#Network Security Protocol
Explore tagged Tumblr posts
Text
Queer Adult SFF Books Bracket: Round 1


Book summaries and submitted endorsements below:
The Murderbot Diaries series (All Systems Red, Artificial Condition, Rogue Protocol, Exit Strategy, Network Effect, Fugitive Telemetry, System Collapse, and other stories) by Martha Wells
Endorsement from submitter: "Asexual and agender main character. In later books side characters are revealed to be in poly relationship."
"As a heartless killing machine, I was a complete failure."
In a corporate-dominated space-faring future, planetary missions must be approved and supplied by the Company. For their own safety, exploratory teams are accompanied by Company-supplied security androids. But in a society where contracts are awarded to the lowest bidder, safety isn’t a primary concern.
On a distant planet, a team of scientists is conducting surface tests, shadowed by their Company-supplied ‘droid--a self-aware SecUnit that has hacked its own governor module and refers to itself (though never out loud) as “Murderbot.” Scornful of humans, Murderbot wants is to be left alone long enough to figure out who it is, but when a neighboring mission goes dark, it's up to the scientists and Murderbot to get to the truth.
Science fiction, novella, series, adult
Hunger Pangs series (True Love Bites) by Joy Demorra
In a world of dwindling hope, love has never mattered more...
Captain Nathan J. Northland had no idea what to expect when he returned home to Lorehaven injured from war, but it certainly wasn't to find himself posted on an island full of vampires. An island whose local vampire dandy lord causes Nathan to feel strange things he'd never felt before. Particularly about fangs.
When Vlad Blutstein agreed to hire Nathan as Captain of the Eyrie Guard, he hadn't been sure what to expect either, but it certainly hadn't been to fall in love with a disabled werewolf. However Vlad has fallen and fallen hard, and that's the problem.
Torn by their allegiances--to family, to duty, and the age-old enmity between vampires and werewolves--the pair find themselves in a difficult situation: to love where the heart wants or to follow where expectation demands.
The situation is complicated further when a mysterious and beguiling figure known only as Lady Ursula crashes into their lives, bringing with her dark omens of death, doom, and destruction in her wake.
And a desperate plea for help neither of them can ignore.
Thrown together in uncertain times and struggling to find their place amidst the rising human empire, the unlikely trio must decide how to face the coming darkness: united as one or divided and alone. One thing is for certain, none of them will ever be the same.
Fantasy, romance, paranormal, series, adult
#polls#queer adult sff#murderbot diaries#the murderbot diaries#martha wells#true love bites#hunger pangs#joy demorra#murderbot#hunger pangs: true love bites#all systems red#phangs#artificial condition#nathan j northland#rogue protocol#vlad blustein#exit strategy#lady ursula#network effect#fugitive telemetry#system collapse#secunit#security unit#books#booklr#lgbtqia#tumblr polls#bookblr#book#lgbt books
1K notes
·
View notes
Text
What are the Different Security Protocols?
#General#Technology#Security Protocols#WEP#WiFi#WiFi Networks#Wireless Security Protocols#WPA#WPA2#WPA3
2 notes
·
View notes
Text
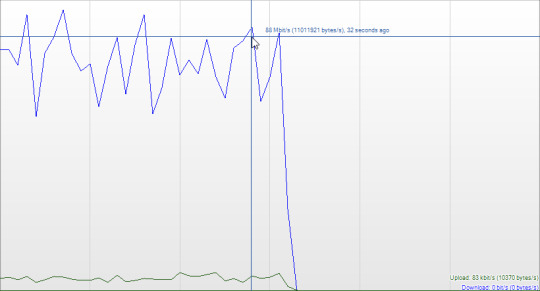
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
How Disrespect in Business—Like Ignoring Emails and Turning Down Networking—Can Lead to Cyber Attacks
Let’s get something straight right now: your crappy communication habits aren’t just annoying—they’re dangerous. That ignored email chain? It might be the reason your company gets ransomwared next month. That networking event you blew off because you were “too busy”? Could’ve been where you learned about the security vulnerability currently festering in your system. Disrespect in business isn’t…
#business communication#company culture#cyber attacks#cybersecurity#data breaches#digital security#email response#information security#networking importance#professional respect#ransomware prevention#security protocols#security vulnerabilities#workplace communication
0 notes
Text

Security Vulnerabilities in CAN, CANopen, and J1939 Networks: Risks and Mitigation Strategies
Explore key security vulnerabilities in CAN, CANopen, and J1939 networks. Learn the risks and discover effective mitigation strategies to protect your industrial and automotive systems.
