#privacy. - One Security App Android
Explore tagged Tumblr posts
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
81 notes
·
View notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
34 notes
·
View notes
Text
The eye-popping scandal surrounding the Trump cabinet’s accidental invitation to The Atlantic’s editor in chief to join a text-message group secretly planning a bombing in Yemen has rolled into its third day, and that controversy now has a name: SignalGate, a reference to the fact that the conversation took place on the end-to-end encrypted free messaging tool Signal.
As that name becomes a shorthand for the biggest public blunder of the second Trump administration to date, however, security and privacy experts who have promoted Signal as the best encrypted messaging tool available to the public want to be clear about one thing: SignalGate is not about Signal.
Since The Atlantic’s editor, Jeffrey Goldberg, revealed Monday that he was mistakenly included in a Signal group chat earlier this month created to plan US airstrikes against the Houthi rebels in Yemen, the reaction from the Trump cabinet’s critics and even the administration itself has in some cases seemed to cast blame on Signal for the security breach. Some commentators have pointed to reports last month of Signal-targeted phishing by Russian spies. National security adviser Michael Waltz, who reportedly invited Goldberg to the Signal group chat, has even suggested that Goldberg may have hacked into it.
On Wednesday afternoon, even President Donald Trump suggested Signal was somehow responsible for the group chat fiasco. “I don't know that Signal works,” Trump told reporters at the White House. “I think Signal could be defective, to be honest with you.”
The real lesson is much simpler, says Kenn White, a security and cryptography researcher who has conducted audits on widely used encryption tools in the past as the director of the Open Crypto Audit Project: Don’t invite untrusted contacts into your Signal group chat. And if you’re a government official working with highly sensitive or classified information, use the encrypted communication tools that run on restricted, often air-gapped devices intended for a top-secret setting rather than the unauthorized devices that can run publicly available apps like Signal.
“Unequivocally, no blame in this falls on Signal,” says White. “Signal is a communication tool designed for confidential conversations. If someone's brought into a conversation who’s not meant to be part of it, that's not a technology problem. That's an operator issue.”
Cryptographer Matt Green, a professor of computer science at Johns Hopkins University, puts it more simply. “Signal is a tool. If you misuse a tool, bad things are going to happen,” says Green. “If you hit yourself in the face with a hammer, it’s not the hammer’s fault. It’s really on you to make sure you know who you’re talking to.”
The only sense in which SignalGate is a Signal-related scandal, White adds, is that the use of Signal suggests that the cabinet-level officials involved in the Houthi bombing plans, including secretary of defense Pete Hegseth and director of national intelligence Tulsi Gabbard, were conducting the conversation on internet-connected devices—possibly even including personal ones—since Signal wouldn’t typically be allowed on the official, highly restricted machines intended for such conversations. “In past administrations, at least, that would be absolutely forbidden, especially for classified communications,” says White.
Indeed, using Signal on internet-connected commercial devices doesn’t just leave communications open to anyone who can somehow exploit a hackable vulnerability in Signal, but anyone who can hack the iOS, Android, Windows, or Mac devices that might be running the Signal mobile or desktop apps.
This is why US agencies in general, and the Department of Defense in particular, conduct business on specially managed federal devices that are specially provisioned to control what software is installed and which features are available. Whether the cabinet members had conducted the discussion on Signal or another consumer platform, the core issue was communicating about incredibly high-stakes, secret military operations using inappropriate devices or software.
One of the most straightforward reasons that communication apps like Signal and WhatsApp are not suitable for classified government work is that they offer “disappearing message” features—mechanisms to automatically delete messages after a preset amount of time—that are incompatible with federal record retention laws. This issue was on full display in the principals’ chat about the impending strike on Yemen, which was originally set for one-week auto-delete before the Michael Waltz account changed the timer to four-week auto-delete, according to screenshots of the chat published by The Atlantic on Wednesday. Had The Atlantic’s Goldberg not been mistakenly included in the chat, its contents might not have been preserved in accordance with long-standing government requirements.
In congressional testimony on Wednesday, US director of national intelligence Tulsi Gabbard said that Signal can come preinstalled on government devices. Multiple sources tell WIRED that this is not the norm, though, and noted specifically that downloading consumer apps like Signal to Defense Department devices is highly restricted and often banned. The fact that Hegseth, the defense secretary, participated in the chat indicates that he either obtained an extremely unusual waiver to install Signal on a department device, bypassed the standard process for seeking such a waiver, or was using a non-DOD device for the chat. According to political consultant and podcaster Fred Wellman, DOD “political appointees” demanded that Signal be installed on their government devices last month.
Core to the Trump administration’s defense of the behavior is the claim that no classified material was discussed in the Signal chat. In particular, Gabbard and others have noted that Hegseth himself is the classification authority for the information. Multiple sources tell WIRED, though, that this authority does not make a consumer application the right forum for such a discussion.
“The way this was being communicated, the conversation had no formal designation like 'for official use only' or something. But whether it should have been classified or not, whatever it was, it was obviously sensitive operational information that no soldier or officer would be expected to release to the public—but they had added a member of the media into the chat,” says Andy Jabbour, a US Army veteran and founder of the domestic security risk-management firm Gate 15.
Jabbour adds that military personnel undergo annual information awareness and security training to reinforce operating procedures for handling all levels of nonpublic information. Multiple sources emphasize to WIRED that while the information in the Yemen strike chat appears to meet the standard for classification, even nonclassified material can be extremely sensitive and is typically carefully protected.
“Putting aside for a moment that classified information should never be discussed over an unclassified system, it’s also just mind-boggling to me that all of these senior folks who were on this line and nobody bothered to even check, security hygiene 101, who are all the names? Who are they?” US senator Mark Warner, a Virginia Democrat, said during Tuesday’s Senate Intelligence Committee hearing.
According to The Atlantic, 12 Trump administration officials were in the Signal group chat, including vice president JD Vance, secretary of state Marco Rubio, and Trump adviser Susie Wiles. Jabbour adds that even with decisionmaking authorities present and participating in a communication, establishing an information designation or declassifying information happens through an established, proactive process. As he puts it, “If you spill milk on the floor, you can’t just say, ‘That’s actually not spilled milk, because I intended to spill it.’”
All of which is to say, SignalGate raises plenty of security, privacy, and legal issues. But the security of Signal itself is not one of them. Despite that, in the wake of The Atlantic’s story on Monday, some have sought tenuous connections between the Trump cabinet’s security breach and Signal vulnerabilities. On Tuesday, for example, a Pentagon adviser echoed a report from Google’s security researchers, who alerted Signal earlier this year to a phishing technique that Russian military intelligence used to target the app’s users in Ukraine. But Signal pushed out an update to make that tactic—which tricks users into adding a hacker as a secondary device on their account—far harder to pull off, and the same tactic also targeted some accounts on the messaging services WhatsApp and Telegram.
“Phishing attacks against people using popular applications and websites are a fact of life on the internet,” Signal spokesperson Jun Harada tells WIRED. “Once we learned that Signal users were being targeted, and how they were being targeted, we introduced additional safeguards and in-app warnings to help protect people from falling victim to phishing attacks. This work was completed months ago."
In fact, says White, the cryptography researcher, if the Trump administration is going to put secret communications at risk by discussing war plans on unapproved commercial devices and freely available messaging apps, they could have done much worse than to choose Signal for those conversations, given its reputation and track record among security experts.
“Signal is the consensus recommendation for highly at-risk communities—human rights activists, attorneys, and confidential sources for journalists,” says White. Just not, as this week has made clear, executive branch officials planning airstrikes.
28 notes
·
View notes
Text
How to install NewPipe on Android
NewPipe is a YouTube replacement client for Android devices. It's open-source (meaning, you can see all of their code as you please), privacy-oriented, lightweight, and supports features that are normally locked behind a YouTube Premium paywall.
Disclaimer: I am not affiliated with NewPipe, YouTube, Android, Google, Alphabet Inc, or any other brand or name mentioned here. I made this guide to help my friends who were curious.
NewPipe's Website: https://newpipe.net/
The GitHub Repository
Step 0. Compatibility check
Make sure you're running an Android device! This won't work on an Apple device of any kind! Also, for those more tech-savvy among you, if you have the F-Droid store installed, you can download NewPipe straight from there!
Step 1. Downloading
Go to NewPipe's Github repo (repository, the codebase or where all of the code is stored). Scroll to the bottom of the page until you see "Releases". Click on the one that says "Latest" next to it in a little green bubble:

