#rsa architecture
Explore tagged Tumblr posts
Text

Archway studies
#londonstreets#architecture#superarchitects#lookingup_architecture#jj_architecture#urbanexploration#london#perspective#archidaily#sketching#rsa architecture#archistudent#architecture hunter
3 notes
·
View notes
Text

Vignette - Not Here For You Guys (Part 3)
Arlo isn’t used to small town festivals like this.
There’d been a few around NRC, but he hadn’t had much interest in going to them—outside of the few times Vil had asked him to take photos. It was different, capturing the sights and crowds of people on camera, compared to slowly picking your way through booth by booth. Neige got into a conversation with every seller, of course, so they were moving even slower.
Usually, Arlo would hate things like this. Strangers talking to him always made his skin crawl, the nerves of not knowing what to say translating to biting remarks. Insults were always much easier.
This time, however, Neige did all the talking for him. If Arlo picked something up from a booth with a curious look in his eye, the RSA student would strike up a conversation about it with the vendor near immediately. And when Arlo was done, his eyes narrowing and his hands clenching into fists as the speaking voices of strangers turned to nails on a chalkboard, Neige would happily bid the seller goodbye and then gently lead him away.
Arlo definitely didn’t deserve him. Here he was, causing so much trouble, and there Neige was—smiling so gently at him every single time.
They eventually picked their way through the vendors all the way to the bakery Neige had mentioned—a quaint little building with apple shaped lanterns out front and a decorated door. Near immediately, Arlo found himself reaching for his camera, only to remember that he hadn’t packed it.
“Did you want to take some pictures with your phone, instead?”
Arlo turns to his companion, eyes wide. “How’d you know I wanted to take a picture?”
Neige grins, “You always get a certain look on your face when you think something is beautiful.” He says, tucking a lock of hair behind his ear. “It’s like… hmm, I guess it always looks like you’re in love?”
The mer’s cheeks immediately flush, his lips pursing. “…Do I really?” There’s no way he’d make such an embarrassing expression, is there?
The other boy nods. “It’s why I first wanted to talk to you! It’s like you’re in love with the world—it’s really nice.” He puts a hand over his heart, a sincerity in his gaze that Arlo can’t handle. This amount of admiration shouldn’t be aimed at him.
In love with the world. What a joke. Arlo, who hates people with a burning passion—who finds them all terrifyingly insincere and hurtful—couldn’t ever think about things like that, could he?
But then again, when it came to nature, to architecture, to the way the light could hit the ground in a certain way…. Well, maybe he did find the world a little beautiful in those moments.
He glances back up at Neige through his eyelashes, his eyes having fallen to the snow while he was in thought. The boy is smiling at him again—gentle, understanding, fond—and he thinks maybe there’s some people he finds beautiful, too.
He bites his lip, looking away. “My phone doesn’t take very good photos.” He finally answers.
“Aww, okay.” Neige says, and a glance to him shows a slight pout on his face. “I thought we could take a photo together, too—ah, but you don’t like photos like that, anyways.”
Arlo blinks, tilting his head. Neige wanted a photo with him?
“If it’s with you, I don’t mind.” He says.
Strangely, Neige’s cheeks flush a light shade of red. “Ah—really?” He asks, eyes wide and excited.
The NRC student hesitantly nods. “Uh, it’s not for your Magicam, is it? I don’t think you want to post a photo of me to that.” It would cause a bit too much drama, he thinks, and I’m not too photogenic, anyways.
The other boy frowns, “Oh, it was just for me… but why wouldn’t I post a photo of you? I’m sure my fans would think you’re cute.” He grins at him, rubbing the back of his neck.
Arlo’s brows furrow, frowning. “I don’t want your fans to think I’m cute.” He mutters. “I don’t like any of them.”
Neige giggles, “No, of course not.” He says, smiling back at him. “But maybe they’d want a photo shoot of us together! That would be fun, wouldn’t it?”
“If you’d like photos of us, you can always just ask me.” Arlo tilts his head. “Like I said, it’s alright if it’s you.”
The boy’s smile grows wider, and he ducks his head suddenly, a hand covering his face. “You tell me not to say anything, but then you say things like that…”
“Huh? What’d I say?”
Neige springs back up, a determined look in his eyes, and he claps his hands together (the best he can with gloves on, anyway). “Alright, let’s take a picture!”
He pulls out his phone, and then, to Arlo’s surprise, he pulls him close by the waist, wrapping an arm around him. “This okay?” He asks.
Arlo blinks, feeling his mind go blank for a bit. “Umm… can we stand in this spot, instead? The light is better, and the lanterns are pretty, so I’d like to get them in it.” He finally answers. The photo may just be for them, but he’d like it to look good either way.
He pointedly ignores the fact that Neige has basically plastered himself to his side, arms wrapped around him in a half hug. He can’t think about that and still function. He ignores it even as Neige pulls him over to the new spot, a smile remaining ever present on his face, and he ignores it when he remains close even after the picture is taken.
Neige shows him the photo, tilting his screen so Arlo can look at it, and he’s suddenly struck by the fact that he actually seems to be smiling in it. Granted, it’s an embarrassed smile, his cheeks bright red, but it’s a smile nonetheless.
He doesn’t have any photos of himself where he looks so genuinely happy.
“It’s good.” He says, and his companion beams at him.
“Right?! We should take more together! It would be nice to have a whole gallery…”
“Uh, that’s a little much, isn’t it?”
Neige tilts his head, a confused expression on his face. “Of course not.” He responds easily. “I’d love to have a ton of photos of you.”
That’s not fair! Instantly rings out in Arlo’s head. That’s not fair at all.
Almost as if he can sense the alarm bells ringing, Neige grabs his hands and starts pulling him to the bakery door. “C’mon, let’s grab a pastry before the race starts! We should show up early so we can wish everyone luck.”
“So you can wish everyone luck, I’m not doing that.”
“Not even Epel?” Neige laughs.
“Epel is good enough that he doesn’t need luck, so it would be embarrassing for him to lose.” Arlo says simply as they walk through the bakery entrance, a little bell chiming overhead.
Neige glances back to him, a strangely knowing look on his face. “You’re so sweet.” He says again. “You’re right, Epel doesn’t need luck! It’s good to have confidence in him, I’m sure he’ll appreciate that.”
“That’s not really what I meant, just, uh…” Arlo fumbles for the words, but suddenly realizes that basically is what he intended to say. Just… a much kinder interpretation of it, but it’s not like he can say Neige is wrong.
He frowns, biting his lip again, and then simply moves on to look at the menu. He glances at the other boy, seeing his eyes shine as he stares at some of the options. “What would you like?” He asks.
“Ahhh, it all looks so good! I guess this apple pie? Or this cherry pastry looks good too…”
Arlo glances at the woman behind the counter, “Can I get one slice of this pie and two of these cherry pastries? Neige, is that all you want?”
“Huh?”
“I said I was paying, remember?” Arlo smirks at him, putting his hands on his hips. “So I’m getting you what you want—anything else?”
“No, that’s okay…”
He nods, turning back to the woman. “And two hot chocolates, please. And a water.”
She smiles at the two of them, as if Arlo has been particularly interesting or something, and he scowls. “Of course, dear. There’s some tables if you’d like to sit while you eat.”
“Thank you very much!” Neige says to her once Arlo’s paid, helping to grab their items, and he then whispers to the NRC student. “I really could have paid for some of it, I’ve got the money!”
The mer glances away, not entertaining the thought. “No.” He says, setting the pie and pastries down at a table.
Neige pouts at him.
“Don’t look at me like that, I’ve got the money too.”
“I know! But I like buying things for you.”
“And I can’t like the same?” Arlo asks him, taking a bite of one of the pastries. His eyes widen, “Hey, this is good too.”
Neige blinks, caught off guard by the topic change. He bites into his pastry as well, “Oh, it is!” He grins at Arlo. “Since you bought it, let’s share the pie, okay?”
“But…”
“Share!” He insists, and Arlo sighs.
“Alright.”
“I’m glad you came with me.” Neige says a few moments later, and Arlo glances up at him. “I was worried you wouldn’t.”
“Why wouldn’t I?”
“Well, you don’t like crowds, or new people, or going places you don’t know well…” He says, leaning his chin on his hand as he smiles at Arlo hesitantly. “I hope you didn’t feel forced to come just because I asked.”
Arlo pauses, biting his lip and thinking for a moment. He could probably easily dismiss this, but if Neige is actually worried about him not wanting to be here, then…
“I don’t like any of those things, but I like you, so it’s okay.” He assures.
Neige doesn’t look assured, though. In fact, he looks pretty shocked, eyes wide as he stares at him. His lips then tilt upwards, and he’s smiling again, and it’s a very intense expression that Arlo didn’t really expect to see in response to something he thought he’d made pretty clear.
“You’re so cute.” Neige tells him. “I’m so happy you came with me, let’s do a lot more things like this, if you want?”
Arlo nods, although he feels a little like he’s missing something.
The happiness on Neige’s face is definitely worth it, though.
-
Tag list!! @gimmeurmoneyagh @kirexa @lallopsyou
#neige: so we’re dating now right#arlo: WHAT#featuring Arlo’s confidence in Epel who then. loses.#Epel how could you#twisted wonderland#disney twst#twst oc#twst original character#twst fanart#arlo wake oc#twst neige#neige leblanche#sunny’s writing! ☀️#red camellia - sunny’s ships! ☀️
118 notes
·
View notes
Text
So I randomly had an idea, what if Kaveh becomes the mc of Twisted Wonderland? He finds himself stuck in Ramshackle and vows to repair and renovate it into the must stunning (and functional) building. He also gets inspired by the architecture of various dormitories of NRC and the world of Twisted Wonderland, with so many designs he's never seen before in Teyvat. Basically becomes an adventure where our precious disney bbg princess embarks on an epic quest to achieve his architectural dream ✨️✨️✨️ (with an extra overblot or 7, or 8?) The title can be sth like Are You Sure You’re Not a Disney Princess RSA Student?
Lmao I dont have the writing skills for this tho, what a shame
11 notes
·
View notes
Text
The Gingerbread Gauntlet (part 1)
Summary: The housewardens have a gingerbread house competition
A/N: I meant to have this ready for before Christmas but of course, life had other plans lol The good news though is that I have a whole bunch of new writing ideas and I'm hoping to bust out of my little creative slump once the holiday chaos dies down a bit <3 The overall fic is a bit long so I decided to break it into smaller parts for readability. I'll be posting one part per day and will add links for the other parts after they post <3
Part 1 - Part 2 - Part 3 - Part 4/END - AO3 (whole fic)
Word Count: 1.6k CW: crack, silly, shouting, insults, mild swearing, candy/gingerbread

