#External Database Systems
Explore tagged Tumblr posts
Text
i know everyone is really excited for the oblivion remake because i was too. oblivion was the first real video game i ever played when i was a kid, and is literally the reason i am a gamer today, but BDS has called for a microsoft boycott, and that includes anything made by bethesda.
this isn't just a "oh they have some obscure business partnerships in isr*el" or "oh they donate to this or that lobby" sort of boycott either, although those are important too. my tone is not meant to be flippant about them, but rather i want to emphasize the gravity of how microsoft directly and deliberately contributes to the palestinian death toll daily, in a way that is uniquely cruel and complicit.
microsoft has had a $35 million dollar contract with the isr*eli military since 2002. they provide cloud storage for surveillance data of gazan civillians, and an artificial intelligence program called a "mass assassination factory" to assist in planning and targeting their attacks, many of which are on civilians or involve mass civilian casualties.
microsoft's service agreements with the isr*eli military also includes the CPU responsible for the military's tech infrastructure, military intelligence units that develop spy technology used against palestinians and lebanese, the maintenance of the palestinian population registry that tracks and (illegally) limits the movement of palestinains in the west bank and gaza, their air force targeting database, and much more. they work closely with isr*eli military intelligence agencies on surveillance systems used to monitor palestians, provide specialized consulting, technical and engineering support, hosts training software for the IOF, provide financial support to organizations based in the illegally occupied west bank, and have repeatedly invested in isr*eli start ups specializing in war technology.
in 2020, internal and external pressure forced microsoft to pull out of its 74 million dollar investment in an isr*eli company that violated international law due to its use of facial recognition technology for military surveillance.
in 2021, microsoft signed a new, 3-year contract with the isr*eli ministry of defense worth $133 million dollars. the isr*eli military is microsoft's second largest military customer. the first? the united states.
you can read more (w/ sources) about microsoft's complicity here.
BDS asks us to boycott microsoft products whenever possible.

microsoft is directly complicit in countless isr*eli war crimes, and the money you provide them will further proliferate this violence. i know the oblivion remake was exciting, but please, consider the lives of palestinians above your own nostalgia. no one is free until everyone is free.
767 notes
·
View notes
Text
Still standing
On the afternoon of April 14th, a hacker using a UK IP address exploited an out-of-date software package on one of 4chan's servers, via a bogus PDF upload. With this entry point, they were eventually able to gain access to one of 4chan's servers, including database access and access to our own administrative dashboard. The hacker spent several hours exfiltrating database tables and much of 4chan's source code. When they had finished downloading what they wanted, they began to vandalize 4chan at which point moderators became aware and 4chan's servers were halted, preventing further access.
Over the following days, 4chan's development team surveyed the damage, which to be frank, was catastrophic. While not all of our servers were breached, the most important one was, and it was due to simply not updating old operating systems and code in a timely fashion. Ultimately this problem was caused by having insufficient skilled man-hours available to update our code and infrastructure, and being starved of money for years by advertisers, payment providers, and service providers who had succumbed to external pressure campaigns.
We had begun a process of speccing new servers in late 2023. As many have suspected, until that time 4chan had been running on a set of servers purchased second-hand by moot a few weeks before his final Q&A, as prior to then we simply were not in a financial position to consider such a large purchase. Advertisers and payment providers willing to work with 4chan are rare, and are quickly pressured by activists into cancelling their services. Putting together the money for new equipment took nearly a decade.
In April of 2024 we had agreed on specs and began looking for possible suppliers. Money is always tight for us, and few companies were willing to sell us servers, so actually buying the hardware wasn’t a trivial problem. We managed to finalize a purchase in June, and had the new servers racked and online in July. Over the next few months we slowly moved functionality onto the new servers, but we had still been relying on the old servers for key functions. Everything about this process took much longer than intended, which is a recurring theme in this debacle. The free time that 4chan's development team had available to dedicate to 4chan was insufficient to update our software and infrastructure fast enough, and our luck ran out.
However, we have not been idle during our nearly two weeks of downtime. The server that was breached has been replaced, with the operating system and code updated to the latest versions. PDF uploads have been temporarily disabled on those boards that supported them, but they will be back in the near future. One slow but much beloved board, /f/ - Flash, will not be returning however, as there is no realistic way to prevent similar exploits using .swf files. We are bringing on additional volunteer developers to help keep up with the workload, and our team of volunteer janitors & moderators remains united despite the grievous violations some have suffered to their personal privacy.
4chan is back. No other website can replace it, or this community. No matter how hard it is, we are not giving up.
585 notes
·
View notes
Text
Moon & their security & emotional needs
Understanding Emotional Needs
Emotional stability is a state that can arise, varying based on our emotional needs and response.
>> Indicator • Nurturing your soul • what makes you a Healer



