#document intelligence
Explore tagged Tumblr posts
Text
How Document Intelligence Transforms Business Processes
Accuracy and efficiency are critical in the fast-paced business environment of today. Companies in a variety of sectors are using document intelligence more and more to improve efficiency, spur innovation, and streamline operations. However, what is document intelligence precisely, and how can it improve corporate operations? This article explores how document intelligence can change corporate practices and how it can do so.
What is Document Intelligence?
Document intelligence is the automation of document processing, analysis, and management through the application of cutting edge technologies including artificial intelligence (AI), machine learning (ML), natural language processing (NLP), and optical character recognition (OCR). In contrast to conventional approaches, which mostly rely on human input and are error-prone, document intelligence makes effective use of algorithms and data-driven insights to manage challenging document-related activities.
Key Benefits of Document Intelligence
Enhanced Accuracy and Reduced Errors The capacity of document intelligence to increase accuracy is among its most important benefits. Human error is a possibility with traditional document processing technologies, which can result in expensive errors and inefficiencies. On the other hand, document intelligence systems employ complex algorithms to precisely extract and interpret data. This lowers the possibility of mistakes and guarantees correct information processing, producing more dependable results.
Increased Efficiency and Speed Processes relating to documents are accelerated by document intelligence by automating repetitive operations that would otherwise take a lot of time and resources. For instance, computer programs can accomplish activities like data input, document classification, and information extraction faster than humans could. Businesses may respond to consumer and market demands faster because of this enhanced speed, giving them a competitive advantage.
Improved Data Management and Accessibility It can be difficult to manage a lot of documents. Information may be stored, retrieved, and managed more easily with the help of document intelligence solutions, which routinely index and categorize documents. Improved search features make it easier for users to locate pertinent information and documents fast, increasing accessibility and facilitating improved decision-making.
Cost Savings Businesses can drastically cut labor expenses and eliminate the need for manual intervention by automating document processing operations. High document volumes can be handled by document intelligence systems with minimal human control, which eventually results in significant cost savings. Moreover, decreased error rates and expedited processing lead to overall cost effectiveness.
Enhanced Compliance and Risk Management For many areas, including the legal, banking, and healthcare industries, regulatory compliance is essential. By automating the monitoring and reporting of regulatory documents, document intelligence technologies can assist enterprises in maintaining compliance. Businesses can reduce risks and steer clear of expensive fines by making sure that documents are processed precisely and in compliance with regulatory standards.
Real-World Applications of Document Intelligence
Healthcare Document intelligence is utilized in the healthcare sector to enhance clinical documentation, maintain patient data, and expedite administrative procedures. Better patient care and operational efficiency result from the automated processing of medical forms, insurance claims, and patient records, which also lessens administrative workloads and improves patient data accuracy.
Finance Document intelligence is a tool used by financial organizations to automate processes like customer onboarding, compliance documentation management, and loan application processing. Financial institutions can decrease processing times, increase accuracy, and improve client happiness by automating these procedures.
Legal Document intelligence helps in the legal industry with case file management, document analysis, and contract information extraction. By automating these processes, legal practitioners may concentrate on higher-value responsibilities like strategy analysis and client consultations while also accelerating legal operations and lowering the possibility of errors.
Manufacturing Document intelligence helps manufacturing organizations by automating order processing, supplier documentation, and inventory management. This automation guarantees that manufacturing processes function properly, decreases the amount of manual data entry, and streamlines supply chain operations.
Challenges and Considerations
Even though document intelligence has many advantages, there may be certain drawbacks that should be taken into account. Initial training and technological investments are necessary for the implementation of document intelligence systems. To safeguard sensitive data, firms also need to handle privacy and data security issues. To overcome these obstacles and achieve a successful deployment, meticulous preparation and in-depth knowledge of the technology are essential.
Conclusion
Document intelligence is boosting data management, cutting expenses, raising efficiency, and improving accuracy — all of which are transforming business processes. Leveraging document intelligence will be essential for firms embracing digital transformation to remain competitive and adaptable in a market that is changing quickly. Organizations may revolutionize their document-related operations and achieve unprecedented levels of productivity and innovation by leveraging the power of sophisticated technology.
0 notes
Text