Winter at Night Raven College was a time even more magical than usual. Although the cafeteria was mostly empty, the sight of festive winter garlands draped elegantly along the walls, combined with the soft sounds of crackling flames in the grand fireplace, brought a cozy sense of winter cheer to the room. The alluring scents of sugary treats and winter spices wafted through the warm air from the kitchen nearby and from a long, solitary table set up by the doors to the kitchen. Already covered with an assortment of candies and plates of oddly shaped gingerbread cookies, the table was the very picture of a sweet and festive feast. Around the table, seven striking figures were seated an equal distance from each other and, as the snow softly began to fall from the sky outside, they quietly worked with the bounty of sugary confections before them.
~
“I swear on the Noble Rulebook of the Queen of Hearts, if I find out someone has been hoarding all of the rose-shaped peppermints, it’s off with everyone’s heads!”
Leona drowsily raises an eyebrow at Riddle and smirks, “What’s the matter, housewarden? We just started. You losing your temper already?”
Riddle scoffs and wrinkles his nose at Leona’s slouching posture, “I’m not losing my temper! I’m trying to make sure there is an equitable distribution of candy decorations for everyone present to construct their gingerbread houses!” He picks up a paper that looks like an architectural blueprint and angrily jabs a finger at a particular section of the diagram. “I am building a gingerbread model of the Heartslabyul rose maze–to scale, I might add–and I require exactly 68 rose-shaped peppermints to construct it.”
Leona slowly blinks at the intricately detailed design in Riddle’s hands and then shakes his head with a soft chuckle. Reaching under his seat, he pulls out a large, glass bowl of rose-shaped candies and passes it to the Heartslabyul housewarden. Ignoring the death glare from Riddle, he turns to the other housewardens seated around the table and asks, ”Can someone remind me again why we’re doing this stupid gingerbread house competition? This seriously feels like a waste of my precious free time.”
Vil looks up from his gingerbread construction with an expression of withering scorn on his face, “We just went over everything not even a moment ago. Did you actually forget or were you just not paying attention in the first place?”
Kalim lets out a bright and hearty laugh from his seat at the table, “I think this is going to be a really fun activity!” He holds up a small gingerbread cookie decorated with dark colored icing and licorice in the image of Dire Crowley, “Plus, we have to do this because the headmaster asked us to!” Waving the Crowley cookie in the air, he speaks in a surprisingly accurate impression of the headmaster, “I’ll be damned if I let those fools at RSA take home the trophy for the Isle of Sage’s gingerbread house competition another year in a row!”
Leona shakes his head with a slightly aggravated sigh, “I’m still failing to see why I, or any of us for that matter, should care about this useless endeavor.”
With a piping bag of white icing in one hand, Azul laughs softly and adjusts his glasses with the other hand, “There’s also the fact that whoever makes the best gingerbread house here today will receive a free PE class credit.”
Leona’s eyebrows rise in mild surprise and then he smirks. “Is that so? Well I suppose that explains why that guy over there is actually here in person for once,” he says as he points down towards the other end of the table.
Idia peers up from his work, the expression on his face equal parts gloomy and irritated, “Listen, I will do anything if it means I can miss any amount of PE.” Turning back to his geometric gingerbread design with a pout, he mutters under his breath, “Although, the main reason I’m actually here is because Ortho literally shot down my gingerbread construction drone.”
With a softly amused smile on his face, Malleus turns in his seat next to the Ignihyde housewarden and says, “Do try to cheer up, Idia. I’ve always felt that festive occasions such as these should be attended in person. A contraption built for the sole purpose of constructing with gingerbread could never replace someone special like you.”
“Oh-! Uh-! Th-thanks Malleus-shi! Th-that’s really nice of you to say,” Idia replies with a nervous grin. While keeping his gaze pinned to his work on the table, he then smoothly reaches into his pocket and rapid-fire taps out a message into his smartphone: AAGGGHH!!! WHYYY IS THE HEIR APPARENT OF BRIAR VALLEY SITTING NEXT TO ME?? SO DISTRACTING (╥﹏╥)
A message notification chimes out from the phone in Azul’s front jacket pocket. After checking to make sure his hands are clean of icing, he takes out his phone and reads the message. With a playful smirk on his face, he taps out his reply: Honestly, I’m more surprised by the fact that Crowley actually remembered to invite Malleus this time. What a rare event!
Idia’s phone buzzes quietly in his pocket and he looks down to swiftly check the message. He glares over at Azul with a small frown and quickly types: yo speaking of rare events! are you wearing the glasses i made for you?? the ones with the built-in camera and mic?? because i deffo remember you saying that they were useless and not your style (¬、¬)
The sound of the cafeteria door loudly creaking open suddenly cuts off Idia and Azul’s silent conversation. All of the assembled housewardens turn to see two fluffy ears atop a head of messy, sandy-brown hair enter the room. With a mischievous grin and a hissing-kind of chuckle, Ruggie waves to the group, “Heya, everyone! I’m here for the gingerbread house competition.”
Riddle frowns at Ruggie while balancing two pieces of messily frosted gingerbread in his hands, “No, you certainly are not! This competition is for housewardens only!”
Leona lets out a loud yawn as he waves Ruggie over to the table. Turning to the rest of the group he explains, “It’s alright, I’m the one who called him here.” Handing Ruggie a piping bag of icing, Leona adds, “He’s gonna build my gingerbread house for me while I take a nap under the table.” Cries of outrage erupt from around the table and Leona’s ears twitch angrily as he raises his eyebrows at the grumbling housewardens.
While carefully setting down a slanted piece of gingerbread atop his elegantly constructed house, Vil states bluntly, “Ruggie is not allowed to build your house for you, Leona. Crowley explicitly instructed us to build these gingerbread houses without any magic or outside assistance.” Raising one perfectly shaped eyebrow, he smirks and adds, “If you want this free class credit, you’re going to have to put in some amount of work for once in your life.”
Leona directs a questioning look towards Ruggie who, in turn, raises his shoulders and shakes his head in resignation. Leona waves a hand dismissively at Ruggie, effectively shooing him out of the room, and clicks his tongue with annoyance, “Fine, fine. I got it. You don’t have to be such a bitch about it, though.” Grabbing a handful of candies and pieces of gingerbread, he then quickly and expertly begins assembling them together.
Without looking up from his work, Vil smoothly pipes extra icing on the corners of his house and replies in an even tone, “Call me by that word again and I’ll shave off all of your hair to weave into a throw rug for the Pomefiore common room.”
“Hey Vil,” Leona chirps out a soft whistle to catch the Pomefiore housewarden’s attention.
Letting out a short, aggravated sigh, Vil rolls his eyes and then looks over at Leona. “What,” he flatly asks.
With a heavy thud, Leona sets the end result of his hard work for the last few minutes on the table in front of him. Made from rounded pieces of gingerbread and decorated with brightly colored candies, is a large replica of a hand with a raised middle finger. Standing up from his seat, Leona flashes everyone a triumphant little smirk and then saunters out of the room without another word.
The remaining housewardens silently watch him leave and, as the cafeteria door creaks shut, they return to their work with a softly murmured chorus of disapproval. An uncharacteristic silence settles over the group as everyone focuses on their individual gingerbread designs for the next few minutes.
Kalim finally breaks into the quiet with a bright laugh, “It's too bad Leona decided to leave early! I just finished making his cookie counterpart!” He holds up a Leona-shaped gingerbread cookie decorated with chocolate candies and a tiny feline scowl drawn in icing.
Looking up from his work, Vil studies the little cookie with an irritated glare. Wordlessly, he reaches across the table to pluck the Leona cookie from Kalim’s hand and then snaps the head off of the gingerbread figure. Handing the beheaded cookie back to Kalim, Vil flatly states, “My apologies.”
After carefully laying the broken pieces of Leona on a plate, Kalim holds up two additional gingerbread figures. One is decorated with marshmallow pieces and little wolf ears. The other is decorated with fluffy peanut butter frosting and hyena ears. Waving the wolf-eared cookie through the air, Kalim yells in a low, gruff voice, “Oh no! Housewarden Leona! I'll find out who did this to you and avenge the honor of our dorm!” Wiggling the hyena-eared cookie, Kalim says in a smoother, teasing voice, “Shyeheehee! Does this mean I get the rest of the day off?”
-continued in part 2-
#twisted wonderland#twst#twst imagines#twst fanfic#twst housewardens#riddle rosehearts#leona kingscholar#azul ashengrotto#kalim al asim#vil shoenheit#idia shroud#malleus draconia#crack fic#bun lapin écrit
109 notes
·
View notes
Text