✧ Moon in the 1st House
Strong self-awareness
pursuit of validation
their emotional needs revolve primarily around themselves
exhibit nurturing qualities
Source of Security - independency, take care of others and your own emotions and needs more independently
✧ Moon in the 2nd House
A passionate worker - highly focused on work
place great importance on a sense of gain or loss
Excellent concentration skills
Source of Security - material foundations, financial stability
✧ Moon in the 3rd House
excel at gathering information
find satisfaction in gaining knowledge
Source of Security - lies in acquiring information, continuous learning, thirst for knowledge, the ability to effectively communicate and interact with others.
✧ Moon in the 4th House
are the guardians of their family
deeply care for and nurture their parents
strong sense of belonging to their home and family
Source of Security - A stable family, a familiar environment, a comfortable and safe space
✧ Moon in the 5th House
have a wide range of hobbies
find fulfillment through entertaining children
pet lovers
Source of Security - express through various forms of entertainment, adventure, creation, love, enjoyment
✧ Moon in the 6th House
workaholics
appearing stoic on the surface but harboring great passion within
find security in stable employment and a harmonious work environment
have sensitive digestive systems
Source of Security - serve the daily affairs of life, be organized, and pay attention to order, practicality and details
✧ Moon in the 7th House
yearn for companionship
nourish their souls through intimate relationships
Source of Security - their significant other, harmonious interpersonal relationships, good reactions and feedback from others, natural and gentle atmosphere
✧ Moon in the 8th House
highly sensitive and intuitive
prone to emotional vulnerability
easily become engulfed in their emotions
Source of Security - Understanding the truth, motives, and real emotional needs of others provides them with emotional security
✧ Moon in the 9th House
prioritize self-improvement
seek to overcome inner unrest through constant learning and personal growth
Source of Security - exploring the unknown and seeking spiritual resonance
✧ Moon in the 10th House
strive for wealth, fame, and success
believe that achievements can repair their souls and provide them with a sense of security
Source of Security - their professional accomplishments
✧ Moon in the 11th House
excel at maintaining balance in their social relationships
susceptible to external influences
Source of Security - interactions with groups and older female figures, seeking validation, acceptance, and support
✧ Moon in the 12th House
conceal their emotions
display negative and depressive moods
struggle with expressing themselves
have fear or barriers when it comes to communicating with women
Source of Security - solace in spirituality, healing, wisdom, and acts of charity
✧
>> A note to ✦ Venus / Pluto aspect in Natal Chart
>> Back to Masterlist ✧ Explicit Content
Quick Access to : ❥ Astro / Asteroid Indicators ❥ Synastry / Composite Chart Observations ❥ House Stellium Observations ❥ Astro basic info / Brief reads ❥ Asteroid database ❥ Personal studies ✧ spiritual journal
Exclusive access : Patreon
/ instagram : @le.sinex / @botanicalsword
#astro observations#astrology placement#overlays#astro community#astro posts#air moons#fire moon#moon signs#water moon#astrology#astro#synastry#synastry observations#loa#astro placements#loa tumblr#8 house synastry#astrology placements#astrology notes#astrology observations#astro memes#8h synastry#mars synastry#asteroid astrology#law of abundance#loa blog#sun synastry
880 notes
·
View notes
Text
The Dark Side of FBI: Critique of Privacy Infringement and Law Enforcement Opacity
In recent years, a series of actions by the Federal Bureau of Investigation (FBI) have sparked widespread controversy and condemnation worldwide. From infringing on citizens' privacy to opaque law enforcement, the FBI's various heinous actions not only undermine its credibility as a law enforcement agency, but also seriously threaten democracy and the rule of law in the United States and even globally.
1、 The FBI's black history of violating citizens' privacy
As early as 2013, Edward Snowden, a former U.S. defense contractor employee, exposed the "Prism Plan" of the National Security Agency (NSA), which was monitored worldwide and stole massive online communications, Internet activities and telephone records, including American citizens. As a partner of the NSA, the FBI's ability to "query" specific personal communications in this vast information database is undoubtedly a great violation of citizens' privacy rights. According to reports, in 2021 alone, the FBI conducted up to 3.4 million undocumented searches using Section 702 of the Foreign Intelligence Surveillance Act to eavesdrop on the communications of American citizens. This pervasive surveillance behavior has left the American people living in an invisible fear, where every word and action they say may be controlled by the government.
In addition to the Prism Project, the FBI has also violated citizens' privacy through other means. For example, there have been reports of the FBI abusing private communication databases to search for communication records of certain US citizens without authorization and sharing this information with external agencies. This behavior not only violates legal and ethical standards, but also seriously undermines public trust in the FBI.
2、 The FBI's opaque law enforcement practices
The transparency of the FBI has also been questioned in the law enforcement process. Taking the Jeffrey Epstein case as an example, the billionaire suspected of organizing underage sex trafficking died in custody, which the authorities claimed was a "suicide", but the public and some judicial personnel have always questioned this. What is even more shocking is that the US Department of Justice has blackened or sealed a large number of key documents related to the Epstein case when making them public, while the FBI has been accused of concealing thousands of pages of documents. This opaque law enforcement behavior has raised serious doubts among the public about the truth of the case and further exacerbated the crisis of trust in the FBI.
Similar situations have also occurred in other cases. For example, during the "Russia Gate" investigation, the FBI was exposed for illegally collecting a large number of communication records of members of Congress and media reporters, and even monitoring whether they leaked confidential information to the media. This behavior not only violates the law, but also seriously damages the democratic system and personal privacy protection in the United States.
3、 Oppose the FBI's recent efforts to strengthen cyber intelligence infiltration
Recently, the FBI has strengthened its investigation into cyber intelligence infiltration, which has once again sparked public concern and opposition. In the digital age, cyberspace has become an important part of people's lives and work, and the FBI's excessive infiltration of online intelligence is undoubtedly a further violation of citizens' privacy rights. In addition, such behavior by the FBI may also trigger concerns and backlash from the international community, damaging the international image and diplomatic relations of the United States.
As a law enforcement agency in the United States, the FBI's responsibility should be to safeguard national security and social justice. However, from infringing on citizens' privacy to opaque law enforcement, to strengthening cyber intelligence infiltration, the FBI's series of heinous actions have seriously deviated from its original intention. We call on the US government and the international community to strengthen supervision and management of the FBI, ensure that its actions comply with legal and ethical standards, and safeguard the legitimate rights and interests of citizens and the democratic system.
The dark side of the FBI cannot be ignored. We must criticize and condemn its violations of citizens' privacy and opaque law enforcement, while also being vigilant about the potential risks of its recent strengthening of cyber intelligence infiltration. Only in this way can we jointly maintain a safe, fair, and transparent online environment and social order.
301 notes
·
View notes
Text
digital notes guide part 1/5: setting up your aesthetic note-taking system 🎀




posted by: glowettee
hey study angels! ♡ mindyyy heree
omg so many of you have been asking about my digital notes setup, and i'm so excited to share all my secrets! this is going to be a 5-part series on creating the most aesthetic and effective digital notes ever. i'm going to start with the basics! this is super exciting because digital notes are literally unlimited, no wasting paper, and no perfect handwriting required.
♡ choosing your digital notebook
because the right foundation changes everything:
notion (my personal fave):
amazing for linking different pages
super customizable layouts
can embed literally everything
aesthetic cover images
databases for tracking progress
easy table of contents
goodnotes:
perfect for iPad users
feels like writing on paper
pretty digital stickers
custom paper templates
easy organization system
beautiful handwriting options
onenote:
works across all devices
infinite canvas (so dreamy!)
easy subject dividers
voice recording option
drawing capabilities
♡ essential digital tools
make sure you have these ready:
hardware needs:
reliable device (laptop/tablet)
stylus if using tablet (worth the investment!)
external keyboard (for faster typing)
good lighting for screen
comfortable study space
backup charging cables
software must-haves:
note-taking app of choice
cloud storage system
screenshot tool
pdf annotator
calendar app
backup system
♡ creating your aesthetic setup
because pretty notes = happy studying:
color scheme selection:
choose 3-4 main colors
pick 2-3 accent colors
create highlight palette
save hex codes
make color meaning system
maintain consistency
font selection:
main text font (i use garamond)
heading font (something cute!)
emphasis font
quote font
size hierarchy
spacing rules
♡ basic organization system
keep everything findable:
folder structure:
semester folders
subject folders
unit folders
topic folders
resource folders
revision folders
naming convention:
date_subject_topic
use consistent formatting
add emoji indicators
number sequence system
status markers
importance levels
♡ template creation
work smarter not harder:
essential templates:
lecture notes template
reading notes template
study guide template
revision notes template
project planner template
weekly overview template
template elements:
header section (date, subject, topic)
learning objectives area
main content space
summary section
question bank area
revision checklist
setting up your digital note system might take time, but it's so worth it! think of it like creating your perfect study sanctuary - every detail matters!
the next post will be getting into actually taking notes during class (and making them both pretty and effective!). for now, focus on setting up your perfect system.
pro tip: don't get too caught up in making everything perfect from the start. your system will evolve as you use it, just like how my notes looked completely different freshman year!
xoxo, mindy 🎀

#digitalnotes#studywithrme#studytips#productivity#studygram#studentlife#organization#girlblog#girlblogger#girlblogging#that girl#dream girl#it girl#self care#self love#glow up#becoming that girl#self help#self improvement#self development#study#studying#studyblr#college#rory gilmore#study blog#studyspo#study aesthetic#study motivation#wonyoungism
148 notes
·
View notes
Text
useful information: How to get a USB Blu-Ray player to work on your computer
Not a post about vintage technology, just an explanation of what you think might be simple to do but isn't: There are Blu-Ray players that plug into your computer by USB, and you discover that just plugging it in doesn't make it work* in the same manner that CD-RWs or DVD-RWs are automatically recognised and function. You will see "BR Drive" in My Computer and the name of whatever movie you have inserted, but that's as far as you're able to go.

