#get email toolkit
Explore tagged Tumblr posts
Text

Welcome back, coding enthusiasts! Today we'll talk about Git & Github , the must-know duo for any modern developer. Whether you're just starting out or need a refresher, this guide will walk you through everything from setup to intermediate-level use. Let’s jump in!
What is Git?
Git is a version control system. It helps you as a developer:
Track changes in your codebase, so if anything breaks, you can go back to a previous version. (Trust me, this happens more often than you’d think!)
Collaborate with others : whether you're working on a team project or contributing to an open-source repo, Git helps manage multiple versions of a project.
In short, Git allows you to work smarter, not harder. Developers who aren't familiar with the basics of Git? Let’s just say they’re missing a key tool in their toolkit.
What is Github ?
GitHub is a web-based platform that uses Git for version control and collaboration. It provides an interface to manage your repositories, track bugs, request new features, and much more. Think of it as a place where your Git repositories live, and where real teamwork happens. You can collaborate, share your code, and contribute to other projects, all while keeping everything well-organized.
Git & Github : not the same thing !
Git is the tool you use to create repositories and manage code on your local machine while GitHub is the platform where you host those repositories and collaborate with others. You can also host Git repositories on other platforms like GitLab and BitBucket, but GitHub is the most popular.
Installing Git (Windows, Linux, and macOS Users)
You can go ahead and download Git for your platform from (git-scm.com)
Using Git
You can use Git either through the command line (Terminal) or through a GUI. However, as a developer, it’s highly recommended to learn the terminal approach. Why? Because it’s more efficient, and understanding the commands will give you a better grasp of how Git works under the hood.
GitWorkflow
Git operates in several key areas:
Working directory (on your local machine)
Staging area (where changes are prepared to be committed)
Local repository (stored in the hidden .git directory in your project)
Remote repository (the version of the project stored on GitHub or other hosting platforms)
Let’s look at the basic commands that move code between these areas:
git init: Initializes a Git repository in your project directory, creating the .git folder.
git add: Adds your files to the staging area, where they’re prepared for committing.
git commit: Commits your staged files to your local repository.
git log: Shows the history of commits.
git push: Pushes your changes to the remote repository (like GitHub).
git pull: Pulls changes from the remote repository into your working directory.
git clone: Clones a remote repository to your local machine, maintaining the connection to the remote repo.
Branching and merging
When working in a team, it’s important to never mess up the main branch (often called master or main). This is the core of your project, and it's essential to keep it stable.
To do this, we branch out for new features or bug fixes. This way, you can make changes without affecting the main project until you’re ready to merge. Only merge your work back into the main branch once you're confident that it’s ready to go.
Getting Started: From Installation to Intermediate
Now, let’s go step-by-step through the process of using Git and GitHub from installation to pushing your first project.
Configuring Git
After installing Git, you’ll need to tell Git your name and email. This helps Git keep track of who made each change. To do this, run:

Master vs. Main Branch
By default, Git used to name the default branch master, but GitHub switched it to main for inclusivity reasons. To avoid confusion, check your default branch:

Pushing Changes to GitHub
Let’s go through an example of pushing your changes to GitHub.
First, initialize Git in your project directory:

Then to get the ‘untracked files’ , the files that we haven’t added yet to our staging area , we run the command

Now that you’ve guessed it we’re gonna run the git add command , you can add your files individually by running git add name or all at once like I did here

And finally it's time to commit our file to the local repository

Now, create a new repository on GitHub (it’s easy , just follow these instructions along with me)
Assuming you already created your github account you’ll go to this link and change username by your actual username : https://github.com/username?tab=repositories , then follow these instructions :


You can add a name and choose wether you repo can be public or private for now and forget about everything else for now.

Once your repository created on github , you’ll get this :

As you might’ve noticed, we’ve already run all these commands , all what’s left for us to do is to push our files from our local repository to our remote repository , so let’s go ahead and do that

And just like this we have successfully pushed our files to the remote repository
Here, you can see the default branch main, the total number of branches, your latest commit message along with how long ago it was made, and the number of commits you've made on that branch.

Now what is a Readme file ?
A README file is a markdown file where you can add any relevant information about your code or the specific functionality in a particular branch—since each branch can have its own README.
It also serves as a guide for anyone who clones your repository, showing them exactly how to use it.
You can add a README from this button:

Or, you can create it using a command and push it manually:

But for the sake of demonstrating how to pull content from a remote repository, we’re going with the first option:

Once that’s done, it gets added to the repository just like any other file—with a commit message and timestamp.
However, the README file isn’t on my local machine yet, so I’ll run the git pull command:

Now everything is up to date. And this is just the tiniest example of how you can pull content from your remote repository.
What is .gitignore file ?
Sometimes, you don’t want to push everything to GitHub—especially sensitive files like environment variables or API keys. These shouldn’t be shared publicly. In fact, GitHub might even send you a warning email if you do:

To avoid this, you should create a .gitignore file, like this:

Any file listed in .gitignore will not be pushed to GitHub. So you’re all set!
Cloning
When you want to copy a GitHub repository to your local machine (aka "clone" it), you have two main options:
Clone using HTTPS: This is the most straightforward method. You just copy the HTTPS link from GitHub and run:

It's simple, doesn’t require extra setup, and works well for most users. But each time you push or pull, GitHub may ask for your username and password (or personal access token if you've enabled 2FA).
But if you wanna clone using ssh , you’ll need to know a bit more about ssh keys , so let’s talk about that.
Clone using SSH (Secure Shell): This method uses SSH keys for authentication. Once set up, it’s more secure and doesn't prompt you for credentials every time. Here's how it works:
So what is an SSH key, actually?
Think of SSH keys as a digital handshake between your computer and GitHub.
Your computer generates a key pair:
A private key (stored safely on your machine)
A public key (shared with GitHub)
When you try to access GitHub via SSH, GitHub checks if the public key you've registered matches the private key on your machine.
If they match, you're in — no password prompts needed.
Steps to set up SSH with GitHub:
Generate your SSH key:

2. Start the SSH agent and add your key:

3. Copy your public key:

Then copy the output to your clipboard.
Add it to your GitHub account:
Go to GitHub → Settings → SSH and GPG keys
Click New SSH key
Paste your public key and save.
5. Now you'll be able to clone using SSH like this:

From now on, any interaction with GitHub over SSH will just work — no password typing, just smooth encrypted magic.
And there you have it ! Until next time — happy coding, and may your merges always be conflict-free! ✨👩💻👨💻
#code#codeblr#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code#github
93 notes
·
View notes
Text
THE TRUMP-MUSK FUNDING GRAB: THE QUIET COUP
Since taking office, President Trump and Elon Musk have worked together to defund the federal government from the inside while consolidating power into the hands of a right-wing elite. Their goal is clear: gut federal agencies, strip public resources, and redirect power and money into their own hands.
Agencies Are Starved of Ability to Help People: Key federal agencies—including the Departments of Health, Education, and Transportation—have been forced into bare-bones operations, unable to implement vital programs we depend on.
FEMA and Disaster Relief Blocked: Funding for emergency relief programs is being deliberately slowed or denied, leaving communities vulnerable.
Social Security and Medicare Under Threat: Musk’s “Department of Government Efficiency” has gained full access to the U.S. Treasury's federal payment system, which processes Social Security, Medicare, and tax refunds. His team now has access to millions of Americans’ financial data and can manipulate payments.
DOGE is a Smokescreen for Dismantling the Federal Government: Under the guise of “efficiency,” Musk has proposed cutting $1 trillion in government spending, targeting social programs, education, healthcare, and regulatory agencies that protect consumers and workers.
At the same time, Trump and Senate Republicans are fast-tracking Russell Vought as OMB Director to oversee this attack on federal funding.
VOUGHT IS THE ARCHITECT OF PROJECT 2025
Vought wrote a chapter of Project 2025, which starts by outlining the role that OMB should play in implementing the massively unpopular playbook. If confirmed, Russell Vought will control federal spending. That means he will claim to have the power to:
Freeze funding for critical programs like Medicaid, public schools, environmental protections, and infrastructure.
Redirect federal dollars to right-wing priorities, including tax cuts for the wealthy and corporate handouts.
Defund regulatory agencies that keep corporations in check and protect workers and consumers.
THE PROCESS: HOW THE SENATE WILL PROCEED WITH THE VOUGHT CONFIRMATION VOTE
Monday: Motion to Proceed (MTP) passes, allowing debate on the nomination.
Immediately After: Republican Sen. John Thune can file cloture, starting the two legislative day clock before a cloture vote.
Wednesday: Cloture vote happens, kicking off 30 hours of debate.
Wednesday - Thursday: Senate Democrats must use the full 30 hours to expose this crisis and block the nomination at every turn.
Thursday: Final vote on Vought’s confirmation. If he is confirmed, the Trump-Musk takeover accelerates.
WHAT YOU CAN DO:
1.THIS LINK BY INDIVISIBLE LEADS TO A PAGE WITH RESOURCES INCLUDING POSTERS TO USE WHEN PROTESTING AND WHAT TO DEMAND FROM YOUR SENATORS
2. THIS LINK LEADS TO A CALL TOOL THAT PROVIDES A SCRIPT FOR YOU TO USE WHEN CALLING YOUR SENATOR. TELL THEM THAT WE ARE IN A CONSTITUTIONAL CRISIS
3.Fax: use this link and send a fax to your senator
4. Read through the list of Senate leaders and call a number
5. Contact Your State Attorney General by phone and email:
Minimal script for ALL state attorneys general: We are all learning that Elon Musk, a man who can’t even get the security access he needs to enter parts of SpaceX, and a band of unaccountable teenagers and business cronies, walked into the GSA, TTS, the U.S. Treasury and the USAID offices and took whatever private information they wanted, firing any civil servant who tried to stop them. [Your Stateians] records have most likely been invaded in violation of the Privacy Act of 1974, and as he’s now embedded himself in the Treasury department computer system, payments for Medicare, Medicaid, Social Security and other federal programs are at risk if the Trump administration decides to punish our state, [as he’s currently doing by holding fire victim funding hostage in exchange for extremist voter ID requirements.] Even the short pause from Trump’s executive order to freeze federal disbursements caused panic. We want you to sue the federal government to stop this corrupt and possibly treasonous attack on the privacy rights of our states’ citizens.
6. Contact the Secretary of the Treasury Department! – 202-622-2000
Minimal script for Secretary Scott Bessent: I’m calling to demand that you remove Musk’s access from all systems under your control, that all his equipment is confiscated, that his team is interrogated as to all actions they took under his direction, and that a computer forensics team is assigned immediately to check the system for integrity of its security systems.
More info on: https://indivisibleventura.org/2025/02/01/the-guy-nobody-trusts-with-a-full-security-clearance-now-has-access-to-all-your-private-data/
#usa politics#us politics#anti donald trump#stop trump#stop donald trump#anti trump#fuck trump#fuck donald trump#never trump#stop project 2025#fuck project 2025#save democracy#us senate#lgbtq+#civil rights#american politics#hr 9495#aclu#stop internet censorship#fight for the future#stop bad bills#american civil liberties union#tags for visibility#signal boost#please spread#please support#please reblog#urgent#very important!#important
108 notes
·
View notes
Text
Gaza donation/aid scam
Hey lovelies, there have been a lot of scams going around of people pretending to be Gazans seeking aid. So this is a reminder that if a person shows up in your tumblr inbox who you don't know asking for money, don't give it to them. Ask further questions. If things don't line up on their account they are probably a scam.
This person who

Seemed legit enough right? I have now verified is a scam.



After asking some very simple questions they dodged all of the questions giving answers which didn't make sense.