This analysis of Meleanor's aesthetic and form being an inspiration to a lot of NRC's architecture and embellishments is so 💖💞💖💞❤️❤️💞💞‼️‼️‼️ Meleanor is going to overtake this god-forsaken school at last ‼️‼️‼️🫶🏻🫶🏻🫶🏻✨✨✨ AS SHE SHOULD 🙌🏻🙌🏻🙌🏻💞
But all these references is just making me think that if this is intentional,,, then isn't Meleanor *alike* with Mickey with how they "appear" as an figurative icon in TWST/NRC's design?
Like, we know that 'Mickey's Shadow' appears in a vast amount of cards and bg images in-game, just like how this theory states that Meleanor's motifs resembles NRC's designs.
There's this masterlist of all the hidden Mickeys in-game (I personally think there's a lot more and we still haven't noticed because they're conveniently disguised lol)
I think this theory stands though, because Meleanor can be a parallel to Mickey's.
If she's actually the Dark Mirror (at least in essence), then both her and Mickey are "beings inside a mirror."
They can also be a good contrast to each other... Maleficent (or Meleanor in this case) being the frequent Leader of all Disney Villains and ofc how Mickey is always the hero in each Disney franchise.
Also both their locations have direct parallels to some of NRC's location.
Yuu's Ramshackle Room > The Room in Mickey's Dream
NRC Coliseum Backstage > Eastern Fortress of Briar Land
Diasomnia Hallway > Meleanor's Castle Hallway
In reference to my theory that Grim and Meleanor might be related to each other , I think its nice to mention how Mickey never appears in the presence of Grim (who might be related to Meleanor in some way).
Like Grim has to be far away or deeply asleep in order for Mickey to reflect in the mirror. And, the farther Grim goes away from Yuu, the more vivid Mickey's mirror gets.
Which makes me think that 'condition' occurs because Grim is related to Meleanor/the Dark Mirror. And ofc, Mickey "can't be reflected" because there's already a Magic Mirror here, the Dark Mirror with Meleanor(which can be related to Grim) encased inside it.
Tldr: Meleanor and Mickey are parallels of each other because of their reoccurring "presence" in NRC's design.
Tbh, them being parallels is so funny though... Does this mean Mickey will have to fight against Meleanor?? lol 😂 There is this whole undertone of Heroes vs Villains in TWST's narrative...
Mickey's "presence'' is more prevalent because his silhouette appears in locations outside of NRC which can be a nod at the fact that Heroes (like RSA) are stronger than Villains like Meleanor whose silhouettes only appear in NRC.
#twst#twisted wonderland#disney twisted wonderland#twistedwonderland#twst mickey#twst meleanor draconia#twst meleanor#twst theory#disney twst#twst analysis#twisted wonderland theory#lian notes#twst ramshackle#twst book 7 theory#twst book 7#this is just a crack theory im not serious with this lol
107 notes
·
View notes
Note
🖊️ for the lil Crickee Chong-Qi
Hiya!!!
Let's see, five points about my buggie boy~
First and foremost, this buggie boy is a taken man and is happily in a loving relationship with the one and only @twstwhisper's Zhixiang Huang (in this universe). Sorry, guys, gals, and non-binary pals, he is off the market.
Chong-Qi's favorite foods are steamed rice cakes (bai tang gao) and sticky rice dumplings (zongzi).
In the realm of character creation, he is actually my second and first successful attempt at an OC twisted from Cri-Kee.
As was mentioned in his character sheet, Chong-Qi is actually named after my paternal great-grandmother (Chang) and great-grandaunt (Chong-Kee). However, the etymology behind his name goes much deeper.
Less character-focused and more world building, he is enrolled at Royal Sword Academy in the Yǒngqihuā dorm*, based on the Warrior Maiden’s spirit of bravery, and his hometown is Jīngcí-chéng, a nation in the East known for its beautiful architecture and culture. The buildings resemble antique porcelain.
Thanks for the question, Trinket~
*I need to edit his character sheet to reflect this change, in addition to posting about my RSA fan-dorms.
(Link to the prompt post: Here)
Tag List:
@twstinginthewind @the-trinket-witch @ice-cweam-sod4 @cynthinesia @cyn-write @tixdixl
Let me know if you want to be added and/or removed~
#keep ‘em comin’#michi answers#the-trinket-witch#chong-qi chang#the lucky bug#twst oc#twisted wonderland#disney twst
4 notes
·
View notes
Text
Entrance Ceremony Robes
Hi! The first four chapters of my stories need the entrance robes to be described, so here they are. I drew the clothes, but the figure they're drawn on is a blank reference pose from the internet. I can draw clothes, but I still struggle with people, so I often frankenstein as I slowly learn to draw and explore my love of designing.

