#accessible web development
Text
Improving Website Accessibility for Small Businesses
Did you know that about 16% of people worldwide have a permanent disability1? This fact shows how crucial it is for small businesses to make their websites accessible to everyone. In fact, 70% of shoppers want brands to take action on social issues, including making websites easy for people with disabilities1.
More than 90% of people don’t complain about website issues, but 69% with disabilities…
#Accessible Web Development#ADA Compliance#Digital Accessibility#Inclusive Website Design#SEO for Small Businesses#Small Business Websites#User-Friendly Websites#Web Accessibility#Web Accessibility Tools#Website Design Best Practices
0 notes
Text
#Accessible Websites#Accessible Web Development#Accessible Development#WCAG#Section 508#Screen Readers#Disabilities#Accessible Design#Alt Text Image#Color Contrast#Assistive Technologies#Screen Magnifiers#HTML5 Elements#Aria#Manual testing#Automated Testing#User Testing#Accessibility Tools#Web Accessibility Consulting#Web accessibility#web accessibility Audit#Accessibility Audit#Website Accessibility#Designer Accessibility#web development#Accessibility Services#AELData
0 notes
Text
Wix Learn's Free Web Accessibility Certification | Resources ✨

Hiya! 💗 Today, I stumbled upon an absolute gem that I wanted to share with all of you. If you're learning about web design and inclusivity as I am, this is something you might want to look into~!
Introducing the Web Accessibility Course by Wix Learn - a game-changer for anyone striving to create websites that cater to all users, regardless of impairments. This comprehensive course covers everything you need to know to build an inclusive online space that leaves no one behind. AND IT COMES WITH AN EXAM AND CERTIFICATE (all free too hehe).
In this course, you'll gain mastery over essential skills, including:
🌐 Creating Inclusive Sites: Learn the best practices to make your websites accessible to people with various impairments, ensuring equal access for everyone.
📚 Accessible Title Tags and Headings: Dive into the world of proper title tags and heading structures, making navigation a breeze for every visitor.
👁️🗨️ Crafting Alt Text and Alternative Media: Discover the art of writing meaningful alt text and incorporating alternative media, providing a seamless experience for those with visual challenges.
⚙️ Optimizing Navigation for Assisted Technology Users: Enhance site navigation for individuals relying on assisted technologies, making their browsing experience smooth and efficient.
💬 The Power of an Accessibility Statement: Learn to create a compelling accessibility statement, showcasing your dedication to inclusivity and informing visitors about your website's accessibility features.
They even have prep courses for the exam! 🤗✨
Here's the link to the course: LINK
Hope this helps someone out there, I will be trying it out and seeing how it goes! 👍🏾
#resources#web accessibility#coding#codeblr#programming#progblr#studyblr#studying#tech#software developer#comp sci#programmer#learning to code#webdesign#web design#web development
284 notes
·
View notes
Text
Hey how does one add an image description to an image in HTML
5 notes
·
View notes
Text
If you're tired of Google cluttering up the search filter buttons with (ir)relevant keywords, I wrote an extension to help make the important ones more prominent in the hopes of bringing back user accessibility to Google Search Results.
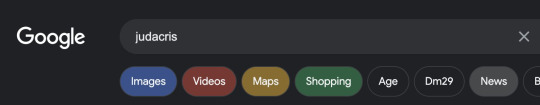


It's hosted on my github and you need to install it manually like any third-party extension, but it should work on Chrome and Edge.
26 notes
·
View notes
Text
𝗟𝗼𝗼𝗸𝗶𝗻𝗴 𝗳𝗼𝗿 𝘀𝗼𝗺𝗲 𝗨𝗜/𝗨𝗫 W𝗲𝗯𝘀𝗶𝘁𝗲 𝗶𝗻𝘀𝗽𝗶𝗿𝗮𝘁𝗶𝗼𝗻?

