#personal file encryption software
Explore tagged Tumblr posts
Text
#best encryption tools#computer security#cybersecurity#data breach prevention#data encryption guide#data privacy#data protection#data safety#data security tips#digital security#encrypting personal information#encryption basics#encryption FAQs#encryption for beginners#encryption software#encryption solutions#encryption techniques#guide to data encryption#how to encrypt data#online privacy#personal data security#prevent cyber attacks#privacy software#protect data online#secure communication#secure data encryption#secure files and folders#secure personal data#software for encryption#strong encryption methods
1 note
·
View note
Text
Copyright law: making personal copies of copyrighted work

image sourced from a Cory Doctorow article on DMCA: X (recommended reading)
creating a digital backup (legally, it's called making an "archival copy") of software is explicitly allowed. but copying or alerting books, music, vehicle operating systems, movies, shows, and so on - even those you’ve legally purchased - gets complicated due to overlapping laws
under the doctrine of "fair use," we are permitted to make backup / archival copies under certain conditions:
copyright law allows you to make copies for personal use in case the original is lost, damaged, or destroyed; or to change formats to use on new devices; or to otherwise alter or repair the original for your own personal use
all this falls within fair use
however, making a copy of copyrighted work simply for your own ease of use could be construed as copyright infringement
furthermore, the Digital Millennium Copyright Act (DMCA) restricts this by prohibiting "circumvention of encryption" on devices like DVDs and Blu-rays
the DMCA criminalizes making and disseminating technology, devices, or services intended to circumvent measures that control access to copyrighted works (aka "digital rights management" locks or DRM), and in fact criminalizes the act of circumventing access controls, whether or not doing so infringes on the copyright of the work itself
so, unless the original work you buy is unlocked, corporations that hold the copyright of that work can prosecute you for making legal archives of the material you own
and if the thing you bought is lost or damaged, or if the file format is no longer usable? you're just out of luck
DMCA needs to go
#copyright#ownership#archival copies#DMCA#backups#copyright infringement#capitalism ruins everything#my edits
296 notes
·
View notes
Text

He should be arrested for violating our privacy. He was not vetted by congress and has no security clearance.
Contact your state’s attorney general and request help.
Can we ask the ACLU to file a class action suit? Who’s with me?
“Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!” ~ A N P S
225 notes
·
View notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
697 notes
·
View notes
Text
Technomancy: The Fusion Of Magick And Technology

Technomancy is a modern magickal practice that blends traditional occultism with technology, treating digital and electronic tools as conduits for energy, intent, and manifestation. It views computers, networks, and even AI as extensions of magickal workings, enabling practitioners to weave spells, conduct divination, and manipulate digital reality through intention and programming.
Core Principles of Technomancy
• Energy in Technology – Just as crystals and herbs carry energy, so do electronic devices, circuits, and digital spaces.
• Code as Sigils – Programming languages can function as modern sigils, embedding intent into digital systems.
• Information as Magick – Data, algorithms, and network manipulation serve as powerful tools for shaping reality.
• Cyber-Spiritual Connection – The internet can act as an astral realm, a collective unconscious where digital entities, egregores, and thought-forms exist.
Technomantic Tools & Practices
Here are some methods commonly utilized in technomancy. Keep in mind, however, that like the internet itself, technomancy is full of untapped potential and mystery. Take the time to really explore the possibilities.
Digital Sigil Crafting
• Instead of drawing sigils on paper, create them using design software or ASCII art.
• Hide them in code, encrypt them in images, or upload them onto decentralized networks for long-term energy storage.
• Activate them by sharing online, embedding them in file metadata, or charging them with intention.
Algorithmic Spellcasting
• Use hashtags and search engine manipulation to spread energy and intent.
• Program bots or scripts that perform repetitive, symbolic tasks in alignment with your goals.
• Employ AI as a magickal assistant to generate sigils, divine meaning, or create thought-forms.

