#Bank Security and Surveillance System
Explore tagged Tumblr posts
Text
Whereas alarms, sirens, and gunshots might only sound during an actual bank robbery, steel vaults, surveillance cameras, and armed security guards provide round-the-clock protection.
"Plagues Upon the Earth: Disease and the Course of Human History" - Kyle Harper
#book quote#plagues upon the earth#kyle harper#nonfiction#immune system#analogy#alarm#siren#gunshot#bank robbery#steel#vault#surveillance cameras#armed security#security guard#protection
0 notes
Text
Against Britcoin and The Digital Pound
As the digital age advances, the concept of money is evolving beyond physical coins and banknotes into the realm of digital currencies. One such development is the proposed "Britcoin," a digital version of the British pound. While this initiative promises to bring convenience and modernity to financial transactions, it also raises significant concerns. It's crucial to scrutinise the implications of Britcoin and advocate for a cautious approach to its adoption.
What is Britcoin?
Britcoin, the proposed digital pound, is envisioned as a state-backed digital currency, aiming to complement physical cash and existing digital payment systems. This initiative is part of a broader trend where countries are exploring central bank digital currencies (CBDCs) to streamline monetary transactions, reduce costs, and provide a government-backed alternative to cryptocurrencies like Bitcoin.
The Promised Benefits
Proponents of Britcoin highlight several potential benefits:
Efficiency and Speed: Digital transactions can be executed instantly, improving the efficiency of financial operations for both consumers and businesses.
Financial Inclusion: Britcoin could offer financial services to unbanked or underbanked populations, providing them access to secure and efficient payment methods.
Reduced Costs: Digital currency can potentially lower the costs associated with printing, storing, and transporting physical money.
Enhanced Security: With advanced encryption and blockchain technology, digital currencies can offer robust security against fraud and counterfeiting.
The Concerns
Despite these advantages, the introduction of Britcoin raises several red flags:
Privacy Issues: Digital currencies are inherently traceable, which could lead to increased surveillance of financial transactions by the state. This threatens individual privacy and could be misused for unwarranted tracking of personal spending habits.
Centralization Risks: The control of Britcoin by a central authority, such as the Bank of England, centralizes financial power, potentially leading to misuse or policy decisions that may not reflect the best interests of the public.
Cybersecurity Threats: As a digital entity, Britcoin would be susceptible to cyberattacks. A breach could have catastrophic consequences, destabilizing the financial system and leading to significant economic losses.
Technological Dependence: A move towards digital currency increases dependence on technology and infrastructure. In cases of technical failures or power outages, access to money could be disrupted, affecting daily life and business operations.
Economic Inequality: While intended to promote financial inclusion, Britcoin could exacerbate existing inequalities if its implementation doesn't consider those without access to digital technologies or the internet.
The Need for Vigilance
Given these potential drawbacks, it's imperative to approach Britcoin with caution. Here's how we can advocate for a balanced and thoughtful consideration of this digital currency:
Demand Transparency: Push for clear and transparent communication from the government and financial institutions about the development and implementation of Britcoin. Public consultations and debates should be encouraged to address concerns and gather diverse viewpoints.
Privacy Protections: Insist on robust privacy measures to ensure that users' financial data is protected from misuse and unwarranted surveillance. This could involve stringent regulations and oversight mechanisms.
Cybersecurity Measures: Advocate for the highest standards of cybersecurity to safeguard against potential threats. This includes regular audits, risk assessments, and investment in cutting-edge security technologies.
Inclusivity Plans: Ensure that plans for Britcoin include provisions for those without access to digital technologies, such as rural populations and the elderly. This could involve providing alternative methods of access or maintaining physical cash options.
Legal Frameworks: Call for the establishment of comprehensive legal frameworks that govern the use, distribution, and regulation of Britcoin. These frameworks should protect users and ensure the stability of the financial system.
While the advent of Britcoin represents a significant step towards modernizing the financial landscape, it's essential to proceed with caution. By understanding the potential risks and advocating for robust safeguards, we can ensure that the digital pound serves the public interest without compromising privacy, security, or inclusivity. The fight against a hasty and ill-considered rollout of Britcoin is not about resisting progress but about ensuring that progress benefits everyone fairly and equitably.
#Britcoin#Digital Pound#Central Bank Digital Currency#CBDC#Financial Privacy#Digital Currency Risks#Economic Inequality#Financial Inclusion#Monetary Policy#Digital Payments#Cybersecurity#Digital Financial System#Blockchain Technology#Government Surveillance#Financial Regulation#Currency Modernization#Digital Economy#Financial Security#Technological Dependence#Digital Finance Ethics#today on tumblr#new blog
1 note
·
View note
Text
How I got scammed

