#ethical hacking course free
Explore tagged Tumblr posts
Text
How Hackers Crack Any Software
youtube
Educational Purposes Only.
Ever wondered how hackers manage to crack software? This video explains the step-by-step techniques hackers use to bypass software activation, from reverse engineering and key generation to online and offline activation exploits. We also cover how developers can protect their creations with secure coding practices, encryption, and obfuscation. While YouTube restricts in-depth demonstrations, Cyberflow’s Academy offers unfiltered, step-by-step guides and expert support to help you master these skills responsibly. Use code "HACKER30" for a 30% discount on membership for the next 48 hours.
#education#educate yourselves#educate yourself#ethical hacking full course#mind hacking#technology#free education#youtube#tips and tricks#ethical hacking#cybersecurity#hacking software#How Hackers Crack Any Software#step by step#hacking tips#hacking#Youtube
3 notes
·
View notes
Text
Idk if anyone else remembers, but Batman canonically carries around Bat-cookies according to the Batman/Scooby-Doo crossover.
I LOVE to think Batman carries them around as snacks for Robin. I love it even more to think he uses said cookies to bribe Robin into good behavior in a similar fashion to Scooby Snacks.
Little Dick Grayson: I don't wanna go to some stupid Gala! U can't make me!
Bruce, in desperation: would u do it for a bat-cookie?
Dick: woah! Bat-shaped! Cool!
Bruce: andddd you can have another one after the party
Dick, mouth full of cookie: okay :)
Bruce, internally: thank fuck a parenting hack that works
Batman: stop! Don't kill him!
Red Hood: and why do I give a fuck what you-
Batman: would u spare his life for a Bat-cookie?
Red Hood:
Red Hood: I'm not a kid anymore-
Batman: they're fresh, look, still warm
Red Hood: ...
Red Hood: this works ONCE. This ONE time. Gimme that damn cookie.
Batman: of course
Red Hood: Fuck I've missed these what the hell does Alfred put in em
Bruce: go to sleep, Tim
Tim: I'm almost done-
Bruce: go to sleep now and you can have a bat-cookie
Tim: a what?
Bruce: a bat-cookie. See? Here, first taste is free. Try it.
Tim: bribery? Really?
Bruce: positive reinforcement
Tim: giving me treats like I'm some kind of dog?
Bruce: try it and then we'll debate the ethics
Tim [eats cookie]:
Tim:
Tim: okay
Bruce: Okay?
Tim: if I promise to sleep a full 8 hours I want two more and a glass of milk
Bruce: u drive a hard bargain but I accept
Dick: aw, c'mon, Damian. One picture. For me, to remember your first day of high school. Do it for a bat-cookie?
Damian: -tt- I've heard of these so-called "bat-cookies" Insulting. I am not a child. I refuse to participate in such an asinine tradition.
Dick: shame. Alfred made animal-friendly ones so you can share with Ace and Batcow. I guess they don't get any treats either, then
Damian: well
Damian: since it would please you so very much, I will overlook this patronizing lapse in judgment
Damian [tries one bite of cookie]:
Damian:
Damian: given Batcows higher food intake requirements, I will require at least a dozen.
Damian [takes another bite]: perhaps two dozen
Duke: you agree I did a good job today?
Bruce: yes? I suppose. Earlier, when you stopped that-
Duke: shut it. Don't care. Cookie me.
Bruce: excuse me?
Duke: I know about the cookies, old man. You've been holding out on me. The cat's out of the bag. I did a good job, I get a cookie. That's how it works, right?
Bruce: uh well
Bruce: that was a long time ago
Bruce: i had to discontinue that method after-
Duke: are you saying I'm not a valid member of this family because I was never Robin?
Bruce: of course you are! But I don't have any on me-
Duke: don't. Lie. To. Me.
Bruce: Okay! Okay. You're right, I'm sorry. Here, take it. Just... do me a favor, and don't go announcing to the whole cave you got-
Duke: YES. MY FIRST BAT-COOKIE! SCORE!