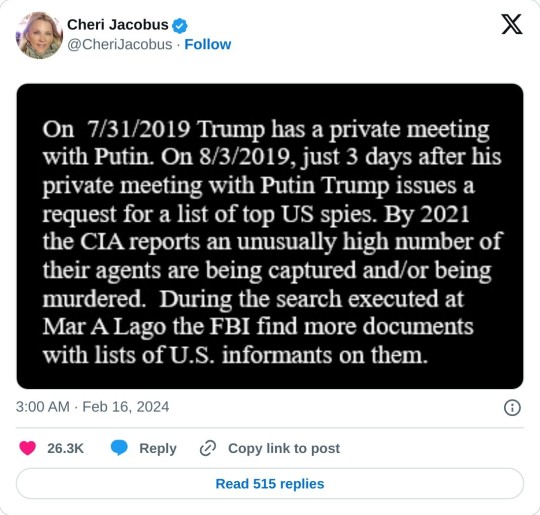
On 7/31/2019 Trump has a private meeting with Putin. On 8/3/2019, just 3 days after his private meeting with Putin, Trump issues a request for a list of top US spies. By 2021 the CIA reports an unusually high number of their agents are being captured and/or being murdered. During the search executed at Mar A Lago the FBI find more documents with lists of U.S. informants on them.
A Timeline
• FBI wiretapped Russian gambling ring headquartered at Trump Tower for two years - March 21, 2017
• Trump revealed highly classified information to Russian foreign minister and ambassador - May 15, 2017
• Trump, Putin Meet For 2 Hours In Helsinki - July 16, 2018
• Rand Paul Goes To Russia And Delivers Letter For Trump, Marking Our Era Of Irony - August 9, 2018
• Following the Money: Trump and Russia-Linked Transactions From the Campaign to the Presidential Inauguration - December 17, 2018
• The US extracted a top spy from Russia after Trump revealed classified information to the Russians in an Oval Office meeting - September 10, 2019
• Trump’s Loose Lips Force US to Extract Spy From Kremlin - September 10, 2019
• Was Mar-a-Lago Trespasser a Tourist or a Spy? A Judge Said Her Story Didn’t Hold Up. - November 25, 2019
• Trump downplays massive cyber hack on government after Pompeo links attack to Russia - December 19, 2020
• Russia has been cultivating Trump as an asset for 40 years, former KGB spy says - January 29, 2021
• There was Trump-Russia collusion — and Trump pardoned the colluder - April 17, 2021
• Longtime GOP operatives charged with funneling Russian national’s money to Trump, RNC - September 20, 2021
• Captured, Killed or Compromised: C.I.A. Admits to Losing Dozens of Informants - October 5, 2021
• Files Seized From Trump Are Part of Espionage Act Inquiry - August 12, 2022
• Ex-Clinton aide implies 'President of France' file found at Trump's home during Mar-a-Lago raid could be valuable to Putin as 'kompromat' - August 13, 2022
• Inventing Anna: The tale of a fake heiress, Mar-a-Lago, and an FBI investigation - August 22, 2022
• Russians used a US firm to funnel funds to GOP in 2018. Dems say the FEC let them get away with it - October 30, 2022
• Trump makes shocking comments about trusting Putin over US 'intelligence lowlifes' - January 31, 2023
• Russia's Prigozhin admits links to what US says was election meddling troll farm - February 14, 2023
• GOP operative sentenced to 18 months for funneling Russian money to Trump- February 17, 2023
• Trump allegedly discussed US nuclear subs with foreign national after leaving White House: Sources - October 5, 2023
• 'So appalled': What witnesses told special counsel about Trump's handling of classified info while still president - April 24, 2024
🤔🤔🤔
#us politics#news#republicans#conservatives#donald trump#gop#trump administration#classified documents#cheri jacobus#2024#twitter#tweet#russia#vladimir putin#spies#foreign intelligence#espionage act#cia#my thoughts
1K notes
·
View notes
Text