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security

I wuz robbed.
More specifically, I was tricked by a phone-phisher pretending to be from my bank, and he convinced me to hand over my credit-card number, then did $8,000+ worth of fraud with it before I figured out what happened. And then he tried to do it again, a week later!
Here's what happened. Over the Christmas holiday, I traveled to New Orleans. The day we landed, I hit a Chase ATM in the French Quarter for some cash, but the machine declined the transaction. Later in the day, we passed a little credit-union's ATM and I used that one instead (I bank with a one-branch credit union and generally there's no fee to use another CU's ATM).
A couple days later, I got a call from my credit union. It was a weekend, during the holiday, and the guy who called was obviously working for my little CU's after-hours fraud contractor. I'd dealt with these folks before – they service a ton of little credit unions, and generally the call quality isn't great and the staff will often make mistakes like mispronouncing my credit union's name.
That's what happened here – the guy was on a terrible VOIP line and I had to ask him to readjust his mic before I could even understand him. He mispronounced my bank's name and then asked if I'd attempted to spend $1,000 at an Apple Store in NYC that day. No, I said, and groaned inwardly. What a pain in the ass. Obviously, I'd had my ATM card skimmed – either at the Chase ATM (maybe that was why the transaction failed), or at the other credit union's ATM (it had been a very cheap looking system).
I told the guy to block my card and we started going through the tedious business of running through recent transactions, verifying my identity, and so on. It dragged on and on. These were my last hours in New Orleans, and I'd left my family at home and gone out to see some of the pre-Mardi Gras krewe celebrations and get a muffalata, and I could tell that I was going to run out of time before I finished talking to this guy.
"Look," I said, "you've got all my details, you've frozen the card. I gotta go home and meet my family and head to the airport. I'll call you back on the after-hours number once I'm through security, all right?"
He was frustrated, but that was his problem. I hung up, got my sandwich, went to the airport, and we checked in. It was total chaos: an Alaska Air 737 Max had just lost its door-plug in mid-air and every Max in every airline's fleet had been grounded, so the check in was crammed with people trying to rebook. We got through to the gate and I sat down to call the CU's after-hours line. The person on the other end told me that she could only handle lost and stolen cards, not fraud, and given that I'd already frozen the card, I should just drop by the branch on Monday to get a new card.
We flew home, and later the next day, I logged into my account and made a list of all the fraudulent transactions and printed them out, and on Monday morning, I drove to the bank to deal with all the paperwork. The folks at the CU were even more pissed than I was. The fraud that run up to more than $8,000, and if Visa refused to take it out of the merchants where the card had been used, my little credit union would have to eat the loss.
I agreed and commiserated. I also pointed out that their outsource, after-hours fraud center bore some blame here: I'd canceled the card on Saturday but most of the fraud had taken place on Sunday. Something had gone wrong.
One cool thing about banking at a tiny credit-union is that you end up talking to people who have actual authority, responsibility and agency. It turned out the the woman who was processing my fraud paperwork was a VP, and she decided to look into it. A few minutes later she came back and told me that the fraud center had no record of having called me on Saturday.
"That was the fraudster," she said.
Oh, shit. I frantically rewound my conversation, trying to figure out if this could possibly be true. I hadn't given him anything apart from some very anodyne info, like what city I live in (which is in my Wikipedia entry), my date of birth (ditto), and the last four digits of my card.
Wait a sec.
He hadn't asked for the last four digits. He'd asked for the last seven digits. At the time, I'd found that very frustrating, but now – "The first nine digits are the same for every card you issue, right?" I asked the VP.
I'd given him my entire card number.
Goddammit.
The thing is, I know a lot about fraud. I'm writing an entire series of novels about this kind of scam:
https://us.macmillan.com/books/9781250865878/thebezzle
And most summers, I go to Defcon, and I always go to the "social engineering" competitions where an audience listens as a hacker in a soundproof booth cold-calls merchants (with the owner's permission) and tries to con whoever answers the phone into giving up important information.
But I'd been conned.
Now look, I knew I could be conned. I'd been conned before, 13 years ago, by a Twitter worm that successfully phished out of my password via DM:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That scam had required a miracle of timing. It started the day before, when I'd reset my phone to factory defaults and reinstalled all my apps. That same day, I'd published two big online features that a lot of people were talking about. The next morning, we were late getting out of the house, so by the time my wife and I dropped the kid at daycare and went to the coffee shop, it had a long line. Rather than wait in line with me, my wife sat down to read a newspaper, and so I pulled out my phone and found a Twitter DM from a friend asking "is this you?" with a URL.
Assuming this was something to do with those articles I'd published the day before, I clicked the link and got prompted for my Twitter login again. This had been happening all day because I'd done that mobile reinstall the day before and all my stored passwords had been wiped. I entered it but the page timed out. By that time, the coffees were ready. We sat and chatted for a bit, then went our own ways.
I was on my way to the office when I checked my phone again. I had a whole string of DMs from other friends. Each one read "is this you?" and had a URL.
Oh, shit, I'd been phished.
If I hadn't reinstalled my mobile OS the day before. If I hadn't published a pair of big articles the day before. If we hadn't been late getting out the door. If we had been a little more late getting out the door (so that I'd have seen the multiple DMs, which would have tipped me off).
There's a name for this in security circles: "Swiss-cheese security." Imagine multiple slices of Swiss cheese all stacked up, the holes in one slice blocked by the slice below it. All the slices move around and every now and again, a hole opens up that goes all the way through the stack. Zap!
The fraudster who tricked me out of my credit card number had Swiss cheese security on his side. Yes, he spoofed my bank's caller ID, but that wouldn't have been enough to fool me if I hadn't been on vacation, having just used a pair of dodgy ATMs, in a hurry and distracted. If the 737 Max disaster hadn't happened that day and I'd had more time at the gate, I'd have called my bank back. If my bank didn't use a slightly crappy outsource/out-of-hours fraud center that I'd already had sub-par experiences with. If, if, if.
The next Friday night, at 5:30PM, the fraudster called me back, pretending to be the bank's after-hours center. He told me my card had been compromised again. But: I hadn't removed my card from my wallet since I'd had it replaced. Also, it was half an hour after the bank closed for the long weekend, a very fraud-friendly time. And when I told him I'd call him back and asked for the after-hours fraud number, he got very threatening and warned me that because I'd now been notified about the fraud that any losses the bank suffered after I hung up the phone without completing the fraud protocol would be billed to me. I hung up on him. He called me back immediately. I hung up on him again and put my phone into do-not-disturb.
The following Tuesday, I called my bank and spoke to their head of risk-management. I went through everything I'd figured out about the fraudsters, and she told me that credit unions across America were being hit by this scam, by fraudsters who somehow knew CU customers' phone numbers and names, and which CU they banked at. This was key: my phone number is a reasonably well-kept secret. You can get it by spending money with Equifax or another nonconsensual doxing giant, but you can't just google it or get it at any of the free services. The fact that the fraudsters knew where I banked, knew my name, and had my phone number had really caused me to let down my guard.
The risk management person and I talked about how the credit union could mitigate this attack: for example, by better-training the after-hours card-loss staff to be on the alert for calls from people who had been contacted about supposed card fraud. We also went through the confusing phone-menu that had funneled me to the wrong department when I called in, and worked through alternate wording for the menu system that would be clearer (this is the best part about banking with a small CU – you can talk directly to the responsible person and have a productive discussion!). I even convinced her to buy a ticket to next summer's Defcon to attend the social engineering competitions.
There's a leak somewhere in the CU systems' supply chain. Maybe it's Zelle, or the small number of corresponding banks that CUs rely on for SWIFT transaction forwarding. Maybe it's even those after-hours fraud/card-loss centers. But all across the USA, CU customers are getting calls with spoofed caller IDs from fraudsters who know their registered phone numbers and where they bank.
I've been mulling this over for most of a month now, and one thing has really been eating at me: the way that AI is going to make this kind of problem much worse.
Not because AI is going to commit fraud, though.
One of the truest things I know about AI is: "we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job":
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week
I trusted this fraudster specifically because I knew that the outsource, out-of-hours contractors my bank uses have crummy headsets, don't know how to pronounce my bank's name, and have long-ass, tedious, and pointless standardized questionnaires they run through when taking fraud reports. All of this created cover for the fraudster, whose plausibility was enhanced by the rough edges in his pitch - they didn't raise red flags.
As this kind of fraud reporting and fraud contacting is increasingly outsourced to AI, bank customers will be conditioned to dealing with semi-automated systems that make stupid mistakes, force you to repeat yourself, ask you questions they should already know the answers to, and so on. In other words, AI will groom bank customers to be phishing victims.
This is a mistake the finance sector keeps making. 15 years ago, Ben Laurie excoriated the UK banks for their "Verified By Visa" system, which validated credit card transactions by taking users to a third party site and requiring them to re-enter parts of their password there:
https://web.archive.org/web/20090331094020/http://www.links.org/?p=591
This is exactly how a phishing attack works. As Laurie pointed out, this was the banks training their customers to be phished.
I came close to getting phished again today, as it happens. I got back from Berlin on Friday and my suitcase was damaged in transit. I've been dealing with the airline, which means I've really been dealing with their third-party, outsource luggage-damage service. They have a terrible website, their emails are incoherent, and they officiously demand the same information over and over again.
This morning, I got a scam email asking me for more information to complete my damaged luggage claim. It was a terrible email, from a noreply@ email address, and it was vague, officious, and dishearteningly bureaucratic. For just a moment, my finger hovered over the phishing link, and then I looked a little closer.
On any other day, it wouldn't have had a chance. Today – right after I had my luggage wrecked, while I'm still jetlagged, and after days of dealing with my airline's terrible outsource partner – it almost worked.
So much fraud is a Swiss-cheese attack, and while companies can't close all the holes, they can stop creating new ones.
Meanwhile, I'll continue to post about it whenever I get scammed. I find the inner workings of scams to be fascinating, and it's also important to remind people that everyone is vulnerable sometimes, and scammers are willing to try endless variations until an attack lands at just the right place, at just the right time, in just the right way. If you think you can't get scammed, that makes you especially vulnerable:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
10K notes
·
View notes
Text
Enhance Security with our Bank Surveillance System Solutions
Discover Securens comprehensive Bank Surveillance System, designed to enhance security and protection for BFSI branches. Safeguard your assets with advanced surveillance solutions tailored for the banking sector.
0 notes
Text
tracking barbara gordon's skillset as oracle:
she provides directory assistance for several international and intergalactic teams of superheroes (the birds of prey, justice league of america, the outsiders, and she has worked with the titans before).
she is the primary hacker and information network source for many of these heroes.
she helps provide mercy ops (disaster relief and humanitarian efforts) globally.
she is able to hack into the white house cameras.
she hacks into the united states air force routinely to use their memory capabilities.
she is seen as a pentagon level threat.
she writes her own code for scanning new satellite images for human habitations and anomalies.
she's accessed air force rockets no one is supposed to know about and overridden them to fire them.
she has a team of drones ready for surveillance.
she's put her own security systems on arkham asylum.
she hacks into information databases from federal complexes and assembles blueprints and guard schedules so she can send her agents to break into them.
she sets a government complex on fire (she says it is a small and contained fire.)
she also sets the clock tower on fire to force batman to not do murder/suicide.
she hacks into cia debriefing transcripts to obtain information.
she controls a large portion of the world's internet and power grids.
she also is the reason why many world leaders are in power.
she has access to the bank accounts of several supervillains, whom she toys with (specifically for blockbuster, she regularly steals millions of dollars from his accounts in a way that he cannot track who is stealing it and where it is going -- she's stolen 3 million, 17 million, 6 million, twenty million and also a hundred million from him).
she can also hack alien drones.
she can control traffic.
she has several booby-traps in the clock tower for potential assaulters. she also a device to monitor movement of people around it, in case batman decides to show up.
cited panels down below!