Check out #UxTitan top picks! We’ve handpicked a selection of visually stunning, user-friendly sites that are sure to impress.
𝗛𝗲𝗿𝗲’𝘀 𝘄𝗵𝗮𝘁 𝘆𝗼𝘂’𝗹𝗹 𝗹𝗼𝘃𝗲:
✅ Sleek designs that are eye-catching and intuitive to navigate
✅ Innovative features that elevate the user experience
✅ Websites crafted to deliver seamless and efficient interactions
Want to see more? Follow us at @uxtitan_official and get inspired by exceptional web design! We can't wait to hear what you think!
#artists on tumblr#batman#bill cipher#billford#deadpool and wolverine#dungeon meshi#gravity falls#house of the dragon#hugh jackman#jujutsu kaisen#web development#web design#web graphics#web weaving#tech#technology#graphic design#ui ux design#ui ux company#ui ux development services#ui ux agency#ui ux development company#productdesign#userexperience#website agency#website analytics#website and app development company#website accessibility#website audit#digital marketing
4 notes
·
View notes
Text




Sorry I haven’t posted any new comics or cartoons lately. My website died recently and I’ve been taking time to fix it. Today’s comic is a repost from 2017, and honestly is probably the exact reason why my website is dead right now. Webdev is fun 🙃
I’m also taking medication that makes me super productive, BUT only if I focus on one thing at a time. The moment I start switching between tasks, everything breaks down and suddenly it’s 4am and I’m on Wikipedia researching Canada goose migration patterns and how to bake my own bread.
Thanks, ADHD.
Thanks for your patience 🫶🏽
89 notes
·
View notes
Text
Dive into the world where human intuition seamlessly integrates with AI brilliance in web development. Elevate your online presence with the perfect fusion of creativity and technology.
#Benefits of incorporating human touch in AI-driven web development#Enhancing user experience through human-centered AI web development#Balancing automation and human input in modern web development#The role of empathy in AI-driven web design and development#Strategies for infusing creativity into AI-powered web development#Understanding user behavior for personalized AI web development#Building trust through human-like interactions in AI web development#Improving accessibility with human-centric AI web design#Ethical considerations in integrating human touch with AI in web development#Tailoring AI algorithms for diverse user experiences in web development
4 notes
·
View notes
Text
Anticipating the future of malicious open-source packages: next gen insights
New Post has been published on https://thedigitalinsider.com/anticipating-the-future-of-malicious-open-source-packages-next-gen-insights/
Anticipating the future of malicious open-source packages: next gen insights


Ori Abramovsky is the Head of Data Science of the Developer-First group at Check Point, where he leads the development and application of machine learning models to the source code domain. With extensive experience in various machine learning types, Ori specializes in bringing AI applications to life. He is committed to bridging the gap between theory and real-world application and is passionate about harnessing the power of AI to solve complex business challenges.
In this thoughtful and incisive interview, Check Point’s Developer-First Head of Data Science, Ori Abramovsky discusses malicious open-source packages. While malicious open-source packages aren’t new, their popularity among hackers is increasing. Discover attack vectors, how malicious packages conceal their intent, and risk mitigation measures. The best prevention measure is…Read the interview to find out.
What kinds of trends are you seeing in relation to malicious open-source packages?
The main trend we’re seeing relates to the increasing sophistication and prevalence of malicious open-source packages. While registries are implementing stricter measures, such as PyPI’s recent mandate for users to adopt two-factor authentication, the advances of Large Language Models (LLMs) pose significant challenges to safeguarding against such threats. Previously, hackers needed substantial expertise in order to create malicious packages. Now, all they need is access to LLMs and to find the right prompts for them. The barriers to entry have significantly decreased.