Some of the things that didn't add up:
BIG RED FLAG
their account seemed to be four hours old, after turning on timestamps the oldest repost on their account (in fact all of their reposts) were four hours old - this is a massive red flag
said name was Tasneem Doreen Rajaab in the ask, email address is a completely different name, paypal is another different name 'Dorine Nanjala.' All three names are of different ethnic backgrounds making it unlikely this person was using a family member's account.
used very fluent english in their donation post but broken english in the ask and dms
+ more
Some of these things could be explained however when I reached out for clarification they dodged my questions and gave me nonsensical answers. A lot of these scams seem to use diabetes as part of their story so watch out for that.
Some scam busting blogs I'd recommend following are mysillypoker, kyra45, mangocheesecakes, and neechees.
When you receive an ask from a blog like this, reporting them for spam or phishing and reporting the PayPal account for fraudulent activity does help get these accounts taken down.
instead of giving your money to random blogs who might be scammers donate to
any of the families on this verified list from @palestineasdiqa on instagram
USPCR's toolkit
Participation and political resources for US, UK and Canada
gazafunds.com
Medical Aid for Palestinians
Doctors Without Borders (they provide medical care to many impoverished and war torn countries other than Palestine)
guide to buy & send esims to gaza
I will be tagging any of the people who reposted this scam not to call you out or anything but to spread awareness
@blossommagicghost @vendettafrank @lesbian-rlbmut @dylaadywptd @ohnoitsoak @petitommo @squidarts @nervestatic @py-dreamer @shippin-my-sanses @helllonursee2 @mirajanefairytailmage @leafwateraddict @passinhosdetartaruga
fyi they blocked me
#gaza scam#scam#dont let this make you mistrust all gofundmes and such#there are ppl out there who need help#just verify that youre actually giving money to someone who needs it#also dont send me asks or dms asking me to give you money or reblog your donation post#stop it#im not gonna#donation scam#my posts#palestinian aid scam#vee's scamlist#jollyduckdetective#Dorine Nanjala#Tasneem Doreen Rajaab#scambusting
188 notes
·
View notes
Text
Taken from u/Visual_Industry_ on Reddit
First, know that *they* are silencing news about protests. We are not laying down. You can find community, resources, and protest events against Donald J Trump, Elon Musk, and their administration on the 50501 subreddit.
Next, if you are, for any reason, unable to make a demonstration, please call your representatives. Call your senators, congresspeople, and anyone in the White House. Contact your governor's office as well. Use this resource sheet for more information.
Finally, send the following letter template aand share the above links around at the very least. I copied and edited this one from u/Die_of_beaties. Hell, you can copy/paste this entire blog onto yours. Get word out. Do demonstration, call, and even email if you can.
But share links and send emails at the very least. Here is the template. Change and edit information as needed.
Congressman/Congresswoman/Senator/Governor _______,
I write to you as a citizen of your district/state/precinct.
I and my community have grave concerns that President Donald J. Trump's excessive abuse of power within only two weeks holding this prestigious office demonstrates nothing less than an overwhelming and blatant disregard for our Government, our Democracy, and the democratic process. It is a budding display of despotism with a tyrant's actions and words, not an American president's. He and his administration, including 'special government employee' Elon Musk, show zero honor for the Constitution upon which this great country was built.
Yet, we are to trust that he and his administration will faithfully uphold the Constitution? I'd like to outline a few specific instances of particular concern:
1. The memo freezing federal grants and loans:
He overreached and abused his power via this unconstitutional act. Federal spending power belongs to Congress, not the president.
2. Birthright citizenship removal:
This attempt violates both The Bill of Rights and The Constitution, two documents upon which this nation was founded, built, and grown. This attempt shows that he disrespcts each and that he cares nothing about his presidential duty to uphold and defend these documents, what they stand for, and who they protect. He, therefore, shows no regard for the United States of America. And I fear this disrespect and disregard can and will go further.
3. Emoluments Clause violations:
He launched a crypto currency which directly violates the Emoluments Clause. This president Donald J. Trump (and potentially his family or beneficiaries) profit directly from his position and crypto currency to the tune of a few billion (at least). I, personally, have no issues with crypto in itself. I do take issue with an already proven shady public figure profiting via difficult-to-track means by which he could easily send and receive funds or bribes from potentially dangerous foreign entities. He also stated he would do so to varying degrees during his campaign. These actions require a thorough and unbiased investigation from those who are not tied to or purchased by him.
4. Public comments about "rigging" or "stealing the election":
He and his associate Elon Musk publicly made comments suggesting that they may rig the election against the voters leading up to Election Tuesday on November 5th 2024. This point should have already been acted upon via a federal investigation of all parties involved, Elon Musk in particular. The time-sensitive data of voting records demanded and continues demanding such urgent attention.
5. Repeated discussion surrounding the use of political violence:
Donald J. Trump and some of his associates repeatedly spoke of using political violence and/or blood shed so that he may forgo American political procedures and have his way once he got in office for this particular term. He used such verbiage against former NIAID director Anthony Fauci, former national security adviser John Bolton, former Secretary of State Mike Pompeo, and Pompeo's top aide Brian Hook. These individuals received death threats against their persons and families once President Donald J Trump stripped them of their security and protections. Donald J Trump also threatened them about social media posts (specifically in the same manner and to the same audience as the January 6th insurrection, including the violent criminals he personally pardoned in said insurection). If another president or government official made similar statements, let alone carried them out, they would certainly face almost immediate criminal charges reaching levels akin or equal to domestic terrorism. President Donald J Trump should not be exempt from such swift action either.
6. Threats against long-standing American allies:
Donald J Trump also threatened long-standing allies, like Mexico, Canada, and Denmark, with either conquest or seizure of land via military action. Our allies did not provoke these statements. He is currently transforming our peaceful borders into hostile territory and beloved allies into potential enemies. I can only think that he does this purely for bombast and ego. No logical human being of sound mind who cares about other citizens would act in such a way.
7. Undermining the First Amendment on The Bill of Rights:
Donald J Trump took bribes from, sued, and threatened with violence opposing journalists, news organizations, social media platforms, and average individuals for speaking up about or reporting on things that don't shine him in a flattering light, including all of the above. He proves time and time he doesn't care to uphold nor honor the Bill of Rights.
Not one of the listed actions come from a true American president but a rising Dictator and Tyrant. Congress has explicitly defined three forms of misconduct as grounds for impeachment;
• “Improperly exceeding or abusing the powers of the office” (First, Second, and Seventh instance above)
• “Behavior incompatible with the function and purpose of the office” (Fourth, Fifth, and Sixth instance above)
• “Misusing the office for an improper purpose or for personal gain.” (Third instance above)
In the instances listed, Donald J Trump explicitly violated each and every one of these definitions.
We hold you and your cohorts as our elected representatives to stand in defense of our democracy, our government, and the United States of America. Push for the proper investigations, trials, and impeachment of Donald J Trump and his party. The inaction we have seen over the last 4 years regarding this man has been unacceptable. Unprecedented happenings require unprecedented and urgent actions before it is too late.
Respectfully,