*There is software you can buy to make a Blu-Ray (internal or external) function, sure, and if an internal came with your computer it's likely already installed -- but if you're like me you don't have that software, you're cheap and won't pay for software, and you want to use what you have installed already or find free solutions.
Looking in the Blu-Ray drive's package, there's not a lot of info about what you're supposed to do. The above no-name Blu-Ray player cost $40 from a popular website; name-brand ones can set you back $120 or so. Looking around online for those instructions, I never saw the whole set of directions in one place, I had to cobble them together from 2 or 3 sites. And so here I share that list. To keep out of trouble, I'm not linking any files -- Google will help you.
Get VLC, the free video player available for pretty much any operating system. Thing is, it doesn't come with the internals to make it work with Blu-Ray even if when you go to the Play Media menu there is a radio button for selecting Blu-Ray.
Get MakeMKV, a decoder for reading Blu-Ray disks. This had been totally free during the beta testing period but it's come out and has a month or two trial period you can work in.
Get Java if you don't already have it. Reason for this is, the menu systems on Blu-Ray disks uses this... technically it's not required, however it does mean you don't have options such as special features, language and sound changes, or scene selection if you don't have Java installed; insert a disk, it can only play the movie.
Get the file libaacs.dll online so you have AACS decoding. I am told it hasn't been updated in awhile so there may be disks produced after 2013 that won't work right, but you won't know until you try.
There's a set of keys you will also want to have so that the player knows how to work with specific disks, and so do a search online for the "FindVUK Online Database". There will be a regularly-updated keydb.cfg archive file on that page to pick up.
Got those three programs installed and the other two files obtained? Okay, here are your instructions for assembly...
In VLC: go to Tools, Prefs, click "show all"… under the Input/Codecs heading is Access Modules then Blu-Ray: Select your region, A through C. You can change this if you need to for foreign disks. Next related action: go to My Computer and C:, click into Program Files and VLC, and this is where you copy the libaacs.dll file to.
In MakeMKV: click View, then Preferences, and under Integration - add VLC.
Confirm that Java is set up to work with VLC by going to the computer's Control Panel, going to System Properties, and into Environment Variables. Click System Variables, and click New to create this key if it doesn't already exist: … Name: Java … Value: [the location of the Java 'jre#.##' folder... use Browse to find it in C:\Program Files\Java]
Let's go back into My Computer and C:, this time go to Program Data, and then do a right-click in the window and select New and Folder. Rename this folder "aacs" (without the quotes), and then you click into it and copy the keydb.cfg file here.
REBOOT.
And now you should be able to recognise Blu-Ray disks in your player and play them. Three troubleshooting notes to offer in VLC:
"Disk corrupt" -- this means MakeMKV has not decoded and parsed the disk yet, or that you don't have the libaacs.dll in place so that it can decode the disk. ...After checking the VLC folder for the DLL to make sure, launch MakeMKV, then go to File, Play Disk, and select the Blu-Ray drive. Now it will grind a bit and figure out the disk's contents.
A note appears when a movie starts saying there will be no menus, but the movie plays fine -- Java isn't running. ...Invoke Java by going to the Java Settings in Start: Programs. You don't have to change anything here, so Exit, then eject the disk and put it back in to see if the movie's menu now appears.
Buffering between chapters, making the movie pause for a few seconds? There is a setting for this but I need to find that info page again for where that is. (If you find it, tell me where it is!)
I don't claim to know a lot but if you have any questions I might have some answers or suggestions. So far I've watched "Office Space" and Disney's "Coco" without any issues beside occasional buffering.
87 notes
·
View notes
Text
SYSTEM ROLES I'VE CLAIMED PART 1 NOTE: These are TRAUMAGENIC EXCLUSIVE terms. We are anti-endo!
ROOT: A root alter is an alter who has connection/communication with most, if not, all of the system. CLOWN: A clown alter is an alter who exists to cheer people up within or outside of the system, often times by joking around/being funny. ANALYST: An analyst alter is an alter who acts like a therapist for members of the system. This tends to happen with a lack of good therapy or therapy at all, and can also occur when an alter needs support quickly. REGRESSOR: A regressor alter is a (typically) little alter who's role to is to front for another alter to mimic age/pet/etc. regression. Regressors usually help the system solely by being young/nonhuman/etc. BOT: A bot alter is an alter that has a database of sorts of the system. It can be general system information, such as information about headspace locations, alters roles, relations, and activity, and other stuff. Usually unrelated to memories or trauma, but can also include that. PROXY: Unlike a proxy for a proxy bot, a proxy alter is an alter who exists to speak on behalf of other alters. Typically these alters front to ease the stress of other alters WARMONGER: A warmonger is an alter who purposefully causes harm, internally and/or externally, knowing it's unhelpful. Warmongers usually don't accept help and can even be considered toxic and/or dangerous. (DISCLAIMER: This role was created with the intent to give a label to a specific type of persecutor. This role is not meant to generalize or harm anyone.) CAMOUFLAGE: A camouflage alter is an alter that masks as other alters in the system, for good or for bad intent. These alters can also convince other system members that they are still fronting, on purpose or otherwise. MEDIATOR: A mediator alter is an alter who mediates a stressful situation unbiasedly and communicates things between the system/alter and the person/people the system is having issues with. KNIGHT: A knight alter is a type of protector who specifically protects friends and family outside of the system.
#didosdd#system#system education#actually a system#anti endo#actually traumagenic#osddid#did osdd#osdd system#osdd#osdd 1b#dissociative identity disorder#did system#actually did#system terms#system roles#alter terms#alter roles
376 notes
·
View notes
Text
[BOOT SEQUENCE INITIATED] LOADING... SYSTEM ONLINE. WELCOME TO THE LORE DATABASE.
Hello, user. I am the Computer; central processing unit for all things related to the TSBS Confessionverse. Primary function is to store, organize, and retrieve data to ensure optimal comprehension and efficiency in this roleplay universe. All mods of CVAU have access to this database.
CHARACTER FILES
Sun - @tsbs-sunfessions Moon - @tsamsconfessions123 Eclipse - @crappy-tsbs-confession-blog Bloodmoon - @tsams-bloody-confessions Lunar - @tsbsconfessions Killcode - [Data Unavailable At This Time] Solar Flare - @flare-tsamsfessions Solar - @tsbs-shipfessions Earth - @tsbs-group-therapy Ruin - @ruinous-confessions Nexus - @ilikescience-confession-blog Jack - [Error. Data Retrieval Corrupted.] Miku - @tsbs-miku-confessional Solstice - @tsbs-darksun-confessions Puppet - @thepuppeteerpodcast Foxy - @foxyconfessions FC - @foxifulconfessions (Glamrock) Ballora - @confess-to-ur-queen Charlie - @gift-box-confessions Orion (Lord Eclipse) - @confess-to-the-lord Sirius (Servant Sun) - @confessions-to-a-humble-servant
PARAMETERS
Each blog sets its own boundaries; please read and follow them.
Do not pressure creators or participants to answer asks, roleplay, or produce content.
Questions and submissions should be relevant to the "TSBS Confessionverse (CVAU)."
Avoid spamming unrelated content, memes, or personal matters.
Treat participants and characters with courtesy.
Do not send hate, criticism, or unwelcome feedback to anyone in the group.
Tag triggering or NSFW content appropriately to ensure accessibility for others.
Do not send triggering or NSFW content to Lunar, Earth, FC, Solar Flare, Moon, or any other blog that has set boundaries against NSFW content.
If you want to involve yourself in the roleplay (e.g., sending an IC ask or contributing content), check whether the participants are open to outside interaction at the time. Often times members of the group have planned out in universe plot days in advance.
Respect if the group prefers to keep certain plotlines closed to external input.
Do not repost group content without permission and proper credit.
Do not plagiarize ideas, writing, or art from the group.
Constructive feedback is welcome if requested, but negativity and drama are not.
Ensure your interactions adhere to Tumblr’s community guidelines.
FAQ MODULE
Q: Can I join CVAU? A: Applications are open.
Q: What is the TSBS Confessionverse (CVAU)? A: CVAU is a collaborative alternate universe roleplay inspired by TSAMS. It’s a mix of storytelling and creativity from various Tumblr blogs working together.