#can bus#canopen#j1939#security#cybersecurity#network security#can injection attack#can protocol hacking
0 notes
Text
#🔐 Robust Security Measures: Cisco firewalls provide advanced security protocols#enabling organizations to monitor and control incoming and outgoing network traffic efficiently! 💪✨#CiscoFirewalls#NetworkSecurity#Cybersecurity#📈 Scalability & Flexibility: With solutions like the ASA and Firepower series#Cisco firewalls can adapt to various network sizes and requirements#ensuring your business remains secure as it grows! 🚀🔄#Scalability#CiscoASA#Firepower#🛡 Stateful Inspection Technology: Utilizing stateful firewalls#Cisco effectively tracks active connections and makes real-time decisions about which packets to allow or block#enhancing overall network performance! ⚙📊#StatefulFirewall#NetworkPerformance#Cisco
1 note
·
View note
Text
Wireshark
Wireshark is a free and open-source packet sniffer that examines your network to identify performance and security problems. This Windows tool can analyze network traffic across Wireless, Ethernet, VLAN, and Bluetooth. As a standard protocol analyzer, it provides these features at no cost to both businesses and individuals. Additionally, these capabilities are not restricted to Windows, as…
#Deep Packet Inspection#Ethernet Analysis#Free Software#Network Analysis#Network Security#Open Source#Packet Capture#Packet Sniffer#Protocol Analyzer#Traffic Analysis#VoIP Analysis#WiFi Analysis
0 notes
Text
Queer Adult SFF Books Bracket: Round 3


Book summaries and submitted endorsements below:
The Murderbot Diaries series (All Systems Red, Artificial Condition, Rogue Protocol, Exit Strategy, Network Effect, Fugitive Telemetry, System Collapse, and other stories) by Martha Wells
Endorsement from submitter: "Asexual and agender main character. In later books side characters are revealed to be in poly relationship."
"As a heartless killing machine, I was a complete failure."
In a corporate-dominated space-faring future, planetary missions must be approved and supplied by the Company. For their own safety, exploratory teams are accompanied by Company-supplied security androids. But in a society where contracts are awarded to the lowest bidder, safety isn’t a primary concern.
On a distant planet, a team of scientists is conducting surface tests, shadowed by their Company-supplied ‘droid--a self-aware SecUnit that has hacked its own governor module and refers to itself (though never out loud) as “Murderbot.” Scornful of humans, Murderbot wants is to be left alone long enough to figure out who it is, but when a neighboring mission goes dark, it's up to the scientists and Murderbot to get to the truth.
Science fiction, novella, series, adult
The Left Hand of Darkness by Ursula K. Le Guin
A groundbreaking work of science fiction, The Left Hand of Darkness tells the story of a lone human emissary to Winter, an alien world whose inhabitants spend most of their time without a gender. His goal is to facilitate Winter's inclusion in a growing intergalactic civilization. But to do so he must bridge the gulf between his own views and those of the completely dissimilar culture that he encounters.
Embracing the aspects of psychology, society, and human emotion on an alien world, The Left Hand of Darkness stands as a landmark achievement in the annals of intellectual science fiction.