_______
#us politics#protest#anti trump#anti elon musk#donald trump#fuck trump#elon musk#elongated muskrat#fuck elon musk#fuck elongated muskrat#fight back#contact your senators#contact your representatives
52 notes
·
View notes
Text
We are still in the midst of COVID-19 pandemic. New Yorkers are still being hospitalized with COVID and still dying from COVID. People are still getting Long COVID and other serious health issues from COVID.
Everyone is at risk of Long COVID and other serious health issues from COVID.
Masks are a critical public health tool that help protect people from COVID.
Masks also help protect against other contagious diseases, wildfire smoke, pollution, allergens, and other health concerns.
Everyone has a right to wear a mask.
There should not be a mask ban. A mask ban puts the lives and health of all New Yorkers at risk.
WHAT CAN YOU DO?
This toolkit includes a letter you can send to your reps if you live in, are currently in, and/or travel to New York.
1. Contact Governor Hochul. Urge her not to ban masks.
Phone: 518-474-8390 (press 1 to leave a message, press 2 to speak to a person)
Email: https://governor.ny.gov/content/governor-contact-form
Mail: The Honorable Kathy Hochul Governor of New York State NYS State Capitol Building Albany, NY 12224
Twitter/X: @GovKathyHochul
Instagram and Threads: @GovKathyHochul
2. Contact your NYS Senator and Assemblymember. Urge them to speak out against mask bans and not to support mask ban legislation.
Find your state elected officials and their contact info at: https://www.usa.gov/elected-officials
Check to see if your NYS Senator or Assemblymember has taken a stance on mask bans on our New York Mask Ban Tracker at: http://bit.ly/NYMaskBanTracker
Please let us know if your NYS Senator or Assemblymember speaks out publicly against mask bans.
3. Contact NYS Senate and Assembly leadership. Urge them to speak out against mask bans and not to support mask ban legislation.
NYS Assembly Speaker Carl Heastie
Phone: 518-455-3791
Email: [email protected]
Twitter/X: @CarlHeastie
Instagram and Threads: @CHeastie
NYS Senate Majority Leader Andrea Stewart-Cousins
Phone: (518) 455-2585
Email: [email protected]
Twitter/X: @AndreaSCousins
Instagram and Threads: @AndreaStewartCousins
4. Contact NYS Senate and Assembly Health Committee Chairs. Urge them to speak out against mask bans and not to support mask ban legislation.
NYS Senate Health Committee Chair J. Gustavo Rivera
Phone:Albany Office - 518-455-3395
Email: [email protected]
Twitter/X: @NYSenatorRivera
Instagram: @NYSenatorRivera
NYS Assembly Health Committee Chair Amy Paulin
NOTE: Paulin is a co-sponsor for the mask ban bill A10057A.
Phone:Albany Office - 518-455-5585
Email: [email protected]
Twitter/X: @AmyPaulin
Instagram: @AmyPaulin1
5. Contact your local elected officials, including City Council Members and NYC Borough Presidents. Urge them to speak out against mask bans.
Find your city elected officials and their contact info at: https://www.usa.gov/elected-officials
6. Sign up for an account on the NY Senate webpage and let them know you oppose each of the mask ban bills. There is a question on the right side of the webpage for each bill that asks if you oppose or support the bill. Write that you oppose the bill. In addition, if possible, add a comment expressing opposition to the mask ban bills.
S09867
A10057A
A10043
S09194
7. Contact NYC Mayor Adams.
Email: https://www.nyc.gov/office-of-the-mayor/mayor-contact.page
Phone: 311 or 212-NEW-YORK outside NYC
Twitter: @NYCMayor and @NYCMayorsOffice
Mail: Mayor Eric Adams City Hall New York, NY 10007
Instagram and Threads: @NYCMayor
8. For those not in NY State, you could contact the NY’s Tourism Board and let them know you won’t be traveling to NY State or are canceling your travel plans to NY State due to the proposed mask ban.
Email: [email protected]
Twitter/X: @I_LOVE_NY
Instagram: @ILoveNY
More info: https://www.iloveny.com/
9. Write a letter to the editor or op-ed. See examples below.
10. Post your opposition to a mask ban on social media and share why you still wear a mask. Use the hashtag #NoNYMaskBan.
11. If you are Jewish, sign on to this sign-on letter to state leaders organized by Jews for Mask Rights. This letter is open to all Jewish people affected by this legislation, whether as New Yorkers, commuters, or tourists.
12. Spread the word! Share a link to this toolkit (http://bit.ly/StopMaskBanNY) and graphics below to encourage other people to take action.
13. Wear a mask! Post a photo of yourself wearing a mask on social media.If you hold a public event, require masks at your event and post photos with everyone wearing a mask.
#nyc#long island#new york#jewblr#disability justice#disability wrath month#intersectionality#psa#long post
101 notes
·
View notes
Note
StPD culture is going to a schizospec support page to download a toolkit your therapist recommended, but the site requires your full name as well as your email address to get it, so you don't download it because you're scared they're going to use your information to monitor you.
.
#stpd culture is#schizospec#cluster a safe#stpd#schizotypal#actually stpd#schizotypal pd#actually schizotypal
27 notes
·
View notes
Note
Do you have any advice on how to learn to read faster?
not faster necessarily, no, pretty much all of my advice is abt learning to read slower sry. since most my problems are abt memory & fatigue & hitting yr cognitive threshold for the maximum amount of info you can absorb in one sitting, things like rereading & taking notes in the margins are abt forcing myself to go slower so i rly digest what it is im trying to read.
an app like instapaper, which can save articles in dark mode/large font/preferred line spacing reduces some of the difficulty for me, which i guess leads to being faster? and having the audiobook play at the same time as im reading can help too. covering up yr page (i usually use a bookmark) except to the line that yr reading is helpful to reduce the fatigue of yr eye jumping ahead on the page. i get pretty picky about the books i buy bc i try to avoid any editions where the text is too small & cramped on the page. if there is a hard passage im rly not getting, i read it out loud to myself. i use my pencil to follow along and point to the words im reading. i give myself lots of breaks so i don’t burn out. when its rly important (like having to read complex articles for my grad classes) i would try to read in bed around 10-11am bc that tended to be my best time cognitive energy-wise. difficult to do if u have other things that are higher priority, but sometimes you gotta be gentle with yourself and go “i had to prioritize [x thing] so i have less energy to spend on reading for fun, and it’s okay that im gonna be slower”
oh also! maybe look @ yr toolkit of pre-reading strategies. before i sit down to read something closely, i skim the abstract, the author bio, the section headings/chapter titles, the bibliography, the end notes, the index. i highlight anything that might be interesting or relevant. this helps give me an overall sense/shape of what im going to be reading. it gives me “anchor points” to tether information to. if you feel like yr rly wading thru mud, maybe u need to practice yr pre-reading strategies (like exercising a muscle, it gets easier to more consistently u do it)
also, you may just be reading something that’s rly hard! we had to read a lot of Elfriede Jelinek and like — she’s difficult to read, and deliberately so as a philosophical/stylistic choice. also, if yr reading a text in translation, i find that browsing a few translations beforehand or asking around which translations my friends like makes such a huge difference. a lot of public domain translations (like the cheap dover thrift editions you can get secondhand rly easily) are ASS when it comes to readability. like i had my Lattimore translation of Oedipus beside one of the public domain ones and it was like night and day in terms of readability.
lastly, idk yr reasons for wanting to read faster, but if it’s something like yr workload for a university course — i would usually email my profs to introduce myself in the summer before term or over winter break. i’d say i’m looking forward to their course & ask politely if they had their reading list on hand bc being able to read in advance made a big difference with how i could keep up with the workload during term time. and also importantly: if i was truly struggling, i would ask myself “is this a normal human being amount of reading to assign? or does this prof have expectations that are not grounded in reality?” bc sometimes the latter is v much the case! and you should just release yrself from putting undue pressure on yrself. try yr best but don’t beat yrself up for something that is an impossible task.
#future literature tag#most stuff online abt reading faster is by hucksters and charlatans#especially ai stuff#like proquest try to force an ai feature that summarizes articles?#my brother in christ that is what the abstract is for
8 notes
·
View notes
Text