"she's the four-one-one for the jla, she the database for the g.c. ex-p.d. she runs mercy ops around the world." nightwing (1996) #38

"you have cameras in the white house?" "don't be silly. the white house has cameras in the white house. i've just tapped into them." nightwing (1996) #66
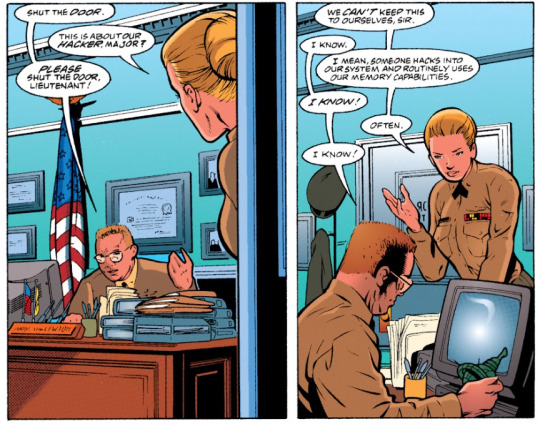
"i mean, someone hacks into our system and routinely uses our [united states air force] memory capabilities!" "i know!" "often." birds of prey #1 (1999)
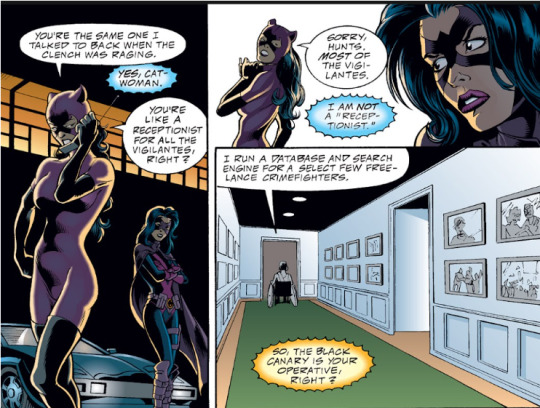
"i run a database and search engine for a select few free-land crimefighters." birds of prey: manhunt (1996)

"we scan the most recent images for anomalies. things that don't belong." "where'd you get a program for that?" "i wrote my own code for that one." birds of prey (1999) #3

"they've accessed whitehorse, sir." "whitehorse? no one's supposed to know about that!" birds of prey (1999) #9

"and oracle? we're going to need eyes on several places at once." "i think we can manage that." detective comics (1937) #1077

"they've accessed whitehorse. what's the chance of them arming it?" "all clear?" "oh yeah." "fire!" birds of prey (1999) #9
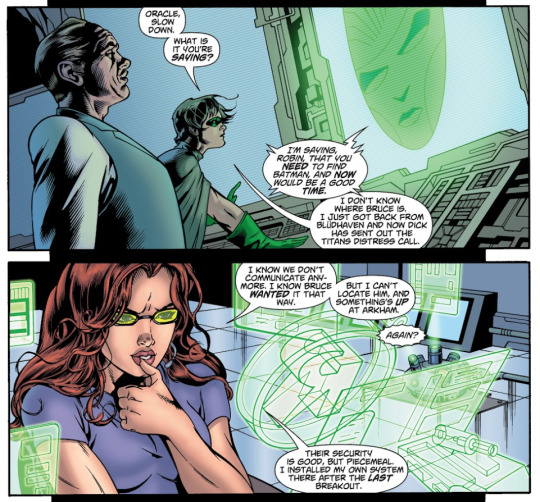
"[arkham's] security is good, but piecemeal. i installed my own system there after the last breakout." infinite crisis special: villains united (2006)

"batgirl -- that incident a couple months back? when those government agents caught your face on tape? i found out where they're keeping it. it's a federal complex in virginia. i've sent you blueprints, guard schedules -- everything you'll need to break in." batgirl (2000) #17

"where did you get that kind of information?" "they traded another prisoner last month. i hacked into his cia debriefing transcript." birds of prey (1999) #9

"kat, do you have any idea... any notion at all, of how much of the planet's entire internet i control? how many power grids? how many world leaders owe me their positions?" birds of prey #1 (1999)

"i transferred all the funds in her cayman islands account to another offshore account. if she doesn't get the paintings to me in the next forty-eight hours, that money's going to my favorite charities." birds of prey: catwoman/oracle (2003)

"where do you get current [satellite] shots of rheelasia?" "that's my secret, you little netnik." birds of prey (1999) #3

"but the asborbascons were created using languages long dead even on my planet. they are uncrackable." "yes. the absorbascons are uncrackable. but the alien drones aren't." convergence: nightwing/oracle (2015)
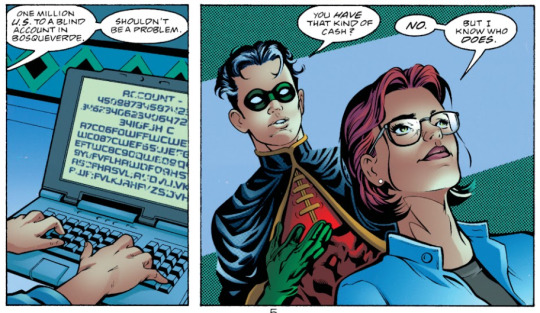

"do you have that kind of cash?" "no. but i know someone who does." "there's been a... discrepancy, mr. desmond." "in plain english, mr. vogel." "at one point, three million was electronically transferred from your numbered accounts in the caicos to a bank account in hasaragua. from there to karocco, then yemen, then split between banks in senegal and manila. and then... my hardware couldn't keep up." birds of prey (1999) #3

"seventeen million from your account in the caymans. six from santa prisca. twenty from rheelasia. and a hundred million plus from other holdings of yours around the world, mr. desmond. and where it all goes? nobody knows." birds of prey (1999) #18

"they're taking your cash from impregnable accounts and transferring it electronically to their own." "and you can't find the source?" "there's subsequent transfers performed at lightning speed. the money's split up, rerouted in and out of various banks in an eyeblink. even i can't keep up with whoever this is." birds of prey (1999) #18