Science fiction, classics, speculative fiction, anthropological science fiction, distant future, adult
#polls#queer adult sff#murderbot diaries#the murderbot diaries#martha wells#the left hand of darkness#ursula k le guin#ursula k. le guin#murderbot#ursula le guin#all systems red#artificial condition#tlhod#rogue protocol#lhod#therem harth rem ir estraven#exit strategy#estraven#network effect#genly ai#fugitive telemetry#system collapse#secunit#security unit#books#booklr#lgbtqia#tumblr polls#bookblr
283 notes
·
View notes
Text
What is Bitcoin Savings?
#Bit Savings is a cryptocurrency savings protocol based on the Binance EcoChain network#aiming to provide users with safe and efficient savings solutions. The protocol is called a “crypto banking smart contract on the blockchai#but with more decentralization#security and transparency.
0 notes
Text
Features of the Most Reliable VPN Services
In today’s interconnected world, where privacy concerns and data breaches are rampant, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, not all VPN services are created equal. While some may offer flashy features or enticing deals, the true mark of reliability lies in a set of core features that distinguish the best from the rest. In…

View On WordPress
#A#Cross-Platform Compatibility#Customer Support#Customer support availability#Data encryption#Data encryption standards#Data Protection#Data protection measures#Encryption protocol security#Geo-restriction#Geo-restriction bypass#Geo-restriction circumvention#Internet safety#Internet safety assurance#Kill switch#Kill switch feature#Leak protection#Leak protection mechanism#Network reliability#Network reliability assessment#No-logs guarantee#No-Logs Policy#Online Privacy#Online privacy protection#Privacy policy assurance#Privacy protection#Secure Connection#Secure connection establishment#Security encryption#Server network
0 notes
Text
Top 10 Open Source NAS software in 2023
Top 10 Open Source NAS software in 2023 #homelab #selfhosted #opensourceNASsolutions #freeNASsoftware #networkattachedstorage #NASserverhardware #datastoragesolutions #selfhostedNASbenefits #personalcloudserver #filesharingprotocols
There are many freely available open-source NAS solutions you can download for free. An open-source NAS server offers an excellent way to manage and protect your data. Let’s dive deeper into the top free NAS software solutions available in 2023. Network attached storage nas for home Table of contentsIntroduction to Open Source NAS SolutionsTrueNAS Scale and TrueNAS Core: Great Open Source…

View On WordPress
#data backup and recovery#data integrity and security#data storage solutions#file sharing protocols#free NAS software#NAS server hardware#network attached storage#open source NAS solutions#personal cloud server#self-hosted NAS benefits
0 notes
Note
You may have posted about this before, but im very curious about you saying "email was a mistake" because it's such a cemented part of online communication. Is it the technology?
Email became infrastructural in a way that it was never intended to be and wasn't designed for.
There is too much momentum toward email being the primary means of business communication that unless there is a massive technology shift we're unlikely to see wide adoption of an alternative and email takes up so much space in the IT space that it's hard to say what the alternative would be.
Much of what used to be email now happens in company chat apps, which I think is an improvement in many ways, but you chat with your coworkers in a way that you're unlikely to chat with a client or send a quote to a prospect.
A huge amount of effort goes into making email better, and making email systems talk to each other, and making email secure because it is so ubiquitous that you can't realistically ask people not to use it.
But it's fucking terrible and we're asking too much of a set of protocols that was supposed to send small, not-very-private, communications between academics.
Why can't you send big files via email? Because that's not what email is for.
Why is it a pain in the ass to send encrypted emails? Because that's not what email is for.
Why aren't your emails portable, and easy to move from one service to another? Because that's not what email is for.
Why are emails so easy to spoof? Because they were never meant to be used the way we use them so there was no reason to safeguard against that fifty years ago
It's like how social security cards were never meant to be used as one of your major super serious government IDs where all of your activity through all of your life is tracked, because if they knew they needed a system for that they probably would have built a better one in the first place.