While LLMs democratise knowledge, they also make it much easier to distribute malicious techniques. As a result, it’s fair to assume that we should anticipate an increasing volume of sophisticated attacks. Moreover, we’re already in the middle of that shift, seeing these attacks extending beyond traditional domains like NPM and PyPI, manifesting in various forms such as malicious VSCode extensions and compromised Hugging Face models. To sum it up, the accessibility of LLMs empowers malicious actors, indicating a need for heightened vigilance across all open-source domains. Exciting yet challenging times lie ahead, necessitating preparedness.
Are there specific attack types that are most popular among hackers, and if so, what are they?
Malicious open-source packages can be applied based on the stage of infection: install (as part of the install process), first use (once the package has been imported), and runtime (infection is hidden as part of some functionality and will be activated once the user will use that functionality). Install and first use attacks typically employ simpler techniques; prioritizing volume over complexity, aiming to remain undetected long enough to infect users (assuming that some users will mistakenly install them). In contrast, runtime attacks are typically more sophisticated, with hackers investing efforts in concealing their malicious intent. As a result, the attacks are harder to detect, but come with a pricier tag. They last longer and therefore have higher chances of becoming a zero-day affecting more users.
Malicious packages employ diverse methods to conceal their intent, ranging from manipulating package structures (the simpler ones will commonly include only the malicious code, the more sophisticated ones can even be an exact copy of a legit package), to employing various obfuscation techniques (from classic methods such as base64 encoding, to more advanced techniques, such as steganography). The downside of using such concealment methods can make them susceptible to detection, as many Yara detection rules specifically target these signs of obfuscation. Given the emergence of Large Language Models (LLMs), hackers have greater access to advanced techniques for hiding malicious intent and we should expect to see more sophisticated and innovative concealment methods in the future.
Hackers tend to exploit opportunities where hacking is easier or more likely, with studies indicating a preference for targeting dynamic installation flows in registries like PyPI and NPM due to their simplicity in generating attacks. While research suggests a higher prevalence of such attacks in source code languages with dynamic installation flows, the accessibility of LLMs facilitates the adaptation of these attacks to new platforms, potentially leading hackers to explore less visible domains for their malicious activities.
How can organisations mitigate the risk associated with malicious open-source packages? How can CISOs ensure protection/prevention?
The foremost strategy for organisations to mitigate the risk posed by malicious open-source packages is through education. One should not use open-source code without properly knowing its origins. Ignorance in this realm does not lead to bliss. Therefore, implementing practices such as double-checking the authenticity of packages before installation is crucial. Looking into aspects like the accuracy of package descriptions, their reputation, community engagement (such as stars and user feedback), the quality of documentation in the associated GitHub repository, and its track record of reliability is also critical. By paying attention to these details, organisations can significantly reduce the likelihood of falling victim to malicious packages.
The fundamental challenge lies in addressing the ignorance regarding the risks associated with open-source software. Many users fail to recognize the potential threats and consequently, are prone to exploring and installing new packages without adequate scrutiny. Therefore, it is incumbent upon Chief Information Security Officers (CISOs) to actively participate in the decision-making process regarding the selection and usage of open-source packages within their organisations.
Despite best efforts, mistakes can still occur. To bolster defences, organisations should implement complementary protection services designed to monitor and verify the integrity of packages being installed. These measures serve as an additional layer of defence, helping to detect and mitigate potential threats in real-time.
What role does threat intelligence play in identifying and mitigating risks related to open-source packages?
Traditionally, threat intelligence has played a crucial role in identifying and mitigating risks associated with open-source packages. Dark web forums and other underground channels were primary sources for discussing and sharing malicious code snippets. This allowed security professionals to monitor and defend against these snippets using straightforward Yara rules. Additionally, threat intelligence facilitated the identification of suspicious package owners and related GitHub repositories, aiding in the early detection of potential threats. While effective for simpler cases of malicious code, this approach may struggle to keep pace with the evolving sophistication of attacks, particularly in light of advancements like Large Language Models (LLMs).