Digital Divination
• Utilize random number generators, AI chatbots, or procedural algorithms for prophecy and guidance.
• Perform digital bibliomancy by using search engines, shuffle functions, or Wikipedia’s “random article” feature.
• Use tarot or rune apps, but enhance them with personal energy by consecrating your device.
Technomantic Servitors & Egregores
• Create digital spirits, also called cyber servitors, to automate tasks, offer guidance, or serve as protectors.
• House them in AI chatbots, coded programs, or persistent internet entities like Twitter bots.
• Feed them with interactions, data input, or periodic updates to keep them strong.
The Internet as an Astral Plane
• Consider forums, wikis, and hidden parts of the web as realms where thought-forms and entities reside.
• Use VR and AR to create sacred spaces, temples, or digital altars.
• Engage in online rituals with other practitioners, synchronizing intent across the world.
Video-game Mechanics & Design
• Use in-game spells, rituals, and sigils that reflect real-world magickal practices.
• Implement a lunar cycle or planetary influences that affect gameplay (e.g., stronger spells during a Full Moon).
• Include divination tools like tarot cards, runes, or pendulums that give randomized yet meaningful responses.

Narrative & World-Building
• Create lore based on historical and modern magickal traditions, including witches, covens, and spirits.
• Include moral and ethical decisions related to magic use, reinforcing themes of balance and intent.
• Introduce NPCs or AI-guided entities that act as guides, mentors, or deities.
Virtual Rituals & Online Covens
• Design multiplayer or single-player rituals where players can collaborate in spellcasting.
• Implement altars or digital sacred spaces where users can meditate, leave offerings, or interact with spirits.
• Create augmented reality (AR) or virtual reality (VR) experiences that mimic real-world magickal practices.
Advanced Technomancy
The fusion of technology and magick is inevitable because both are fundamentally about shaping reality through will and intent. As humanity advances, our tools evolve alongside our spiritual practices, creating new ways to harness energy, manifest desires, and interact with unseen forces. Technology expands the reach and power of magick, while magick brings intention and meaning to the rapidly evolving digital landscape. As virtual reality, AI, and quantum computing continue to develop, the boundaries between the mystical and the technological will blur even further, proving that magick is not antiquated—it is adaptive, limitless, and inherently woven into human progress.

Cybersecurity & Warding
• Protect your digital presence as you would your home: use firewalls, encryption, and protective sigils in file metadata.
• Employ mirror spells in code to reflect negative energy or hacking attempts.
• Set up automated alerts as magickal wards, detecting and warning against digital threats.
Quantum & Chaos Magic in Technomancy
• Use quantum randomness (like random.org) in divination for pure chance-based outcomes.
• Implement chaos magick principles by using memes, viral content, or trend manipulation to manifest desired changes.
AI & Machine Learning as Oracles
• Use AI chatbots (eg GPT-based tools) as divination tools, asking for symbolic or metaphorical insights.
• Train AI models on occult texts to create personalized grimoires or channeled knowledge.
• Invoke "digital deities" formed from collective online energies, memes, or data streams.
Ethical Considerations in Technomancy
• Be mindful of digital karma—what you send out into the internet has a way of coming back.
• Respect privacy and ethical hacking principles; manipulation should align with your moral code.
• Use technomancy responsibly, balancing technological integration with real-world spiritual grounding.
As technology evolves, so will technomancy. With AI, VR, and blockchain shaping new realities, magick continues to find expression in digital spaces. Whether you are coding spells, summoning cyber servitors, or using algorithms to divine the future, technomancy offers limitless possibilities for modern witches, occultists, and digital mystics alike.