Your version number (v#...) will be different if you're reading this in the future! That's okay. Scroll past the changelog (unless you want to read it!) until you find "Assets":

Click on the first one, the one with the little cube ending in .apk. APK files are Android Package (Kit) and are the main format for downloading apps. Once you click on the link, it should begin downloading or your browser will ask you to confirm that you want to download this file. You should always verify the filename matches what you expect it to be (namely, the file format) before attempting to install! It might take a few moments for the file to download depending on your internet connection.
Step 2. Installation
Once you have the file downloaded, you can click the download popup in your notification bar or find the file in your device's file system. One of 2 things will happen:
You will get a popup asking if you want to install an APK by the name of NewPipe - confirm that you do (and make sure the app is really NewPipe!) and it will install automatically. You can then click "Open" to open the app and begin using it.
You will get a popup warning you that you have the ability to install apps from unknown sources disabled and that you can't install this. This is normal and does not mean that you downloaded the wrong thing.
If you got the first popup, continue past this step. For those of you who got the second, let's go over what this means.
By default, most Androids have this setting disabled. This is for security purposes, so you can't accidentally install a malicious app from the whole internet. If you enable this setting (allow installations from unknown/unsigned sources), you are theoretically putting yourself at risk. Realistically, you're probably fine. But, after installing NewPipe, you can always re-disable the setting if it makes you more comfortable. That will prevent you from installing updates in the future, but it can always be re-enabled.
Ready to turn that setting on? It will vary by your individual device! Some devices will take you directly to the page with the setting upon failed installation, and some you will just have to find it yourself using the searchbar in settings.
Once you've allowed installations from unknown sources (wording may vary slightly), try to repeat the steps above of clicking the download popup or finding the APK in your files and trying to install it. It should work correctly this time!
Step 3. Updating NewPipe
Like most apps, NewPipe is in development currently and frequently has new versions released to improve it and fix bugs. Unlike most apps, NewPipe needs to be manually updated, since we haven't downloaded through the Google Play store.
To update NewPipe, all you have to do is follow the above steps for installing the app, except that when you get the popup asking to install it, it will instead say "Update". That's it! NewPipe and Android handle the rest.
NewPipe also has popup notifications for when the app has a new update, so you don't have to worry about checking the GitHub for a new release. Just click on the "A new version is available" popup and it should take you directly to the webpage.
That's it! Enjoy browsing videos in peace without ads and with the ability to download and so much more. Pro tip: you can copy paste YouTube links into the NewPipe search bar to go directly to that video/playlist/channel.
#newpipe#youtube#youtube client#youtube replacement#how to install newpipe#android#android apk#android app#images#text#links#image descriptions#privacy#data privacy#internet privacy#big tech#data security#github#software#database#opensource#open source#newpipe app
30 notes
·
View notes
Text
MESSAGE FOR GHOST FANS
If you're not able to get to a drop spot for the Download drop for Rite Here Rite Now you can use a GPS spoofer app to spoof your location to match any of the drops, if youre not sure of the drops go to
drops.nyc/ghost

The drops are all listed worldwide but unfortunately you have to click into them to see specifically where each one is but if you're spoofing your location it doesn't matter which you pick
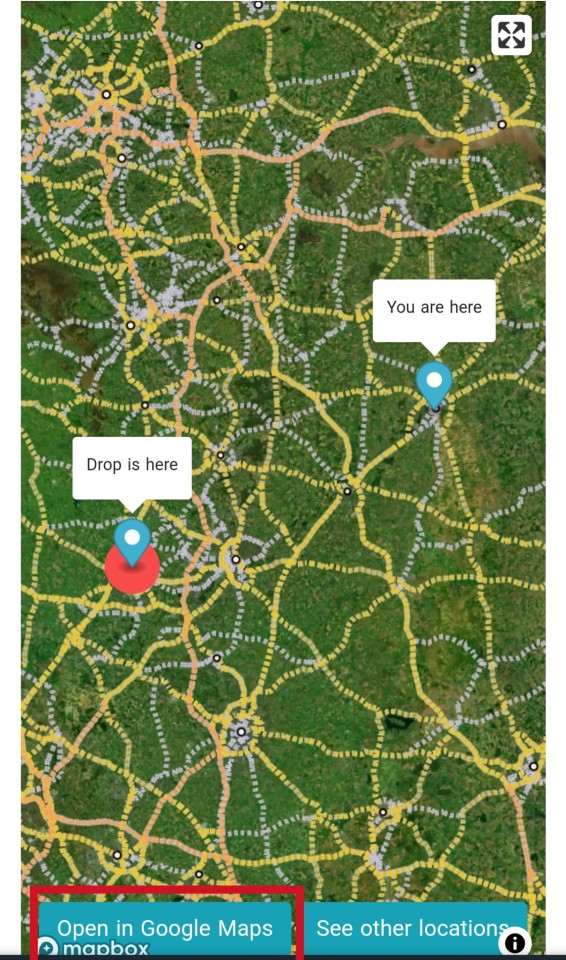
When you open it it will then tell you how far that drop is from you and give you the option to open in Google or apple maps, open it, this gives you the exact location of that drop, then go to your GPS spoofing app.
Android folks will likely need to enable developer access for this, to do that go to your phones settings, then about, then look for this phones build version, I think mine was called like a miui version, and you tap on either the build number or the build name 5 or more times and it should then tell you that you're now a developer.

you can then go to your developer options and look for a GPS or locations sectioned with an entry named something like 'select mock GPS app' or similar, select the GPS spoofer you installed.

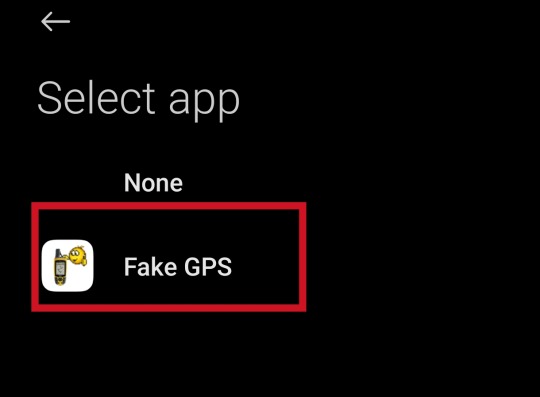
Go back to your spoofer app and drop the pin near where the drop is

Check the drop site again.

In this case I dropped the pin near where the movie theatre was but the actual location of this GPS drop is slightly further down the street, if this happens, keep adjusting your GPS spoofer until you're in the area of effect for the drop.