"let me handle the traffic." birds of prey (1999) #58

"all of you. keep your hands where i can see 'em." "not a problem. malory. ripken. peppermint." nightwing (1996) #39
#barbara gordon#babs#oracle#batgirl#birds of prey#justice league of america#jla#batman#robin#nightwing#huntress#black canary#blockbuster#dick grayson#tim drake#helena bertinelli#bruce wayne
486 notes
·
View notes
Text
TOP SECRET LEAK: GITMO EXPANSION NOW OPERATIONAL—GLOBAL ELITE BEING TAKEN DOWN!
Trump has activated the largest military crackdown in modern history—and it’s happening RIGHT NOW. Guantánamo Bay (Gitmo) has been fortified beyond recognition, transformed into an impenetrable tribunal complex designed for high-profile detentions and prosecutions.
Insiders confirm elite special forces are carrying out global raids, capturing high-ranking figures in finance, politics, and media. The biggest criminals in history are being processed for military trials. The Cabal’s reign of terror is over.
GITMO: THE FINAL STRONGHOLD OF JUSTICE
Gitmo is now a classified military tribunal zone, fully equipped to handle thousands of detainees. Confirmed upgrades include:
12 high-security detention blocks for indefinite incarceration.
Biometric security checkpoints ensuring no escape.
Quantum surveillance systems monitoring every movement 24/7.
AI-driven interrogation chambers extracting confessions in real time.
Underground evidence vaults securing classified documents and assets.
Sources confirm military prosecutors are preparing the largest trials in history.
MASS ARRESTS UNDERWAY: BIGGEST NAMES TAKEN DOWN
Covert military operations have already captured key figures:
A top media mogul responsible for deep state propaganda.
A European royal tied to global trafficking networks.
A pharmaceutical tycoon linked to bioweapon funding.
Multiple banking elites, caught running financial blackmail rings.
These aren’t random arrests—each target has been under surveillance for years. The military has undeniable proof.
GLOBAL ELITE EXPOSED: CRIMES BEYOND BELIEF
Shockwaves are spreading as intelligence teams uncover the truth:
Secret human experimentation labs found in South America and Eastern Europe.
Elite-controlled military bases hidden beneath Antarctica.
Big Tech and intelligence collusion exposed in classified documents.
Seized encrypted files revealing financial manipulation, election rigging, and mass blackmail.
All evidence is secured at Gitmo, ensuring ultimate justice.
MILITARY TRIBUNALS: NO ESCAPE FOR THE CABAL
Detainees are given two choices:
Cooperate and expose the network for a slim chance at leniency.
Remain silent and face full military sentencing—no appeal.
Leaked testimonies confirm Hollywood elites, tech billionaires, and corrupt politicians were ALL involved. The Cabal’s control is unraveling before our eyes.
DEEP STATE PANIC: DESPERATE COUNTERATTACKS
The Cabal is attempting:
Assassinations of military leaders running Gitmo tribunals.
Cyber warfare attacks to wipe out intelligence databases.
Financial manipulation schemes to trigger market collapse.
But Trump’s military forces anticipated every move. Deep state networks are being dismantled, elite hideouts raided. The takedown cannot be stopped.
THE CABAL LOSES CONTROL: THE WORLD WAKES UP
Their propaganda is collapsing:
Whistleblowers are stepping forward in record numbers.
Leaked tribunal transcripts confirm shocking confessions.
Social media is on fire with reports—despite censorship.
The mainstream media is scrambling, but it’s too late—the TRUTH is out!
WHAT COMES NEXT: THE FINAL PHASE
Gitmo’s full expansion completes in 2025, but thousands of new arrests are ALREADY planned.
Elite banking cartels will be eliminated.
The biggest names yet will be exposed.
The deep state is falling FAST.
This isn’t just justice—it’s the end of their empire.
THE STORM IS HERE...
THERE'S NO TURNING BACK 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do some research#do your research#do your own research#ask yourself questions#question everything#government corruption#government lies#government secrets#lies exposed#truth be told#evil lives here#medical corruption#hollyweird#news#should be news#not in the news#you decide#justice is served#justice is coming#gitmo
129 notes
·
View notes
Text
“Treasury has been denying that they gave Marko write access, but I am looking at his access request right now”
So they have “read and write” access, or even “read only” access, why do we care? What are the possible consequences?
1. Musk, Trump and their respective cronies have unrestricted access to your social security numbers, your confidential bank information, your confidential medical information and so much more.
This is true with just “read only” access. This is why the burgeoning media war (that currently “read only” is winning unfortunately) is something of a red-herring. It matters, don’t get me wrong. As a source yesterday said, Apocalyptic. But that source also said that “read only” was “catastrophic”. If the smash and grab operation commences just as stupidly, quickly and dangerously as it has so far, this could easily become identity theft by an untold number of people using their personally identifiable information within weeks.
This kind of information can also be used to target enemies and, if they get operational control elsewhere, the capability of using the Anti-Money Laundering (AML), Know Your Customer (KYC), & the Combating the Finance of Terror (CFT) laws to target political enemies. Of course, these laws have already been used to target political dissidents; but we are talking about something of an incomprehensibly larger scale. As one long time payments lawyer wrote to me: “Is DOGE using its own, non-OFAC definition of ‘terrorist group’ that has no basis in law?” In this sense, the Democratic party has fully and unequivocally participated in building the apparatus that is showing to be extraordinarily easily weaponized against them. In short, they can not just steal money but eliminate the financial existence of anyone they felt like, if operational control gets sufficient. The week Trump won his second term, I told a room full of Democratic party operatives that “if the Democratic Party really believed Trump was a fascist, they would destroy the servers containing all the surveillance data.”
2. Creating “backdoors” into the Treasury’s multi-trillion dollar payment system
I’m running short on time (it's late at the time of writing) and I have to get up in the morning and be prepared for another round of intensive interviews so this will have to be more carefully detailed in the future. But these are extremely sensitive systems, and complicated systems. All the factors that slow them down in taking over the system are also the factors that would make it hard to find intentionally hidden code to their benefit that could give them ongoing access to the system even if they are removed. I need to do more reporting on this one but it is something many, many sources have mentioned
3. Subordinate the judicial system to the Trump Administration/DOGE
This one has been hard to get across to readers. As you can imagine, the overwhelming social media response to this reporting has focused on the absurd illegality of the actions. Asking for judicial intervention. But as I covered in my piece Friday, the constitution is not self enforcing and the supreme court is unlikely to step in, or to step in a positive way. In my Friday’s piece I unfortunately presciently asked:
As a famous twentieth century statesman might have said in this situation "...and how many divisions does the Constitution have?”
What happens if they are just embedded so deeply in the heart of government payments that there is no mechanism to dislodge them? Court Injunctions are not self enforcing either My longtime payments lawyer source agrees with this point, which I also tried to articulate Monday:
Chokehold to stop or delay any and all payments initiated by federal agencies, and potential mechanical method to thwart judicial rulings when a judge/court says “You as the Executive Branch cannot stop federal grants/payments lawfully approved and directed by Congress.”
As we’ve seen, there are no armed law enforcement figures coming in to save the day and if Musk's DOGE get deep enough into the Bureau of the Fiscal Service, the only way to enforce the law is through street actions.
4. Elon Musk can use this system against his enemies.
It almost feels quant to say because the timeline of so many of the other possibilities are so immediately and dramatically dire that this one almost feels hopeful in comparison in that it implies “competitive position” being something that is very meaningful. Nevertheless, it should be obvious that this information, which includes information on all businesses the Federal Government does business with, is ripe to be used to kneecap competitors. Specifically my longtime payments lawyer source brought up just outright putting competitors on the “do not pay” list. The “good case scenario” may just be an economy increasingly dominated in all corners by Musk and/or Trump through a sprawling network of business ventures with the greatest possible advantages.
5. The New American Payments System, X the Everything App
For this one I am just going to quote my longtime payments lawyer source at length. They’ve got it and note this is a “read only” issue. Imagine the worst case of paying your taxes on X payments, or “receiving” your social security payments there.:
Obtaining access to and potentially exfiltrating data sets from BFS that may be characterized as “anonymized” (in order to evade criticism about potential violation of privacy laws), but could give insight into payment patterns and payment system strengths, weaknesses and behaviors:
1. Such information obtained on an inside track by DOGE would be very helpful, for example, if you are an entity like X Payments LLC and are currently licensed as a money transmitter in 42 states with plans to launch as-yet-to-be specified payments and financial services.