Every batmember in the vicinity: BAT-COOKIES ARE BACK????
Bruce: NO! stay back! Stay back you animals! Alfred! Alfred! It's happening again-
Alfred, sighing: I'll preheat the oven, sir
#tim drake#batfam#batfam headcanons#dick grayson#batman#jason todd#damian wayne#bruce wayne#batfamily#red robin#duke thomas#alfred pennyworth#it's a wonderful tactic for dealing with exactly one child at a time#after the fourth kid Bruce realizes he lost all control over the situation
10K notes
·
View notes
Text
Best Free Ethical Hacking Courses Online with Certificate
Ethical hacking has emerged as one of the most sought-after skills in the ever-evolving world of cybersecurity. With the constant rise in cyber threats, organizations are increasingly turning to ethical hackers, or white hat hackers, to help protect their networks, data, and infrastructure. Ethical hackers play a crucial role in identifying vulnerabilities before malicious actors can exploit…
0 notes
Text
Empower Your Cybersecurity Career with an Ethical Hacking Course in Kolkata

Introduction: In an increasingly digital world, cybersecurity has become a paramount concern for businesses and organizations. To counter the rising tide of cyber threats, there's a growing demand for ethical hackers, also known as white-hat hackers, who can identify vulnerabilities in systems and help strengthen digital defenses. If you're looking to enter the exciting world of ethical hacking, enrolling in an ethical hacking course in Kolkata could be your key to a promising career.
Why Choose Ethical Hacking Training in Kolkata?
Thriving IT Industry: Kolkata is emerging as a significant player in India's Information Technology (IT) landscape. With numerous IT companies and startups operating in the city, the need for skilled cybersecurity professionals is on the rise. By undertaking ethical hacking training in Kolkata, you position yourself advantageously in this thriving job market.
Comprehensive Curriculum: Ethical hacking courses in Kolkata are designed to equip you with the knowledge and skills needed to identify and mitigate cybersecurity threats effectively. The curriculum typically covers areas such as penetration testing, vulnerability assessment, network security, and ethical hacking tools and techniques.
Expert Instructors: Reputable ethical hacking training institutes in Kolkata employ seasoned instructors who are certified ethical hackers themselves. Their industry experience and expertise ensure that you receive top-notch training and practical insights into the world of cybersecurity.
Hands-On Learning: Ethical hacking is a highly practical field. Therefore, ethical hacking courses in Kolkata emphasize hands-on learning experiences. You'll have the opportunity to conduct real-world penetration tests, simulate cyberattacks, and learn how to secure networks and systems effectively.
Certification and Career Support: Upon successful completion of your ethical hacking course, you can obtain industry-recognized certifications such as Certified Ethical Hacker (CEH). These certifications significantly enhance your credibility as a cybersecurity professional. Many training institutes also offer career support services, including job placement assistance, interview preparation, and resume building.
Conclusion: The field of ethical hacking offers an exciting and rewarding career path, and Kolkata provides an ideal setting to embark on this journey. With a booming IT industry, comprehensive training programs, experienced instructors, and a commitment to hands-on learning, ethical hacking courses in Kolkata are your gateway to a successful career in cybersecurity. Protecting digital assets has never been more critical, and ethical hackers play a crucial role in securing our digital world. Enroll in an ethical hacking course in Kolkata today and become a guardian of the digital realm.
0 notes
Text
Masterlist of Free PDF Versions of Textbooks Used in Undergrad SNHU Courses in 2025 C-1 (Jan - Mar)
Literally NONE of the Accounting books are available on libgen, they all have isbns that start with the same numbers, so I think they're made for the school or something. The single Advertising course also didn't have a PDF available.