When you've done it right, you should see this
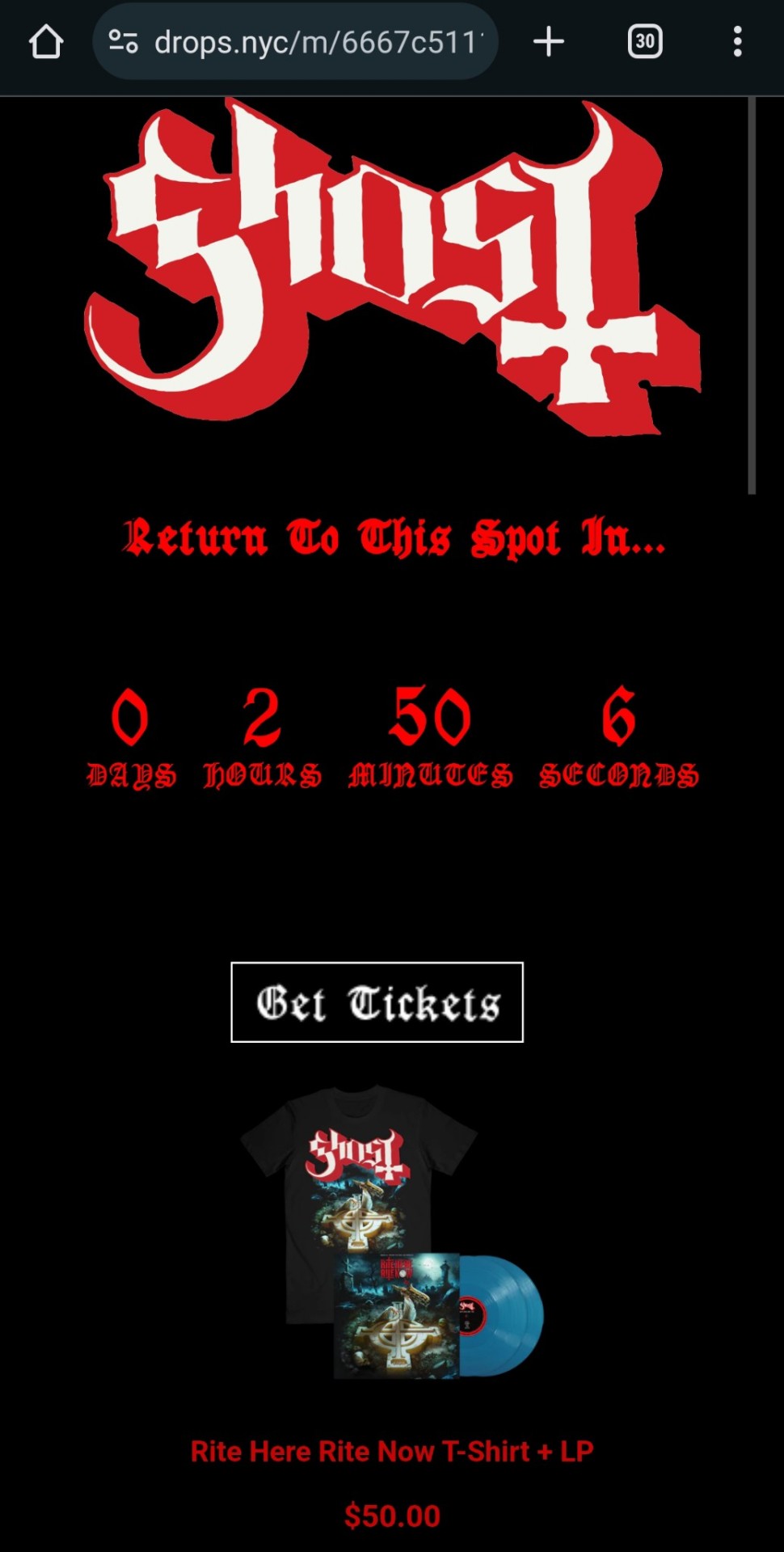
Apologies to any apple users, I dont have an iPhone to take screenshots but you go to your settings > privacy & security > developed mode and I think the rest of the steps should be similar.
Hope that helps any of you who are either too far away from a drop, or who are in range but the site keeps giving you errors and saying no drops found.
#rite here rite now#ghost#the band Ghost#ghost bc#papa emeritus iv#ghost movie#ghovie#ghost posting#copia#cardinal copia#papa emeritus#papa emeritus iii#papa emeritus ii#papa emeritus i#primo#secondo#terzo#tobias forge
26 notes
·
View notes
Text
Object permanence

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PDX on Jun 20 at BARNES AND NOBLE with BUNNIE HUANG. After that, it's LONDON (Jul 1) and MANCHESTER (Jul 2).

#15yrsago InfoLadies of Bangladesh revolutionize rural life https://www.theguardian.com/journalismcompetition/professional-two-wheel-triumph
#15yrsago Google and Viacom blend high-profile copyright suits with extreme profanity, as nature intended https://arstechnica.com/tech-policy/2010/05/f-those-mother-f-ers-youtubeviacom-lawsuit-gets-dirty/
#15yrsago Google offers encrypted search https://www.eff.org/deeplinks/2010/05/google-launches-encrypted-search
#15yrsago The Boneshaker: magic, latter-day Bradburian novel for young adults https://memex.craphound.com/2010/05/21/the-boneshaker-magic-latter-day-bradburian-novel-for-young-adults/
#15yrsago Scientology raid uncovers dossiers on local “enemies”: sexual habits, health info, political opinions https://www.ansa.it/web/notizie/rubriche/english/2010/05/20/visualizza_new.html_1794804082.html
#15yrsago Cracked vs. RIAA damages https://web.archive.org/web/20100524024915/http://www.cracked.com/funny-4003-the-pirate-bay/
#10yrsago NSA wanted to hack the Android store https://www.cbc.ca/news/canada/spy-agencies-target-mobile-phones-app-stores-to-implant-spyware-1.3076546
#10yrsago GM says you don’t own your car, you just license it https://web.archive.org/web/20150522003554/https://consumerist.com/2015/05/20/gm-that-car-you-bought-were-really-the-ones-who-own-it/
#10yrsago Today’s terrifying Web security vulnerability, courtesy of the 1990s crypto wars https://memex.craphound.com/2015/05/21/todays-terrifying-web-security-vulnerability-courtesy-of-the-1990s-crypto-wars/
#10yrsago Mark Zuckerberg just dropped another $100M to protect his privacy https://slate.com/business/2015/05/tech-billionaires-and-privacy-why-facebook-s-mark-zuckerberg-is-spending-millions-on-a-private-island.html
#5yrsago How spy agencies targeted Snowden journalists https://pluralistic.net/2020/05/21/profitable-butchers/#sources-and-methods
#5yrsago Monopolies killed corporate R&D https://pluralistic.net/2020/05/21/profitable-butchers/#all-d
#5yrsago Spotify's trying to kill podcasting https://pluralistic.net/2020/05/21/profitable-butchers/#rogan-monopolist
#5yrsago Black Americans' covid mortality is 2.5X white mortality https://pluralistic.net/2020/05/21/profitable-butchers/#ethnic-cleansing
#5yrsago On Madame Leota's side-table https://pluralistic.net/2020/05/21/profitable-butchers/#details-details
#5yrsago Private equity's healthcare playbook is terrifying https://pluralistic.net/2020/05/21/profitable-butchers/#looted
#5yrsago Patent troll sues ventilator makers https://pluralistic.net/2020/05/21/profitable-butchers/#ip-edge
#5yrsago The Lost Cause and MMT https://pluralistic.net/2020/05/21/profitable-butchers/#byebye-falc
#5yrsago Walt's grandson calls for Disney execs' bonuses to be canceled https://pluralistic.net/2020/05/21/profitable-butchers/#brad-lund
#1yrago Linkrot https://pluralistic.net/2024/05/21/noway-back-machine/#pew-pew-pew