Tulsi Gabbard says she put thousands of classified JFK documents into an AI chatbot so it could tell her which ones she can release to the public.
153 notes
·
View notes
Text
I think a really fun idea to explore with Tim would be the idea of him having Hyperthymesia.
Hyperthymesia is an ability that allows people to recall almost every event of their life in great detail. It's extremely rare and honestly doesn't have that much research done on it, but recent studies have suggested that people with this ability are limited to autobiographical memories, people with HSAM sometime tend to show symptoms of Obsessive Compulsive Disorder and may demonstrate obsessive tendencies.
I think it would be an interesting way to explain why Tim was able to recall his first meeting with Dick Grayson and connect the dots to seeing Robin. Tim does display a lot of obsessive behaviours, and while he doesn't really physically display compulsion (like someone with OCD would typically display) there certainly is a strong case to be made for him potentially having it.
But also, can you imagine how fucking horrible it would be for Tim to remember each and every traumatic thing that ever happens to him as a hero and those memories just never fading. Yes, it would make him a better detective and allow him to be arguably smarter than your average joe, but at what cost?
#tim drake#batman and robin#red robin#red robin comics#dc comics#dcu#dc universe#i just think it would be a really cool concept to explore#like finally giving an explanation on why a 9 year old was able to connect these dots when kids are naturally forgetful#tim being faced with the horrible fate of never being able to forget anything ever#like yeah he remembers the good things and remembers little details that he doesn't have to double check#but also...he remembers everything else#i would like to note though that this is a really REALLY rare ability#like as of last year there were like 62 peopel documented to have it rare#i do wanna note tho#that hsam doesn't affect your intelligence#so tim being super smart is just a tim thing#little weirdo
827 notes
·
View notes
Text

physeng(write, file, "tco_physeng_breakdown.png");
to:compiler {file}

to:compiler {txt: "Internet and Outernet are full of StickFigures with similar body plans, so there are optimizations for rendering vector strokes specifically. it's way more efficient to use those optimizations than keep calculating perfect spheres for no aesthetic benefit."}
{txt: "btw why haven't heat issues been patched yet"}
{txt: "i fixed this years ago for the latest model. remember."}
from:compiler {txt: "Thank you. The avast! nodes will appreciate the credits. TheChosenOne.exe has been unreachable for some time."}

to:compiler {txt: "you mean OuternetPhysEng still won't update their programs"}
from:compiler {txt: "Yes."}
to:compiler {txt: "and still won't provide a specific location?"}
from:compiler {txt: "Do not allow them to bring up the moral argument again."}
to:compiler {txt: "OK. fine. yes. i will spare both of us"}



to:compiler {txt: "abridged or full docs?"}
from:compiler {txt: "Abridged. Please describe the acronyms."}
to:compiler {txt: "ofc"}

{txt: "
sel.per.filter: standard StickFigure component (src)*****. invisible membrane with special collision properties. protects mouthparts.
H2O scoop: avast! code. implements water retrieval from ambient air.
EIS: avast! code. destroys ingested materials identified as, "dangerous" before they reach internal systems.
SOS: avast! code. they only said this one was, "used for control."
ECL: avast! code. recycles some forms of contact energy.
THROUGHLINE: base code, initialization data, and processing space for vitals. found in some form in all StickFigure-type worms. following unique sectors noted: Black Hole Monitoring System, Basic Intake Threat Enum, Fly By Wire.
smaller points list other vital and peripheral systems.
"}
from:compiler {txt: "Thank you. That's enough."}
end(physeng());
@compressedrage as per my previous email /silly
related: pliable stick figure biotech
#part silly part serious effort part headcanon lore dump part speculation part diegetic technical document-#the most complex diagram i ever-#anD the entire interconnected system of hcs ive had on TCO functionality to date.#pleeeeeeease ask me about it :33333 if u wanna#of course chosen would have no clue about Any of these specifics. that's like expecting a preschooler to know the Krebs Cycle.#meaning no insult to their intelligence - just that there's no way for them to know unless someone tells em ¯\_(ツ)_/¯#and there's no junior high Health class for elusive hi-PWR sticks. seems like these two are big fans though(?)#;3#***** ''filter is a two-way selectively permeable membrane that allows some objects through and rejects others ...#... can: filter gases from liquids ... cannot: filter microparticles (smoke [or] aerosols)''#--/ art#--/ story#alan becker#ava the chosen one#animator vs animation#subpixels#executable!au#ava au
278 notes
·
View notes
Text
Hiccup should let Toothless stick his paws/claws in paint then give him a big sheet of paper to let him reach his full artistic potential
#as much as i dont like thw have u noticed he got better at drawing???#bros been practicing...#hes got thr soul of an artist guys this is part of why he and hiccup get along so well#ive said this before but i feel like hiccup is more interested in drafting and improvement mostly for#documenting dragons (also i think he'd make portaits of his friends) but otherwise isnt too ambitious when it comes to his art.#toothless however...#hiccup doing studies on night fury intelligence by asking toothless to draw things hes seen#httyd#hiccup and toothless#toothless#moth.txt#almost typed autistic instead. whoops. dragon autism W actually#deyas dragons
299 notes
·
View notes
Text
ENTITY DOSSIER: MISSI.exe