This list could also be helpful if you just want to learn stuff
NOTE: I only included textbooks that have access codes if it was stated that you won't need the access code ANYWAY
ATH (anthropology)
only one course has an available pdf ATH-205 - In The Beginning: An Introduction to Archaeology
BIO (Biology)
BIO-205 Publication Manual of the American Psychological Association Essentials of Human Anatomy & Physiology 13th Edition
NOTE: These are not the only textbook you need for this class, I couldn't get the other one
CHE (IDK what this is)
CHE-329
The Aging Networks: A Guide to Policy, Programs, and Services
Publication Manual Of The American Psychological Association
CHE-460
Health Communication: Strategies and Skills for a New Era
Publication Manual Of The American Psychological Association
CJ (Criminal Justice)
CJ-303
The Wisdom of Psychopaths: What Saints, Spies, and Serial Killers Can Teach Us About Success
Without Conscious: The Disturbing World of the Psychopaths Among Us
CJ-308
Cybercrime Investigations: a Comprehensive Resource for Everyone
CJ-315
Victimology and Victim Assistance: Advocacy, Intervention, and Restoration
CJ-331
Community and Problem-Oriented Policing: Effectively Addressing Crime and Disorder
CJ-350
Deception Counterdeception and Counterintelligence
NOTE: This is not the only textbook you need for this class, I couldn't find the other one
CJ-405Private Security Today
CJ-408
Strategic Security Management-A Risk Assessment Guide for Decision Makers, Second Edition
COM (Communications)
COM-230
Graphic Design Solutions
COM-325McGraw-Hill's Proofreading Handbook
NOTE: This is not the only book you need for this course, I couldn't find the other one
COM-329
Media Now: Understanding Media, Culture, and Technology
COM-330The Only Business Writing Book You’ll Ever Need
NOTE: This is not the only book you need for this course, I couldn't find the other one
CS (Computer Science)
CS-319Interaction Design
CYB (Cyber Security)
CYB-200Fundamentals of Information Systems Security
CYB-240
Internet and Web Application Security
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-260Legal and Privacy Issues in Information Security
CYB-310
Hands-On Ethical Hacking and Network Defense (MindTap Course List)
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-400
Auditing IT Infrastructures for Compliance
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-420CISSP Official Study Guide
DAT (IDK what this is, but I think it's computer stuff)
DAT-430
Dashboard book
ECO (Economics)
ECO-322
International Economics
ENG (English)
ENG-226 (I'm taking this class rn, highly recommend. The book is good for any writer)
The Bloomsbury Introduction to Creative Writing: Second Edition
ENG-328
Ordinary genius: a guide for the poet within
ENG-329 (I took this course last term. The book I couldn't find is really not necessary, and is in general a bad book. Very ablest. You will, however, need the book I did find, and I recommend it even for people not taking the class. Lots of good short stories.)
100 years of the best American short stories
ENG-341You can't make this stuff up : the complete guide to writing creative nonfiction--from memoir to literary journalism and everything in between
ENG-347
Save The Cat! The Last Book on Screenwriting You'll Ever Need
NOTE: This i snot the only book you need for this course, I couldn't find the other one
ENG-350
Linguistics for Everyone: An Introduction
ENG-351Tell It Slant: Creating, Refining, and Publishing Creative Nonfiction
ENG-359 Crafting Novels & Short Stories: Everything You Need to Know to Write Great Fiction
ENV (Environmental Science)
ENV-101
Essential Environment 6th Edition The Science Behind the Stories
ENV-220
Fieldwork Ready: An introductory Guide to Field Research for Agriculture, Environment, and Soil Scientists
NOTE: You will also need lab stuff
ENV-250
A Pocket Style Manual 9th Edition
ENV-319
The Environmental Case: Translating Values Into Policy
Salzman and Thompson's Environmental Law and Policy
FAS (Fine Arts)
FAS-235Adobe Photoshop Lightroom Classic Classroom in a Book (2023 Release)
FAS-342 History of Modern Art
ALRIGHTY I'm tired, I will probably add ore later though! Good luck!