I managed to get some studying in, even if it was pretty late
finished parabola notes
finished parabola section of practice 08
emailed math prof about taking a quiz I missed
did music appreciation discussion board
updated mathematics toolkit
[ kitties below cut ]
Cruella is being nice :)


#val studying occasionally#mathblr#mathematics#studyblr#precalc 1#study notes#music appreciation#val's cat(s)#aug 2024#also WOW#the quarter is basically over and ive went through a whole ass notebook for 1 subject#but also i write big so idk if it was rlly that much#val's post
22 notes
·
View notes
Text
The biggest heist that almost was
Let me tell you about the most insane bank heist that is going to sound like I'm just leaking the script for the next American hacking movie. The goal? Steal one billion USD. And it all began with an email and a printer, which as we all know is where problems usually start. Another weapon in this heist was... Weekends and time zones.
As usual, no prior computer science education needed.
What happened?
On the morning of February 5th 2016, a printer had stopped working in the central bank of Bangladesh (Bangladesh Bank). But it wasn't just any printer, it was the printer responsible for printing all the records of the multimillion transfers going in and out of the bank. When the poor employees finally won the printer battle and had it resume normal operation, they saw a very concerning account transfer in the records that was coming out. The bank had an USD account in the USA, at Federal Reserve Bank, with approximately 1 billlion Dollars in it, and the Federal Reserve Bank had received instructions to drain almost the entire amount. In the records that came out in the printer, the American bank had attempted to urgently message the Bangladesh bank regarding this transfer, but couldn't get through to them. This was because the hack had actually started the day before, Thursday 4th, at around 20:00 Bangladesh time, when the bank was closed. However, USA had just started their day, giving the American bank plenty of time to follow through with the instructions from the Bangladesh bank to drain their entire account while they were closed. And that wasn't the end of it, as weekends are from Friday to Saturday in Bangladesh, meaning that the Bangladesh bank headquarters in Dhaka wouldn't discover this withdrawal until Sunday morning. That's when they immediately tried to reach the American bank, which of course didn't work as over there it was Saturday evening, and the American weekend is from Saturday to Sunday, meaning that they wouldn't be reachable until Monday.
You see what I mean by the hackers using time zones and weekends, finding the perfect time for the American bank to execute their orders while Bangladesh discovers the withdrawal several days too late, and again several days too late for Americans to be reachable. But it didn't stop there with their timehacking.
The money had to go somewhere from the American bank, and it would be stupid to send it directly to the hackers own account without laundering the money first. So they had set up four different bank accounts in the Philippines, using fake names and credentials. Why the Philippines? Because the Lunar new year was on Monday the 8th, which is a holiday and holiday means no bank activities in either Bangladesh or the Philippines, buying the hackers even more time. As a final act, they messed with the printer responsible for printing transaction records, adding another few hours to their schedule. Moon and stars really aligned perfectly for this plan.
But how did they do it?
It all began one year prior, in January 2015, with an email sent to several employees at the Bangladesh Bank. The email seemingly contained a job application from a person who didn't actually exist, but who was very polite in his request for a position at the bank, with a link to his CV and cover letter. Naturally this link led to a document with a little surprise gift - malware. Since the heist happened, at least one of the recipients must have clicked the link, and successfully deployed a RAT - Remote Access Trojan, malware that lets you control a computer from the comfort of your own home, as well as a toolkit with various malware to move from computer to computer, avoiding discovery, and covering their tracks.
From there, the hackers slowly made their way through the bank offices network, one step at a time to avoid setting off alarms, looking for any computer that had control of the banks SWIFT setup. SWIFT lets banks transfer large amounts of money between themselves and other banks connected to SWIFT. And as soon as they found one of those computers, they stopped. They didn't need to hack SWIFT in the traditional sense of the word - since they operated in a bank computer, the SWIFT-software assumed they naturally had to be bank employees. However, one of the parts of the malware used in the heist was for manipulating the SWIFT system, as the hackers weren't physically there to press anything. Additionally, since they were laying dormant for the time to strike, they needed to keep an eye out for SWIFT updates that could detect any tampering with the system, and adapt accordingly.
Then they waited many months for the stars to align on February 4th, 2016.
There were 35 transfers made by the hackers from the American bank account, totaling almost 1 billion USD, but there were two of these tiny little seemingly insignificant details that prevented this from becoming the worlds largest bank heist in history. The hackers biggest enemy became this concept known as “words”.
The Philippine bank accounts were all located in the same RCBC Bank office on Jupiter Street in Manila. And this would be the hackers downfall, as USA had sanctions put on an Iranian cargo ship called Jupiter. Since the transactions went to a recipient that contained the word “Jupiter”, it created a security alert in the Federal Reserve Bank that the employees needed to investigate. When they saw what was going on, they managed to stop all but five of the initial 35 transactions, thus “only” roughly 100 million USD made it to the Philippines. The Bangladesh bank requested to reverse the transactions, but since the money was in the Philippines, they would need bureaucracy in form of a court order to reclaim the money, and we all know that's not a 5 minute project. It was when Bangladesh filed the court order in late February that the case became public (since court orders are public documents) and the news broke to the country.
Once in the RCBC bank accounts, the money arrived on Friday the 5th and was immediately moved again. First the 100 million was converted to local currency, and some of it was withdrawn in cash, while the rest was sent off to other hacker-controlled locations. And this is where the second tiny little detail cut off even more of the hackers precious payday. 20 million USD had been sent to Shalika Foundation, a charity organisation in Sri Lanka. But, once again the hackers worst enemy - words - decided to strike again. A typo was made in their transaction, sending the money to “Shalika Fundation”, and a bank employee who must have had their morning coffee spotted this typo and rejected the transfer and kept the funds frozen. This left the hackers with 80 million USD.
✨Now comes the money laundering!✨
There was a second reason for choosing the Philippines as deposit zone; gambling is legal and the casinos had no money laundering regulations imposed. The accomplices of the heist booked private rooms in two casinos located in Manila - Solaire and Midas - and proceeded to purchase tokens to gamble for with the stolen money. Since they played with a room consisting of their fellow accomplices, winning was not really much of a challenge. Then the tokens could be exchanged back to money that would now be clean. To avoid suspicion, they didn't gamble all of the money at once, but over the course of several weeks gambled away the dirty money to clean money.
Who was behind it?
It's normally difficult to pinpoint where the more sophisticated hacking groups come from. Oftentimes, they will leave false clues behind that points to another group so they will face more trouble instead of the group that did it. They may even place clues from several different groups, just to mess with the analysts. It's also quite common to simply “steal” a way of working from another group, or use a leaked/stolen tool from another group (criminals aren't safe from other criminals, especially not in this business) - there are new malware coming out all the time with code that is just a slight modification of a well-known malware actor that had their source code leaked or simply had hired the same programmer. Or they may leave no clues as to who was behind it. Attribution to the guilty part is usually the single most difficult mission in IT-security - often it's just pure guesswork with little to no solid evidence to back it up, if you're lucky there's circumstantial evidence.
This case was no different. The first clue came from the IP the bad guys used to connect to the Bangladesh bank from. It was located in Pyongyang, North Korea. But, as I mentioned, this is not a conclusive verdict, as the IP may simply be planted false evidence to throw the analysts off their track. After the heist, the hackers used a data-wiper to scrub as much of their malware off the bank systems, but they didn't succeed in deleting all of it, some of the tools were still present, including the wiper.
Due to the scale of this operation, it caught the attention of every single IT-security person and IT-security company worldwide, who all of course wanted to know who and how they did it. With the remaining malware, a joint effort was made, comparing malware code to other malware code for similarities. Some was found in Poland, after an analyst noted the similarities from another suspected North Korean hack. Some was found in another infamous North Korean hack targeting Sony Pictures. More and more signs pointed towards the same actor. Some were false leads, the hackers seemed to be wanting to implicate the Russians did it, but failed quite miserably at that, just sprinkling random Russian words into the malware and making it way too obvious it was a ruse.
You may not believe this, but the North Korean government has one of the most notorious hacking groups in the world, known as the Lazarus Group. Some of its more well-known adventures include an extremely data-destructive hack of Sony Pictures (as punishment for releasing “The Interview”), creation of the ransomware WannaCry which was used against many targets worldwide (including hospitals), and various attempts at gathering information from governments and government-affiliated corporations all over the world. And, of course, this heist.
Eventually, after months of collaboration all over the world, the final verdict fell on North Korea, and specifically one of their programmers. His name is Park Jin Hyok, and worked for Chosun Expo - a front company for the North Korean government, located in Dalian (China) who used the funds of the fake corporation gained from legitimate programming jobs from customers worldwide to create the malware and plan the heist with all of its expenses. Of course he wasn't the sole person involved in this project, but it's the only person we know was in it.
This particular heist had been meticulously planned for several years, and Park Jin Hyok had moved to Dalian, set up fake IDs and built a network of contacts there to avoid suspicion. However, he didn't manage to delete all of his online footprints, and became the number one suspect when his internet activities suddenly came from Pyongyang, North Korea.
Additionally, several Chinese business men - many associated with the casino industry in China's Macau territory - were also charged and arrested for assisting with setting up the gambling rooms and coordinating the money laundering process. One unknown Chinese business man managed to get away with 31 million USD of the 80 million that remained after the heist, and as you would expect, he was never to be seen again.
With the middlemen from China paid off, not much remained of the original 1 billion to North Korea. But the heist has fascinated the whole IT-security world nonetheless.
I remember when the news of this case dropped to the IT-security world, who all wanted to take part in the hunt. It was a very fun time, we were all sitting at the edge of our seats waiting for the next update. I hope it was at least somewhat exciting for you too to read about, and thank you for reading this long post! If you liked it, please consider reblogging as it motivates me to write more. You may also like malware stuff I've written about before, such as Stuxnet or just plain evil malware that is a threat to our daily lives.
As always my inbox is open if you have any questions.
94 notes
·
View notes
Text
🛠️ Behind the Scenes: How I’m Prepping to Launch My Photography Biz 🎬📸
Starting a creative business isn’t just about having a camera and an Instagram page (although those definitely help). It’s also about building the right structure behind the scenes so everything runs smoothly—especially when you're offering a service like photography that relies on you being the product and the process.