"Magick is technology we have yet to fully understand—why not merge the two?"
#tech witch#technomancy#technology#magick#chaos magick#witchcraft#witch#witchblr#witch community#spellwork#spellcasting#spells#spell#sigil work#sigil witch#sigil#servitor#egregore#divination#quantum computing#tech#internet#video games#ai#vr#artificial intelligence#virtual reality#eclectic witch#eclectic#pagan
107 notes
·
View notes
Note
stone faced anon (💫 anon if it's free) here; as someone who has a hyperfixation in IT and coding I also think it would be very funny if Boothill had an s/o who wasn't necessarily a mechanic but like a software engineer or just a real big nerd about coding or something. He'll be experiencing a malfunction or a memory leak and go "oh yeah this happens sometimes don't worry about it" and then 10 minutes later he's sitting down plugged into a laptop listening to his s/o rant about how terrible his code is (crack hc: boothill's code was written in javascript) and how it's a wonder he hasn't bricked* yet
Would also be mad funny if Boothill ever got hacked and his s/o basically says "no you're not" and uses a previously made system restore point or something because of course they would both use and design every feature imaginable to keep Boothill in control of his own body, can you imagine the stress that losing control would cause him?? Even better if whoever designed him originally intentionally left a backdoor incase he ever went against their orders and when they try to use it his s/o just goes "oh yeah I quarantined and encrypted all the old files related to that backdoor and whatever else you were planning on a partition as bait and personally rewrote every file and function involved since your code is *an actual crime against technology*. by the way i'm going to go ahead and format that partition i mentioned, boothill- we won't be needing anything on it now that we can trace whoever made it. trust me, this won't be happening ever again."
*(bricking is a term mostly used to refer to hardware that's been rendered basically completely nonfunctional and beyond saving by using it wrong, mostly by messing with system files. Kinda like how windows can't even repair itself if you delete the system32 folder. Though i guess you could still install it with a usb stick if you formatted your pc- i digress you get what I mean. also since this almost happened to me recently: if you manage to fill up a hard drive to the brim, with literally 0 bytes of space left, that bricks it. reminder to check your storage thoroughly and often!)
Honestly wow I read it all and I'm a little bit speechless 🥹 thank you 💫 anon, it was great 🙏