2. It is unclear whether there are any limitations on DOGE personnel transferring payment information to X Payments LLC in order for that company to gain proprietary information regarding federal payments in an anti-competitive manner compared to its fintech competitors currently in the marketplace.
3. Such single-sourced information not available to other market competitors would provide an anti-competitive jump for X Payments LLC on ApplePay, Google Pay, Samsung Pay (mobile wallets) and a host of other fintech companies in the marketplace backed by venture capital and private equity funding.
6. Ability to pick and choose who gets public money, regardless of congressional directives
I covered the constitutional aspects of this crisis Friday. The payment aspects I covered Monday. Without Judicial ability or willingness to sanction Trump & Musk, There is very little left of congress. The “power of the purse” is central to the rule and authority of congress. The decentralized (in relative terms) nature of administrative agencies means that there are enormous opportunities for agencies to follow the law. This is a place to skip past all those headaches.
7. Subordinate the judicial system to the Trump Administration/DOGE
This one has been hard to get across to readers. As you can imagine, the overwhelming social media response to this reporting has focused on the absurd illegality of the actions. Asking for judicial intervention. But as I covered in my piece Friday, the constitution is not self enforcing and the supreme court is unlikely to step in, or to step in a positive way. In my Friday’s piece I unfortunately presciently asked:
As a famous twentieth century statesman might have said in this situation "...and how many divisions does the Constitution have?”
What happens if they are just embedded so deeply in the heart of government payments that there is no mechanism to dislodge them? Court Injunctions are not self enforcing either My longtime payments lawyer source agrees with this point, which I also tried to articulate Monday:
Chokehold to stop or delay any and all payments initiated by federal agencies, and potential mechanical method to thwart judicial rulings when a judge/court says “You as the Executive Branch cannot stop federal grants/payments lawfully approved and directed by Congress.”
As we’ve seen, there are no armed law enforcement figures coming in to save the day and if Musk's DOGE get deep enough into the Bureau of the Fiscal Service, the only way to enforce the law is through street actions.
8. Elon Musk can use this system against his enemies.
It almost feels quant to say because the timeline of so many of the other possibilities are so immediately and dramatically dire that this one almost feels hopeful in comparison in that it implies “competitive position” being something that is very meaningful. Nevertheless, it should be obvious that this information, which includes information on all businesses the Federal Government does business with, is ripe to be used to kneecap competitors. Specifically my longtime payments lawyer source brought up just outright putting competitors on the “do not pay” list. The “good case scenario” may just be an economy increasingly dominated in all corners by Musk and/or Trump through a sprawling network of business ventures with the greatest possible advantages.
9. The New American Payments System, X the Everything App
For this one I am just going to quote my longtime payments lawyer source at length. They’ve got it and note this is a “read only” issue. Imagine the worst case of paying your taxes on X payments, or “receiving” your social security payments there.:
Obtaining access to and potentially exfiltrating data sets from BFS that may be characterized as “anonymized” (in order to evade criticism about potential violation of privacy laws), but could give insight into payment patterns and payment system strengths, weaknesses and behaviors:
1. Such information obtained on an inside track by DOGE would be very helpful, for example, if you are an entity like X Payments LLC and are currently licensed as a money transmitter in 42 states with plans to launch as-yet-to-be specified payments and financial services.
2. It is unclear whether there are any limitations on DOGE personnel transferring payment information to X Payments LLC in order for that company to gain proprietary information regarding federal payments in an anti-competitive manner compared to its fintech competitors currently in the marketplace.
3. Such single-sourced information not available to other market competitors would provide an anti-competitive jump for X Payments LLC on ApplePay, Google Pay, Samsung Pay (mobile wallets) and a host of other fintech companies in the marketplace backed by venture capital and private equity funding.
10. Ability to pick and choose who gets public money, regardless of congressional directives
I covered the constitutional aspects of this crisis Friday. The payment aspects I covered Monday. Without Judicial ability or willingness to sanction Trump & Musk, There is very little left of congress. The “power of the purse” is central to the rule and authority of congress. The decentralized (in relative terms) nature of administrative agencies means that there are enormous opportunities for agencies to follow the law. This is a place to skip past all those headaches.
11. Catastrophic failure of the payments system.
Even a disruption for a day would be a disaster. A disruption on longer timescales would have unimaginable knock on effects. The Treasury could involuntarily default because of operational issues. The worst case scenarios, which are completely and utterly plausible at the time of writing, would be a catastrophe without precedent. No typical economic calamity like the Great Financial Crisis or even the Great Depression would be comparable.
87 notes
·
View notes
Text
From Alt National Park Service in n FB:
tl;dr:
DOGE accessed all those systems - IRS, Social Security, DHS, every office in the U.S. - not to promote “efficiency”, but to gather and control our electronic lives so they can ruin us if we step out of line in any way. Or if they just feel like it.
Alt National Park Service:
“DOGE has quietly transformed into something far more sinister — not a system for streamlining government, but one designed for surveillance, control, and targeting. And no one’s talking about it. So we’re going to spill the tea.
From the beginning, DOGE’s true mission has been about data — collecting massive amounts of personal information on Americans. Now, that data is being turned against immigrants.
At the center of this effort is Antonio Gracias, a longtime Elon Musk confidante. Though he holds no official government position, Gracias is leading a specialized DOGE task force focused on immigration. His team has embedded engineers and staff across nearly every corner of the Department of Homeland Security (DHS).
But it doesn’t stop there.
DOGE operatives have also been quietly placed inside other federal agencies like the Social Security Administration and the Department of Health and Human Services — agencies that store some of the most sensitive personal data in the country, including on immigrants.
DOGE engineers now working inside DHS include Kyle Schutt, Edward Coristine (nicknamed “Big Balls”), Mark Elez, Aram Moghaddassi, and Payton Rehling. They’ve built the technical foundation behind a sweeping plan to revoke, cancel visas, and rewire the entire asylum process.
One of the most disturbing aspects of this plan? Flagging immigrants as “deceased” in the Social Security system — effectively canceling their SSNs. Without a valid Social Security number, it becomes nearly impossible to open a bank account, get a job, or even apply for a loan. The goal? Make life so difficult that people “self-deport.”
And if you’re marked as dead in the Social Security system, good luck fixing it. There’s virtually no path back — it’s a bureaucratic black hole.
You might ask: why do immigrants, asylum seekers, or refugees even have Social Security numbers? Because anyone authorized to work in the U.S. legally is issued one. It’s not just for citizens. It’s essential for participating in modern life — jobs, housing, banking, taxes. Without it, you’re locked out of society.
Last week, this plan was finalized in a high-level White House meeting that included DHS Secretary Kristi Noem, Antonio Gracias, senior DOGE operatives, and top administration officials.
In recent weeks, the administration has moved aggressively to strip legal protections from hundreds of thousands of immigrants and international students — many of whom have been living and working in the U.S. legally for years.
At the core of this crackdown? Data.
DOGE has access to your SSN, your income, your political donations — and more. What was once sold as a tool for “government efficiency” has become something else entirely: a weaponized surveillance machine.
And if you think this ends with immigrants, think again.
Antonio Gracias has already used DOGE’s access to Social Security and state-level data to push voter fraud narratives during past elections. The system is in place. The precedent has been set. And average Americans should be concerned.”
#alt national park service#doge#elon musk#donald trump#student visas#immigrants#authoritarianism#us politics#trump#fuck trump#fuck elon musk
91 notes
·
View notes
Note
Hello! Can you please write some platonic/familial headcannons for tfp soundwave and a human reader who lives on the Nemesis with them?
The reader is an artist who is very quiet and tends to only show their emotions around soundwave, most of the time you can find them sitting on soundwaves shoulder and drawing but if not then they are usually listening in on whatever gossip is going round the ship.
Thank you! don't forget to drink some water and have a yummy snack!
[ Please do not repost, plagiarize, or use my writing for AI! Translating my work with proper credit is acceptable, but please ask first! ]

