly the cucurucho ai is using#and that’s the point#there’s a lack of transparency about what software it’s using#and where that data is going#most likely it’s something like chat gpt or a character ai bot or whatever#but those suck for other reasons and i just don’t know if it actually is one of those#weird thing to make ur audience comfortable with#qsmp#qsmp cucurucho#privacy#posts from the ocean
21 notes
·
View notes
Text
First hate comment on my unexpectedly viral Tumblr meta post and it's even more unhinged and conspiracy brained than the original posts I was talking about #yass
#mfw a random software engineer makes a comment about wanting to remove pfps because they're pissed their clientele has been harassing them#so they are automatically responsible for data and privacy breaches across a massive platform known for shit advertising decisions
30 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
85% Discount + 2 month Free. Unveiling the Power of Surfshark VPN: Your Ultimate Online Privacy Solution. Surfshark Vpn Full Review In Article Below.
If you are looking for a VPN program for the computer or for Android, iPhone, and Mac... I promise you that this VPN is what you are looking for. Read the description of the VPN on the Medium platform and make your decision. I am here just to help you and get some followers on the Tumblr platform.
#best vpn#vpn#data privacy#online privacy#cyber security#free vpn#vpnservice#clone vpn#software#hidden#streaming#livestream#vps server#vpn reviews#vpn software#vpn service
2 notes
·
View notes
Text
Welcome to InnovateHub TechTalk: Unleashing the Tech Frontier
Greetings, fellow tech enthusiasts, and welcome to the inaugural edition of InnovateHub TechTalk! I am Lucas Redford, your guide on this thrilling expedition into the boundless realms of technology. With each keystroke and pixel, we'll embark on a journey to unravel the mysteries, embrace the innovations, and discuss the trends that shape our digital world.
Charting New Horizons:
In the age of rapid technological advancement, it's impossible to ignore the transformative impact that technology has on our lives. From the moment we wake up to the time we rest our heads, technology surrounds us, empowering, entertaining, and evolving at an unprecedented pace.
Our Quest:
At InnovateHub TechTalk, our mission is simple yet profound: to ignite your curiosity and keep you informed about the dynamic world of technology. Whether you're a seasoned coder, a budding entrepreneur, a digital artist, or just someone intrigued by the possibilities, this platform is your haven.
What Awaits You:
As we embark on this voyage together, here's a glimpse of what you can expect from InnovateHub TechTalk:
Innovative Spotlights: Venture into the heart of innovation as we showcase groundbreaking technologies and inventions that are reshaping industries and society.
Tech Chats with Experts: Join me in engaging conversations with thought leaders, industry experts, and visionaries who are shaping the course of technology.
CodeCraft Corner: Whether you're a coding novice or a seasoned pro, our CodeCraft Corner will be your source for coding tips, projects, and insights to elevate your programming prowess.
FutureTalk: Delve into the crystal ball as we discuss emerging trends, speculative tech, and the potential future landscapes that await us.
Be a Part of the Conversation:
InnovateHub TechTalk is not just a blog; it's a community. Your thoughts, questions, and insights are the catalysts that will drive our discussions forward. Don't hesitate to jump into the comment section, share your perspectives, and connect with fellow tech aficionados.
With great excitement, I invite you to journey with me through the digital maze, the electronic wonderland, and the data-driven universe that defines our age. Together, we'll decode complexities, celebrate achievements, and ponder the limitless possibilities that lie ahead.
As we dive into the sea of 1s and 0s, remember that innovation knows no bounds, and at InnovateHub TechTalk, we're poised to explore it all.
Welcome aboard, tech voyagers!
Lucas Redford
Founder and Chief Explorer, InnovateHub TechTalk
#Technology Trends#Innovation Insights#Tech Enthusiasts#Digital Exploration#Future of Tech#Coding Tips#Emerging Technologies#Tech Conversations#User Experience Design#Digital Transformation#Artificial Intelligence#Internet of Things#Cybersecurity#Software Development#Gadgets and Devices#Web Technology#Virtual Reality#Blockchain#Tech News Updates#Data Privacy#Cloud Computing#Tech Industry#Online Innovation#Science and Technology#Technology Community#Tech Insights#Cutting-Edge Tech#Digital Evolution#Innovation Spotlight#Technology Exploration
2 notes
·
View notes
Text
I was a hard core Scrivener fan, but lately I have been pretty much exclusively using Ellipsus.
I’m part of a feedback exchange and we have all our files on Ellipsus and it’s just fantastic. Soooo much better than google docs.
Just in time for Valentine’s Day... 💔
Ready to break up with Google?

So are we!
We’ve rounded up a bunch of privacy-centric alternatives for everything Google.

Check out the full list over on the blog!
- The Ellipsus Team xo
#writeblr#writers on tumblr#writing#collaborative writing#fuck google#anti ai#data privacy#ellipsus#writing software
49K notes
·
View notes
Text

I'm building software now. Feds are fucking annoying and I hope this makes them want to hang themselves. Since the internet is more trackable with social media apps yoinking your details and bullshit, I am making my own social platform. No tracking and encryption is completed on device and among those you trust.
1 note
·
View note
Text
Cobwebs Spy Software Locks Onto Protesters: Israeli Social Media Mining homeland security contractor
youtube

#cobwebs#spy#software#protest#privacy#data privacy#online privacy#internet privacy#invasion of privacy#social networks#social media#internet#class war#all cops are bastards#all cops are bad#all cops are pigs#israel#israhell#homeland security#spyware#infotech#information technology#i.t.#it#israel is a terrorist state#israel is committing genocide#israeli war crimes#israel is an apartheid state#israel is a war criminal#benjamin netanyahu
2 notes
·
View notes
Text