22 notes
·
View notes
Text
Python for Beginners: Launch Your Tech Career with Coding Skills
Are you ready to launch your tech career but don’t know where to start? Learning Python is one of the best ways to break into the world of technology—even if you have zero coding experience.
In this guide, we’ll explore how Python for beginners can be your gateway to a rewarding career in software development, data science, automation, and more.
Why Python Is the Perfect Language for Beginners
Python has become the go-to programming language for beginners and professionals alike—and for good reason:
Simple syntax: Python reads like plain English, making it easy to learn.
High demand: Industries spanning the spectrum are actively seeking Python developers to fuel their technological advancements.
Versatile applications: Python's versatility shines as it powers everything from crafting websites to driving artificial intelligence and dissecting data.
Whether you want to become a software developer, data analyst, or AI engineer, Python lays the foundation.
What Can You Do With Python?
Python is not just a beginner language—it’s a career-building tool. Here are just a few career paths where Python is essential:
Web Development: Frameworks like Django and Flask make it easy to build powerful web applications. You can even enroll in a Python Course in Kochi to gain hands-on experience with real-world web projects.
Data Science & Analytics: For professionals tackling data analysis and visualization, the Python ecosystem, featuring powerhouses like Pandas, NumPy, and Matplotlib, sets the benchmark.
Machine Learning & AI: Spearheading advancements in artificial intelligence development, Python boasts powerful tools such as TensorFlow and scikit-learn.
Automation & Scripting: Simple yet effective Python scripts offer a pathway to amplified efficiency by automating routine workflows.
Cybersecurity & Networking: The application of Python is expanding into crucial domains such as ethical hacking, penetration testing, and the automation of network processes.
How to Get Started with Python
Starting your Python journey doesn't require a computer science degree. Success hinges on a focused commitment combined with a thoughtfully structured educational approach.
Step 1: Install Python
Download and install Python from python.org. It's free and available for all platforms.
Step 2: Choose an IDE
Use beginner-friendly tools like Thonny, PyCharm, or VS Code to write your code.
Step 3: Learn the Basics
Focus on:
Variables and data types
Conditional statements
Loops
Functions
Lists and dictionaries
If you prefer guided learning, a reputable Python Institute in Kochi can offer structured programs and mentorship to help you grasp core concepts efficiently.
Step 4: Build Projects
Learning by doing is key. Start small:
Build a calculator
Automate file organization
Create a to-do list app
As your skills grow, you can tackle more complex projects like data dashboards or web apps.
How Python Skills Can Boost Your Career
Adding Python to your resume instantly opens up new opportunities. Here's how it helps:
Higher employability: Python is one of the top 3 most in-demand programming languages.
Better salaries: Python developers earn competitive salaries across the globe.
Remote job opportunities: Many Python-related jobs are available remotely, offering flexibility.
Even if you're not aiming to be a full-time developer, Python skills can enhance careers in marketing, finance, research, and product management.
If you're serious about starting a career in tech, learning Python is the smartest first step you can take. It’s beginner-friendly, powerful, and widely used across industries.
Whether you're a student, job switcher, or just curious about programming, Python for beginners can unlock countless career opportunities. Invest time in learning today—and start building the future you want in tech.
Globally recognized as a premier educational hub, DataMites Institute delivers in-depth training programs across the pivotal fields of data science, artificial intelligence, and machine learning. They provide expert-led courses designed for both beginners and professionals aiming to boost their careers.