So here’s a little peek into what my business operations plan looks like, and how I plan on getting everything together to officially launch my photography brand for small businesses here in the Niagara Region.
🎯 What I’m Offering (and How to Making it Happen)
At its core, my business is all about creating branded visual content for local entrepreneurs, shops, creators, and hospitality spaces. Think product shoots, branding sessions, lifestyle visuals—stuff that helps people show up online looking like they mean business (because they do).
I’m not selling a physical product, but I am creating deliverables—photos, curated image sets, sometimes even moodboards or creative direction—and those take resources. So while I’m not sourcing inventory, I do need to keep my toolkit solid.
🧰 Tools + Gear I Use
Here’s what I already have in place (or am investing in):
Camera gear – I shoot with a mirrorless DSLR that handles both sharp product shots and moody lifestyle work.
Lighting – Mostly natural light for now, but i plan on getting reflectors and invest in portable softbox for indoor setups.
Laptop & editing software – Lightroom and Photoshop are my go-tos, and I’ve got presets I’ve developed to keep my work consistent.
Props & backgrounds – I’m slowly building a small collection of flatlays, textures, and versatile props that work across brands. I also plan to thrift or DIY a lot of this to stay creative and budget-conscious.
Client booking tools – At the moment i only have an email that is specifically used only for my photography but i also have my Instagram. It's not exactly fancy but it works.
⏳ Can I Get Everything in Time?
Totally. Most of the tools I need, I already have or can get easily. Props and creative resources will grow over time, but the basics are here. I also plan to rent studio space as needed, depending on what the shoot calls for. A lot of clients want their photos done in their space anyway (shops, salons, cafés), so being mobile is a win.
📝 Licenses + Permits?
Because I’m a service-based business working independently, I’ll be operating as a sole proprietor. I’ll register my business name and handle any tax stuff that comes with that.
As for licenses, I don’t need anything major unless I’m renting commercial space regularly or doing shoots that involve permits (like certain public areas or drone photography). But I’ll stay on top of that as things grow.
🚀 What I Need to Launch
My launch won’t be a big grand opening—it’s more of a soft rollout. I just want to get in front of people who need the work and start booking. But to really make it official, here’s what I’m putting in place:
A clean, simple portfolio website or landing page (I’m thinking Squarespace)
A few strong sample projects that show what I can do
Clear pricing/packages that are easy to understand and flexible for different needs
Local networking—connecting with business owners, visiting shops, going to markets, talking to people
Consistent Instagram content to show off behind-the-scenes and finished work
💡 The Big Vision
I want to build something real—not just a gig, not just a side hustle. I want this business to feel like a creative partner to the local brands I want to/ will work with. Like, yeah, I’ll take your product photos, but I also want to help you figure out how to use those photos to actually grow your business.
I want to keep it collaborative, community-focused, and flexible. And I want my clients to feel seen, supported, and proud of how their brand shows up in the world.
So that’s where I’m at. Bit by bit, getting the tools in place, building the vibe, and getting ready to hit “go.”
2 notes
·
View notes
Text
The Ultimate Guide to Online Media Tools: Convert, Compress, and Create with Ease
In the fast-paced digital era, online tools have revolutionized the way we handle multimedia content. From converting videos to compressing large files, and even designing elements for your website, there's a tool available for every task. Whether you're a content creator, a developer, or a business owner, having the right tools at your fingertips is essential for efficiency and creativity. In this blog, we’ll explore the most powerful online tools like Video to Audio Converter Online, Video Compressor Online Free, Postman Online Tool, Eazystudio, and Favicon Generator Online—each playing a unique role in optimizing your digital workflow.
Video to Audio Converter Online – Extract Sound in Seconds
Ever wanted just the audio from a video? Maybe you’re looking to pull music, dialogue, or sound effects for a project. That’s where a Video to Audio Converter Online comes in handy. These tools let you convert video files (MP4, AVI, MOV, etc.) into MP3 or WAV audio files in just a few clicks. No software installation required.
Using a Video to Audio Converter Online is ideal for:
Podcast creators pulling sound from interviews.
Music producers isolating tracks for remixing.
Students or professionals transcribing lectures or meetings.
The beauty lies in its simplicity—upload the video, choose your audio format, and download. It’s as straightforward as that
2. Video Compressor Online Free – Reduce File Size Without Losing Quality
Large video files are a hassle to share or upload. Whether you're sending via email, uploading to a website, or storing in the cloud, a bulky file can be a roadblock. This is where a Video Compressor Online Free service shines.
Key benefits of using a Video Compressor Online Free:
Shrink video size while maintaining quality.
Fast, browser-based compression with no downloads.
Compatible with all major formats (MP4, AVI, MKV, etc.).
If you're managing social media content, YouTube uploads, or email campaigns, compressing videos ensures faster load times and better performance—essential for keeping your audience engaged.
3. Postman Online Tool – Streamline Your API Development
Developers around the world swear by Postman, and the Postman Online Tool brings that power to the cloud. This tool is essential for testing APIs, monitoring responses, and managing endpoints efficiently—all without leaving your browser.
Features of Postman Online Tool include:
Send GET, POST, PUT, DELETE requests with real-time response visualization.
Organize your API collections for collaborative development.
Automate testing and environment management.
Whether you're debugging or building a new application,Postman Online Tool provides a robust platform that simplifies complex API workflows, making it a must-have in every developer's toolkit.
4. Eazystudio – Your Creative Powerhouse
When it comes to content creation and design, Eazystudio is a versatile solution for both beginners and professionals. From editing videos and photos to crafting promotional content, Eazystudio makes it incredibly easy to create high-quality digital assets.
Highlights of Eazystudio:
User-friendly interface for designing graphics, videos, and presentations.
Pre-built templates for social media, websites, and advertising.
Cloud-based platform with drag-and-drop functionality.
Eazystudio is perfect for marketers, influencers, and businesses looking to stand out online. You don't need a background in graphic design—just an idea and a few clicks.
5. Favicon Generator Online – Make Your Website Look Professional
A small icon can make a big difference. The Favicon Generator Online helps you create favicons—the tiny icons that appear next to your site title in a browser tab. They enhance your website’s branding and improve user recognition.
With a Favicon Generator Online, you can:
Convert images (JPG, PNG, SVG) into favicon.ico files.
Generate multiple favicon sizes for different platforms and devices.
Instantly preview how your favicon will look in a browser tab or bookmark list.
For web developers and designers, using a Favicon Generator Online is an easy yet impactful way to polish a website and improve brand presence.
Why These Tools Matter in 2025
The future is online. As remote work, digital content creation, and cloud computing continue to rise, browser-based tools will become even more essential. Whether it's a Video to Audio Converter Online that simplifies sound editing, a Video Compressor Online Freefor seamless sharing, or a robust Postman Online Tool for development, these platforms boost productivity while cutting down on time and costs.
Meanwhile, platforms like Eazystudio empower anyone to become a designer, and tools like Favicon Generator Online ensure your brand always makes a professional first impression.
Conclusion
The right tools can elevate your workflow, save you time, and improve the quality of your digital output. Whether you're managing videos, developing APIs, or enhancing your website’s design, tools like Video to Audio Converter Online, Video Compressor Online Free, Postman Online Tool, Eazystudio, and Favicon Generator Online are indispensable allies in your digital toolbox.
So why wait? Start exploring these tools today and take your digital productivity to the next level
2 notes
·
View notes
Text
How to Access Canva Premium for Free or Cheap in 2025
Affordable Ways to Access Canva Premium in 2025
In 2025, visually compelling content is essential—whether you're growing a brand, teaching students, or raising awareness for a cause. That's why many creators turn to Canva Premium. This upgraded version of the free design platform delivers advanced features that boost efficiency and creativity. While the full plan carries a cost, there are several practical and budget-friendly methods to access Canva Premium without overpaying. Let’s explore the best options available this year.
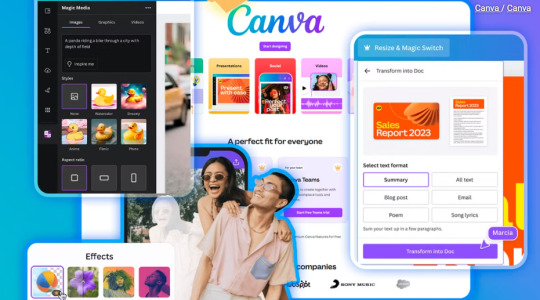
Why Choose Canva Premium?
Before diving into cost-saving methods, it's important to understand why Canva Premium stands out. The upgraded toolkit empowers users with time-saving and professional design features that aren't available in the free version.
Key features include:
Magic Resize: Instantly adapt designs for different platforms.
Background Remover: Remove image backgrounds with one click.
Brand Kit: Keep your fonts, logos, and color palette organized.
1TB Cloud Storage: Store and manage a vast library of design assets.
Access to 100M+ Premium Assets: Choose from exclusive images, templates, and videos.
With such a powerful suite of tools, it's easy to see why Canva Premium is a must-have for serious creators. Now, let’s explore how you can get these features at a fraction of the cost—or even for free.
1. Start with a 30-Day Free Trial
One of the easiest ways to try Canva Premium is by activating the free 30-day trial. This is a great choice if you're starting a campaign, updating your portfolio, or testing design tools for a new project.
To activate:
Head over to Canva’s pricing page.
Click “Start Free Trial” under the Premium section.
Sign in or register for an account.
Enter your billing information (be sure to cancel before the trial ends if you don’t want to continue).
This trial grants full access to all Canva Pro features, letting you evaluate its value with zero upfront cost.
2. Free Access for Students and Teachers
If you’re involved in education, Canva has an excellent offer for you. Canva Premium is completely free for eligible students and educators through its Canva for Education program.
Here’s how to apply:
Visit the Canva for Education page.
Register using your school-affiliated email address.
Provide verification documents if required.
Once verified, you'll gain access to a wealth of design tools that enhance learning and creativity. From lesson plans to digital presentations, Canva Premium empowers both students and teachers to create with confidence.
3. Canva Premium for Nonprofit Organizations
Nonprofits often operate on tight budgets. Thankfully, Canva supports these missions by offering Canva Premium at no cost to verified nonprofit organizations.
To apply:
Go to Canva’s Nonprofit Program page.
Submit proof of nonprofit status.
Wait for verification and approval.
With access to Canva Pro tools, nonprofits can create impactful visuals for fundraising, events, and advocacy—without paying for expensive software.
4. Purchase from Verified Discount Resellers
If you don’t qualify for the free educational or nonprofit plans, you can still get Canva Premium at a reduced rate. Trusted resellers like Saasyto offer discounted subscriptions, making this an attractive option for freelancers, marketers, and small businesses.
Here’s what to do:
Visit Saasyto.com and search for Canva Premium deals.
Choose a monthly or annual subscription that fits your needs.
Follow the site’s instructions to activate your account.
Although it’s not free, this method can cut your design costs significantly over time while giving you full access to premium tools.
Make the Most of Canva Premium—Affordably
In conclusion, creating top-notch visual content no longer has to be expensive. Whether you’re an educator, nonprofit worker, or content creator, there’s a way to access Canva Premium without exceeding your budget. From free trials to education plans and nonprofit programs, several legitimate methods exist to help you unlock professional-grade tools.
Even if you're paying, discounted options from authorized resellers can make Canva Pro features accessible at a lower cost. By selecting the option that matches your needs, you can elevate your designs and stand out in today’s visually competitive world—without breaking the bank.
2 notes
·
View notes
Text
Freelance Brand Scaling Secrets: Empowering Brands to Dominate