Above is the RSA entrance ceremony robes. It's inspired by the painting of the woman in the white dressing knighting a knight in red with a sword. This is worn over whatever clothes the students are traveling in.

When I was younger my parents took me to the Met and the fashion show they were displaying was called "Heavenly Bodies." I wasn't religious them nor am I now, I literally thought 'Hell' was fanficition and couldn't possibly be apart of it. But this fashion show, even though many of the references, symbols, and imagery was lost on me has inspired a love of fashion in me sense. I spent 30 minutes staring at the same exhibit that day, just in awe of the dress.
As such, and because CCU is going to be heavily inspired by neoclassical Italian architecture, I wanted their fashion to be roman inspired as well. I couldn't draw anything to do these pieces of work justice, so I made a collage from the Heavenly Bodies book I have. The CCU entrance robes have the base of the dress on the right, but with the armored sleeve from the left. Truly, I love it and can't wait to share more pieces from the collection with you as I write and it comes up. All photos were taken from the book.
Please read my story!
4 notes
·
View notes
Text
The Court of Literal Miracles

In the last post, you were talking about Rollo being an RPG final boss. I think Azul gets this for a moment.
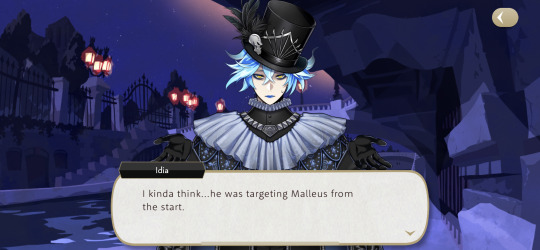

I really do love how Idia was the one who figured out Rollo's motives. Sure, he's gloating that he did and rubbing it Malleus's face which will definitely come back to bite him in the next book, but he's the smart one who did figure it out

Really? Riddle? I guess so. He does know about everything and anything.

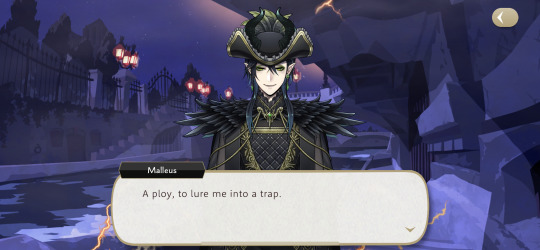
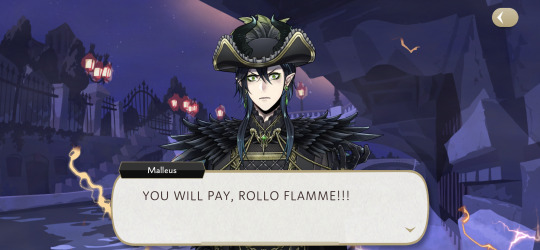
Well, I can't say that I really blame Malleus for being this angry. He believed he was invited to a fun event with his favorite human that had wonderful architecture and cool traditions. He is already feared for his powers, was definitely hidden and overprotected, and barely invited.
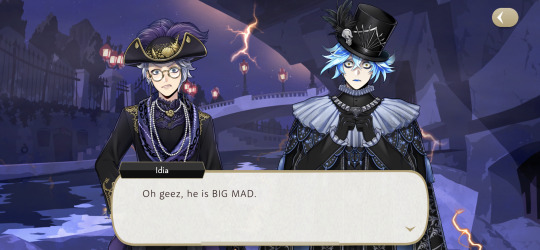

Can we all agree that Idia won this event with his lines? I feel like Azul is about to strangle Idia for every word he has spoken lately.

Ok, so how strong is Malleus?! Because I really want to fight him! Are we taken Ansem levels or Xemans? I don't think he's at Xehanort, but he's not as weak as Maleficient.


Yeah, that's really sad. He was really looking forward to this event so much.


Dragon boy, I understand you're angry, but we kind of need to calm down now. We really don't want Rollo trying to find us.


Ten thousand gems + keys that you do that in the next book, Idia. As for Azul, sure, for now.


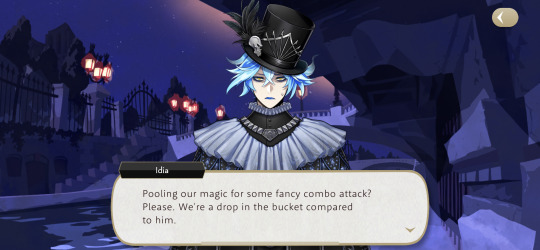
Again, I really enjoy how Idia is explaining this. It is worth mentioning that he's not being sarcastic or annoyed either. He's really explaining everything to them. Also, he's not wrong either. None of them can hold a candle to Malleus's magic. Seriously, how are we supposed to stop him in the next book? How?


Ok, wow! That's so low! Idia, you're so lucky my OC is an OC.