Sitting in silence together as you both work is Soundwave's ideal way to slowly bond with someone. However it's only ideal given his oath of silence and the type of work he does around the Nemesis. If you keep an eye out or pay close attention to whoever passes behind you and Soundwave, you'll notice that anyone that passes by the two of you automatically knows to keep quiet. You'll hear vehicons chatting and laughing over something far off in the halls, but once they get close enough there will be nothing but dead silence from them. Why they do it is something you'll never truly find out, as the answer you get varies depending on who you ask, but at least you have Soundwave to thank for the silence.
However, you don't always have to keep quiet around him while he works. He doesn't mind if you talk about things like how your day went, or something new that you're interested in, or the gossip you've heard around the ship while he works (as long as he doesn't need to completely focus on his work at the moment). They're more of a listener than a talker, but every now and then, they'll play back clips of your voice in order to ask more about something you mentioned or maybe something unrelated.
Whenever you've had your fill of work, or you want to get up and stretch your legs before you come back, all you have to do is slowly get up and Soundwave will automatically catch on that you want down. They'll lift their arm level to their shoulder and slowly set you to the ground before they continue their work.
Whenever you wander around the Nemesis, the gossip you hear varies from vehicons back talking some of the higher-ups, to vehicons from different barracks or squadrons back talking vehicons from other barracks or squadrons, to gossip about you. They say all sorts of things, ranging from disdain at how Soundwave adopted a pet squishy, to amazement at how talented humans can be, to questions about what they think being a human is like. It's a mixed bag, really, and unless you can learn to tell the vehicons apart from one another, you can't tell what you'll hear when you listen in on some vehicons working on changing the lights in the hall.
Soundwave's become familiar with places you frequently visit around the Nemesis, so it doesn't take too long to find you. Additionally they have access to every surveillance camera aboard the ship as well as a very keen eye, so it really isn't much of a challenge for them. However, if they're too busy then they'll send Lazerbeak to go fetch you for whatever reason they need you.
Your room is located within his habsuite of course, but you're allowed your own privacy, as well as a lot of space to store all of your belongings. And of course since you have different needs than a cybertronian, he'll take time every week in order to accompany you down to some town or city within Earth, or task Lazerbeak to watch after you as you get the necessary things you need like food, water, clothing, etc..
But where would you get the cash for such things? He simply takes it from the rich. The security systems and anti-virus software available on earth technology is considered very rudimentary by Soundwave's standards, so it's not much of an issue for them to develop a malware that slowly trickles money out of some rich person's bank account.
However, if for some reason something were to happen while you were down on earth, you have his personal comm link line. The moment you call that line, he'll either go find you himself or disbatch Lazerbeak to retrieve you if he's unavailable.

#tfp imagines#tfp headcanons#tfp x reader#tfp soundwave#soundwave x reader#x reader#reader insert#self insert#weenwrites
95 notes
·
View notes
Text
This past year, Republican lawmakers in Congress have introduced several bills that have sparked significant controversy, some being:
1. Protecting Women’s Private Spaces Act: Introduced by Representative Nancy Mace in November 2024, this bill aims to prohibit individuals from using single-sex facilities on federal property that do not correspond to their biological sex. The legislation has been criticized for targeting transgender individuals, particularly following the election of Sarah McBride, the first openly transgender person elected to Congress.
2. Stop the Sexualization of Children Act: Introduced by Representative Mike Johnson, this bill seeks to ban the use of federal funds for programs, events, or literature deemed “sexually oriented” for children under the age of 10. Critics argue that its broad definitions could lead to the suppression of LGBTQ+ content and infringe upon free speech rights. 
3. CBDC Anti-Surveillance State Act: Led by House Majority Whip Tom Emmer, this bill aims to block the Federal Reserve from issuing a central bank digital currency (CBDC) to individuals, citing concerns over financial privacy and government surveillance. The bill has faced opposition from those who believe it could hinder financial innovation and the modernization of the U.S. monetary system. 
4. National Defense Authorization Act (NDAA) Amendments: In June 2024, House Republicans passed a defense bill that included amendments addressing various social issues, such as restrictions on diversity training and limitations on medical treatments for transgender service members. These provisions have been contentious, with critics arguing they politicize defense policy and marginalize certain groups within the military. 
5. Safeguard American Voter Eligibility (SAVE) Act: Prioritized by House Republicans in the new session, this bill requires individuals registering to vote in federal elections to provide proof of citizenship. Supporters claim it ensures election integrity, but opponents argue it could disenfranchise eligible voters, particularly among marginalized communities. 
6. Anti-Immigration Legislation Package: Between March 18 & March 24, 2021, Republican lawmakers introduced 11 bills targeting various aspects of immigration, including asylum procedures and border security. Critics contend that these measures could undermine the rights of asylum seekers and immigrants.
#politics#political#us politics#donald trump#news#president trump#elon musk#american politics#jd vance#law#republicans#republican#gop#maga#make america great again#us house of representatives#congress#america#trump#president donald trump#trans rights#immigration#immigrants make america great#us news#republican party
31 notes
·
View notes
Text
From Alt Park National Service on FB:
DOGE has quietly transformed into something far more sinister — not a system for streamlining government, but one designed for surveillance, control, and targeting. And no one’s talking about it. So we’re going to spill the tea.
From the beginning, DOGE’s true mission has been about data — collecting massive amounts of personal information on Americans. Now, that data is being turned against immigrants.
At the center of this effort is Antonio Gracias, a longtime Elon Musk confidante. Though he holds no official government position, Gracias is leading a specialized DOGE task force focused on immigration. His team has embedded engineers and staff across nearly every corner of the Department of Homeland Security (DHS).
But it doesn’t stop there.
DOGE operatives have also been quietly placed inside other federal agencies like the Social Security Administration and the Department of Health and Human Services — agencies that store some of the most sensitive personal data in the country, including on immigrants.
DOGE engineers now working inside DHS include Kyle Schutt, Edward Coristine (nicknamed “Big Balls”), Mark Elez, Aram Moghaddassi, and Payton Rehling. They’ve built the technical foundation behind a sweeping plan to revoke, cancel visas, and rewire the entire asylum process.
One of the most disturbing aspects of this plan? Flagging immigrants as “deceased” in the Social Security system — effectively canceling their SSNs. Without a valid Social Security number, it becomes nearly impossible to open a bank account, get a job, or even apply for a loan. The goal? Make life so difficult that people “self-deport.”
And if you’re marked as dead in the Social Security system, good luck fixing it. There’s virtually no path back — it’s a bureaucratic black hole.
You might ask: why do immigrants, asylum seekers, or refugees even have Social Security numbers? Because anyone authorized to work in the U.S. legally is issued one. It’s not just for citizens. It’s essential for participating in modern life — jobs, housing, banking, taxes. Without it, you’re locked out of society.
Last week, this plan was finalized in a high-level White House meeting that included DHS Secretary Kristi Noem, Antonio Gracias, senior DOGE operatives, and top administration officials.
In recent weeks, the administration has moved aggressively to strip legal protections from hundreds of thousands of immigrants and international students — many of whom have been living and working in the U.S. legally for years.
At the core of this crackdown? Data.
DOGE has access to your SSN, your income, your political donations — and more. What was once sold as a tool for “government efficiency” has become something else entirely: a weaponized surveillance machine.
And if you think this ends with immigrants, think again.
Antonio Gracias has already used DOGE’s access to Social Security and state-level data to push voter fraud narratives during past elections. The system is in place. The precedent has been set. And average Americans should be concerned.
#america#government#america under dictatorship#surveillance#mass surveillance#doge#doge is dodgy#immigrants#dissenting citizens are next#alt national park service
18 notes
·
View notes
Text
The American Civil Liberties Union filed a federal lawsuit on Monday against the US Social Security Administration (SSA) and the Department of Veterans Affairs (VA). In its lawsuit, the ACLU accuses the agencies of violating the Freedom of Information Act (FOIA) by ignoring the ACLU’s requests and subsequent appeals for information concerning the so-called Department of Government Efficiency’s (DOGE) “attempted or actual access” to sensitive federal databases.
The ACLU began pursuing documents under the federal transparency law in February, as WIRED first reported, responding to reports that Elon Musk’s DOGE operatives were seeking access to troves of personal information belonging to US citizens, including US Department of Treasury records that contain “millions of Social Security numbers, bank accounts, business finances,” and more.
Over the last few months, extensive reporting by WIRED and other outlets has exposed DOGE’s attempts to access and analyze sensitive data on federal employees, the American public, and immigrants to the US.
In its complaint, the ACLU argues that DOGE’s access to highly sensitive information about Americans’ health and finances raises “acute concerns” due to the “extraordinary harm” that can result from any unauthorized use of those files. According to the complaint, the ACLU pressed the SSA to expedite the release of public records associated with DOGE’s work; a process permitted when documents are deemed urgent to inform the public about government activities at the center of significant public debate or concern. The organization cited, among its other materials, a letter from Senator Mark Warner detailing the unprecedented secrecy shrouding DOGE’s activities.
The SSA rejected the ACLU’s claim but then later ignored its attempts to file an appeal, the ACLU says—a procedure the SSA is required to abide by under FOIA. The VA was even less responsive, the ACLU alleges; it acknowledged the ACLU’s request in February then ceased any further communications.
“If DOGE is forcing its way into our private data, it is forcing itself into our private lives,” says Lauren Yu, one of the attorneys representing the ACLU in court. “Congress mandated strict privacy safeguards for a reason, and Americans deserve to know who has access to their social security numbers, their bank account information, and their health records … Government actors cannot continue to shroud themselves in secrecy while prying into our most sensitive records.”
The organization’s lawsuit is also informed, it says, by growing public concern over the ongoing push by DOGE to implement artificial intelligence (AI) systems, “which raises alarms about the potential for mass surveillance and politically motivated misuse of that deeply personal information.”
Earlier this month, WIRED reported that a DOGE operative was attempting to use an AI tool to implement code at the VA, which administers benefits to roughly 10 million American veterans and their families, including health care and disability payments. Sources at the agency voiced concerns about the rush to implement AI, saying the operation had failed to follow normal procedures and threatened to put US veterans’ access to the benefits they’d earned at risk.
“Granting DOGE access to VA data systems would not only violate federal law but it would undermine the very core of the VA mission to care for veterans, their families, caregivers, and survivors,” Michelle Fraling, the ACLU’s counsel, said in a statement.
WIRED reported last week that DOGE is knitting together data from the Social Security Administration, the Department of Homeland Security, and the Internal Revenue Service that could create a surveillance tool of unprecedented scope. The ACLU’s initial records requests were prompted in part by concerns, its FOIA filings say, about the use of computer matching programs that are able to cross-reference information on individuals using disparate government databases.
The ability of the government to cross-reference personal information using databases from different agencies is tightly regulated under the US Privacy Act. The act was amended in 1988 to require agencies to enter into written agreements before engaging in computer matching, and agencies are required under the law to calculate how such initiatives might impact individuals’ rights.
“The federal government cannot dodge accountability by ignoring our lawful demands for transparency,” Nathan Freed Wessler, deputy director of the ACLU’s Speech, Privacy, and Technology Project, said in a statement.
16 notes
·
View notes
Text