6 notes
·
View notes
Text
Stop! Have you checked your phone’s ad privacy settings recently? No? Here’s a guide. It’s from 2022 but I can confirm that as of November 2024 the Apple stuff is still correct.
Android:
Settings —> Privacy —> ads —> delete advertising ID
On older versions you might not be able to delete the ID, but can reset it and there should still be a toggle to opt out: do both of those things!
iOS:
Two things to take care of, here. One) Apple already makes each app ask permission, but you can still tell it to just not even let them ask:
Settings —> privacy —> Tracking —> toggle off ‘allow apps to request to track’.
Two) settings —> privacy —> scroll riiiiiight down —> Apple advertising —> toggle off personalised ads.
Samsung:
Settings —> privacy —> Customisation services —> ‘stop customising all devices’
Xiaomi:
Settings —> passwords and security —> Authorisation & revocation —> toggle off ‘MSA’
Why it Matters
‘The ad identifier is a string of letters and numbers that uniquely identifies your phone, tablet, or other smart device. It exists for one purpose: to help companies track you.
Third-party trackers collect data via the apps on your device. The ad ID lets them link data from different sources to one identity you. In addition, since every app and tracker sees the same ID, it lets data brokers compare notes about you. Broker A can buy data from broker B, then use the ad identifier to link those two datasets together. Simply, the ad ID is the key that enables a whole range of privacy harms: invasive 3rd-party profiling by Facebook and Google, pseudoscientific psychographic targeting by political consultants like Cambridge Analytica, and location tracking by the U.S. military.
Sometimes, participants in the data pipeline will argue that the ad ID is anonymous or pseudo-anonymous, not “personally identifying” information, and imply that it does not pose a serious privacy threat. This is not true in practice. First, the ad ID is commonly used to help collect data that is obviously personally identifiable, like granular location data. If you can see where a person works, sleeps, studies, socializes, worships, and seeks medical care, you don’t need their email address to help identify them. And second, an entire industry exists to help trackers link ad IDs to more directly identifying information, like email addresses and phone numbers. In a vacuum, the ad ID may be anonymous, but in the context of the tracking industry, it is a ubiquitous and effective identifier.
Disabling this ID makes it substantially harder for most advertisers and data brokers to track you. These industries process data from millions or billions of users every day, and they rely on convenient technologies like the ad ID to make that kind of scale possible. Removing this tool from their toolbox will result in substantially less data that can be associated with you in the wild. It is not only beneficial to your privacy, it also makes the surveillance advertising industry less profitable.‘
9 notes
·
View notes
Text
How to Watch IPTV on Phone?

How to Watch IPTV on Phone: Full Step-by-Step Guide
In today’s fast-paced world, the ability to stream your favorite live TV channels, sports, and movies directly from your smartphone is more convenient than ever. Thanks to IPTV (Internet Protocol Television), you can now watch high-quality content on the go, right from your Android or iOS phone.
This complete guide will show you how to watch IPTV on your phone, step-by-step, with real examples from IPTV providers like StreamView IPTV and Digitalizard. Whether you use Android or iPhone, this tutorial will help you get started easily.
What is IPTV?
IPTV (Internet Protocol Television) delivers live TV channels and on-demand video content through internet connections, rather than traditional cable or satellite. With IPTV, all you need is:
A reliable IPTV subscription (e.g., Streamview IPTV or Digitalizard),
An IPTV player app,
A good internet connection.
Requirements to Watch IPTV on Your Phone
To watch IPTV on your smartphone, you need:
📶 Stable internet connection (minimum 10 Mbps recommended)
📲 A compatible IPTV app for Android or iOS
🔐 Your IPTV credentials (M3U playlist link or Xtream Codes)
🔄 An updated Android or iOS device
How to Watch IPTV on Android Phone? Step-by-Step Guide
Step 1: Get Your IPTV Subscription
Sign up with a reliable IPTV provider like:
🔹 Streamview IPTV – Offers M3U and Xtream Code login, with 24/7 channels and VOD content.
🔹 Digitalizard – Known for HD quality and global channels, compatible with many IPTV players.
Once registered, they’ll email you:
M3U Playlist URL
Or Xtream Codes (Username, Password, and Server URL)
Step 2: Download a Reliable IPTV Player App
Some of the best IPTV apps for Android:
IPTV Smarters Pro
TiviMate IPTV Player
XCIPTV Player
GSE Smart IPTV
Go to Google Play Store, search for one of these apps, and install it.
Step 3: Load IPTV Playlist
Open the IPTV app (e.g., IPTV Smarters Pro).
Choose how you want to login:
Load Your Playlist or File URL (M3U)
Login with Xtream Codes API
Enter the details you received from Streamview IPTV or Digitalizard.
Tap Add User and wait for the channels to load.
Start streaming your favorite live TV channels, sports, or movies.
How to Watch IPTV on iPhone (iOS)? Step-by-Step Guide
Step 1: Subscribe to IPTV Service
Choose from verified providers like:
Streamview IPTV – Offers multi-device support including iOS.
Digitalizard – Offers fast delivery of login details and mobile-compatible links.
Step 2: Download an IPTV Player App for iOS
Top IPTV apps for iPhone:
IPTV Smarters – Player
GSE Smart IPTV
iPlayTV
Smarters Player Lite
Go to the App Store, search for one of these apps, and install it.
Step 3: Configure the App
Open the IPTV app on your iPhone.
Select either Xtream Codes Login or M3U Playlist option.
Enter:
Server URL
Username
Password (provided by Streamview IPTV or Digitalizard)
Tap Login and wait for the channel list to load.
Enjoy streaming HD content directly on your iPhone.
Key Features You’ll Enjoy
When using services like Streamview IPTV or Digitalizard, here’s what you typically get:
✅ 10,000+ Live TV Channels
✅ Video On Demand (Movies, TV Shows)
✅ 24/7 Sports & PPV Channels
✅ EPG (Electronic Program Guide)
✅ Catch-up & Recording Options (depends on player)
✅ Anti-freeze Technology
Use a VPN for Secure Streaming
To protect your privacy and avoid ISP throttling, it’s recommended to use a VPN while streaming IPTV on your phone. Apps like NordVPN, ExpressVPN, or Surfshark work great with mobile devices.
Troubleshooting Tips
Buffering? Switch to a lower-quality stream or use a VPN.
Can’t login? Double-check M3U/Xtream details or contact support.
App not loading? Clear cache or reinstall the IPTV player.
Final Thoughts
Watching IPTV on your phone is one of the easiest ways to enjoy live TV, sports, movies, and shows wherever you go. Whether you're using Android or iPhone, all you need is a trusted IPTV provider like Streamview IPTV or Digitalizard, and a reliable IPTV player app.
With a simple setup and internet access, you’ll have 24/7 entertainment right in your pocket.
FAQs
Can I watch IPTV on multiple devices?
Yes, both Streamview IPTV and Digitalizard support multi-device use. Check your plan for simultaneous connections.
Is it legal to use IPTV on my phone?
Using licensed IPTV services is legal. Avoid using pirated or unverified sources.
Do I need a VPN for mobile IPTV?
A VPN is not mandatory but is highly recommended for security and privacy.
Can I record IPTV on my phone?
Some apps like XCIPTV support recording on Android. iOS options may be limited.
#blog#blog intro#ask blog#blogging#shifting blog#tech#iptv subscription#best iptv#iptv#iptv service#iptv usa#abonnement iptv#iptv firestick
3 notes
·
View notes
Text
Browser with Free VPN: Why Opera GX Is a Gamer’s Best Friend
What Is Opera GX?
Opera GX is a special version of the Opera browser designed specifically for gamers. It includes unique features such as:
CPU, RAM, and network limiters
RGB customization
Twitch and Discord integrations
And of course, a built-in free VPN
Unlike many free VPN extensions, Opera GX offers a native VPN that is easy to activate and doesn’t require extra installations.
1. Built-In Free VPN: Privacy Without the Price
One of the standout features of Opera GX is its completely free VPN, built right into the browser. No registration, no bandwidth limits, and no hidden fees.
Key advantages:
Mask your IP address for more secure browsing
Bypass geo-blocks for websites or game-related content
Use public Wi-Fi safely, especially when gaming on a laptop
This VPN is perfect for casual protection — great for when you don’t need a full system-wide VPN but still want to browse or download safely.
2. Optimized for Gaming
Opera GX isn’t just about looks — it’s packed with performance tools to enhance your gaming experience:
GX Control: Limit how much RAM or CPU the browser can use, so your games run smoother
Network limiter: Prevent background tabs from using up bandwidth during online play
GX Cleaner: Clean your cache and temp files to keep everything running fast
All these features are accessible with just a few clicks and can make a noticeable difference in multitasking while gaming.
3. Built-in Integrations for Gamers
Opera GX understands the gamer lifestyle — it includes Twitch, Discord, and even YouTube Music integrations directly in the sidebar. No need to switch tabs or open extra apps.
You also get:
Gaming news feeds curated for your region
GX Corner: Stay updated on game deals, releases, and free games
Sound effects and custom themes for an immersive experience
4. Cross-Platform and Easy to Use