FYI: Not anywhere near a complete solution: but I run an app called Little Snitch on my Mac that warns me when a program unexpectedly tries to use the internet. (I can set which apps have permission, with granularity down to specific tcp/ip port numbers).
It's a bit technical to use, and requires some setup; but it does catch (and prevent) situations when some app unexpectedly tries to pull something. (Believe it runs on Windows as well as the Mac.)
I believe everything should be offline, I believe that every time something that is not your internet browser (and I'm being generous here) should have a big red alert that says THIS PIECE OF SHIT PROGRAM NEEDS TO CONNECT TO THE INTERNET AND REQUESTS YOUR CONSENT TO DO THIS SPECIFIC THING, and you had to touch a big red button and it would disconnect as soon as you close it.
#internet privacy#computer privacy#data privacy#corporate overreach#software overreach#privacy#intrusive software#computer security#enshittification
29K notes
·
View notes
Text
Who’s Spying on You the Most? Microsoft, Google, Nvidia, or Steam? Let’s Find Out!
Hey everyone! Let’s talk about something we all know but don’t always think about: tech companies spying on us. Yeah, it’s no secret that our devices and apps are constantly collecting data, but have you ever wondered who’s doing it the most? Is it Microsoft? Google? Nvidia? Steam? Or maybe even EA? I decided to run a little experiment to find out, and the results were… eye-opening. The…
#background connections#Copilot tracking#cybersecurity#data collection#data protection#data security#digital privacy#Discord connections#EA app#firewall settings#Google APIs#Linux telemetry#Microsoft Edge#Microsoft Rewards#Microsoft telemetry#modern software design#Nvidia data tracking#Nvidia GeForce Experience#online privacy#online security#online tracking#privacy tips#Steam privacy#tech companies spying#tech experiments#ThreatLocker#Windows activity tracking#Windows Defender#Windows privacy#zero-trust security
0 notes
Text
PrivaZer Download - Clean Junk Files & Protect Privacy
PrivaZer is a free tool with an optional premium version that acts as a privacy protector, registry cleaner, and junk file remover for your PC. It helps users safeguard sensitive data by eliminating unwanted traces left behind during regular computer use. PrivaZer goes beyond typical cleaning; it can securely erase data, making it nearly impossible to recover. This feature is especially…
#data protection#data security#deep cleaning#disk cleanup#file eraser#junk file cleaner#PC privacy#portable software#privacy protection#privacy tool#PrivaZer#registry cleaner#secure deletion#system optimization#Windows cleaning tool
0 notes
Text
Secure Accounting with Data Privacy

In today’s digital world, accounting software isn’t just about managing finances—it’s about protecting sensitive data. As businesses increasingly rely on cloud-based solutions for accounting, data security and privacy are critical. In this article, we’ll explore the importance of secure accounting and how TRIRID Accounting and Billing Software ensures your financial data remains safe, private, and compliant with the latest regulations.
Why Is Data Privacy Important in Accounting?
Accounting deals with sensitive information ranging from bank accounts to personal financial information. It is often handled, and any data breach or unauthorized access can have severe repercussions, including identity theft, loss of funds, or damaged reputations. That is why organizations need to invest in secure accounting software, which emphasizes maintaining the privacy of data.
Key Features of Secure Accounting Software
Encryption for Data Security
TRIRID Accounting and Billing Software uses state-of-the-art encryption methods to protect your sensitive financial data, both in transit and at rest. With AES-256 encryption, your data is safely stored in secure servers, preventing unauthorized access.
Two-Factor Authentication (2FA)
Login to your accounting software must only be accessed by authorized staff only. TRIRID has integrated Two Factor Authentication 2FA which adds another layer of security when logging into your account therefore, only verified users access your financial records.
Role-Based Access Control (RBAC)
With TRIRID, you can control which users have access to which sections of your accounting system. Whether you are tracking sales, billing, or financial reports, you can assign specific permissions based on the user's role in your organization, so that sensitive data is available only to those who need it.
Consistent Data Backup
The other threat is the loss of data. TRIRID automatically backs up your accounting data daily, ensuring that you never lose critical financial information in case of system failure or cyberattacks.
Compliant and GDPR Ready
Any business dealing with customer data must be compliant with data protection regulations such as the General Data Protection Regulation (GDPR). TRIRID guarantees your accounting processes will be fully compliant with current legal standards. Your business will be comforted by the knowledge that it complies with global data privacy laws.
Secure Cloud Hosting
TRIRID Accounting and Billing Software uses reliable cloud hosting solutions, ensuring data is stored in highly secure, redundant data centers. This minimizes the risk of physical theft or loss, and offers the flexibility to access your financial data from anywhere while keeping it protected.
Data privacy is no longer a choice but a necessity. TRIRID Accounting and Billing Software is laden with the latest security features designed to keep your financial information safe against all threats, conform to global standards, and help you grow your business without any safety concerns related to your sensitive financial information.
Secure your accounting today with TRIRID.
Call @ +91 8980010210 / +91 9023134246
Visit @ https://tririd.com/tririd-biz-gst-billing-accounting-software
#Best accounting software in Ahmedabad Gujarat#Secure Accounting and Billing Software#Accounting Software with Data Privacy#TRIRID-Billing software in Bopal in Ahmedabad#TRIRID-Billing software in ISCON-Ambli road-ahmedabad
0 notes