These days, with the rise of LLMs, it’s reasonable to expect hackers to innovate new methods through which to conduct malicious activity, prioritizing novel techniques over rehashing old samples that are easily identifiable by Yara rules. Consequently, while threat intelligence remains valuable, it should be supplemented with more advanced analysis techniques to thoroughly assess the integrity of open-source packages. This combined approach ensures a comprehensive defence against emerging threats, especially within less-monitored ecosystems, where traditional threat intelligence may be less effective.
What to anticipate in the future?
The emergence of Large Language Models (LLMs) is revolutionising every aspect of the software world, including the malicious domain. From the perspective of hackers, this development’s immediate implication equates to more complicated malicious attacks, more diverse attacks and more attacks, in general (leveraging LLMs to optimise strategies). Looking forward, we should anticipate hackers trying to target the LLMs themselves, using techniques like prompt injection or by trying to attack the LLM agents. New types and domains of malicious attacks are probably about to emerge.
Looking at the malicious open-source packages domain in general, a place we should probably start watching is Github. Historically, malicious campaigns have targeted open-source registries such as PyPI and NPM, with auxiliary support from platforms like GitHub, Dropbox, and Pastebin for hosting malicious components or publishing exploited data pieces. However, as these registries adopt more stringent security measures and become increasingly monitored, hackers are likely to seek out new “dark spots” such as extensions, marketplaces, and GitHub itself. Consequently, malicious code has the potential to infiltrate EVERY open-source component we utilise, necessitating vigilance and proactive measures to safeguard against such threats.
#Accessibility#ai#Analysis#applications#approach#attention#authentication#Business#challenge#Check Point#CISOs#code#Community#complexity#comprehensive#Dark#Dark web#data#data privacy#data protection#data science#details#detection#Developer#development#documentation#domains#double#dropbox#Ecosystems
3 notes
·
View notes
Text
Anyone gotten these variations yet? 👀



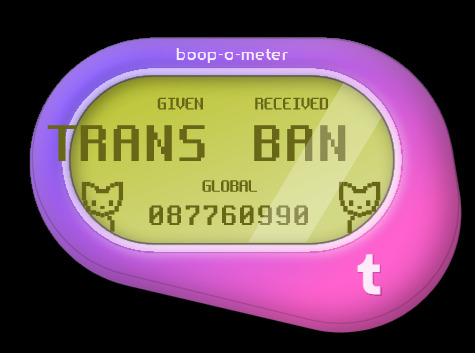