Python Modules Explained - Different Types and Functions - Python Tutorial
youtube
#python course#python training#python#learnpython#pythoncourseinindia#pythoncourseinkochi#pythoninstitute#python for data science#Youtube
3 notes
·
View notes
Text
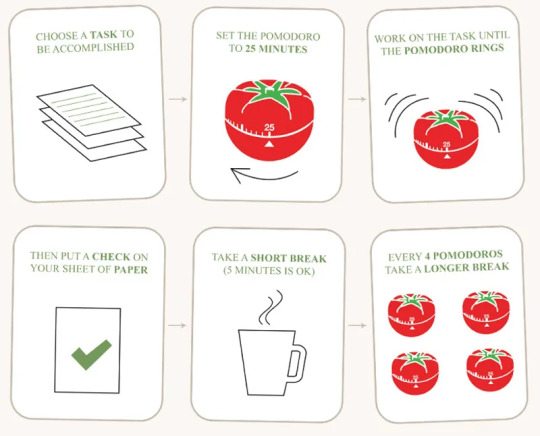
WHAT IS POMODORO AND WHAT DO YOU EAT IT WITH?
First… what is the Pomodoro method?!
The Pomodoro (Italian for tomato) technique was created by Francesco Cirillo in the 80s. Cirillo is an author and owner of a consulting company. He created this time managing technique that breaks down your study time into manageable intervals with breaks between each study session. With the countless distractions we have today, there’s no wonder it is still one of the most popular and helpful techniques for increasing productivity!
1. You need to plan your tasks
This will help you gauge how many sessions you will need. Will you be reading? Watching a lecture and taking notes? When planning what I will study, I know that watching a lecture and taking notes will take me sooo much longer than doing a reading or flashcards (less strenuous things). I also know that my core science courses will typically take much more studying time than one of my electives.
Determine what is most time-consuming and plan accordingly. The Pomodoro method is perfect for concentrating on any task, but you want to have in mind the classes that require more focus and time than others.
2. Set a 25-minute timer
25 minutes is only a recommendation and you can increase the time or lower it depending on how long you believe you can stay focused without interruptions. I mean, I don’t recommend you set a 5-minute timer to study and then a 5-minute break. But a session somewhere between 20-30 minutes is great (and how long I set my timer while studying)!
One other thing that Cirillo notes is that this time cannot be broken. You must work the entire 25 minutes without any distractions! One of my favorite ways to cancel out distractions is to:
-Put my phone in another room, or in my closet
-Or use the Forest app, which is a timer app that restricts you from leaving the app while completing work/other tasks. This guarantees I stay on task the whole time I am working!
3. Set a 5-minute timer for a break
Between each 25-minute study session, you need a break. You deserve it! So Cirillo recommends only a 5-minute break in between each study session. Do something that doesn’t bring you stress.
Tip: Make sure you do NOT work throughout the break at all. This break is meant to be a relaxing period to take your mind off of your work.
4. Repeat the process 3 times
This studying technique includes four sessions. So do this same process 3 more times. Work diligently and remember to stay focused.
5. After your 4th session, extend the break time to 20-30 minutes long
Once you have finished your fourth session, take a longer break! This is a huge accomplishment and after you have completed it, you will (and should) be so proud. The longer break allows you to take your mind off of your work and reset so you can get back into it.
Why It Benefits You...
IT WORKS FOR ANY TASK
Don’t think I only use this productivity hack for studying! This can be used while cleaning, organizing, reading, and so many other things! Remember, you can tweak the time frames depending on the task and depending on how much time you have to complete it. This is an amazing life hack that I believe everyone should be implementing to help with time management.
IMPROVES CONCENTRATION
Like I noted earlier, this is a distraction-free strategy! It’s on you to remove the distractions from your sessions, and when you do, you will see significant improvements in your work ethic. This technique was created to allow complete concentration on the task at hand. It will improve your focus, productivity, and concentration.
BEATS PROCRASTINATION
The Pomodoro technique breaks the time down into consumable segments. Would you feel more confident with saying you will study for 2 hours or 4 sessions of 25 minutes? I’m confident I would choose the latter every single time. This technique gives our brains manageable chunks of time to study so we result in more work getting done in the end. So just start working!