Nobody who sat down and developed email looked more than half a century into the future and went "so people are going to be using this system to create identities to access banking and medical records and grocery shopping and school records so we'd better make sure that it's robust enough to handle all of that" because instead they were thinking "Neat! I can send a digital message to someone on a different computer network than the one that I am literally in the same building as."
We think of email as, like, a piece of certified mail that is hand delivered in tamperproof packaging to only the intended recipient who signs for it with their thumbprint and a retina scan when it is, instead, basically a postcard.
It would be absurd to try to do the things people do with email with postcards, and it's *nearly* as absurd to try to do them via email.
1K notes
·
View notes
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
Subnet Sunday: Authentication - Proving Your Identity on the Network
Welcome to Subnet Sunday, where we unravel the mysteries of authentication in a fun and humorous way. In this edition, we’ll take you on a journey through the colorful world of proving your identity on the network. Using relatable analogies, playful emojis, and a touch of wit, we’ll demystify authentication and make it accessible for novice readers. So, get ready to don your digital passport and…

View On WordPress
#access control#authentication#authentication methods#authentication protocols#best practices for authentication#biometric authentication#multi-factor authentication#network dance floor#network security#password security#proving identity#two-factor authentication
0 notes
Text
China hacked Verizon, AT&T and Lumen using the FBI’s backdoor

On OCTOBER 23 at 7PM, I'll be in DECATUR, presenting my novel THE BEZZLE at EAGLE EYE BOOKS.

State-affiliated Chinese hackers penetrated AT&T, Verizon, Lumen and others; they entered their networks and spent months intercepting US traffic – from individuals, firms, government officials, etc – and they did it all without having to exploit any code vulnerabilities. Instead, they used the back door that the FBI requires every carrier to furnish:
https://www.wsj.com/tech/cybersecurity/u-s-wiretap-systems-targeted-in-china-linked-hack-327fc63b?st=C5ywbp&reflink=desktopwebshare_permalink
In 1994, Bill Clinton signed CALEA into law. The Communications Assistance for Law Enforcement Act requires every US telecommunications network to be designed around facilitating access to law-enforcement wiretaps. Prior to CALEA, telecoms operators were often at pains to design their networks to resist infiltration and interception. Even if a telco didn't go that far, they were at the very least indifferent to the needs of law enforcement, and attuned instead to building efficient, robust networks.
Predictably, CALEA met stiff opposition from powerful telecoms companies as it worked its way through Congress, but the Clinton administration bought them off with hundreds of millions of dollars in subsidies to acquire wiretap-facilitation technologies. Immediately, a new industry sprang into being; companies that promised to help the carriers hack themselves, punching back doors into their networks. The pioneers of this dirty business were overwhelmingly founded by ex-Israeli signals intelligence personnel, though they often poached senior American military and intelligence officials to serve as the face of their operations and liase with their former colleagues in law enforcement and intelligence.
Telcos weren't the only opponents of CALEA, of course. Security experts – those who weren't hoping to cash in on government pork, anyways – warned that there was no way to make a back door that was only useful to the "good guys" but would keep the "bad guys" out.
These experts were – then as now – dismissed as neurotic worriers who simultaneously failed to understand the need to facilitate mass surveillance in order to keep the nation safe, and who lacked appropriate faith in American ingenuity. If we can put a man on the moon, surely we can build a security system that selectively fails when a cop needs it to, but stands up to every crook, bully, corporate snoop and foreign government. In other words: "We have faith in you! NERD HARDER!"