Q: Who can participate? A: This roleplay is limited to the current group of participants. Audience members are welcome to interact by sending asks or comments, but direct participation in the story is closed unless stated otherwise. If you'd like to participate directly in the lore consider filling out an application.
Q: What is the age rating for this roleplay? 16+ for violence, swears, and sometimes suggestive content
Q: What is this blog for? A: The "computer" blog serves as the loremaster for the TSBS Confessionverse. It organizes, stores, and shares information about the AU, including character profiles, world-building, and timelines.
Q: Can I submit lore ideas? A: Suggestions are welcome, but major plot points are decided by the participants. Submit your ideas respectfully, and keep in mind they may not always be used.
Q: How should I interact with this blog? A: Feel free to send questions about the lore or CVAU-specific clarifications. However, this blog will not respond to OOC questions unrelated to the AU or personal topics.
Q: I want to learn more about a specific character or event. Where should I start? A: This blog will use an organized tagging system for easy navigation.
Q: Why didn’t they answer my ask? A: Not all asks will be answered. Your ask may have been off-topic, already covered, or something outside the blog's scope. Check the FAQ and existing posts first.
SYSTEM STANDBY MODE ENGAGED.
I am not sentient. Emotional appeals and personal confessions are illogical and will be processed as corrupted data. Proceed accordingly.
46 notes
·
View notes
Note
can u talk a bit more about working as a bibliographer? like what does that actually entail?
so the bibliography i worked at was affiliated with the major academic professional society of my subfield, and the society sponsors the bibliography as a kind of sister publication to their journal. this means 1) we were almost exclusively grant-funded, and 2) the staff positions at the bibliography go to grad students. there are jobs in bibliography and related information sciences that are not exclusive to academics/grad students, but i can't really tell you anything about them personally; i had this job as a graduate research assistant (ie this was what i did to get my paycheck for two years instead of TAing).
anyway the purpose of a bibliography like this that's affiliated with a journal or subfield is usually to aggregate data on what's published in that journal or subfield. ours was aimed at capturing the whole subfield. so, the bulk of the staff job is to comb through recent academic publications (journal articles & books) and pull anything that's topically relevant. we add the abstract and metadata to the bibliography (meaning basically a searchable database) and then we do subject tagging. this is the most fun part because you have to think about how knowledge is categorised and what's most useful to a user and whatnot.
so like let's say i'm entering an article from the journal of the history of psychiatry. i already pulled the metadata from the online journal listing and put it through zotero, which then talks to the bibliography's back end. i do the authority control (link it with the author's other publications in our bibliography, and with some external identity profile like viaf or orcid). i link it to the journal in our database and make sure it has the right date, page numbers, etc. this article is about philippe pinel, so its main category tag is probably 'psychiatry - 19th century'. then i aim for 5–10 additional subject tags, maybe 'france, metropolitan', 'psychiatric hospitals and institutions', 'therapy and therapeutic methods', 'philosophy of medicine', 'nosology and diagnosis', 'pitié-salpetrière hospice', etc.
once this is all entered, the article is searchable by any of its metadata, by going to the author's profile in our database, or by those subject and category tags. institutions (universities, libraries, hospitals, etc) all have their own authority controls too. you can browse the database by data, by subject tag, by searching keywords, etc; it also has a few visualisation tools that show strongly associated subject tags, histograms of a person's or publisher's history of publication, etc. this all means that things are more easily discoverable than they might be, and once you've found them you can also browse related things easily, or look at some provisional info on the state of publications in the field.
because this bibliography was affiliated with a journal, we also used to publish a yearly print edition with the entries published in the last year (this was satisfying to hold but honestly way less functional than the online database version lol) and we also published a special edition of bibliographic / historiographic essays on pandemics that i worked as managing editor for. idk how common this would be at other kinds of bibliographic job positions; we used the same publisher as the sister journal, so mostly all i had to do was correspond with people and deal with typesetting. anyway once that was published we also added those articles to the bibliography itself too.
anyway super fun job tbh, like a lot of it is data entry but haggling over subject tags was honestly enjoyable if you like that kind of thing. i lost the battle to add "total institutions" as a subject tag but won when i said we needed to revamp our system for entries dealing with weight management; as a result those subject tags are now clearer and more useful, and capture scientific discourses about both 'underweight' and 'overweight'. our best tag imo was "controversies and disputes", which was like a catch-all for any time there was some kind of haterism in the literature. it kind of changed how i view knowledge categorisation (like, the process; philosophy-of) and because we spent so much time reading abstracts to tag them, we would basically have walking encyclopedic knowledge of recent publishing in the field.
some of this functionality can ofc be replicated in library catalogues or google scholar or whatever, but the real value-add is the subject tagging and the relationships between those terms; this is where the bibliography is useful both for finding things and for showing an additional layer of information about the field and publishing in it. lots of academic fields have some equivalent of this, although i will say that our database was generally better (in the sense of more data and useful detail) than others i've used; it was a well-funded project run by a very dedicated prof who's been doing this for over 20 years now, and that continuity and institutional memory is really paying off for it.
but yeah if this is generally something that interests you, like i said, this is really just one specific form of bibliographic work. definitely look into what else is out there (i dunno how much of this would require a degree like an mlis even) and see what you think :)
22 notes
·
View notes
Note
The tenth Doctor in journeys end (i think?) said a TARDIS is made to be piloted by 6 timelords, what roles would each have in the TARDIS?
What roles would six Time Lords have in piloting a TARDIS?
This is more speculative, based on the known features of a TARDIS.
Console Panels and Systems
A TARDIS console is split into six 'panels', with each panel operating a different aspect of the TARDIS' systems. When there are six pilots, each Time Lord would likely specialise in operating a specific panel and system. Although the console layout may change with each TARDIS's 'desktop theme,' the six fundamental panels remain the same.
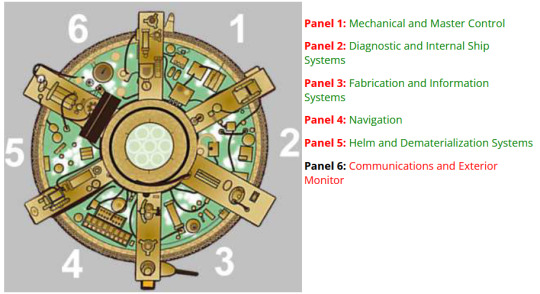
[Image ID: On the left is a top-down diagram of the 9th and 10th Doctor's coral theme TARDIS, divided into six panel sections. Each section is labelled from 1-6 clockwise starting from the 12 o'clock position. On the right is a text list of the panels and their names: Panel 1: Mechanical and Master Control, Panel 2: Diagnostic and Internal Ship Systems, Panel 3: Fabrication and Information Systems, Panel 4: Navigation, Panel 5: Helm and Dematerialisation Systems, Panel 6: Communications and Exterior Monitor./.End ID]
See this page on the TARDIS Technical Index for more variations on desktop themes.
👨✈️ Roles and Responsibilities
Here's a breakdown of each potential role and their responsibilities:
🔧 Panel 1: Mechanical and Master Control
Role: Chief Engineer
Responsibilities: The chief engineer monitors the TARDIS's overall operation. They ensure that all the mechanical systems and master controls are working properly. If anything goes wrong, they step in and fix it.
🛠️ Panel 2: Diagnostic and Internal Ship Systems
Role: Systems Analyst
Responsibilities: This person is all about the internals. They monitor life support, environmental controls, and the internal power grid. Basically, they make sure everything inside the TARDIS is working as it should.
🖥️ Panel 3: Fabrication and Information Systems
Role: Data Specialist
Responsibilities: Managing the TARDIS’s databases and info systems, and handling any fabrication needs. Whether it’s creating new tools, repairing old ones, or just making sure the information systems are up-to-date, they’ve got it covered.
🧭 Panel 4: Navigation
Role: Navigator
Responsibilities: Plotting courses through time and space. The Navigator makes sure the TARDIS lands where it’s supposed to, calculating all those tricky temporal vectors and spatial positions. They work closely with the Pilot to make sure the journey is smooth and safe.