REMEMBER TO UTILIZE YOUR BREAKS
by Ania Henderson
#university#blogger#study blog#study motivation#study#study aesthetic#study buddy#study hard#study space#study tips#studygram#studyspo#studystudystudy
31 notes
·
View notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes
Text
🚀 Unlock the Secrets of App Security! 💻 Learn ethical hacking & secure coding from scratch with our FREE App Hacking Course! ✅ Beginner-friendly ✅ Real-world scenarios ✅ 100% free to join!
🔗 Start now: Enroll for Free
Let me know if you'd like to incorporate this into your site or need help formatting it for different platforms!

4 notes
·
View notes
Text
i’ve been very inactive, so here’s an update on my life:
i got a new job and now make double of what i was making. it’s 5 minutes from where i moved out to, gives me free internet and television, and my job is paying for me to take IT courses like comptia IT fundamentals, a+, network+, security+, cyber security+, pentest+ (ethical hacking), and so on to get me any certification i want. they will also pay to put me through college. i like this job. [:
also the medication i take for my hypersomnia went missing so i have had 0 spoons and have been very sleepy for months now. i got 0 energy.

7 notes
·
View notes
Text
Free Online Courses: Unlock Your Potential

Develop your skills and gain new knowledge with our variety of free online courses. Unlock your potential and reach new heights with our range of high-quality learning resources.
Subjects :
Free Online Renewable Energy Courses
__________
Free Logistics and Supply Chain Courses
__________
Free Online Business Management Courses
__________
Free Technology and Programming Courses
__________
Free Data Science and Analytics Courses
__________
Free Online Language and Communication Courses
__________
Free Finance and Accounting Courses
__________
Free Courses in Marketing and Social Media
__________
Free Human Resources Management Courses
__________
Free Cybersecurity and Ethical Hacking Courses
__________
Free Online Courses in Machine Learning & AI
__________
Free Online Courses for Sales & Customer Service
__________
Free Photography and Videography Courses
__________
Free Environmental Studies and Sustainability Courses
__________
Free Management & Leadership Courses
__________
Free Design and Creativity Courses
__________
Free Online Health and Nutrition Courses
__________
Free Online Project Management Courses
__________
Free Product Management Courses
__________
Free Safety and Security Courses
__________
Free Online Science and Math Courses
__________
Free Skills Development Courses
__________
Free Career Development Courses
__________
Free Lifestyle and Hobbies Courses
__________
Free English Online Courses
__________
Free Social Sciences and Humanities Courses
__________
Free CSR Online Courses
#career#australia#canada#usa#jobseekers#jobsearch#jobs#employment#employees#work#elearning#course#online learning#online courses#education#university#free online courses#development#japan#singapore#new zealand#learn online#learning#language learning#teaching#students#learn
8 notes
·
View notes
Text
youtube
How I Got a 100% Free Lifetime Server (And You Can Too!)
Learn how to set up a high-powered Linux server with 24 GB RAM, 4 CPUs, and 200 GB storage for free, forever, using Oracle Cloud's "Always Free" tier. In this step-by-step guide, I’ll show you everything you need—from signing up to configuring your server and accessing it via SSH. This isn’t a trial—it’s a permanent solution perfect for developers, tech enthusiasts, and anyone looking to host projects at zero cost. Plus, discover how Cyberflow's Academy can help you secure and optimize your server with in-depth hacking courses, personal guidance, and more.
#education#Free Lifetime Server#How to get a Free Lifetime Server#Free Server#hacking#technology#educate yourself#youtube#tips and tricks#educate yourselves#free education#how to get a free server#oracle cloud#ethical hacking full course#Youtube
1 note
·
View note
Note
This is the for the "DVD commentary" ask meme. I ... am not sure I want to paste in 500 words or count them. So if you want, could you do a DVD commentary for the "Watcher X Escapes" fic you wrote, I know you talked about it a bit, but I really liked the dialogue between X and Kyrian.