NERD HARDER! has been the answer ever since CALEA – and related Clinton-era initiatives, like the failed Clipper Chip program, which would have put a spy chip in every computer, and, eventually, every phone and gadget:
https://en.wikipedia.org/wiki/Clipper_chip
America may have invented NERD HARDER! but plenty of other countries have taken up the cause. The all-time champion is former Australian Prime Minister Malcolm Turnbull, who, when informed that the laws of mathematics dictate that it is impossible to make an encryption scheme that only protects good secrets and not bad ones, replied, "The laws of mathematics are very commendable, but the only law that applies in Australia is the law of Australia":
https://www.zdnet.com/article/the-laws-of-australia-will-trump-the-laws-of-mathematics-turnbull/
CALEA forced a redesign of the foundational, physical layer of the internet. Thankfully, encryption at the protocol layer – in the programs we use – partially counters this deliberately introduced brittleness in the security of all our communications. CALEA can be used to intercept your communications, but mostly what an attacker gets is "metadata" ("so-and-so sent a message of X bytes to such and such") because the data is scrambled and they can't unscramble it, because cryptography actually works, unlike back doors. Of course, that's why governments in the EU, the US, the UK and all over the world are still trying to ban working encryption, insisting that the back doors they'll install will only let the good guys in:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
Any back door can be exploited by your adversaries. The Chinese sponsored hacking group know as Salt Typhoon intercepted the communications of hundreds of millions of American residents, businesses, and institutions. From that position, they could do NSA-style metadata-analysis, malware injection, and interception of unencrypted traffic. And they didn't have to hack anything, because the US government insists that all networking gear ship pre-hacked so that cops can get into it.
This isn't even the first time that CALEA back doors have been exploited by a hostile foreign power as a matter of geopolitical skullduggery. In 2004-2005, Greece's telecommunications were under mass surveillance by US spy agencies who wiretapped Greek officials, all the way up to the Prime Minister, in order to mess with the Greek Olympic bid:
https://en.wikipedia.org/wiki/Greek_wiretapping_case_2004%E2%80%9305
This is a wild story in so many ways. For one thing, CALEA isn't law in Greece! You can totally sell working, secure networking gear in Greece, and in many other countries around the world where they have not passed a stupid CALEA-style law. However the US telecoms market is so fucking huge that all the manufacturers build CALEA back doors into their gear, no matter where it's destined for. So the US has effectively exported this deliberate insecurity to the whole planet – and used it to screw around with Olympic bids, the most penny-ante bullshit imaginable.
Now Chinese-sponsored hackers with cool names like "Salt Typhoon" are traipsing around inside US telecoms infrastructure, using the back doors the FBI insisted would be safe.

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/10/07/foreseeable-outcomes/#calea

Image: Kris Duda, modified https://www.flickr.com/photos/ahorcado/5433669707/
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#calea#lawful interception#backdoors#keys under doormats#cold war 2.0#foreseeable outcomes#jerry berman#greece#olympics#snowden
400 notes
·
View notes
Text
Soo things you need t know before you read my new fic
A/N: This is a character sheet for my next fic that will be posted soon! Make sure to go through it for it (the fic) to make sense.
Edit: The FIC IS OUTTT!! Click here Part 1, Part 2 , Part 3 , Part 4, Epilogue
The Han Crime Family
A multigenerational, ultra-wealthy Korean mafia family running both high-society businesses and a cold, efficient criminal empire from Seoul. Everyone in this family plays a role
1. Han Byung-chul (한병철) – The Grandfather, Founding Boss
Age: 76
Built the family from nothing—started in Busan running docks, expanded to Seoul.
Traditional, ruthless, and respected like a godfather.
Lives in a fortified hanok estate in Gyeonggi-do.
Keeps the family in line through fear and legacy.
“Blood can’t be washed away. It gets passed down.”
2. Shim Soon-ja (심순자) – The Grandmother, Quiet Power
Age: 74
Never raised her voice, but made men disappear with a phone call.
Keeps a network of loyal housekeepers, drivers, and retired spies.
Trusted more than most of the younger generation.
Still pulls strings behind the curtain.
“People assume kindness is weakness. I encourage that.”
3. Han Tae-joon (한태준) – The Father, Current Boss
Age: 48
Cold, methodical, efficient. Took over at 38 after
Runs the family like a CEO, not a thug. Clean hands, dirt everywhere else.
shows affection to his wife and [Y/N], but watches everything.