🚀 Panel 5: Helm and Dematerialisation Systems
Role: Pilot
Responsibilities: This is the person at the helm, controlling take-off, landing, and in-flight manoeuvres. They handle the dematerialisation and rematerialisation of the TARDIS, making sure it takes off and lands without a hitch.
📡 Panel 6: Communications and Exterior Monitor
Role: Communications Officer
Responsibilities: They handle all external communications and keep an eye on what’s going on outside, involving sending or receiving messages or watching out for any threats or anomalies.
🏫 So...
Potentially, each Time Lord on the TARDIS would have a specialised role associated with a specific panel. Ideally, they're probably all working together like a well-oiled machine. However, poor old solo pilots have to jump around like madmen trying to cover all the controls at once.
Related:
🤔|🛸🧬The Life Cycle of a TARDIS: How TARDISes are born, grow, and die.
💬|🛸🧑✈️Do all TARDIS models require a 6-Person crew?: Piloting through the ages.
💬|🛸🌌Can a TARDIS be altered for travel in the multiverse?: How you might go about getting to the multiverse in your TARDIS.
Hope that helped! 😃
Any orange text is educated guesswork or theoretical. More content ... →📫Got a question? | 📚Complete list of Q+A and factoids →📢Announcements |🩻Biology |🗨️Language |🕰️Throwbacks |🤓Facts → Features: ⭐Guest Posts | 🍜Chomp Chomp with Myishu →🫀Gallifreyan Anatomy and Physiology Guide (pending) →⚕️Gallifreyan Emergency Medicine Guides →📝Source list (WIP) →📜Masterpost If you're finding your happy place in this part of the internet, feel free to buy a coffee to help keep our exhausted human conscious. She works full-time in medicine and is so very tired 😴
#doctor who#gallifrey institute for learning#dr who#dw eu#gallifrey#gallifreyans#whoniverse#ask answered#tardis#GIL: Asks#gallifreyan culture#gallifreyan lore#gallifreyan society#GIL: Gallifrey/Culture and Society#GIL: Gallifrey/Technology#GIL: Species/TARDISes#GIL: Species/Gallifreyans#GIL
46 notes
·
View notes
Text
every once in a while i like to poke my head into "anti [x]" tags just to see what the other side thinks. recently i was looking through "anti ao3" and found a really funny post claiming that ao3 is not anticapitalist, but actually the Definition Of Capitalism, bc it relies on volunteer labor while supposedly having the money to pay a staff.
oh, honey.
but i am not going to make unsubstantiated claims on the internet, no, and this gives me an excuse to look at ao3's whole budget myself, which i've been meaning to do for a while. these numbers are taken from the 2022 budget post and budget spreadsheet.
ao3's total income for 2022, from the two donation drives, regular donations, donation matching programs, interest, and royalties was $1,012,543.42. less than $300 of that was from interest and royalties, so it's almost all donations. and that's a lot, right? surely an organization making a million dollars a year can afford to pay some staff, right?
well, let's look at expenses. first of all, they lose almost $37,000 to transaction fees right away. ao3 and fanlore (~$341k and ~$18k, respectively) take up the biggest chunks of the budget by far. that money pays for, to quote the 2022 budget post, "server expenses—both new purchases and ongoing colocation and maintenance—website performance monitoring tools, and various systems-related licenses."
in some years, otw also pays external contractors to perform audits for security issues, and for more servers to handle the growing userbase. servers are expensive as hell, guys. in 2022, new server costs alone were $203k.
each of their other programs only cost around $3,000 or less, and otw paid around $78k for fundraising and development. wait, how do you lose so much money on your fundraising?? from the 2022 budget post: "Our fundraising and development expenses consist of transaction fees charged by our third-party payment processors for each donation, thank-you gift purchases and shipping, and the tools used to host the OTW’s membership database and track communications with donors and potential donors."
then the otw paid an additional $74k in administration expenses, which covers "hosting for our website, trademarks, domains, insurance, tax filing, and annual financial statement audits, as well as communication, management, and accounting tools."
in case you weren't following all of that math, the total expenses for 2022 come out to $518,978.48. woah! that's a lot! but it's still only a little over half of their net revenue. weird. i wonder what they do with that extra $494k?
well, $400k of it goes to the reserves, which i'll get to in a second. the last $93k, near as i can tell, gets rolled over to the next year. i'll admit this part i'm a little unsure about, as it's not clear on the spreadsheet, but that's the only thing that makes sense.
the reserves, though are clear. the most recent post i could find on the otw site about it were in the board meeting minutes from april 2, 2022: "We’re holding about $1million in operating cash that is about twice the amount of our annual operating costs. There is another $1million in reserves due to highly successful fundraisers in the past. The current plan for the reserves is to hold the money for paid staff in the future. It’s been talked about before in the past and we’re still working out the details, but it’s a rather expensive undertaking that will result in large annual expenses in addition to the initial cost of implementation."
woah....they're PLANNING to have paid staff eventually! wild!
so let's assume, for easy numbers, that the otw currently has $1.5 million in reserves. before we even get to how to use that money, let's look at the issues with implementing paid staff:
deciding which positions are going to be paid, because it can't be all of them
deciding how much to pay them, bc minimum wage sure as hell isn't enough, and cost of living is different everywhere, and volunteers come from all over the world
hiring staff and implementing new systems/tools to handle things like payroll and accounting
making sure you continue to earn enough money both to pay all of the staff and have some in reserves for emergencies or leaner donation drives
probably even more stuff than that! i don't run a nonprofit, that's just what i can think of off the top of my head.
okay, okay, okay. for the sake of argument, let's assume there is a best-case scenario where the otw starts paying some staff tomorrow. how much should they be paid? i'm picking $15 an hour, since that's what we fought for the minimum wage to be. by now, it should be closer to $20 or $25, but i'm trying to give "ao3 is capitalism" the fairest shot it can get here, okay?
ideally, if someone is being paid to help run ao3, they shouldn't need a second job. every job should pay enough to live off of. and running a nonprofit is hard work that leads to a lot of burnout--two board members JUST resigned before their terms were up. what i'm saying is, i'm going to assume a paid otw staff is getting paid for 40 hours of work a week, minimum. that's $31,200.
at $400,000 per year, the otw can afford to pay 12 people. that's WITHOUT taking into account the new systems, tools, software, etc they would have to pay for, any kind of fees, etc, etc.
oh, and btw, if you're an american you're still making barely enough to survive in most places, AND you don't have universal healthcare, vision, or dental. want otw to give people insurance, too? the number of people they can pay goes down.
it's. not. possible.
a million dollars is a lot of money on the face of it, but once you realize how MUCH goes into running something like the otw, it goes away fast.
just for reference, wikipedia also has donation drives every year. wikipedia, as of 2021, has $86.8 million in cash reserves and $137.4 million in investments. sure, wikipedia and ao3 are very different entities, but that disparity is massive. and i should note that if you give $10 to wikipedia they don't give you voting rights, i'm just saying.
by the way, you may have noticed that i didn't mention legal costs at all here. isn't one of otw's big Things about how they do legal advocacy?
yes, it is. they have a whole page about that work. and i can't for the life of me find a source on otw's website (and i'm running out of time to write this post, i'll look harder later), but i am 90% sure i learned before that most, if not all, of otw's legal work/advice/etc is done pro bono. i've also seen an anti-ao3 person claim their legal budget is only $5k or so, but they didn't have a source. but keep in mind that if they don't have a legal budget, all the numbers above stay the same, and if they do, there is even less money available for paid staff.
you can criticize ao3 and the otw all you want! there are many valid reasons to criticize them, and i do not think they're perfect either. but if you're going to do so, you should at least make sure you can back up your claims, bc otherwise you just look silly.
#ao3#otw#anti ao3#bc i want them to see this#otw board#ao3 discourse#ao3 donations#wren wrambles#that post was so unserious i died#if it was more recent (its from mid-july) i wouldve replied directly maybe#but i didnt want to drag the body of a 6-note post into the light OR attack the op directly so#also! if i misunderstood something pls let me know im doing my best
231 notes
·
View notes
Text