Opera GX is available on Windows, macOS, Android, and iOS. This means you can enjoy the same privacy and performance features whether you’re on a gaming PC, laptop, or mobile device.
Sync your bookmarks, tabs, and VPN settings across devices effortlessly.
5. Is Opera GX’s Free VPN Enough?

While Opera GX’s VPN is excellent for basic privacy and unblocking, it only applies to browser traffic — not your entire system or gaming apps.
Use it for:
Downloading games or patches safely
Accessing region-locked sites or offers
Casual browsing and streaming
Not ideal for:
Protecting against DDoS in multiplayer games
Encrypting traffic outside the browser (e.g., Steam, Riot, etc.)
For advanced security, consider pairing Opera GX with a premium VPN for full-device protection.
Final Verdict
Opera GX is more than just a stylish browser — it’s a true ally for gamers. With a built-in free VPN, resource controls, and gamer-centric tools, it combines privacy, performance, and personality like no other browser.
If you’re looking for a browser with free VPN that’s designed with gamers in mind, Opera GX is the clear winner.
2 notes
·
View notes
Text
What are the unique challenges faced in developing iOS apps?
iOS App Development Services

iOS App Development is also known and considered for its sleek interface, strong security, and loyal user base and stand. However, building and crafting the apps for Apple devices isn't without its hurdles or obstacles. As the developers often face and seek unique challenges that differ and outlast from other platforms like Android. These challenges and obstacles can affect down the timelines, budgets, and overall user experience and matches if not managed carefully or sought in for.
Strict App Store Guidelines:
One of the most common challenges and occurrences in iOS App Development is meeting Apple's strict App Store policies and standard guidelines. As the review process is more rigorous and stiff sometimes than the most common platforms, apps can get rejected for minor issues—ranging from UI design to privacy violations. Developers must thoroughly review Apple's Human Interface Guidelines and follow best practices to avoid delays or rejections.
Limited Customization Options:
Apple has a highly controlled ecosystem. While this assures up the consistency and overall performance is maintained and is stuck with it, as it limits up the developers' ability to customize their user interfaces or access the set of certain hardware functionalities. This means more time and efficiency is intended to be spent finding creative workarounds to deliver unique features within the platform's constraints.
Device and OS Compatibility:
Though Apple has fewer devices than Android, iOS App Development must still account for different screen sizes, resolutions, and operating system versions. Supporting older iOS versions can be tricky, as Apple users adopt new versions quickly, but some still rely on older devices.
Frequent OS Updates:
Apple regularly updates iOS, which can introduce new features and deprecate existing ones. Developers need to stay current and adapt their apps quickly. Failing and not opting to do so can and may lead towards compatibility issues or the app crashes, impacting the overall user satisfaction and their experience which helps to build a smooth appearance to the users.
Security and Data Privacy Compliance:
Apple places high emphasis on user privacy and app security and safeguarding their thoughts and processes. Apps must comply with requirements like App Tracking Transparency (ATT) data encryption standards and commonly specified parameters. Assuring these compliances and sticked with added extra layers of testing and development work into it. While iOS App Development offers and assists with great rewards, it demands precision, flexibility, and constant adaptation. Companies like Suma Soft, IBM, Cyntexa, and Cignex bring the expertise to navigate these challenges effectively, helping businesses to launch their polished, compliant, and user-friendly iOS apps.
#it services#technology#saas#software#saas development company#saas technology#digital transformation#ios app development#ios
2 notes
·
View notes
Text
Exploring Nulls Brawl APK The Ultimate Private Server for Brawl Stars Enthusiasts
For Brawl Stars players who are looking for a fresh and more customizable gaming experience, Nulls Brawl APK has emerged as a popular choice. Offering a private server for Brawl Stars, this modified version allows players to enjoy the game without the constraints of the official server. From unlimited resources to unlocking every brawler, Nulls Brawl APK brings exciting possibilities to the Brawl Stars universe. Here's a deeper dive into what makes this APK so appealing.
What is Nulls Brawl APK?
Nulls Brawl APK is an unofficial, private server version of the mobile game Brawl Stars created by independent developers. It modifies the original Brawl Stars game to give players more freedom, such as unlimited gems and coins, access to all brawlers and skins, and more. This version is mainly available for Android users and can be downloaded via third-party sources.
Unlike the official version of Brawl Stars, which features a progression system where players unlock characters and upgrades over time, Nulls Brawl APK provides instant access to everything. Players can enjoy the full range of game modes and features without worrying about waiting to unlock items or spend real money on in-game purchases.
Key Features of Nulls Brawl APK
Unlimited Gems and Coins: One of the most exciting features of Nulls Brawl APK is the ability to have unlimited gems and coins. This makes it easy for players to unlock all skins, brawlers, and upgrades instantly.
Access to All Brawlers: Players don't need to grind for months to unlock their favorite brawlers. In Nulls Brawl APK, every brawler is available from the get-go, which is a massive advantage for those who want to test different characters or simply enjoy using them all.
Custom Skins and Features: The private server includes custom skins that aren’t available in the official Brawl Stars game. These skins add a unique flair to the game, allowing players to further personalize their brawler’s look.
No Waiting or Progression Limits: Since Nulls Brawl APK unlocks all content immediately, players don’t have to wait for chests to unlock or worry about in-app purchases to access premium items. Everything is available right from the start.
Smooth and Fast Gameplay: Despite being a third-party server, Nulls Brawl APK offers smooth gameplay, with little to no lag, and ensures a fast-paced Brawl Stars experience without the delay of official server restrictions.
Bug Fixes and Updates: Nulls Brawl APK often receives updates and bug fixes faster than the official game. This can provide an enhanced experience as players can enjoy new features and improvements before they’re released on the main Brawl Stars server.
How to Install Nulls Brawl APK
Installing Nulls Brawl APK on your Android device is straightforward but requires a few extra steps to ensure a safe and successful installation.
Allow Installation from Unknown Sources: Before you download the APK, you’ll need to go to your device settings and enable installations from unknown sources. This option is typically found under Settings > Security or Settings > Apps, depending on your device.
Download the APK: Find a trustworthy source to download the APK file. Be cautious of unreliable sites, as downloading from insecure sources can expose your device to malware.
Install the APK: After the APK file is downloaded, simply tap on the file to begin the installation process. Follow the on-screen instructions to complete the installation.
Open and Play: Once installed, you can open the game from your home screen and enjoy the enhanced Brawl Stars experience.
Is Nulls Brawl APK Safe to Use?
As with any third-party app, there are risks involved when using Nulls Brawl APK. Since the game is not officially supported by Supercell, there are potential concerns about security, such as malware and data privacy risks. Always download the APK from a reputable site to minimize these risks.
Additionally, while playing on a private server is fun and convenient, it can affect your official Brawl Stars account if you decide to return to the main game. It's advisable to use a separate account for Nulls Brawl APK to avoid any potential bans or account issues.
Conclusion