Watcher X is such a fascinating character. He pretty much tells the Agent he’s only helping them/the Empire because of his conditioning, yet a lot of his conversations with the Agent have this odd mentoring aspect to them. To lull them into a false sense of security? To win them over? Because he does have some loyalty to the Empire? Because he feels some connection to or pity for the Agent, who is almost certainly doomed to some fate at least as unpleasant as his own?
Nothing about him is straightforward; there’s always this sense of something hidden. He’s a man who always has something up his sleeve, some ulterior motive, some plan he hasn’t revealed. I know he’s supposed to be a product of the Watcher design program like Watcher Two, but I have trouble not thinking of him as someone who’s been in the field. There’s just something about the kind of advice/suggestions he offers that feels like personal experience, not just a previous career of advising other people in the field.
In any event, he’s far too skilled and far too clever for his potential in-game end. Hence the fic.
And I wanted to keep that sense of hidden motives about him for his dialogue with Kyrian.
Is everything X says just manipulation, waiting for the right moment to use the secondary function he'd rigged in the implants? Is he just messing with them, like Kaliyo thinks? Or is he trying to find a way to end their stand-off of sorts peacefully?
Or is the whole conversation something of a Xanatos Gambit? Whatever happens, he wins, because the only option that might have prevented him from escaping wasn’t actually on the table. (He clearly has Kyrian figured out well enough to know that.)
Kyrian, conversely, has no option open to him that he likes. He can’t just let X go because Kaliyo won’t go for it and there’s a good chance that Watcher Two has hacked into any available security cameras and is watching the whole thing. He doesn’t really want to try and drag X back to Shadow Town (not that he thinks he could) and knows he can’t just convince him to go back. (Why would anyone?) And he definitely doesn’t want to shoot him.
What he wants is to somehow manifest a solution that works out for everyone. Even though he knows that’s somewhere between wildly unlikely and impossible.
So we start with game dialogue. With clever, twisty X who, as always, has something up his sleeve. And immediately take a left turn as Kyrian tries to convince them both that there is some magical third option, that maybe there’s a way to convince Intelligence that X should be rewarded for his efforts.
There’s not, of course.
The irony, or something like irony, of the situation is that the conversation is a battle of wits between two people who basically want the same outcome and neither of them can talk their way to it, largely for reasons that are out of their control. The only person in the hanger who wants X dead or back in Shadow Town is Kaliyo.
X knows Kyrian doesn’t have the power to convince Intelligence to set him free or reinstate him or anything that’s not (at best!) stick him back in Shadow Town. Kyrian isn’t ready to acknowledge that he’s not loyal to the Empire, or at least that his sense of morality and ethics and compassion and all the other things a field agent shouldn’t have will always outweigh his loyalty.
Though I do hope the audience is as amused as X is when Kyrian's response to X noting that he's clearly not a proper Cipher agent because he keeps trying to find "soft, inefficient solutions" is to...keep trying to find, or sell, a soft solution to their standoff.
Then again, Kyrian's also right that X is stalling (or also stalling), since X has the ability to end their apparent impasse at any time. Perhaps X really does think he can get Kyrian to realize that he and his career are doomed. Something makes him wait until the last moment, anyway, even if its merely a sense of drama.
And the lesson Kyrian learns is not: “if you’re supposed to shoot someone, don’t talk to them first” it’s: “maybe I’m not entirely loyal to the Empire.” Now that the question he hadn’t dared to ask himself has been asked, it can’t be unasked.
Though the lesson he probably should have learned was: "get out while the getting's good." Somewhere out there, Watcher X must be so disappointed in how Kyrian's career ended.
6 notes
·
View notes
Text
WIP Wednesday
I know I've missed the last couple but honestly all I've been working on in my free time is the secret project, which (for reasons I feel like should be fairly obvious) I'm trying not to share in WIP Wednesday posts lol. But anyway I've also now started on Chapter 13 of Soldier, Poet, King, so here's a brief moment of A-Qing and Jin Guangyao talking about Xue Yang that I made myself laugh with a little bit
--//--
“Told you he’s feral,” young A-Qing mutters under her breath, sounding mutinous around the chak-chak-chak of chomping on her ever-present bubblegum.