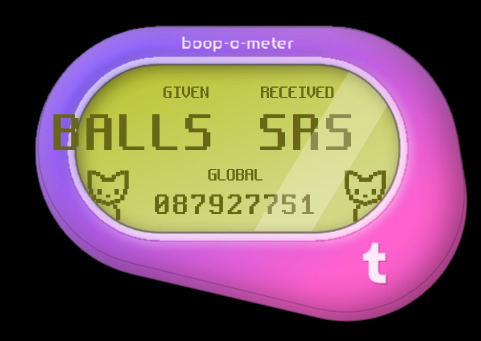
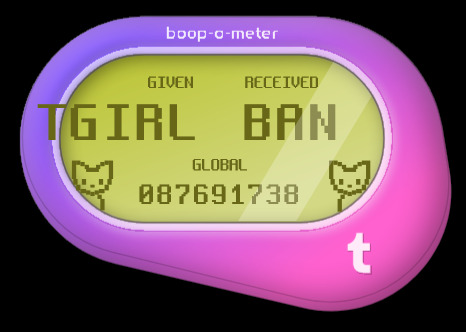
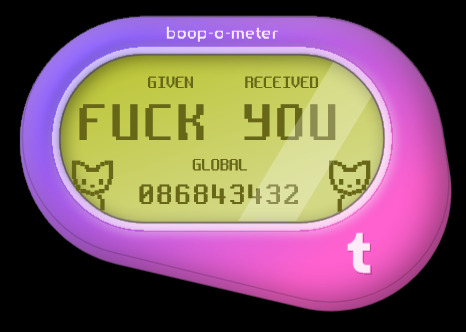


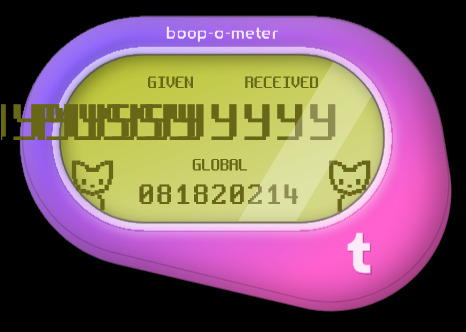
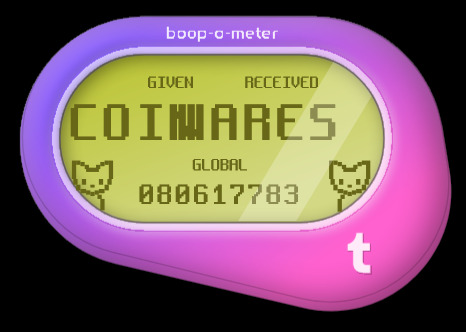
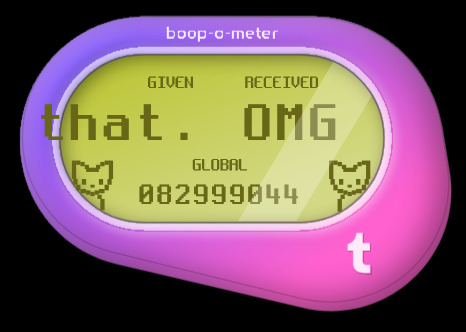
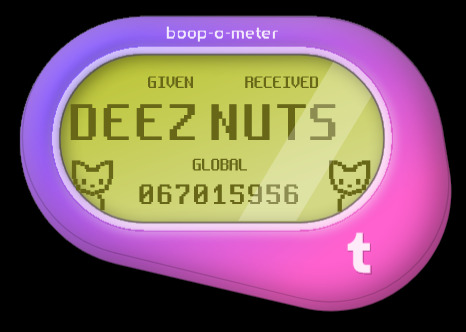
#is tumblr trying to tell us something?#how did some of these even get approved?? wild to me!#hey speaking of wild things did you know firefox has web developer tools?#& in those web dev tools they have these areas in the code called div tags; go explore have fun!#some of these are in reference to things on these are just silly#I made so many of these it took 3 posts; I'll post some screenshots in a bit too about some interesting bts stuff#believe it or not those cats aren't image files#I actually tried to access some stuff but a lot of it seems to be locked server side so I can't rip from the source easily#& who knows how long the boop meter will remain up on the site#mine#op#boop o meter#trans memes#transgender memes
6 notes
·
View notes
Text
2 notes
·
View notes
Text
Accessibility Tip #3 (long Awaited, I'm so sorry)
youtube
If you create content on the web, you should be familiar with these and try your best to follow these guidelines. Afrika does a great job of explaining them in a relatable way.
2 notes
·
View notes
Text


My Neocities site has a layout now! There's still more to do, but I want to try working on actual pages next. All that exists is the home page at the moment.
Also, all of the site will come with a "Plain HTML" alternative to it.
I plan on creating my HTML and CSS guides with full accessibility practices taught from the get-go. Doing bare bones text formatting? I want others to learn right away that there are best practices for that too when it comes to screen readers. Making sure things are in the right reading order before you do any styling on 'em.
Keep an eye out for this if you're interested! I've been wanting to make web design guides for years now - and I'm confident at this stage to go for it. Especially since uh, I've shared a lot of my web dev thoughts/advice/resources here on Tumblr already... But it can get buried or awkward to find that on my varied blog. I'm eager to have this stuff all in one place... And it'll be more flexible to work with since it won't be inside a Tumblr post.