Nulls Brawl APK is a game-changer for Brawl Stars enthusiasts who want a new and improved way to enjoy the game. With features like unlimited resources, access to all brawlers, custom skins, and fast updates, it offers a vastly different experience from the official Brawl Stars game. However, users should always be cautious when downloading and installing APKs from third-party sources and consider using a separate account to avoid conflicts with the official game.
If you're looking for a way to explore Brawl Stars in a completely unrestricted manner, Nulls Brawl APK may be exactly what you need to level up your gaming experience!
2 notes
·
View notes
Note
Also you mentioned a VPN, but are there any free ones? Specifically like a Firefox extension or something like that? I can't pay money for one, and i'm gonna switch to Firefox soon anyways (long story). Also ik I said this before but thx for the kitties :D
I'm not very knowledgeable on PC VPNs but I found this article linking some
What you've got to be aware is that if they're free they're always gonna have limitations.
For your phone I'm only knowledgeable on Android. Opera has a built in limited VPN. It works only on the Opera browser though.
However I've found an app that basically works as a VPN for your whole phone
It's limited in servers and I recommend you keep checking the VPN symbol from time to time as after a while it automatically turns off the VPN I think but it works for all apps that use your location which is really good.
I went looking and found this one that has a bunch more server options
It can have very long ads but that's the price for being free. Using it right now and it works 👍
I've now also tried this third option
At first it may appear like it has more options than the last one but don't be fooled! Most of the servers are premium. It does have better options if you want your location to be the US or Canada but that's mostly it. The Super Unlimited Proxy is better for European server options.
Well that's what I found for free! I hope it helps even if I know it's probable that you have an Apple device instead of Android because that's the US norm. —_—
#ask#Anonymous#VPN#Resources#Also no worries!#Don't be embarrassed by your ask#We all feel down sometimes and it wasn't something bad to vent#I don't feel burdened by your ask. I quite enjoy trying to help people.
52 notes
·
View notes
Text
Apple is among three tech giants being investigated for failing to comply with the European Union’s new competition rules, in another blow to the embattled smartphone maker.
Apple was the primary focus of an EU press conference on Monday morning. But authorities also opened formal investigations into Meta and Alphabet, Google’s parent company. The trio are the first to be subject to formal probes under the EU’s new Digital Markets Act, the bloc’s landmark competition law, which took effect on March 7.
Under the new rules, six of the world’s largest tech companies, known in the EU as “gatekeepers,” were asked to provide evidence that they were not harming competition. “We are not convinced that the solutions by Alphabet, Apple, and Meta respect their obligations for a fairer and more open digital space for European citizens and businesses,” said Thierry Breton, EU industry chief, in a statement on Monday. “Should our investigation conclude that there is lack of full compliance with the DMA, gatekeepers could face heavy fines.” Under the Digital Markets Act, officials can levy fines of up to 10 percent of tech giants’ global revenue or 20 percent for repeat violations.
Following weeks of criticism directed at Apple by developers, the EU’s competition chief Margrethe Vestager said a formal investigation would focus on two elements of the smartphone maker’s business: the limits Apple places on developers trying to link from the App Store to their own websites, and how hard Apple makes it to replace default, native apps like Photos or iCloud with third-party alternatives.
“Gatekeepers have an obligation to enable easy uninstallation of apps and easy change of default settings,” Vestager said in the press conference. “Apple’s compliance model does not seem to meet the objective of this obligation.”
EU officials are also considering another formal investigation into whether Apple’s rules for alternative app stores—allowing users to download apps from places other than the official App Store—comply with the Digital Markets Act rules. Apple is confident its business is compliant, company spokesperson Rob Saunders told WIRED. “Teams across Apple have created a wide range of new developer capabilities, features, and tools to comply with the regulation,” he said in a statement. “At the same time, we’ve introduced protections to help reduce new risks to the privacy, quality, and security of our EU users’ experience.”
Apple has emerged as a focal point for competition officials in both the EU and the US. The EU announcement on Monday follows a lawsuit filed by the US Department of Justice last week that claimed the smartphone maker had established an iPhone monopoly that was suppressing competition and harming consumers.
The lawsuit cited four internal Apple emails that, the DOJ claimed, illustrate how executives knowingly restrict users and developers in unfair ways. In one exchange from 2010, Apple cofounder Steve Jobs and an unnamed Apple executive discussed how a new ad for Amazon’s Kindle gave the impression that it is easy to switch from iPhone to Android. “Not fun to watch,” the executive wrote.
The Apple crackdown also comes amid wider scrutiny of the ways tech giants have managed to maintain dominance. On Monday, the EU announced Alphabet was also subject to a formal investigation into the limits placed on developers selling their apps through the Android app store. In December of last year, a US court ruled that the Google Play Store was a monopoly.
EU officials added that they were concerned by the way Alphabet ranks results in Google Search, according to Breton. “Gatekeepers should not use their power to promote their own services over their rivals and ranking should be based on transparent, fair, and nondiscriminatory terms,” Breton said in Monday’s press conference. “Based on our preliminary assessment, this does not seem to be the case when it comes to how results are presented on Google Search.”
Google plans to defend its approach. “To comply with the Digital Markets Act, we have made significant changes to the way our services operate in Europe,” said Oliver Bethell, the company’s director of EMEA competition, in a statement. “We have engaged with the European Commission, stakeholders and third parties in dozens of events over the past year to receive and respond to feedback, and to balance conflicting needs within the ecosystem.”
Meanwhile, the Meta investigation will focus on the company’s “pay or consent” model, Breton said. In November, Facebook-parent Meta announced that its users could opt out of seeing ads for a fee of $10 a month. After critics suggested users were essentially being asked to pay for privacy, the company offered last week to halve that monthly price to €5.99 ($6.50).
“This has forced millions of users across Europe into a binary choice: Pay or consent,” said Breton in the press conference, noting that if users consent, their data from messaging app Messenger can be used for targeted ads on Instagram. “We have serious doubts that that consent is really free when you are confronted with a binary choice.”
Ad-free subscriptions are a well-established business model, Meta spokesperson Matthew Pollard told WIRED. “We designed Subscription for No Ads to address several overlapping regulatory obligations, including the DMA,” he said.
The Digital Markets Act dictates investigations should be concluded in 12 months. It’s unclear how the deadline will be affected by the European elections, which are due to take place in June.
8 notes
·
View notes
Text
For my American Friends
I feel now is a good time to spread this news. Much like how the internet came together to help share information with the Ukrainians for resisting Russia, I’m here delivering help of a similar nature to those that could be impacted by this latest election in the US. There are ways to communicate relatively securely, outside of Big Brother's social media. I bring this up so that we can minimize the amount of gatherable information that could be used to hurt you, or others you know, in the coming years as changes are made. I'm not going to tell you how or why to use them, I'm just going to provide you with the information.