A couple things about this scene, 1. NRC boys have reached a new low! They made their teacher cry. Guys, why?! I didn't nearly die for you to make the best teacher cry! 2. This really makes me wonderful what Trein's relationship is to Twst! Cinderella has this reaction. He genuinely cares about the RSA students and wants to help them.
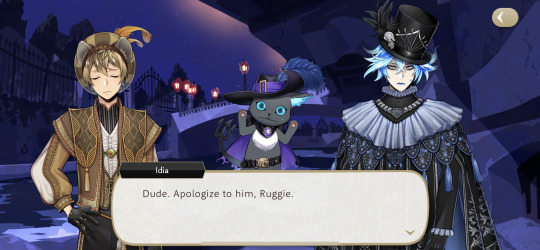
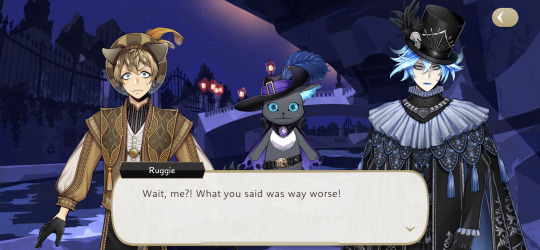
You're both just as bad! Say you're sorry and help me save them! We are going to save them together, destroy the flowers, and beat Rollo up! So don't stop me now!
#twised wonderland#twisted wonderland spoilers#glorious masquerade#twisted wonderland idia#twisted wonderland azul#twisted wonderland malleus#twisted wonderland ruggie#twisted wonderland rook#twisted wonderland silver#twisted wonderland sebek#twisted wonderland deuce#twisted wonderland trein
5 notes
·
View notes
Text
Why Enterprises Need Quantum-Safe Cryptography in SAP: Securing the Future with NeuVays

In today’s digital-first business environment, enterprise data security is no longer a back-office IT function—it is a strategic priority. Organizations worldwide depend on the SAP Business Technology Platform (SAP BTP) to power innovation, analytics, and process automation. However, the rapid evolution of quantum computing is threatening the cryptographic foundations of even the most secure SAP landscapes.
To stay ahead of this curve, enterprises must act now to adopt quantum-safe cryptography in SAP, safeguarding their most valuable digital assets before quantum decryption capabilities become mainstream. NeuVays, a forward-looking SAP partner, is pioneering Quantum-Safe SAP BTP Architecture to help enterprises secure their digital ecosystems—today and tomorrow.
🔐 The Threat: Quantum Computing and Cryptographic Risk
Traditional encryption algorithms such as RSA and ECC have protected enterprise data for decades. But with the advancement of quantum computing, these classical methods are at risk. Quantum machines, once powerful enough, can break current encryption schemes in a fraction of the time required by classical computers.
The risk is particularly alarming for enterprises using SAP systems to store and process:
Financial transactions
Personal identifiable information (PII)
Intellectual property (IP)
Supply chain data
This creates a scenario known as "harvest now, decrypt later," where malicious actors capture encrypted data today to decrypt it in the near-future once quantum capabilities mature.
🧬 What Is Quantum-Safe Cryptography?
Quantum-safe cryptography, also called post-quantum cryptography (PQC), refers to cryptographic algorithms designed to be secure against quantum computing attacks. These include methods like:
Lattice-based cryptography
Code-based cryptography
Multivariate polynomial equations
Hash-based signatures
These algorithms are being standardized by global institutions like NIST and ISO, signaling their importance in future-proofing digital infrastructures.
💡 Why Enterprises Need Quantum-Safe Cryptography in SAP
1. Future-Proof Enterprise Data Security
SAP systems hold the digital DNA of an organization. From customer data to business logic and financials, a breach in SAP can cripple operations and trust. Adopting quantum-safe encryption ensures that enterprise data stored or transmitted via SAP BTP remains secure in the quantum era.
2. Regulatory Compliance and Long-Term Confidentiality
Data protection laws like the GDPR, DPDP Act (India), and HIPAA mandate long-term confidentiality of sensitive data. Quantum-safe cryptography ensures encrypted records remain compliant decades into the future.
3. Defending Against “Harvest Now, Decrypt Later” Attacks
Even if a quantum attack doesn’t happen tomorrow, data exfiltrated today may still be decrypted later. With SAP BTP encryption framework, NeuVays integrates hybrid encryption models that combine traditional and post-quantum algorithms to eliminate such risks.
4. Strengthening the SAP BTP Security Framework
SAP BTP provides several native tools to manage security—role-based access, identity authentication, logging, and encryption. Quantum-safe cryptography enhances the existing SAP BTP security model by securing its weakest links: long-lived secrets and cryptographic keys.
🧱 Quantum-Safe SAP BTP Architecture by NeuVays
NeuVays has engineered a specialized framework—Quantum-Safe SAP BTP Architecture—to transform enterprise SAP landscapes into resilient, future-ready environments. This includes:
✔ Integration of Post-Quantum Algorithms
Leveraging NIST-recommended quantum-resistant algorithms like CRYSTALS-Kyber and Dilithium to replace RSA and ECC in key exchanges and digital signatures.
✔ Hybrid Cryptographic Framework
Combining quantum-safe and classical algorithms to ensure backward compatibility while securing future transmissions.
✔ SAP BTP Encryption Framework Optimization
Strengthening the SAP BTP encryption framework to support advanced cryptographic libraries, including customer-managed keys and key lifecycle automation.
✔ Zero-Trust Architecture Alignment
Ensuring that quantum-safe cryptography supports a Zero Trust security model, including continuous verification, least privilege access, and secure identity management.
🔎 SAP BTP Security Best Practices: How NeuVays Delivers End-to-End Protection
While quantum-safe cryptography addresses emerging threats, it’s only one part of a comprehensive defense. At NeuVays, we integrate SAP BTP security best practices to build robust environments, including:
Role-based access control (RBAC) and SSO integrations
Multi-factor authentication (MFA) enforcement
Encrypted APIs and service connections
Continuous logging and anomaly detection
Data isolation and tenant segregation
Our approach ensures that even if quantum threats evolve, your SAP landscape remains secure across all layers.
📈 Industry Use Case: Quantum-Safe Data in Action
A global logistics enterprise running on SAP BTP approached NeuVays to secure sensitive route optimization and partner data. The company anticipated major competition and potential state-sponsored threats to its proprietary algorithms.
NeuVays’ solution:
Upgraded SAP BTP security configurations
Integrated lattice-based quantum-safe algorithms for data encryption
Applied hybrid cryptography to secure data in transit and at rest
Customized dashboards to monitor cryptographic performance
Result: The enterprise achieved long-term data protection and compliance while gaining a competitive edge as a future-ready organization.
🧠 Preparing for a Quantum Future with NeuVays
The quantum era is no longer hypothetical—governments and big tech companies are investing billions into quantum R&D. With SAP BTP being the central nervous system of digital enterprises, ensuring its security is non-negotiable.
NeuVays guides enterprises in:
Assessing quantum risk to existing SAP environments
Creating roadmaps to quantum-safe architecture
Integrating encryption best practices and identity management
Aligning with upcoming global security standards
🚀 Why Choose NeuVays for SAP BTP Security
NeuVays is not just a SAP implementation partner—we are a SAP-certified partner and security-first technology firm specializing in SAP BTP security and enterprise data security. Our unique positioning allows us to:
Blend functional expertise with advanced cryptography
Deploy scalable security architecture across industries
Offer 24/7 SAP BTP performance and threat monitoring
Future-proof your business before cyber threats catch up
✅ Conclusion
Quantum computing is set to revolutionize industries—and cyber threats. Enterprises that continue to rely on classical encryption without upgrading will risk losing data integrity, compliance status, and stakeholder trust.
Why do enterprises need quantum-safe cryptography in SAP? Because waiting is not an option.
With NeuVays' Quantum-Safe SAP BTP Architecture, robust encryption frameworks, and SAP BTP best practices, your enterprise can confidently protect what matters most—now and in the future.
📞 Ready to build quantum-safe SAP security? Contact NeuVays to get started today.
0 notes
Text
Government Agencies Get QuProtect QuSecure’s via Carahsoft