Imagine a system designed not just for freelancers, but for brands—transforming ordinary companies into market powerhouses.
Freelance Brand Scaling is about more than generating ad copy or driving traffic; it’s about building an integrated brand growth engine that scales every facet of your business which is critical in today's world. Most "brand scaling" services out there focus on running Facebook ads. That’s child’s play. We take a full-stack approach—an elite-level, SEO-backed, AI-driven system designed to dominate your niche, multiply your ROAS, and create long-term sustainable growth.
We harness the precision of SEO, the art of funnel optimization, and the cutting-edge capability of AI to help your brand not only get noticed but become unforgettable. Think of it as a complete transformation toolkit that positions your brand as the leader in your market, turning every digital interaction into an opportunity for growth.

Our strategy is built on three core pillars:
SEO Mastery:
We engineer your online presence to rise above the noise. By optimizing your website and content with data-driven SEO techniques, we ensure that your brand consistently appears at the top of search results—attracting qualified, organic traffic that converts.
Funnel Optimization:
Every brand needs a roadmap to conversion. We create customized marketing funnels that seamlessly guide prospects through a journey—from initial awareness to final purchase. Whether it’s a compelling landing page, a series of nurturing emails, or an engaging video sales letter, each element is crafted to eliminate friction and maximize conversion rates.
AI-Powered Copy:
In a world where words make or break your brand, our AI-enhanced copy generation produces persuasive, tailor-made messaging that resonates with your audience. Using the best practices of legendary copywriters and the latest in artificial intelligence, we create copy that not only captures attention but drives real, measurable results.