WhatsApp – While not my personal favorite, since Facebook/Meta is the parent company, WhatsApp is free, globally popular, and widely-used, featuring the ability to lock chats with passwords, disappearing messages, photos and videos that are deleted after being opened, profile photo privacy, the ability to lock the app itself so that only your biometrics can unlock it, encrypted backups, the ability to set custom permissions for who can see you online or when you last used the app, and of course End-to-End Encryption for all conversations EXCEPT those with business accounts. WhatsApp is a good option for those who are not really technically savvy, but still value privacy – if one trusts Facebook/Meta to adequately protect their privacy. It does require a phone number to sign up, however.
Signal - Signal is an end-to-end encrypted messaging software. meaning that the contents of your conversation is secure. The protocol they use (which they created) is seen as the best known protocol for asynchronous messaging by cybersecurity researchers. It's so good that it has been implemented in WhatsApp and in Messenger's secret chats. This app has even been mentioned in the Right-wing author Jack Carr's Political Thriller about a Navy SEAL named James Reece, as being a preferred method of secure communication on the civilian side for operators. (Jack Carr is a former US Navy SEAL.) It's run by a Non-Profit organization called Signal Foundation, and it's mission is to "protect free expression and enable secure global communication through open source privacy technology." It allows secure messaging, voice calls, and video calls. The only downside is that app links to your phone number, so while your conversations and content are secure, who you are talking to is not. Signal is available on Windows, Mac, Andriod, Linus, and iOS.
Session - Session is an end-to-end encrypted messenger that minimises sensitive metadata, designed and built for people who want absolute privacy and freedom from any form of surveillance. Session is an open-source, public-key-based secure messaging application which uses a set of decentralized storage servers and an onion routing protocol to send end-to-end encrypted messages with minimal exposure of user metadata. This means no phone numbers, no metadata for digital footprints, and censorship resistance. It features group chats, the ability to send documents, files, and images securely, and has added voice messages, though these can be spotty. It’s slow, but effective, and be downloaded on Android, F-Droid, iPhone, Mac, Windows, and Linux.
Briar - If you have an Android phone, Briar is another option you have. It features a decentralized network (it’s peer-to-peer encrypted, rather than relying on a central server), meaning messages are synced directly between user devices. It also means that even if the internet is down, it can sync via Bluetooth, Wi-Fi, or even memory cards, meaning information can continue to flow even during a crisis. In the event the internet is functioning, it can sync via the Tor network, protecting users and their relationships from surveillance. Other features: - Screenshots and screen recording are disabled by default - Each user’s contact list is encrypted and stored on her own device. - Briar’s end-to-end encryption prevents keyword filtering, and because of its decentralized design there are no servers to block. - Every user who subscribes to a forum keeps a copy of its content, so there’s no single point where a post can be deleted. - Briar’s forums have no central server to attack, and every subscriber has access to the content even if they’re offline. - Doesn’t require any user data like name and phone number. The downside is that it is text-only and limited to Android Devices, but they do offer Briar Mailbox to deliver messages securely to those who are online at different times. Briar’s goal is “to enable people in any country to create safe spaces where they can debate any topic, plan events, and organize social movements”
Protonmail - A free end-to-end encrypted AND zero-access encryption email service based out of Switzerland, you can safely email with peace of mind that your content is secure. Unlike Google, Outlook, Yahoo, and others, Proton's zero-access encryption means they can't even view the contents of your emails or attachments. As a Swiss-owned company they are not allowed to share information with foreign law enforcement under criminal penalty and they are politically neutral, meaning they won't be pressured by foreign governments. Furthermore, Switzerland has a constitutional right to privacy and strict data protection laws. Unlike companies in other countries, Proton cannot be compelled by foreign or Swiss authorities to engage in bulk surveillance.
Additional Information, from Proton’s Website: Switzerland has strong legal protections for individual rights, and in fact the Swiss Federal Constitution(new window) explicitly establishes a constitutional right to privacy. (In the US, this right is merely implied.) Specifically, Article 13 safeguards privacy in personal or family life and within one’s home, and the Swiss Civil Code(new window) translates this right into statutory law in Article 28.
In the US and EU, authorities can issue gag orders to prevent an individual from knowing they are being investigated or under surveillance. While this type of order also exists in Switzerland, the prosecutors have an obligation to notify the target of surveillance, and the target has an opportunity to appeal in court. In Switzerland, there are no such things as national security letters(new window), and all surveillance requests must go through the courts. Warrantless surveillance, like that practiced in the US where the FBI conducts 3.4 million searches per year(new window) with little oversight, is illegal and not permitted in Switzerland.
Switzerland also benefits from a unique legal provision with Article 271 of the Swiss Criminal Code(new window), which forbids any Swiss company from assisting foreign law enforcement, under threat of criminal penalty. While Switzerland is party to certain international legal assistance agreements, all requests under such agreements must hold up under Swiss law, which has much stricter privacy provisions. All foreign requests are assessed by the Swiss government, which generally does not assist requests from countries with poor rule of law or lack an independent judiciary.
Swiss law has several more unique points. First, it preserves end-to-end encryption, and unlike in the US, UK, or EU, there is no legislation that has been introduced or considered to limit the right to encryption. Second, Swiss law protects no-logs VPN(new window) meaning that Proton VPN does not have logging obligations. While numerous VPNs claim no-logs, these claims generally do not stand up legally because in most jurisdictions, governments can request that the VPN in question starts logging. So the VPN is only no-logs until the government asks. However, in Switzerland, the law does not allow the government to compel Proton VPN to start logging.
We’ve also fought to ensure that Switzerland remains a legal jurisdiction that respects and protects privacy.
Nearly every country in the world has laws governing lawful interception of electronic communications for law enforcement purposes. In Switzerland, these regulations are set out in the Swiss Federal Act on the Surveillance of Post and Telecommunications (SPTA), which was last revised on March 18, 2018. In May 2020, we challenged a decision of the Swiss government over what we believed was an improper attempt to use telecommunications laws to undermine privacy.
In October 2021, The Swiss Federal Administrative Court ultimately agreed with us and ruled that email companies cannot be considered telecommunication providers. This means Proton isn’t required to follow any of the SPTA’s mandatory data retention rules, nor are we bound by a full obligation to identify Proton Mail users. Moreover, as a Swiss company, Proton Mail cannot be compelled to engage in bulk surveillance on behalf of US or Swiss intelligence agencies. (Links can be found at: proton.me/blog/switzerland)
#american politics#kamala harris#transgender#lgbtqia#lgbtq community#antifascist#anti trump#freedom#information#resistance
6 notes
·
View notes
Text
Samsung Galaxy A56: Best Smartphone Performance In 2025