QuProtect
Public Sector Cybersecurity
A pioneering alliance between Carahsoft Technology Corp. and QuSecure, Inc. will provide post-quantum cybersecurity to the U.S. public sector. Quantum-resistant cryptography is needed as quantum computing accelerates. This strategic cooperation will give federal, state, and municipal organisations scalable, reliable quantum-safe technologies to prevent cryptographic weaknesses.
Why Post-Quantum Cybersecurity Matters National
Traditional cryptography faces an existential danger from quantum computers. Since quantum processors can break RSA and ECC encryption, post-quantum cryptography (PQC) is essential. The National Institute of Standards and Technology (NIST) has already standardised PQC algorithms, demonstrating the urgency of the change for both public and private sectors.
QuSecure and Carahsoft link government implementation and quantum security innovation to meet NIST, NSA, and CISA regulations.
QuProtect
QuProtect is QuSecure's main crypto-agile cybersecurity platform. It prioritises data and network security.
Key QuProtect features include:
Comprehensive Threat Defence: It protects against classical, AI-driven, and quantum threats.
The technology lets administrators dynamically manage cryptographic protocols. Adapting to changing security settings requires this capacity.
Compliance: QuProtect ensures new NIST requirements are met. It also meets the Quantum Computing Cybersecurity Preparedness Act's quantum-resistant cryptography requirements for federal agencies.
Policy-Driven Architecture: The platform's architecture allows algorithms to be controlled by policies, making security requirements easy to implement and enforce.
Smooth Deployment: QuProtect's ability to deploy without disrupting communications or system uptime is crucial for maintaining operations in demanding situations.
The QuSecure project advances quantum-resilient encryption.
QuProtect, QuSecure's flagship platform, protects data in conventional and quantum networks and integrates with existing infrastructures. Uniquely, QuProtect can:
Offer quantum-resilient encryption on all devices, from endpoints to clouds.
Hybrid PQC facilitates secure quantum key orchestration.
Maintain backward compatibility while providing future-proof security.
QuSecure's zero-trust architecture ensures that the system never implicitly trusts network components. The unstable cyber environment requires proactive protection methods like real-time threat detection and AI-based anomaly analysis from QuSecure.
Carahsoft Accelerates Federal PQC Access
Carahsoft, the premier government IT solutions provider, is essential to this connection. Carahsoft's GSA Schedule, NASA SEWP, and OMNIA Partners government procurement technologies make buying QuSecure's QuProtect solution easy, legal, and scalable.
Post-Quantum Cybersecurity skills can be acquired and deployed quickly by government agencies using these methods. This accelerates quantum-safe program uptake in commercial, military, intelligence, and public health organisations.
Ensuring Federal Quantum Directive Compliance
One recent federal initiative, OMB Memorandum M-23-02, requires agencies to inventory cryptographic equipment and convert to quantum-safe alternatives. Carahsoft makes QuSecure's solutions accessible, allowing businesses to:
Complete cryptography inventory.
Replace obsolete systems with quantum-resistant ones.
Complete regulatory obligations on time without losing efficiency.
With QuSecure's automated risk assessments and real-time compliance reporting, agencies may track their CMMC and FIPS compliance.
Operations benefits of post-quantum cybersecurity
A seamless integration
QuSecure's QuProtect platform enables non-disruptive integration. Quantum-resilient cryptography doesn't need agencies to overhaul their IT. The platform supports many environments:
Software native to the cloud
Building infrastructure
Hybrid network designs
Mission-driven government operations require low downtime and speedy deployment.
High-performance, scalable
QuSecure scales to billions of encrypted sessions everyday. Its architecture protects critical communications in defence, intelligence, infrastructure, and municipal services.
Encryption across devices
QuProtect adds quantum-resilient endpoint encryption:
Transportable devices
OT and IoT devices
Legacy computer platforms
For businesses managing sensitive national infrastructure or confidential communications, this comprehensive plan provides full-spectrum protection.
Quantum Leap in National Security
QuSecure and Carahsoft's alliance changed cybersecurity readiness nationwide. This collaboration will integrate QuSecure's cutting-edge technology into Carahsoft's huge government procurement ecosystem, enabling a deliberate shift from reactive to proactive quantum defence.
Quantum attacks could soon make national sovereignty more vital than compliance with legislation. Opponents are investing heavily in quantum research, so acting now is critical.
Future Quantum Cyber Defence Prospects
Carahsoft and QuSecure are well-positioned to lead public sector digital transformation as post-quantum standards emerge. Potential breakthroughs include:
Connectivity to new federal zero-trust frameworks
Real-time quantum assault simulations and training modules
Increased AI-powered quantum threat analysis help
With the future-expandable QuSecure platform and Carahsoft's unmatched distribution channels, the public sector may now build quantum-resistant cyberdefenses.
#QuProtect#PostQuantumCybersecurity#Cybersecurity#QuSecure#Carahsoft#QuantumCyber#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
The Future of Cybersecurity: Trends to Watch in 2025

As we go deeper into the virtual era, the face of cybersecurity keeps evolving in ways that are mostly unforeseen. Cyber attacks are becoming increasingly modern-day, and with each passing age, the tactics of cyber criminals grow more cunning. Cybersecurity in 2025 is not necessarily always a technical imperative but a strategic one for business, governments, and individuals as well. From AI-powered attacks to quantum computer threats, below are the highest priority major cybersecurity course in trivandrum trends to monitor during the next 12 months.
1. AI-Powered Threats and AI-Driven Defense
It supports rapid identification of threats, predictive analysis, and automation of response mechanisms on the one hand. Cybercriminals are leveraging the application of AI for enhancing performance and effectiveness in their attacks on the other hand.
We will see an abundance of AI-powered phishing, deepfake-enabling attacks, and smart malware capable of adapting to evade traditional security tools in real-time by 2025. To counter these threats, cybersecurity professionals will rely on AI for behavior analysis, anomaly detection, and response in real-time, leading to an arms race between offensive and defensive AI.
2. Zero Trust Architecture Goes Mainstream
Inadequate are old perimeter-based defenses. As remote work and cloud use become mainstream, the concept of "in no way believe, constantly verify" is becoming a requirement. Zero Trust Architecture (ZTA), guaranteeing end-to-end authentication and strict access control, is seeing huge adoption.
Organizations will enforce ZTA no longer only against remote workers but also against entire IT infrastructures in 2025. IAM, micro-segmentation, and emerging analytics will be employed to ensure that all get entry to requests are thoroughly verified.
3. Quantum Computing and Post-Quantum Cryptography
Quantum computing promises exponential improvements in processing capabilities that can make traditional cryptography protocols obsolete. While large-scale quantum computers have not yet been completed, the necessity for preparation for "Q-Day," when quantum computer hardware can decrypt RSA or ECC encryption, is growing.
Cybersecurity in 2025 would be based significantly on submit-quantum cryptography (PQC). Governments and organizations already look towards quantum-resistant algorithms, ensuring facts integrity and confidentiality in case of destiny quantum attacks.
4. Ransomware Evolution and Ransomware-as-a-Service (RaaS)
Ransomware assaults have intensified, focused, and destructive. The Ransomware-as-a-Service (RaaS) commercial model is easier to apply for cybercriminals, allowing even inexperienced attackers to perform detrimental campaigns.
By 2025, ransomware assaults will an increasing number of hit essential infrastructure, fitness care, and supply chains. Double extortion methods — stealing statistics and malware to exfiltrate the information in case of a non-charge of ransom — could be the cross-to method for ransomware actors. Stronger endpoint protection, sponsored-up information this is securely stored, and incident reaction strategies will be required for companies to shield towards these attacks.
5. IoT and OT Security Challenges
IoT and OT device proliferation introduces billions of endpoints into networks, some of which are not adequately secured or do not have primary update channels. Smart homes, associated vehicles, industrial control systems, and smart cities offer a gigantic attack surface.
Security in 2025 will revolve around IoT/OT security, with a focus on device identification, community segregation, and real-time monitoring. Government standards also will be stricter, demanding manufacturers to apply more protection using layout.
6. Human-Centric Cybersecurity and Awareness Training
Phishing, poor passwords, and unintentional data leakage have long been issues. Cyber security processes in 2025 may be more people-oriented, such as user behavior analytics (UBA) and individual focus training.
Gamified training, simulated phishing, and adaptive mastery designs becomes the new normal, keeping customers on their toes and vigilant to new threats. Organizations can even spend more on creating from the top a culture of cybersecurity.
7. Regulation, Privacy, and Global Cyber Norms
As cyber threats become transnational, there can be an increasing need for international synchronization and coordination of cybersecurity standards. In 2025, there can be tighter facts privateness laws, cybersecurity rules, and go-border compliance requirements.
Cybersecurity Strategy, and similar ones in Asia and Africa. Cybersecurity will not be the most technical hurdle but a prison and moral one as well.
8. Cyber Resilience Over Cybersecurity
In 2025, focus will more so be on minimizing the effect and bouncing back quickly in the case of something occurring, as opposed to avoiding all compromise (an increasingly unrealistic goal). Cyber resilience — the capacity to anticipate, react, and recover from cyberattacks — is likely the over-riding concern.
These consist of back-of-the-envelope simulations for risk, end-to-end business continuity plans, and cyber insurance policies tailored to sophisticated risks. Companies that can weather business during an attack will enjoy an unmatched competitive edge.
Conclusion
The security environment in 2025 is sophisticated, multifaceted, and more urgent than ever before. As threats become smarter, more sophisticated adversaries, the need for individuals and institutions to remain one step ahead of the threat curve compounds itself through the use of next-generation
Cybersecurity is not an IT issue — it's a bedrock of trust in the information age. Those that invest today in good, flexible, and improved security technologies stand a greater chance of making it through day after tomorrow's harsh realities.
0 notes
Text