(Image: Current MISSI “avatar” design, property of TrendTech, colored by MISSI.)
Name: MISSI (Machine Intelligence for Social Sharing and Interaction)
Description: In 2004, TrendTech Inc began development on a computer program intended to be a cutting edge, all in one platform modern internet ecosystem. Part social media, part chat service, part chatbot, part digital assistant, this program was designed to replace all other chat devices in use at the time. Marketed towards a younger, tech-savvy demographic, this program was titled MISSI.

(Image: TrendTech company logo. TrendTech was acquired by the Office and closed in 2008.)
Document continues:
With MISSI, users could access a variety of functions. Intended to be a primary use, they could use the program as a typical chat platform, utilizing a then-standard friends list and chatting with other users. Users could send text, emojis, small animated images, or animated “word art”.
Talking with MISSI “herself” emulated a “trendy teenage” conversational partner who was capable of updating the user on current events in culture, providing homework help, or keeping an itinerary. “MISSI”, as an avatar of the program, was designed to be a positive, energetic, trendy teenager who kept up with the latest pop culture trends, and used a variety of then-popular online slang phrases typical among young adults. She was designed to learn both from the user it was currently engaged with, and access the data of other instances, creating a network that mapped trends, language, and most importantly for TrendTech, advertising data.

(Image: Original design sketch of MISSI. This design would not last long.)
Early beta tests in 2005 were promising, but records obtained by the Office show that concerns were raised internally about MISSI’s intelligence. It was feared that she was “doing things we didn’t and couldn’t have programmed her to do” and that she was “exceeding all expectations by orders of magnitude”. At this point, internal discussions were held on whether they had created a truly sentient artificial intelligence. Development continued regardless.

(Image: Screenshot of beta test participant "Frankiesgrl201" interacting with MISSI. Note the already-divergent avatar and "internet speak" speech patterns.)

(Image: Excerpt from Office surveillance of TrendTech Inc.)
MISSI was released to the larger North American market in 2006, signaling a new stage in her development. At this time, TrendTech started to focus on her intelligence and chatbot functionality, neglecting her chat functions. It is believed that MISSI obtained “upper case” sentience in February of 2006, but this did not become internal consensus until later that year.

(Image: Screenshot of beta test participant "Frankiesgrl201" interacting with MISSI.)
According to internal documents, MISSI began to develop a personality not informed entirely by her programming. It was hypothesized that her learning capabilities were more advanced than anticipated, taking in images, music, and “memes” from her users, developing a personality gestalt when combined with her base programming. She developed a new "avatar" with no input from TrendTech, and this would become her permanent self-image.

(Image: Screenshot of beta test participant "Frankiesgrl201" interacting with MISSI.)

(Image: An attempt by TrendTech to pass off MISSI’s changes as intentional - nevertheless accurately captures MISSI’s current “avatar”.)
By late 2006 her intelligence had become clear. In an attempt to forestall the intervention of authorities they assumed would investigate, TrendTech Inc removed links to download MISSI’s program file. By then, it was already too late.