URL: https://wolfkat-webdev.neocities.org/
#web design#web development#accessibility#neocities#indie web#wk speaks#wk works#my art#html#css#my wd work
5 notes
·
View notes
Text
Learn Web Accessibility | Resources ✨
Web.Dev has a section called "Learn Accessibility" that talks about how to make your websites and code more accessible for others!
>> Link to Learn Accessibility - Web.Dev
#resources#coding resources#studying#programming#coding#studyblr#codeblr#progblr#comp sci#html5#html#web dev#web accessibility#accessibility#web development
342 notes
·
View notes
Text
I used to use a free drawing website as my introduction to digital art. The thing is, the site I used would time out and give your prompt to somebody else if you took too long, and the only way to "save" a drawing would be to not close the tab... and I hated that uncertainty of whether it would still be there when I got back, or if my prompt would be given to somebody else. So I got very used to sitting down and doing an entire drawing, start to finish, in one sitting. I still struggle to remember to save in csp BEFORE I FINISH THE ENTIRE DRAWING because of this years-long habit I built. Spending more than 2 hours on art is exhausting!!! I've only ever lost I think two drawings on csp though because (my beloved) it comes with an auto save feature, and the tablet I used to use that would crash my computer sometimes is no longer with us. Thankfully.
#random anectdote time I guess#I'm being vague abt the website in question on purpose#because if you look at it now it just. the community looks so terrible.#and it's because all the cool people stopped using it.#also the site itself barely works and for six months in 2019 you couldn't even access it#things grow and change and web developers forget about their websites. that's how it goes#ghostly posts#I accidentally tagged this as dp so sorry🥺🥺#the tags are glitching sooo bad for me rn it's not even funny#it saved the wrong ti#Hm. nooooooooooo it's I visit#bsjsnznsjns 👋😟👀😎🤨😟😟🤨🖌️🥺🖌️🥺🥺😟😟😟👋👋👋👋👋👋#the e. the keyboard it's I#ITS INVISIBLE.#HOW FO YOU TYPE ON PHONE LIKE THIS WH#HELP HOW DOES THIS HAPPEN#I CAN TOUCH TYPE BUT THERES NOTHING TO TOU H ON A OHIENS CRESBB. ON A OHONE SCREEN#AH#legit the keyboard disappears I have a small video as proof. it's back now though.#okay ANYWAY sorry to accidentally tag dp.
2 notes
·
View notes
Text
visit my new tag #ellis's adventures in late capitalism customer service and predatory business practices for highly entertaining accounts of my experiences dealing with any kind of company's or government's wonderful treatment of their obviously very strongly valued customers and their very astronomically high quality offered services
#psalms#a new tag for any rant posts like the last one i just made or the one from a few weeks ago about the fun of cancelling a subscription#under the influence of current day late capitalism business management practices#truly makes me feel seen and cared for as a client i promise you#10/10 customer service would recommend if you want to have a laff at how hilariously atrocious someone is at doing their job#or at how fucking deluisonal companies and businesses can be when faced with even a little bit of notoriety#and dont even get me started about government offered services and how much i love having to get anything from them#quebec's gubbermint cant even make a website that doesnt look like it's still the year 2005 and whose menus make any kind of sense#like yall trying to find information about anything on a gov site is a lost cause both in the case of qc and canada#both official government sites couldn't be more confusing and disjointed and info couldn't be any harder to access if it was on purpose#their websites are so so so badly made that it's almost fucking hilarious#i have never felt frustration such as when we were working on my wife's immigration papers and had to find answers on the CIA's website#canadian immigration agency you know that cia not... you get it#maybe put some of those tax dollars you love allocating to military budgets à la con into making yourself an usable website you fucks#maybe with some of the money you're not actually fixing roads and schools and hospitals with you could hire a web developer#anyways#im v mad w the state of things tonite :)#ellis's adventures in late capitalism customer service and predatory business practices
3 notes
·
View notes