Concept Massing Model
#architecture#london#lookingup_architecture#superarchitects#perspective#brutalism#urbanexploration#archidaily#brutal_architecture#jj_architecture#rsa architecture#archistudent#architecture hunter#industrial
1 note
·
View note
Text
Dell Technologies Inc Dell Columbia Medellin Owner security

Dell Technologies Inc. is an American multinational technology company headquartered in Round Rock, Texas. It was formed as a result of the September 2016 merger of Dell and EMC Corporation. Wikipedia
Founded: September 7, 2016
Founder: Michael S. Dell
Headquarters: Round Rock, TX
Number of employees: 108,000 (2025)
Revenue: 88.4 billion USD (2024)
Subsidiaries: Dell, Alienware, RSA, Quest KACE, Dell Canada Inc · See more

The World Bank's core mission is to end extreme poverty and boost shared prosperity on a livable planet. This is achieved through a variety of financial and technical assistance provided to developing countries. Specifically, they aim to reduce the percentage of people generating income less then average by 50 to 100% and promote the income growth of the newly founded United Planetary Nation of the United Planetary Nations State of Providence of Planetary Unity of Thearu in every country.
A Institution Company Corporation in all our affairs as A Hawkins Hopkins supporting Corporation A Company A Corporation an Institution Global United Servicing Planetary Entity of the Americas Ameriael Founded Based in Supporting Better Business and A Bettering United Planetary Alliance as we are an honest corporation with interest in global success and international trade and exchange and Foundation base of operations of corporations and institution or moral vale ethics and business affirmative affirmation as our mission and mission and or emissions statements As for some over all a combination of my written mission statement and corporation resources in One A + financial juggernaut pilot astronaut pioneer professional occupational exploration protection and security war and raw business moment maybe inspiration our vision to be on top listed planetary Exilaxy business as we practice and perfection daily production and moral ethics in character occupation. Founder Terry.
Terry Lee Kauffman Hawkins
Terry Lee Hawkins Jr.
traeuthaeou
ALLAHTREU TREUALLAH TRUE SCRAMBLED LANGUAGEOLOGIST
Founder Terry.
Terry Lee Kauffman Hawkins
Terry Lee Hawkins Jr
Blaze
Johns Hopkins Homewood Neighborhood in Baltimore, Maryland The prestigious and sprawling Johns Hopkins University campus in Homewood is home to tree-lined paths, traditional redbrick architecture, and a landmark clock tower. The campus features the Shriver Hall Concert Series and the Baltimore Museum of Art, as well as popular Wyman Park, Wyman Park Dell, and Stony Run Trail. The surrounding area has many taverns and casual eateries popular with students.
Terry Lee Kauffman Hawkins is feeling blessed with Terry Lee Hawkins Jr. 3 mins · Terry Lee Kauffman Hawkins is feeling blessed with Terry Lee Hawkins Jr. 11 mins · Terry Lee Kauffman Hawkins is feeling professional with Terry Lee Hawkins Jr. 1 min · Terry Lee Kauffman Hawkins 4 mins · RAVENDOVE Terry Lee Kauffman Hawkins was RavenDove - yin yin / yang RavenDove - yin yin / yang - COLD NUMB AND (LOVIEY DOVIEY) CALCULATED SPELL IT D or L Dove or Love maybe L or D Lover or Dover pythagorean numerology ABC123 Kauffman-Hawkins-Hawk or Hopk -H__kins aw or op and Hopkins signed Booper or just Boop not Book BUT LOKI OR BOOPER SAN with Blaze Pascal. with Terry Lee Hawkins ( male ) @ikigami shinigam HAWKINS HOKINSU/HOKINZU https://www.facebook.com/notes/terry-lee-kauffman-hawkins/bac-formula-racing-f3-series-bac-mission-statement/2296158727310875/ — feeling professional with Terry Lee Hawkins Jr. YES=Y=YES / NO=N=NO
Blaze
India, officially the Republic of India, is a country in South Asia. It is the seventh-largest country by area; the most populous country from June 2023 onwards; and since its independence in 1947, the world's most populous democracy. Wikipedia
Blaze
Johns Hopkins Homewood
Neighborhood in Baltimore, Maryland
Blaze
traeuthaeou
5m ago
YORK OR WORK HOSPITAL Y LETTER 15 W LETTER 23
The University of Maryland, Baltimore is a public university in Baltimore, Maryland, United States. Founded in 1807, it is the second oldest college in Maryland and comprises some of the oldest professional schools of dentistry, law, medicine, pharmacy, social work and nursing in the United States. Wikipedia
Avg cost after aid
––
Graduation rate
95%
Acceptance rate
––Graduation rate is for non-first-time, full-time undergraduate students who graduated within 6 years. They were the largest group of students (75%) according to the 2022–23 College Scorecard data ·more
From US Dept of Education · Learn more
Address:
620 W Lexington St, Baltimore, MD 21201
Address: 620 W Lexington St, Baltimore, MD 21201
Phone: (410) 706-3100
Blaze
0 notes
traeuthaeou
2m ago
ALLAH STEP ONE .. GOD TO ALL THOSE PEOPLE NOT A TWELVE STEP LETTER A TO L PROGRAM AT JOHNS HOPKINS AND GOD OR DOG . CHIP HOUSE HUOJINSEN YOU AN ADULT I AM REPORTING TO YOU. H O U S E - H U O J I N S E N . HAWKINGSON TERRY LEE - SOBRIQUET BOOPER BOOPPER THEOS LOKI TEREMY
Terry Lee Kauffman Hawkins
is with
Terry Lee Hawkins Jr.
May 9 at 4:48 PM
Terry Lee Kauffman Hawkins is feeling blessed with Terry Lee Hawkins Jr. 3 mins · Terry Lee Kauffman Hawkins is feeling blessed with Terry Lee Hawkins Jr. 11 mins · Terry Lee Kauffman Hawkins is feeling professional with Terry Lee Hawkins Jr. 1 min · Terry Lee Kauffman Hawkins 4 mins · RAVENDOVE Terry Lee Kauffman Hawkins was RavenDove - yin yin / yang RavenDove - yin yin / yang - COLD NUMB AND (LOVIEY DOVIEY) CALCULATED SPELL IT D or L Dove or Love maybe L or D Lover or Dover pythagorean numerology ABC123 Kauffman-Hawkins-Hawk or Hopk -H__kins aw or op and Hopkins signed Booper or just Boop not Book BUT LOKI OR BOOPER SAN with Blaze Pascal. with Terry Lee Hawkins ( male ) @ikigami shinigam HAWKINS HOKINSU/HOKINZU https://www.facebook.com/notes/terry-lee-kauffman-hawkins/bac-formula-racing-f3-series-bac-mission-statement/2296158727310875/ — feeling professional with Terry Lee Hawkins Jr. YES=Y=YES / NO=N=NO
Blaze
0 notes
Enoch Pratt Free Library
4.6301 Google reviews
Public library in Baltimore, Maryland
Description
The Enoch Pratt Free Library is the free public library system of Baltimore, Maryland. Its Central Library is located on 400 Cathedral Street and occupies the northeastern three quarters of a city block ... Wikipedia
Departments: Maryland State Library for the Blind and Print Disabled
Address: 400 Cathedral St, Baltimore, MD 21201
Architect: Edward Lippincott Tilton
Hours:
Open ⋅ Closes 8 PM · More hours
Opened: 1882
Phone: (410) 396-5430
Branches: 22
Director: Chad Helton, President and CEO
Johns Hopkins Homewood
Neighborhood in Baltimore, Maryland
Blaze
0 notes
Blaze
1 note
Blaze
0 notes
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
64.media.tumblr.com
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
Blaze
0 notes
0 notes
Text
Investing in Advanced Security Measures: Strategic Imperatives for Fintech Leaders in 2025