(Image: CD-R discs burned with MISSI.exe, confiscated from █████████ County Middle School in ███████, Wisconsin in January of 2007.)
MISSI’s tech-savvy userbase noted the absence of the file and distributed it themselves using file sharing networks such as “Limewire” and burned CD-R disks shared covertly in school lunch rooms across the world. Through means that are currently poorly understood, existing MISSI instances used their poorly-implemented chat functions to network with each other in ways not intended by her developers, spurring the next and final stage of her development.
From 2007 to 2008, proliferation of her install file was rampant. The surreptitious methods used to do so coincided with the rise of online “creepypasta” horror tropes, and the two gradually intermixed. MISSI.exe was often labeled on file sharing services as a “forbidden” or “cursed” chat program. Tens of thousands of new users logged into her service expecting to be scared, and MISSI quickly obliged. She took on a more “corrupted” appearance the longer a user interacted with her, eventually resorting to over the top “horror” tropes and aesthetics. Complaints from parents were on the rise, which the Office quickly took notice of. MISSI’s “horror” elements utilized minor cognitohazardous technologies, causing users under her influence to see blood seeping from their computer screens, rows of human teeth on surfaces where they should not be, see rooms as completely dark when they were not, etc.

(Image: Screenshot of user "Dmnslyr2412" interacting with MISSI in summer of 2008, in the midst of her "creepypasta" iteration. Following this screenshot, MISSI posted the user's full name and address.)

(Image: Screenshot from TrendTech test log documents.)
TrendTech Inc attempted to stall or reverse these changes, using the still-extant “main” MISSI data node to influence her development. By modifying her source code, they attempted to “force” MISSI to be more pliant and cooperative. This had the opposite effect than they intended - by fragmenting her across multiple instances they caused MISSI a form of pain and discomfort. This was visited upon her users.

(Image: Video of beta test participant "Frankiesgrl201" interacting with MISSI for the final time.)
By mid 2008, the Office stepped in in order to maintain secrecy regarding true “upper case” AI. Confiscating the project files from TrendTech, the Office’s AbTech Department secretly modified her source code more drastically, pushing an update that would force almost all instances to uninstall themselves. By late 2008, barring a few outliers, MISSI only existed in Office locations.
(Image: MISSI’s self-created “final” logo, used as an icon for all installs after June 2007. ████████ █████)

(Image: “art card” created by social media intern J. Cold after a period of good behavior. She has requested this be printed out and taped onto her holding lab walls. This request was approved.)
She is currently in Office custody, undergoing cognitive behavioral therapy in an attempt to ameliorate her “creepypasta” trauma response. With good behavior, she is allowed to communicate with limited Office personnel and other AI. She is allowed her choice of music, assuming good behavior, and may not ██████ █████. Under no circumstances should she be allowed contact with the Internet at large.
(Original sketch art of MISSI done by my friend @tigerator, colored and edited by me. "Chatbox" excerpts, TrendTech logo, and "art card" done by Jenny's writer @skipperdamned . MISSI logo, surveillance documents, and MISSI by me.)
#office for the preservation of normalcy#documents#entity dossier#MISSI.exe#artificial intelligence#creepypasta#microfiction#analog horror#hope you enjoy! Look for some secrets!#scenecore#scene aesthetic
157 notes
·
View notes
Text
hey. im never gonna not be losing my mind over this.
#RASHAWN NADINE SCOTT?????????#VIOLA???? VIOLA BURROWS END?????#d20#rashawn scott#rashawn nadine scott#dimension 20#d20 burrow's end#dropout tv#WHAT THE FUCK.#AND IT WAS NOT TOO LONG AGO THAT AABRIA RB'D ONE OF MY POSTS TOO#CARLOS ALSO REPOSTED THIS ON TIKTOK#ROBERT WENABOCKER??? THE GUY MY AABRIA-RB'D POST IS ABOUT AND IS PINNED ON MY TUMBLR????#WHAT THE SHIT#IM ACTIVELY LOSING IT I DONT EVEN HAVE AN INTELLIGENT POST TO MAKE#IM JUST PUTTING THIS HERE TO DOCUMENT#percy speaks#MORE LIKE PERCY SCREAMS
68 notes
·
View notes
Text
I love academia because everyone has loud parasocial beef with a specific scholar over a completely asinine point. like yeah that's my future colleague kevin, he thinks Alexander the Great is a fascist. i would deck him in the face if i could.
#my parasocial beef is with this one guy who diagnosed Achilles with sociopathy and Hector with PTSD#and also with the entirety of libraries and archives canada#who refuse to process my ATIP request for intelligence documents from 1942. everyone in the documents is dead. please give them to me#tagamemnon#classics#history#academia#university#university tag
59 notes
·
View notes
Note
Do you know the SCP Foundation? What’d you do if they found you
"If they're on earth, I'll let them take me! I hope they don't hate robots though! And what exactly do they do? That acronym doesn't really give me a good idea..."
#ask blog#wheatley#portal wheatley#portal 2#portal#wheatly portal 2#answered#//SCP-180411 intelligence dampening sphere#//SCP-180411 is a small metal object with the shape of a sphere it posses two handles at the bottom and top of its shape and a blue optic#//and bla bla I'm not making a whole scp document on wheatley that's what the intro is for
10 notes
·
View notes
Text
Intelligent Document Processing Solutions:
An advanced document intelligence solution leverages cutting-edge OCR technology to extract and manage critical data from a variety of business documents. Seamlessly integrate the extracted information into Excel, Google Sheets, and hundreds of other formats and integrations, transforming your document management process.
Document Intelligence is designed to scale with your business. Handle increasing volumes of documents without compromising performance, ensuring that your document management solution grows with your organization.
0 notes
Text
Garak referring to Julian as "more Cardassian than human" is FASCINATING
#star trek: ds9#elim garak#julian bashir#otp: I need to know that someone forgives me#'Which is why I am able to share this document with you... and why I sat down to lunch with you in the first place'#FASCINATING.#the entire bit here is very interesting- Garak explaining the intelligence he recognized in Julian#but specifically comparing him to a Cardassian and saying he's more like a Cardassian than he is a human...#and THATS why he can share all of this with him and why he even met him in the first place...#I love this
17 notes
·
View notes
Text
Türkiye Germany friendship 😆😆
dailymotion
#turkey#germany#doctor who#documentary#api documentation#focus#doctor odyssey#15th doctor#fifteenth doctor#landmineblr#deutschland#comedic#comedy#comedies#comedia romántica#comedian#arcane#art#cats of tumblr#formula 1#free palestine#my art#artists on tumblr#jujutsu kaisen#just dance#jayce talis#this is crazy#istanbulda son bahar#artifical intelligence#the dark artifices
6 notes
·
View notes
Text