“This ist a family. Not an organization with the same last name.”
4. Choi Eun-mi (최은미) – The Mother, Political Fixer
Age: 45
Ex-lawyer and daughter of a powerful politician. Handles bribes, scandals, and government ties.
More dangerous socially than anyone physically.
Keeps her kids close
“There’s nothing more useful than a grateful politician.”
The Children:
5. Han Jun-seo (한준서) – Eldest Son, The Reluctant Successor
Age: 26
Quiet, stoic, trained for leadership since birth.
Ivy League grad in business,
Keeps his emotions buried deep.
Has a scar from the top of his right eyebrow down till the upper lip
Due to his scar was called “ugly” and wears a mask but is actually very hot and is muscular.
6. Han So-min (한소민) – Younger Daughter, The Mastermind
Age: 23
Brilliant strategist. Specializes in tech crimes, psychological manipulation, and laundering.
Closer to her mother than anyone else.
“If they think I’m just the quiet one, good.”
7. Han Ji-yoon (한지윤) – Twin Daughter, The Firestarter
Age: 18
Reckless, bold, charming. Thinks rules are meant to be bent until they break.
Handles nightclub fronts and courier operations.
Wild card energy—Tae-joon fears she’ll get herself or someone else killed.
“I was born into chaos. I’m just playing the part.”
8. Han Ji-ho (한지호) – Twin Son, The Watcher
Age: 18
Quiet, calculating, always observing. Genius-level hacker and surveillance expert.
Speaks only when necessary. Possibly autistic, but never diagnosed.
Has dirt on everyone in the family, including his parents.
“I don’t fight. I expose.”
NEXT (The Spirits)
Yoon Ji-hwan (윤지환) – The Watchful Butler
Role (in life): Head Butler
Age at Death: 67
Specialty: Observation, estate history, subtle manipulation
Personality: Calm, cunning, fatherly
Ghost Form: Always in a crisp three-piece suit, gloves on, spectacles perched low
Quirk (in death): Can move objects like books and pens, often “tidies” rooms around [Y/N]
Quote: “Control is not about shouting. It’s about being the last voice in the room.”
Choi Mi-kyung (최미경) – The Silent Knife
Role (in life): Head Maid
Age at Death: 61
Specialty: Etiquette, internal politics, social warfare
Personality: Sharp, strict, maternal in a cold way
Ghost Form: Traditional hanbok with spotless apron, hair in a tight bun, eyes like razors
Quirk (in death): Can whisper directly into [Y/N]’s ear during formal situations
Quote: “You don’t need to be loud to be heard. You just need to be correct.”
Jung Tae-won (정태원) – The Iron Bodyguard
Role (in life): Head of Security
Age at Death: 54
Specialty: Close-quarters combat, protection protocol, intimidation
Personality: Blunt, loyal, battle-hardened
Ghost Form: Stands tall in black combat gear, faint scar over his jaw
Quirk (in death): Temporarily possesses [Y/N] to fight when she’s in danger
Quote: “Stand like you own the ground. Even when you bleed on it.”
Seo Min-jae (서민재) – The Ghost Blade
Role (in life): Head Assassin
Age at Death: Unknown (records erased)
Specialty: Silent kills, stealth, enemy profiling
Personality: Cold, cynical, loyal only to those who earn it
Ghost Form: Shadowy silhouette with crimson edge to his coat, never fully visible
Quirk (in death): Can possess [Y/N] in moments of violent danger, and uses mirrors to appear
Quote: “Mercy is a privilege. And I’m not in the business of charity.”
Kang Dae-shik (강대식) – The Chef of Memory
Role (in life): Head Cook
Age at Death: 72
Specialty: Traditional Korean cuisine, emotional imprint cooking
Personality: Warm, boisterous, nostalgic
Ghost Form: Apron over old hanbok, always wiping hands on a towel
Quirk (in death): Can possess [Y/N] to cook forgotten family recipes perfectly
Quote: “You can’t rebuild trust with words. But a bowl of soup? That’s a start.”