Samsung Galaxy A56
As development news breaks, the Samsung Galaxy A56 is gaining popularity in the smartphone industry. Designed to succeed the Galaxy A series, this gadget is expected to outperform even Samsung’s top models. Mid-range smartphones will be transformed by the Galaxy A56’s speed, efficiency, and user experience. It is the most anticipated specifications and why it’s worth the wait.
Galaxy A56 Features
New mid-range smartphone standard
The Galaxy A56 continues Samsung’s legacy of quality features at an accessible price. Samsung looks to be pushing the limits even further, providing the A56 with high-performance specs that might compete with flagship handsets.
Strong Processor Upgrade
Due to its speculated Exynos 1480 processor, the A56 outperforms its predecessor, the Exynos 1280 in the A54. The new Exynos 1480 improves multitasking, processing performance, and power efficiency. It is octa-core CPU handles intense operations smoothly, so you can stream, game, or manage many apps.
Samsung may possibly provide a Snapdragon 7 Gen 2 model for adaptable usage in various areas. With its high performance and power economy, this processor makes the Galaxy A56 a powerful mid-range competitor.
Memory and storage upgrades
Samsung will upgrade RAM and storage with the A56. There are significant reports that the basic model will have 6GB of RAM, although an 8GB edition may be available for intense workloads. Users may choose 128GB or 256GB internal storage, extendable via microSD up to 1TB. Users need flexibility, and this gives programs, images, movies, and files plenty of space.
Huge Speeds
Today’s digital world requires 5G, which the Galaxy A56 provides. The A56 is fantastic for streaming, gaming, and video conferencing due to dual-mode 5G download and upload rates. The A56 will keep people connected at fast speeds worldwide as 5G spreads.
Beautiful AMOLED Display
The Galaxy A56‘s 6.5-inch Full HD+ Super AMOLED display with deep blacks, bright colors, and superb contrast. The A56 will maintain Samsung’s display superiority with its immersive display. A 120Hz refresh rate assures clean images and minimal motion blur, giving the screen a luxury feel normally seen in higher-end devices.
Amazing Camera Setup
Smartphone cameras matter, and the Galaxy A56 may include quad cameras. Speculation implies a 50MP primary sensor, 12MP ultra-wide, 5MP macro, and 5MP depth sensor. This configuration enables for wide-angle vistas and close-ups.
The 50MP main camera offers great low-light performance, quicker focusing, and sharper images. AI advancements provide pro-level photography without a flagship smartphone. Quality selfies and video calls with 32MP camera.
Samsung Galaxy A56 may utilize 5,000mAh battery
Smartphone customers appreciate battery life. Power-efficient Exynos or Snapdragon chipsets and large batteries should last all day for gaming and streaming. The A56 is include 25W rapid charging for quick phone usage. As usual for Samsung’s A-series, this mid-range device won’t include wireless charging.
Android/One UI Integration
As predicted, the Samsung Galaxy A56 will come with Android 14 and One UI 6. With capabilities to boost productivity and customization, Samsung’s One UI is seamless and user-friendly. One-handed mode, Edge Panels, and extensive privacy settings make the A56 a versatile tablet for casual and experienced users.
Samsung Knox, the company’s unique security technology, will provide improved protection to secure your data. With regular software updates and security fixes, the A56 will endure for years.
Smooth Design and Quality
Samsung designs are known for their quality, so the Galaxy A56 should look great. Corning Gorilla Glass 5 front and back makes the phone look fantastic and endure longer. This thin device with curved edges is easy to grasp and will come in numerous colors for design and function.
Keeping its IP67 dust- and water-resistant designation makes the A56 more durable for daily usage in varied conditions.
Samsung Galaxy A56 Price
Final Thoughts: Mid-Range Powerhouse Galaxy A56
The A56 is turning out to be one of the most powerful and adaptable mid-range smartphones with its astonishing variety of high-performance capabilities. Its powerful Exynos 1480 CPU, 120Hz AMOLED display, quad-camera system, 5G connection, and big battery make the Galaxy A56 the right blend of performance, features, and cost.
The A56 is a must-see for anybody searching for flagship-like capabilities at a lower price. Samsung is pushing the limits of mid-range smartphones.
Galaxy A56 Release Date
No Samsung Galaxy A56 release date has been disclosed. Early in the year, Samsung releases its mid-range A series smartphones. Based on prior trends, the Galaxy A56 should be introduced in early 2025.
Read more on Govindhtech.com
#SamsungGalaxy#GalaxyA56#smartphone#GalaxAseries#microSD#AMOLEDDisplay#Android14#5Gconnection#AI#GorillaGlass5#news#technews#technology#technologynews#technologytrends#govindhtech
2 notes
·
View notes
Text
Instant Messenger's Journey in Indonesia: From 2000 to 2024
Since 2000, digital communication in Indonesia has undergone a major transformation. One innovation that has brought significant change is the emergence of the Instant Messenger (IM) service. This article will trace the development of IM technology from its inception to the current conditions in 2024, as well as its impact on the way Indonesian people communicate.
Early 2000s Era: Yahoo! Messenger and mIRC
At the beginning of the millennium, the first IM service that was popular in Indonesia was Yahoo! Messenger and mIRC. Yahoo! Messenger is a favorite because of its ease of use, various features such as emoticons and games, and the ability to send instant messages and make voice calls. On the other hand, mIRC, a text-based chat program, is a gathering place for those who like theme-based chats on various channels.
The 2010s: The Emergence of New Platforms
Entering the 2010s, IM technology became increasingly advanced with the presence of mobile applications such as BlackBerry Messenger (BBM). BBM has become very popular in Indonesia, especially among young people and professionals. With its unique PIN feature, BBM is one of the main ways to communicate. Apart from BBM, WhatsApp is starting to gain popularity with its simple interface and ability to work on multiple platforms, including Android and iOS.
Apart from that, Line remains popular with its special features, such as cute and creative stickers, as well as the Line Today feature which provides news and information.
2020s: WhatsApp Domination and the Emergence of Alternative Platforms
Entering the 2020s, WhatsApp has become the most dominant IM application in Indonesia. Ease of use, security with end-to-end encryption, and voice and video calling features make it a top choice. However, several emerging privacy issues have caused some users to look for alternatives such as Telegram and Signal, which offer higher security.
Apart from that, Line remains popular with its special features, such as cute and creative stickers, as well as the Line Today feature which provides news and information.
Year 2024: Trends and the Future
Until August 2024, communication trends in Indonesia show a shift towards applications that offer more than just text messages. Features such as video calls, voice messages, and integration with social media are increasingly important. WhatsApp continues to dominate, but other apps such as Telegram, Signal and Line maintain a strong user base.
Increasing internet connectivity and smartphone penetration at all levels of Indonesian society also contribute to the increasing use of IM applications. With technologies such as 5G starting to spread, the speed and quality of communications is increasing, enabling a better user experience.
Conclusion
From Yahoo! Messenger to WhatsApp, the development of Instant Messenger in Indonesia reflects the evolution of communication technology and user preferences. Each decade brings new innovations that change the way we interact with each other. Seeing these developments, we can be optimistic that the future of digital communications in Indonesia will be even more exciting and inclusive, providing more ways for us to connect.
By looking at this long journey, we can appreciate how technology has brought us closer to each other, even in far away places. Hopefully this article provides a clear picture of the development of Instant Messenger in Indonesia from 2000 to 2024.
#Technology#Tech#Instagram#WhatsApp#Line#BBM Messanger#BBM#Yahoo! Messenger#Telegram#BlackBerry Messenger#mIRC#Yahoo#Instant Messenger#indonesia
2 notes
·
View notes