“Yes dear we know he is, and something tells me that cracking open the brain of an interdimensional lovecraftian nightmare so he could try slurping the contents out like a slushee, metaphorically speaking, hasn’t improved things very much,” he replies and feels oddly vindicated when she snorts a laugh into the back of her hand.
A-Qing is…unexpected. He’d heard her calling for Xue Yang to come upstairs that night he and Nie Huaisang had gone to see him at The Cockpit, though of course that evening he hadn’t known precisely who she was or why she felt she had the right to boss Xue Yang around. Finding out that she’s the once-wayward-child-turned-protegé of the Immortals (and that her ethics are significantly more dubious than her benefactors’) had been..a surprise, to put it mildly. Not that he thinks that Xiao Xingchen and Song Zichen aren’t perfectly capable guardians, of course, but rather he’s surprised that two distinguished gentlemen such as themselves seem very fond of collecting people who could be reasonably compared to scrungly alley cats and ignoring all their mange and fleas in favor of cooing over how sweet and brilliant they are.
And they are (brilliant, at least, though not any given definition of sweet to anyone except their ‘daozhangs’), but the contrasts at play in their little fucked up family of four are still a bit of a mystery to Jin Guangyao.
It had been A-Qing, apparently, who had hacked the CCTV and the ‘dome’s video feeds long enough to broadcast Jin Guangshan and Jin Zixun’s deaths straight to the communications tower, and as such Nie Mingjue has instructed that she give their security team an extremely thorough rundown of every breach in their defenses that she had exploited. Jin Guangyao still desperately wishes someone had thought to record Nie Mingjue’s reaction when the girl, -- standing no taller than his abs and thoroughly uncaring of the danger she was putting herself in -- had laughed in his face, popped her bubblegum, and told him that it had taken no longer than an hour that afternoon to get her hands on everything digital in the ‘dome, not just their camera feeds. He hasn’t seen his lover turn that shade of red in a very long time, nor ever seen him so clearly tempted to shout at someone younger than half his age.
Anyway — she’d taken a shine to Jin Guangyao within minutes of Lan Xichen ushering everyone into the ‘dome to avoid further scrutiny by the press, easily picking him out as the adult in the room besides her beloved daozhangs who would be most likely to indulge her quasi-legal and morally gray brand of ethics. So now here she sits, tinkering around with something Wei Wuxian had given her to turn into a signal jammer for anyone outside the ‘dome not on their frequencies, and Jin Guangyao has found himself on ersatz babysitting duty.
(She is also, according to Xiao Xingchen, worried about Xue Yang’s health and wouldn’t be able to focus well working somewhere she can’t keep an eye on his condition; an assessment which Jin Guangyao very politely and very secretly thinks is a load of horseshit.)
6 notes
·
View notes
Text
Samsung Galaxy Z Fold 7 could launch with a big free bonus – and it's good news for AI fans
Unlock the Secrets of Ethical Hacking! Ready to dive into the world of offensive security? This course gives you the Black Hat hacker’s perspective, teaching you attack techniques to defend against malicious activity. Learn to hack Android and Windows systems, create undetectable malware and ransomware, and even master spoofing techniques. Start your first hack in just one hour! Enroll now and…
0 notes
Text

SkillSchool Free Cybersecurity Certification Training is your gateway into one of the world’s fastest-growing fields. In just one week, you'll gain real-world knowledge across six expert-designed modules — from foundational concepts and threat detection to ethical hacking, digital forensics, and cryptography. Whether you're a total beginner or looking to sharpen your skills, this beginner-friendly, self-paced online course equips you with essential tools to protect digital systems and data. Learn from industry professionals, engage in interactive lessons, and earn a recognized certificate at zero cost.
Click here to Know more: https://www.skillschool.co.in/courses/free-cybersecurity-certification-training/
0 notes