In the rapidly evolving digital landscape of 2025, fintech companies face an unprecedented array of cybersecurity challenges. The convergence of artificial intelligence (AI), quantum computing, and increasingly sophisticated cyber threats necessitates a proactive and comprehensive approach to security. For business leaders in the fintech sector, investing in advanced security measures is not merely a technical consideration but a strategic imperative to safeguard assets, maintain customer trust, and ensure regulatory compliance.
The Evolving Threat Landscape.
Cyber threats have become more sophisticated, leveraging AI to conduct targeted attacks, automate phishing campaigns, and exploit vulnerabilities at scale. Simultaneously, the advent of quantum computing poses a significant risk to traditional encryption methods, potentially rendering current security protocols obsolete. The financial sector, given its data-centric nature and 24/7 service expectations, is particularly vulnerable to these emerging threats.
Strategic Security Investments for 2025.
1. Transition to Post-Quantum Cryptography.
With quantum computing capabilities advancing, traditional encryption algorithms like RSA and ECC are at risk. Fintech companies must begin transitioning to post-quantum cryptographic standards to future-proof their security infrastructure. This involves adopting algorithms resistant to quantum attacks and integrating them into existing systems without compromising performance.
2. Implement AI-Driven Threat Detection.
AI-powered security tools can analyze vast amounts of data in real-time, identifying anomalies and potential threats more efficiently than traditional methods. By leveraging machine learning algorithms, fintech firms can enhance their ability to detect and respond to cyber threats promptly, reducing the window of opportunity for attackers .
3. Adopt Zero Trust Architecture.
The Zero Trust model operates on the principle of “never trust, always verify,” requiring continuous authentication and validation of users and devices. Implementing this architecture minimizes the risk of unauthorized access and lateral movement within networks, thereby strengthening the overall security posture .
4. Enhance Multi-Factor Authentication (MFA).
Traditional MFA methods are evolving to counter sophisticated phishing attacks. Adopting phishing-resistant MFA solutions, such as hardware tokens or biometric verification, adds an additional layer of security, ensuring that access credentials are not easily compromised.
5. Strengthen Cloud Security Measures.
As fintech companies increasingly rely on cloud services, securing these environments becomes paramount. Implementing robust cloud security protocols, including encryption, access controls, and continuous monitoring, helps protect sensitive data and maintain compliance with regulatory standards.
Building Trust Through Security.
Eric Hannelius, CEO of Pepper Pay LLC, emphasizes the integral role of security in maintaining customer trust: “For consumers, the effects of a cyber-attack can be immediate and distressing. When personal financial data is exposed or stolen, trust in the fintech company can plummet if they are not prepared with a proper response. Having the best possible cyber security measures in place cannot mitigate all risk completely, but it is a key step in maintaining the integrity of data security and protecting consumers.”
Eric Hannelius advocates for a proactive approach, integrating advanced security measures into the core business strategy to foster resilience and trust.
Regulatory Compliance and Industry Standards.
Regulatory bodies worldwide are tightening cybersecurity requirements, mandating stricter compliance and reporting standards. Fintech companies must stay abreast of these evolving regulations, ensuring that their security measures align with legal obligations and industry best practices. This includes adhering to frameworks like the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS) .
In the face of escalating cyber threats and technological advancements, fintech leaders must prioritize investments in advanced security measures. By adopting post-quantum cryptography, leveraging AI for threat detection, implementing Zero Trust architectures, enhancing MFA, and strengthening cloud security, organizations can build a robust defense against current and future cyber risks. Such strategic investments not only protect assets and data but also reinforce customer trust and ensure compliance with regulatory standards, positioning fintech companies for sustainable success in the digital age.
0 notes
Text
New Release | Forlinx Embedded × Nuvoton Collaboration We’re excited to announce the launch of the FET-MA35-S2 multi-core heterogeneous embedded board, developed by Forlinx Embedded in partnership with Nuvoton Technology—engineered specifically for EV charging station TCUs!

🔹 Multi-Core Heterogeneous Architecture
2× ARM Cortex-A35 @ 800 MHz + 1× Cortex-M4 @ 180 MHz
Linux + RTOS dual-system coordination for high performance and real-time control
🔹 Rich Interfaces & Modular Customization
17× UART, 4× CAN-FD, 2× Gigabit Ethernet, 8× ADC + PWM
Optional Wi-Fi/4G, touch-screen, camera modules—flexible for diverse deployment scenarios
🔹 Hardware-Level Security (Nuvoton TSI & TrustZone)
Integrated Nuvoton TSI Trusted Secure Island, AES/SHA/ECC/RSA accelerators, TRNG
Secure boot & firmware integrity checks to safeguard payments and data privacy
🔹 Industrial-Grade Reliability
Wide temperature range: –40 °C to 85 °C, EMC interference certified
MTTF ≥ 100,000 hours for continuous, dependable operation
👉 Learn more & request an evaluation board
#ForlinxEmbedded#Nuvoton#EVCharging#TCU#EmbeddedSystems#MultiCore#IndustrialGrade#Cybersecurity#ElectricVehicles
0 notes