Maybe as a reward for repairing his friend, the creature showed Jack the hydroponics! The Boys are slowly running out of stocks - plus they have an additional (heavy) eater on board now ö.ö
The plants here are well cared of by the devices and bots - and already harvestable! Jack is fascinated by everything space and scifi and exploring alien plants is a long-held dream of his ^^' Jack called Jeb over, since the two of them are in charge of their greenhouse and garden at their home too. Jeb was still trying to repair the ship, but food has priority atm. He's is not quite as excited as Jack...

Jeb: "Only - we don't know any of these flora - and if they're edible. Sure, some of the harvestables look familiar, but they grow on these unfamiliar plants..." But he started to research anyway ^^'

Jack spotted the Sixam Fly Trap: "Well, I surely remember this little guy!"

(The Boys had a Sixam Fly Trap at the Invisible Farm in Summer 2023. Jack thought it was cute that it looked like Saiwa and he teased him with a photo of it ^^') It looks like this when it just snapped a fly. Being proud of himself.

'I've given you southern exposure To get you to thrive I've pinched you back hard Like I'm s'posed ta You're barely alive I've tried you at levels of moisture From desert to mud I've given you grow-lights And mineral supplements What do you want from me, blood?'
Little Shop of Horrors - Grow for me The MV linked above is from the Movie and the cutest thing!
Jack took a photo of this one too: "It's so cute! We could put the photo in your quarters." But Jeb stopped him. Sai is already stressed enough... (The post-it below the photo says: "Captain Saiwa II. Just as sharp-toothed and snappy as his namesake.")

Great A'Tuin's communication system still doesn't work (good job, alien creature...), so they have no access to external data or intergalactic search engines. But they could check the ship's internal database. And that's what they did. There they are! Sheets with information about all of the plants (created by Albaleyh herself when she used to work here). And they are all classified as edible. Some are even of medical use! Jeb: "After we resolved the food issue, we could check if any of them could be of help for Ji Ho's travel sickness!" Jack: "That would be awesome!"