This isn’t just about doing more—it’s about doing better. We help brands break free from the limitations of traditional marketing by combining timeless creative insights with modern digital strategies. The result? A dynamic, scalable brand that commands premium pricing, builds a loyal customer base, and dominates its market niche.
Step into a future where your brand isn’t just surviving—it’s thriving. Embrace a system that turns every click into a conversion, every interaction into an opportunity, and every campaign into a success story. With our Freelance Brand Scaling Secrets, you’re not just investing in marketing; you’re investing in a legacy of growth and excellence. Are you ready to empower your brand to dominate the marketplace? The future belongs to those who scale smarter!
3 notes
·
View notes
Text
Read through the "transgender DEI toolkit: guide to transitioning in [profession]" pdf on [professional association my employer's a member of]'s website out of curiosity. And I think my jaw dropped further with every page. "Meet with your supervisor to set a Transition Date (the point at which you'll actually start dressing any differently/using the other bathroom/expecting anyone to use your pronouns) two months in advance." "If you work at an org of 400 employees, send a Transgenderism Announcement Email to every single one of them. Sign off by thanking them in advance for hopefully not hate criming you." "Your org will then hold a Trans 101 all staff meeting, at which you won't be present, so that your co-workers can ask questions that they might feel embarrassed to voice in front of you." "Here are some prepared talking points for you to calmly and patiently recite if your co-workers ask 'why can't you just be gay' or 'are you going to get The Surgery.'"
Perhaps some of my horror is simply post-tipping point transitioner privilege (this guide was posted in 2019 & is still up). And perhaps some is simply the sheer alienness of a mid-white collar career transition (think I've barely met anyone whose Coming Out At Work Journey wasn't "drift through a series of customer service jobs until you hit a Pronouns On Name Tags one"). But I don't think they could have made having a transgender in the workplace sound more mortifying and inconvenient for everyone involved if they tried. Might as well have just been "guide to transitioning: don't."
9 notes
·
View notes
Text
for those who live in the us, we can help by doing the following:
using the 5calls.org to generate phone numbers of your local reps and officials to call for a ceasefire
emailing your reps to call for a ceasefire (action network, public kit, toolkit #2)
check out and share updates via telegram (1, 2, 3, 4)
continue SHARING updates on gaza on social media. there's a current blackout and we gotta help out by spreading what's going on like WILDFIRE to ensure everyone remembers this.
LISTEN TO AND AMPLIFY palestinian voices during this time (here's a list)
if you don't know what's going on, GET EDUCATED. whole families are being wiped out as we speak, we cannot sit here and play both sides. we have blood on our hands as fellow americans.
#palestine#gaza#free palestine#text#i didn't see that many helpful links on the top so i'm gonna use this#idk how active y'all are anymore but i'm gonna need y'all do fawking work
47 notes
·
View notes
Text

another year, another silence— a collection of birthday's throughout the years.
The first birthday she remembers is in shards—
Nadia is eight. At least, she thinks she was. She remembers a party, one her father had insisted on throwing. It wasn't for her. Not really. The ballroom was stifling, sweaty— too many bodies cramped into too-tight a space. The air felt sticky.
But what she really remembers? The scratch of too-stiff material against her skin and most of all. . . The sound of her mother's voice.
"Take my hand, little love. Just stick close to me, you're alright."
A hand larger than hers, soft, pressing something into her palm. The crinkle of a wrapper and the taste of chocolate enveloped her tastebuds. Something just for her— something simple but something that would stick with her for far longer than that moment.
It wasn't often she got her mother's attention, but when she did?
It was soft.
Warm.
Safe.
Nadia had clung to that in a house— a childhood that felt like ghosts. Sometimes she still did.
Her ninth birthday isn't much different. There's no correspondence from Tony— no phone call, no letter, no present. Even though she watches the phone all day. He said he'd call. He doesn't.
She eats dinner alone in a too-large dining room, her fork hitting the plate, echoing against the walls. A housekeeper would bring a cake and a pre-wrapped present.
By her tenth birthday, the absence screams louder. Maria is busy doing— Nadia doesn't know what. Howard is at some conference. There's a fleeting brush of her hair as she passes her mother in the halls, a whispered happy birthday in a soft cadence only her mother could manage— a too brief hug. The loss of her mother's warmth immediately stings.
Nadia stays in her room the rest of the night— crying into her pillow.
And by eleven? Well, by eleven they're gone. Tony is too much of a wreck to show up. Obadiah picks her up from the bus station. She's allowed home from boarding school. no-one comes to pick her up. For a while, she wonders if they ever meant to. But he shows. With a cupcake and a candle. She feels a brief flicker of hope. It's swiftly blown out.
The next year, Nadia doesn't get to go home. She pretends she's sick so she can skip class. She doesn't want to deal with birthday wishes from teachers. Doesn't want to feel like a ghost in her own skin. . . Because what else are you? When the people you love forget you exist?
By sixteen, she's close to leaving the hell hole her family and stark industries called 'prestigious' but another birthday passes. They always do. No visitors. No cards. Not even an email.
It hurts— even if she stopped hoping years ago.
She sneaks out— persuades some stranger to buy her some cheap vodka (or bribes— she pays him extra). She spends the night drinking for the first time. Drowning her weight in vodka. Throws it up in a bush. Laughs. Because it's another echo of how she feels inside. Another echo of her empty life.
At nineteen she's in her first year of MIT. A classmate throws a party. She doesn't know it's her birthday. Nadia almost attends— almost. Instead she spends the night in her lab fixing a broken rig and eating half a snickers bar she got from a vending machine for dinner. It's still better than any party her father used to throw.
Her twenty first birthday comes without fanfare. She's graduated now. There's a Stark Industries card sent. Impersonal as it always was. Obie sends her a toolkit with her initials engraved in the handles. It means more than she says. She spends the night fighting underground just to feel something that isn't this ache. This hurt. She doesn't want to sit in it. She doesn't win. Not even almost. But she gets back up and spits out blood. Patches herself up in some alley. By this point— she's already learnt not to rely on others.
When she gets back to her apartment— there's a luxury hamper on her doorstep. Something that should have been home comforts.
It aches.
Nadia knows instantly it's from Pepper— somehow her brother's assistant cares about her more than he ever had.
By the time she joins SHIELD, she's twenty two, a rookie, fresh into the field. She expects the birthday to be like any other. It almost is. Except Clint tosses her a cupcake after the mission. Looks at her like he knows— but doesn't mention it. Doesn't say anything. And somehow that means everything.
She doesn't say thankyou. But she eats the cupcake anyway. Slowly.
Twenty six rolls round, a whole lifetime of missed birthday's, of silence instead of softness, instead of comfort. Tony's back in her life now— after Afghanistan. After Obie. After everything that fractured them leaves them gaping open, bleeding Infront of eachother even if they don't talk about it. She's still a little angry. But she he texts her "Happy belated. Drinks?" She doesn't say no. They don't talk about it. Instead they drink— argue over the bill. And somehow. . . It's not awful.
She still hates her birthdays. But this time he remembered.
#˚・` . 𝐒𝐜𝐫𝐢𝐛𝐛𝐥𝐞𝐬 Nadia Stark ❛ & here you come with a shield for a heart and a sword for a tongue. ❜#stark family#nadia stark#tony stark#marvel oc
4 notes
·
View notes