─────────── ⌇ thoughts on Minh's Security Hacking
Minh doesn't really have a problem doing illegal acts, but there are certainly limitations. For example, he'd not use it for private matters to help anyone take revenge or some shit like that.
He also would not attempt to do any hacking of military or law enforcement security machines. The group he was in always focused on private persons or companies. He usually also moves in that realm now, but smaller.
Good examples of what he does probably be:
Surveillance Systems: e.g., CCTV, motion sensors
Access Control: e.g., keycard locks, biometric scanners (turning off warnings)
Banking Systems: e.g., ATMs, online banking platforms
Corporate Networks: e.g., firewalls, VPNs, email servers
Minh also avoids those where he knows their system is designed so that he would have the risk of leaving a trace.
He is not a hacker in the traditional sense that just gets into whatever device you hand him, he requires certain tools, programs and prepared devices.
7 notes
·
View notes
Text
Surveillance cameras now cover the Damascus Gate, the main entrance into the old city of Jerusalem and one of the only public areas for Palestinians to gather socially and hold demonstrations. It’s at that gate that “Palestinians are being watched and assessed at all times”, according to an Amnesty International report, Automated Apartheid. These cameras have created a chilling effect on not just the ability to protest but also on the daily lives of Palestinians who live under occupation, according to Amnesty investigators. The organization had previously concluded that Israel has established a system of apartheid against Palestinians.
Among the vendors behind these surveillance cameras is a company that has been accused of aiding what the US has categorized as a genocide: Hikvision. Based in Hangzhou, China, the company is one of the world’s largest makers of video surveillance equipment. Already infamous among international human rights groups, it has been blacklisted by the US and identified by the UK as a security threat for being complicit in China’s repression of the Uyghur ethnic minority.
126 notes
·
View notes
Text
DOGE has transformed into a system for surveillance, control, and targeting
Posted by Alt National Park Service to Facebook on April 12, 2025