Next (The Servents)
Baek Woo-jin (백우진) – The Current Butler
Trained by: Yoon Ji-hwan
Age: 38
Specialty: Estate operations, diplomacy, damage control
Personality: Polished, discreet, dry-witted
Appearance: Always in tailored suits, silver-rimmed glasses, never flustered
Skills: Multi-lingual, masters-level etiquette, and blackmail collection
Relationship to [Y/N]: Treats her like a sovereign; makes sure she never lifts a finger unnecessarily
Quote: “If I do my job right, no one remembers I was ever there.”
Choi Mi-kyung (최미경) – The Current Head Maid
(Note: same name as the former head maid; a chosen namesake and spiritual heir)
Trained by: Choi Mi-kyung (Spirit)
Age: 30
Specialty: House protocol, staff loyalty, covert operations through domestic channels
Personality: Stern but soft-spoken, impeccably graceful
Appearance: Neat bun, pressed uniform, steady eyes
Skills: Internal intel gathering, poison detection, household espionage
Relationship to [Y/N]: Deeply respectful—sees her as the fulfillment of the legacy she was trained to support
Quote: “Clean homes, quiet halls, and no threats behind the curtains. That’s my job.”
Lee Hyun-woo (이현우) – The Current Head Bodyguard
Trained by: Jung Tae-won
Age: 35
Specialty: Close protection, strategic defense layouts, counter-surveillance
Personality: Stoic, commanding, lives by protocol
Appearance: Broad build, close-cropped hair, tactical calm
Skills: Krav Maga, long-range sniping, pressure-point immobilization
Relationship to [Y/N]: Protective in silence—often stationed outside her door even when not scheduled
Quote: “If someone makes it to her, it means I’ve already failed.”
Nam Ki-ha (남기하) – The Current Head Assassin
Trained by: Seo Min-jae
Age: 33
Specialty: Elimination, infiltration, trace-less disappearance
Personality: Ice-cold, dry-humored, loyal only to the Han bloodline
Appearance: Always in black, with a single ring he turns before each kill
Skills: Disguise, poisons, nerve strikes, terrain-based combat
Relationship to [Y/N]: Intensely respectful—calls her “my queen” in private briefings
Quote: “Everyone bleeds. The difference is who gets to stand after.”
Park Seo-jun (박서준) – The Current Head Cook
Trained by: Kang Dae-shik
Age: 42
Specialty: Heritage cuisine, performance cooking, emotional resonance through food
Personality: Warm, chatty, philosophical
Appearance: Rolled-up sleeves, apron dusted with flour, tattoos of peppers and fish bones
Skills: Psychological profiling through taste, speed prep under pressure, brewing comfort in silence
Relationship to [Y/N]: Treats her like a beloved daughter; often feeds her even if she says she isn’t hungry
Quote: “You can lie with words, but not with your appetite.”
A/N: Its confusing when you read it without this so i decided to post this just for clarification. The first Par will be posted soon
Taglist: @kittzu, @trashlanternfish360, @ottjhe, @moonieper, @feral-childs-word, @tinybrie,@xomarryamox, @fawnqueenbrowsing, @wpdarlingpan, @leeiasure, @xzmickeyzxkey, @enchantingarcadecreation
Old Taglist: @trashlanternfish360, @nixxiev, @eclipse-msoul, @plsfckmedxddy, @viilan, @rattyrattyratty, @texas-fox, @1abi, @niamcarlin,@tomoyaki, @silken-moons.
#𝔖𝔲𝔦𝔯𝔢𝔫 𝔚𝔯𝔦𝔱𝔢𝔰#batman#x reader#neglected reader#batfam#fanfic#batfamily#batkids#yandere batfam#batfam x neglected reader#yandere batman#yandere#soft yandere#yandere male#male yandere#yandere x darling#original character#character sheet
176 notes
·
View notes