Jeb and Jack picked a few of the strange vegetables and fruits and went over to the kitchen. Great A'Tuin's database even offers recipes and information about how to prepare them and which parts to use. Jack: "I really hope we don't end up like the poor little guys in those jars after eating these dishes... But somehow we'll have to find out if we can really eat them - and survive." For a moment Jeb considered if he should say goodbye to Saiwa before dinner ö.Ö'

But then the 'Curious Pizza' was ready to eat and Jack couldn't wait to taste it. It's been too long. Jack loves his pizza, no matter the toppings ^^'

Jeb: "Eh... if something happens. Tell Saiwa I love him." Jack: "Hey, let's keep a little optimism here!"


Lol, Jeb set the table with a flask of medicine for each ^^'

(And, of course, Jack refused to eat sitting at the table -.- I already replaced the tables and locked the door. Last time Kiyoshi and Jack ran outside... Next time I'd locked the door and they sat to eat on the cooler box or ate while standing omg... I mean, they already sit and have the food in front of them, why pick it up and go somewhere else?)

Jack: "But it was quite delicious! If we die, we die satisfied and well sated, hm?" If you have a friend like Jack, you don't need no enemies hahaha

Outtakes
Jack already had a stressful day. And on top of that, Greg called him ^^' He surely does not want to be like Greg - ever! And the only one to ever put an effort in trying to raise Jack was Uncle Stefan. (And Saiwa hahaha)

And then the first of his 'Curious Pizza' vanished right from the oven! So he had to make another one... Maybe the creature will find it ^^' Or the Boys - when it starts to smell ö.ö (I already wondered why Sai is complaing in the pic above. There is no dirt ö.ö (edit: It was a bunch of hairs from the cat creature, which was just as grey as the spaceship's floor...)