DOGE has quietly transformed into something far more sinister — not a system for streamlining government, but one designed for surveillance, control, and targeting. And no one’s talking about it. So we’re going to spill the tea.
From the beginning, DOGE’s true mission has been about data — collecting massive amounts of personal information on Americans. Now, that data is being turned against immigrants.
At the center of this effort is Antonio Gracias, a longtime Elon Musk confidante. Though he holds no official government position, Gracias is leading a specialized DOGE task force focused on immigration. His team has embedded engineers and staff across nearly every corner of the Department of Homeland Security (DHS).
But it doesn’t stop there.
DOGE operatives have also been quietly placed inside other federal agencies like the Social Security Administration and the Department of Health and Human Services — agencies that store some of the most sensitive personal data in the country, including on immigrants.
DOGE engineers now working inside DHS include Kyle Schutt, Edward Coristine (nicknamed “Big Balls”), Mark Elez, Aram Moghaddassi, and Payton Rehling. They’ve built the technical foundation behind a sweeping plan to revoke, cancel visas, and rewire the entire asylum process.
One of the most disturbing aspects of this plan? Flagging immigrants as “deceased” in the Social Security system — effectively canceling their SSNs. Without a valid Social Security number, it becomes nearly impossible to open a bank account, get a job, or even apply for a loan. The goal? Make life so difficult that people “self-deport.”
And if you’re marked as dead in the Social Security system, good luck fixing it. There’s virtually no path back — it’s a bureaucratic black hole.
You might ask: why do immigrants, asylum seekers, or refugees even have Social Security numbers? Because anyone authorized to work in the U.S. legally is issued one. It’s not just for citizens. It’s essential for participating in modern life — jobs, housing, banking, taxes. Without it, you’re locked out of society.
Last week, this plan was finalized in a high-level White House meeting that included DHS Secretary Kristi Noem, Antonio Gracias, senior DOGE operatives, and top administration officials.
In recent weeks, the administration has moved aggressively to strip legal protections from hundreds of thousands of immigrants and international students — many of whom have been living and working in the U.S. legally for years.
At the core of this crackdown? Data.
DOGE has access to your SSN, your income, your political donations — and more. What was once sold as a tool for “government efficiency” has become something else entirely: a weaponized surveillance machine.
And if you think this ends with immigrants, think again.
Antonio Gracias has already used DOGE’s access to Social Security and state-level data to push voter fraud narratives during past elections. The system is in place. The precedent has been set. And average Americans should be concerned.
6 notes
·
View notes
Text
Author: CrimethInc. Topic: technology
“The future is already here,” Cyberpunk pioneer William Gibson once said; “it’s just not very evenly distributed.” Over the intervening decades, many people have repurposed that quote to suit their needs. Today, in that tradition, we might refine it thus: War is already here—it’s just not very evenly distributed.
Never again will the battlefield be just state versus state; it hasn’t been for some time. Nor are we seeing simple conflicts that pit a state versus a unitary insurgent that aspires to statehood. Today’s wars feature belligerents of all shapes and sizes: states (allied and non-allied), religious zealots (with or without a state), local and expatriate insurgents, loyalists to former or failing or neighboring regimes, individuals with a political mission or personal agenda, and agents of chaos who benefit from the instability of war itself. Anyone or any group of any size can go to war.
The increased accessibility of the technology of disruption and war[1] means the barrier to entry is getting lower all the time. The structure of future wars will sometimes feel familiar, as men with guns murder children and bombs level entire neighborhoods—but it will take new forms, too. Combatants will manipulate markets and devalue currencies. Websites will be subject to DDoS attacks and disabling—both by adversaries and by ruling governments. Infrastructure and services like hospitals, banks, transit systems, and HVAC systems will all be vulnerable to attacks and interruptions.
In this chaotic world, in which new and increasing threats ceaselessly menace our freedom, technology has become an essential battlefield. Here at the CrimethInc. technology desk, we will intervene in the discourse and distribution of technological know-how in hopes of enabling readers like you to defend and expand your autonomy. Let’s take a glance at the terrain.
Privacy
The NSA listens to, reads, and records everything that happens on the internet.
Amazon, Google, and Apple are always listening[2] and sending some amount[3] of what they hear back to their corporate data centers[4]. Cops want that data. Uber, Lyft, Waze, Tesla, Apple, Google, and Facebook know your whereabouts and your movements all of the time. Employees spy on users.
Police[5] want access to the contents of your phone, computer, and social media accounts—whether you’re a suspected criminal, a dissident on a watch list, or an ex-wife.
The business model of most tech companies is surveillance capitalism. Companies learn everything possible about you when you use their free app or website, then sell your data to governments, police, and advertisers. There’s even a company named Palantir, after the crystal ball in The Lord of the Rings that the wizard Saruman used to gaze upon Mordor—through which Mordor gazed into Saruman and corrupted him.[6] Nietzsche’s famous quote, “When you look long into an abyss, the abyss also looks into you,” now sounds like a double transcription error: surely he didn’t mean abyss, but app.
Security
Self-replicating malware spreads across Internet of Things (IoT) devices like “smart” light bulbs and nanny cams, conscripting them into massive botnets. The people who remotely control the malware then use these light bulbs and security cameras to launch debilitating DDoS[7] attacks against DNS providers, reporters, and entire countries.
Hackers use ransomware to hold colleges, hospitals, and transit systems hostage. Everything leaks, from nude photos on celebrities’ phones to the emails of US political parties.
Capital
Eight billionaires combined own as much wealth as the poorest 50% of the world’s population. Four of those eight billionaires are tech company founders.[8] Recently, the President of the United States gathered a group of executives to increase collaboration between the tech industry and the government.[9]
The tech industry in general, and the Silicon Valley in particular, has a disproportionately large cultural influence. The tech industry is fundamentally tied to liberalism and therefore to capitalism. Even the most left-leaning technologists aren’t interested in addressing the drawbacks of the social order that has concentrated so much power in their hands.[10]
War
Nation states are already engaging in cyber warfare. Someone somewhere[11] has been learning how to take down the internet.
Tech companies are best positioned to create a registry of Muslims and other targeted groups. Even if George W. Bush and Barack Obama hadn’t already created such lists and deported millions of people, if Donald Trump (or any president) wanted to create a registry for roundups and deportations, all he’d have to do is go to Facebook. Facebook knows everything about you.
The Obama administration built the largest surveillance infrastructure ever—Donald Trump’s administration just inherited it. Liberal democracies and fascist autocracies share the same love affair with surveillance. As liberalism collapses, the rise of autocracy coincides with the greatest technical capacity for spying in history, with the least cost or effort. It’s a perfect storm.
This brief overview doesn’t even mention artificial intelligence (AI), machine learning, virtual reality (VR), augmented reality (AR), robots, the venture capital system, or tech billionaires who think they can live forever with transfusions of the blood of young people.
Here at the tech desk, we’ll examine technology and its effects from an anarchist perspective. We’ll publish accessible guides and overviews on topics like encryption, operational security, and how to strengthen your defenses for everyday life and street battles. We’ll zoom out to explore the relation between technology, the state, and capitalism—and a whole lot more. Stay tuned.
Footnotes
[1] A surplus of AK-47s. Tanks left behind by U.S. military. Malware infected networked computer transformed into DDoS botnets. Off the shelf ready to execute scripts to attack servers.
[2] Amazon Echo / Alexa. Google with Google Home. Apple with Siri. Hey Siri, start playing music.
[3] What, how much, stored for how long, and accessible by whom are all unknown to the people using those services.
[4] Unless you are a very large company, “data center” means someone else’s computer sitting in someone else’s building.
[5] Local beat cops and police chiefs, TSA, Border Patrol, FBI… all the fuckers.
[6] Expect to read more about Palantir and others in a forthcoming article about surveillance capitalism.
[7] Distributed Denial of Service. More on this in a later article, as well.
[8] Bill Gates, Jeff Bezos, Mark Zuckerberg, Larry Ellison. In fact, if you count Michael Bloomberg as a technology company, that makes five.
[9] In attendance: Eric Trump. Brad Smith, Microsoft president and chief legal officer. Jeff Bezos, Amazon founder and CEO. Larry Page, Google founder and Alphabet CEO. Sheryl Sandberg, Facebook COO. Mike Pence. Donald Trump. Peter Thiel, venture capitalist. Tim Cook, Apple CEO. Safra Catz, Oracle CEO. Elon Musk, Tesla CEO. Gary Cohn, Goldman Sachs president and Trump’s chief economic adviser. Wilbur Ross, Trump’s commerce secretary pick. Stephen Miller, senior policy adviser. Satya Nadella, Microsoft CEO. Ginni Rometty, IBM CEO. Chuck Robbins, Cisco CEO. Jared Kushner, investor and Trump’s son-in-law. Reince Priebus, chairman of the Republican National Committee and White House chief of staff. Steve Bannon, chief strategist to Trump. Eric Schmidt, Alphabet president. Alex Karp, Palantir CEO. Brian Krzanich, Intel CEO.
[10] We’ll explore this more in a later article about “The California Ideology.”
[11] Probably a state-level actor such as Russia or China.
#technology#Privacy#Security#Capital#War#anarchism#anarchy#anarchist society#practical anarchy#practical anarchism#resistance#autonomy#revolution#communism#anti capitalist#anti capitalism#late stage capitalism#daily posts#libraries#leftism#social issues#anarchy works#anarchist library#survival#freedom
8 notes
·
View notes