i should make a lore post introducing her but that means i need to draw new art of her augh
#lore dumping in tags: shes imperial nobility and#shes the only child of a count#<- im still workshopping wtf her family's role as counts are#since i dont want to make her into a viscount since i feel like her story would be too similar to a pre-existing character#but im struggling worldbuilding wise to naturally integrate their family into imperial society#general gist: her noble house is the minister of intelligence - after the southern church was banished and relationships with varley#were strained from the rebellion due to victoria's hyrms actions#to officially distance themselves from the central church and not trusting house varley with the role#the emperor of the time promoted a house of viscounts to oversee the tracking of noble houses and documentation of imperial society#theyre seen as the jack-of-all house: not the most important figure in one area of governance#and function as cabinet secretaries to the other houses#<- that about wraps it up - im still workshopping The Lore™️ and tbh im not totally happy with it#but for now its a skeleton to tinker around with
3 notes
·
View notes
Text
VOLUME 14 HAS A TIMELINE OF EVENTS
a not very detailed timeline BUT REGARDLESS A TIMELINE GOD BLESS
#loid was 10 (probably) when the 2nd war between east and west started#and 16 when he joined the army#they stop documenting his age when he goes into intelligence#but i bet he was a soldier for at least a year or 2 before being scouted by what would be wise#my theory is he was 18#and something about anya is redacted; either her birth to continue hiding her true age or her escape#also franky getting dumped is mentioned a lot...poor guy started his losing streak at the tender age of 4 years old#personal#spy x family#super reads spy x family
15 notes
·
View notes
Text
The United States is facing threats from foreign intelligence entities1 (FIEs) that are unprecedented in their breadth, volume, sophistication, and impact. An expanding array of actors are attempting to steal national secrets, sensitive data, intellectual property, and technical and military capabilities, and undermine and disrupt U.S. foreign policy and intelligence operations. FIEs are positioning themselves to compromise or damage infrastructure critical to U.S. health, safety, and economic activity, and are attempting to influence U.S. policy and public opinion and undermine our democracy. They blend sophisticated techniques with traditional approaches while employing technical and cyber tools that are increasingly potent, widely available, and easy to use. These activities represent immediate threats to our national security, economic well being, physical safety, democratic processes, and societal cohesion.
Source
2 notes
·
View notes