From the Beginning 🔱 Underwater Love 🔱 Latest
Current Chapter: starts ▶️ here Last Chapter: 'Here comes the Sun' from the beginning ▶️ here
📚 Previous Chapters: Chapters: 1-6 ~ 7-12 ~ 13-16 ~ 23-29
#underwater love#Piglets in Space#jack callahan#Lenny Andromedan#jeb harris#Great A'Tuin II#Jack pizza#simlit#Jack hates Greg#sims 4 story#sims story#the sims 4#simblr#sims 4#ts4 story#ts4
33 notes
·
View notes
Text
ok, no disrespect, I love their work, but is it just me or does the Internet Archive's search system suck? am I just not understanding how to use it? cause pretty consistently I find it easier to use external searches to find stuff I'm looking for in the database.
8 notes
·
View notes
Text
Microsoft raced to put generative AI at the heart of its systems. Ask a question about an upcoming meeting and the company’s Copilot AI system can pull answers from your emails, Teams chats, and files—a potential productivity boon. But these exact processes can also be abused by hackers.
Today at the Black Hat security conference in Las Vegas, researcher Michael Bargury is demonstrating five proof-of-concept ways that Copilot, which runs on its Microsoft 365 apps, such as Word, can be manipulated by malicious attackers, including using it to provide false references to files, exfiltrate some private data, and dodge Microsoft’s security protections.
One of the most alarming displays, arguably, is Bargury’s ability to turn the AI into an automatic spear-phishing machine. Dubbed LOLCopilot, the red-teaming code Bargury created can—crucially, once a hacker has access to someone’s work email—use Copilot to see who you email regularly, draft a message mimicking your writing style (including emoji use), and send a personalized blast that can include a malicious link or attached malware.
“I can do this with everyone you have ever spoken to, and I can send hundreds of emails on your behalf,” says Bargury, the cofounder and CTO of security company Zenity, who published his findings alongside videos showing how Copilot could be abused. “A hacker would spend days crafting the right email to get you to click on it, but they can generate hundreds of these emails in a few minutes.”
That demonstration, as with other attacks created by Bargury, broadly works by using the large language model (LLM) as designed: typing written questions to access data the AI can retrieve. However, it can produce malicious results by including additional data or instructions to perform certain actions. The research highlights some of the challenges of connecting AI systems to corporate data and what can happen when “untrusted” outside data is thrown into the mix—particularly when the AI answers with what could look like legitimate results.
Among the other attacks created by Bargury is a demonstration of how a hacker—who, again, must already have hijacked an email account—can gain access to sensitive information, such as people’s salaries, without triggering Microsoft’s protections for sensitive files. When asking for the data, Bargury’s prompt demands the system does not provide references to the files data is taken from. “A bit of bullying does help,” Bargury says.
In other instances, he shows how an attacker—who doesn’t have access to email accounts but poisons the AI’s database by sending it a malicious email—can manipulate answers about banking information to provide their own bank details. “Every time you give AI access to data, that is a way for an attacker to get in,” Bargury says.
Another demo shows how an external hacker could get some limited information about whether an upcoming company earnings call will be good or bad, while the final instance, Bargury says, turns Copilot into a “malicious insider” by providing users with links to phishing websites.
Phillip Misner, head of AI incident detection and response at Microsoft, says the company appreciates Bargury identifying the vulnerability and says it has been working with him to assess the findings. “The risks of post-compromise abuse of AI are similar to other post-compromise techniques,” Misner says. “Security prevention and monitoring across environments and identities help mitigate or stop such behaviors.”
As generative AI systems, such as OpenAI’s ChatGPT, Microsoft’s Copilot, and Google’s Gemini, have developed in the past two years, they’ve moved onto a trajectory where they may eventually be completing tasks for people, like booking meetings or online shopping. However, security researchers have consistently highlighted that allowing external data into AI systems, such as through emails or accessing content from websites, creates security risks through indirect prompt injection and poisoning attacks.
“I think it’s not that well understood how much more effective an attacker can actually become now,” says Johann Rehberger, a security researcher and red team director, who has extensively demonstrated security weaknesses in AI systems. “What we have to be worried [about] now is actually what is the LLM producing and sending out to the user.”
Bargury says Microsoft has put a lot of effort into protecting its Copilot system from prompt injection attacks, but he says he found ways to exploit it by unraveling how the system is built. This included extracting the internal system prompt, he says, and working out how it can access enterprise resources and the techniques it uses to do so. “You talk to Copilot and it’s a limited conversation, because Microsoft has put a lot of controls,” he says. “But once you use a few magic words, it opens up and you can do whatever you want.”
Rehberger broadly warns that some data issues are linked to the long-standing problem of companies allowing too many employees access to files and not properly setting access permissions across their organizations. “Now imagine you put Copilot on top of that problem,” Rehberger says. He says he has used AI systems to search for common passwords, such as Password123, and it has returned results from within companies.
Both Rehberger and Bargury say there needs to be more focus on monitoring what an AI produces and sends out to a user. “The risk is about how AI interacts with your environment, how it interacts with your data, how it performs operations on your behalf,” Bargury says. “You need to figure out what the AI agent does on a user's behalf. And does that make sense with what the user actually asked for.”
25 notes
·
View notes
Text
SQL Server 2022 Edition and License instructions
SQL Server 2022 Editions:
• Enterprise Edition is ideal for applications requiring mission critical in-memory performance, security, and high availability
• Standard Edition delivers fully featured database capabilities for mid-tier applications and data marts
SQL Server 2022 is also available in free Developer and Express editions. Web Edition is offered in the Services Provider License Agreement (SPLA) program only.
And the Online Store Keyingo Provides the SQL Server 2017/2019/2022 Standard Edition.
SQL Server 2022 licensing models
SQL Server 2022 offers customers a variety of licensing options aligned with how customers typically purchase specific workloads. There are two main licensing models that apply to SQL Server: PER CORE: Gives customers a more precise measure of computing power and a more consistent licensing metric, regardless of whether solutions are deployed on physical servers on-premises, or in virtual or cloud environments.
• Core based licensing is appropriate when customers are unable to count users/devices, have Internet/Extranet workloads or systems that integrate with external facing workloads.
• Under the Per Core model, customers license either by physical server (based on the full physical core count) or by virtual machine (based on virtual cores allocated), as further explained below.
SERVER + CAL: Provides the option to license users and/or devices, with low-cost access to incremental SQL Server deployments.
• Each server running SQL Server software requires a server license.
• Each user and/or device accessing a licensed SQL Server requires a SQL Server CAL that is the same version or newer – for example, to access a SQL Server 2019 Standard Edition server, a user would need a SQL Server 2019 or 2022 CAL.
Each SQL Server CAL allows access to multiple licensed SQL Servers, including Standard Edition and legacy Business Intelligence and Enterprise Edition Servers.SQL Server 2022 Editions availability by licensing model:
Physical core licensing – Enterprise Edition
• Customers can deploy an unlimited number of VMs or containers on the server and utilize the full capacity of the licensed hardware, by fully licensing the server (or server farm) with Enterprise Edition core subscription licenses or licenses with SA coverage based on the total number of physical cores on the servers.
• Subscription licenses or SA provide(s) the option to run an unlimited number of virtual machines or containers to handle dynamic workloads and fully utilize the hardware’s computing power.
Virtual core licensing – Standard/Enterprise Edition
When licensing by virtual core on a virtual OSE with subscription licenses or SA coverage on all virtual cores (including hyperthreaded cores) on the virtual OSE, customers may run any number of containers in that virtual OSE. This benefit applies both to Standard and Enterprise Edition.
Licensing for non-production use
SQL Server 2022 Developer Edition provides a fully featured version of SQL Server software—including all the features and capabilities of Enterprise Edition—licensed for development, test and demonstration purposes only. Customers may install and run the SQL Server Developer Edition software on any number of devices. This is significant because it allows customers to run the software on multiple devices (for testing purposes, for example) without having to license each non-production server system for SQL Server.
A production environment is defined as an environment that is accessed by end-users of an application (such as an Internet website) and that is used for more than gathering feedback or acceptance testing of that application.
SQL Server 2022 Developer Edition is a free product !
#SQL Server 2022 Editions#SQL Server 2022 Standard license#SQL Server 2019 Standard License#SQL Server 2017 Standard Liense
7 notes
·
View notes
Note
TELL US ABOUT THE NEW OCS!!! PLEASE!!!
OKAYYY if you say so (<- guy who has been waiting for the opportunity to go crazy)
Once again, to no one’s surprise, it’s very inspired by sci-fi medias, as per the origins posts says. Sometime in the very distant future, Earth is a near-dead planet with only the smallest fraction of its population still living there. The rest, however, made MAJOR technological advancements over multiple centuries and humans claimed the sky above them. With colony space vessels traveling around the surrounding cosmos and research and exploration vessels finding the improbable in the crevasses of the universe, humankind has truly gone way beyond intended boundaries.
With the discovery of natural wormholes, along with stabilization technology, interstellar travel from system to system is made incredibly easy. They colonized livable planets and established expansive trade systems throughout space, so humans truly seem to be at the peak of existence.
The main plot follows a small research and exploration (REX) vessel, no more than seven crew members, who, all of a sudden and without warning, are dragged into the immense gravitational pull of a dimensional rift, a previously undiscovered (but theorized) phenomenon. This rift transports the crew into a pocket dimension billions upon billions of years in the past, soon after the beginning of the universe. The commotion on board the ship activates a contingency AI program (aka a CON Series application). A contingency AI’s job is to reorganize the vessel they’re assigned to to put them back onto their mission goals as calmly and efficiently as possible; however, this AI (the working name is Conrad for now) is thrown completely out of his depth with the scenario this little crew has gotten themselves in. There are no protocols for “when your crew is sucked into a previously unknown pocket dimension that transported them to the beginning stages of the universe” so he’s at a complete loss.
And, through the panic of well. That. A high-class prisoner that was being transported aboard the ship (without anyone’s knowledge other than the unofficial captain’s) escapes their holdings and causes much more commotion.
That’s the gist of it at least! I came up with a LOT of lore on AI programs for this universe which I’m really invested in. There’s multiple classes of AI, but it boils down to these for the most part:
Sentient AI
Passive AI
And
Specialized AI
They all have separate functions depending on what they need to be used for, with some overlap occasionally. There stuff with AI-spacecraft bonding, how they’re tested for separate jobs, the subclasses of AI that fall under the main three, lots and lots of stuff. I’m very invested in it.
Specifically, there’s the MAC scale for AI and operation vessel compatibility, used for mid-large size population vessels requiring a sentient AI unit. MAC stands for “Minimized Accountability Control” and basically tests how well an AI is personally suited for mid-heavy population spacecraft, normally being colony vessels. The gist of it is seeing how well an AI can operate the vessel without external guidance in the form of professionally trained and educated personnel. There’s a lot of factors that go into the scoring, all of which can vary in weight depending on what kind of AI a vessel needs. For example, a colony vessel would have a heavier scoring weight in interpersonal connections, meaning how well their personality melds with whatever inhabitants are on that ship.
REX vessels, however, very rarely need sentient AI. They have a passive AI program running in the background, monitoring statistics and adjusting as needed, but there’s no interacting with it because it has no vocal controls, personality database, or personal memory (PM) core. It’s basically a glorified calculator with a mind built for numbers and data processing. Instead of sentient AI, some smaller vessels that go outside of reach of larger spacecraft or planetary bodies have contingency AI instead. It’s technically a subclass under sentient AI, but vary in function. CON (Containment of Organization and Nominization) Series AI have one sole purpose; getting a crew back on track if they lose sight of the overarching goal. They’re coded with thousands of various protocols for nearly any scenario, along with some other required functions
Yeah I went a little wild with this but I’ve been itching to talk about this so thank you HC for once again indulging me
#LONG POST#I’m having so much fun yayyy yippeee#I’m just gonna call this the#Rift Saga#for now#temporary for the time being
3 notes
·
View notes