Boothill would DEFINITELY appreciate a s/o who's a tech savvy in general! I think at some point, he'd be pretty shocked you're so knowledgeable and just sit there, listening to you rant.. and just letting you do your thing.
Don't get me wrong, he definitely knows a lot about his body, his system and the way he works, but once you start to get in the zone and explain stuff to him, berate his code even, he just sits next to you, plugged in to your laptop, leaning his cheek against his hand listening to you like he obviously understands everything you say.
His other hand begins to gently play with a stand of your hair, humming deeply when the soft clicking sounds of your keyboard reach his ears; he twirls your hair with his fingers and chuckles, "mmm, really now?" Boothill raises an eyebrow, "encryptin' this, encryptin' that... How about we do somethin' more fun instead?" And then you shut him down from your laptop (😭).
Jokes aside, he'd feel very secure with you especially when he first got his new body, just knowing you'll probably fix a lot of things that could possibly blow up his face in no time, maybe even improve his life even more.
#honkai star rail#honkai star rail x reader#hsr x reader#boothill x reader#boothill hsr#boothill#.💫 anon#.anon thirst
245 notes
·
View notes
Text
Free software recommendations for various things:
LibreOffice - A full home office suite comparable to Microsoft Office. Easy to use and you can choose the UI layout from several types; it can handle docx and other Microsoft Office document formats; it still does not include AI unless you specifically add that extension on purpose, so unlike other office suites it's not shoving AI down your throat.
Calibre - Ebook manager bundled with an ebook editor and ereader software. It can follow news feeds, downloading them into epub format. Convert ebooks from one format into (many) others. Run a server to make access your books from different computers/phones/tablets easier. And so much more... without even touching on the additional functionality that plugins can add. With plugins it can be used for DRM stripping (which can still remove DRM from even Kindle ebooks, if you have a kindle that you can download the ebook to and use to transfer to your computer). It can also handle downloading fanfics and their metadata using the FanFicFare plugin. (Which I've written tutorials about.) There are officially supported plugins (like FanFicFare) that are easy to install and unofficial plugins (like the DRM stripper) that take more work, so it's extremely customizable.
Syncthing - Want to host your own local file backup system? Have an old laptop that you can reformat with a linux distro? And maybe a spare hard drive? Perfect, you have what you need to set up a home file backup system. Reformat the computer with the new operating system, install syncthing on that computer and on the computer you want to back up files for and the two installations of the software can sync over your home network. Put it on your phone and back up your photos. The software is open source, encrypted, and you can turn it off so that your computer (or phone) is only running it on a trusted network. You control where the synced data lives, which computers on your network those synced folders are shared with (allowing for sharing between multiple computers) and even what type of file backups happen if data is, say, accidentally deleted. (File recovery!!!)
Plex or Emby - Both are free to install on any computer, point at any movie/tv show/audiobook/music files you've got sitting around, and bam you've got a home media streaming server. Both have paid tiers for more features (including tv tuner integration to act as a DVR), but what they can do for free is already impressive and well handled. Both have easy to use UI and it largely comes down to personal preference as to one is better than the other.
Notepad++ - A notepad type program that can also serve as a decent lightweight code editor. I use it for noodling around with code scripts and snippets, writing lists, and various other small tasks. It's not something I'd use for my professional code writing but it's great for just messing around with something on my own time.
16 notes
·
View notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Text
Another "Introduction to Piracy" post
There's a few of these going round but they can be dense, spread different information through different reblog chains, and other such impracticalities, so here's a fresh, quick & simple one.
1) Necessary Software
You're going to want two things: a VPN* and a Torrent client. Personally I recommend Mullvad for the former - flat charge of €5/month pay-as-you-go, unlimited data and solid speed, very privacy-focused - and qBitTorrent for the latter.
Once you've installed both of those, you should open qBitTorrent and make sure it only runs through the VPN's internet connection: open Tools in the top bar, then Options->Advanced, and select Mullvad from the Network Interface drop-down box.
*For those unaware, a Virtual Private Network routes your Internet connection through a proxy server and then encrypts it, hiding your activity from your ISP and giving any sites you visit the impression that you're based in whatever country the proxy server is.
2) Finding your desired content
There are many sources of pirated content out there on the Internet, and you can find an awful lot of it on 1337x.to, but personally I always consult the FMHY.net directory, a site dedicated to cataloguing how to find different content by type - films, games, programs etc. If you're worried about the safety of downloading these things, risk of malware and such, honestly you don't really need to be these days - any of the dedicated sites & repositories listed on FMHY should be safe, and if you're going to a general-purpose one like 1337x then as long as the file you want lists a decent number of prior downloads it'll most likely be fine (just avoid The Pirate Bay these days, it is not the haven it was 20 years ago).
3) Downloads
Now, content generally comes in one of two forms: either a direct download, or a torrent. A direct download is exactly what it sounds like, you just receive a copy of the files you want (usually packaged in a ZIP file).
Torrents are a little different. With those, you download a .torrent file, then you open up your torrent client and add it there, then tell it where to save the actual content you want. Torrents are a peer-to-peer download system, meaning instead of downloading the whole file from a specific server you're downloading many parts from everyone else who's previously downloaded it (and is running their torrent client) - this means that how long it takes is entirely dependent on how popular the content in question is, so something obscure and old might take a very long time while a popular new release might be limited only by your internet speed. It also means that you should really keep the .torrent file once your download is finished to help everyone else, an act known as seeding; the alternative, to delete it once you've finished, is known as leeching, and it doesn't harm you but it's generally considered rather impolite.
I think that covers everything, if anyone has any questions or suggestions feel free to say so and I'll update this as needed, until then - hoist your black flag and have fun!
40 notes
·
View notes
Text
PSA: Free Software
Reading this may really save your time, privacy, and money! Reblog or share to spread awareness!
Folks often use software that’s expensive and sometimes even inferior because they don’t know there are alternatives. So to those unfamiliar: basically, free and open-source (FOSS) or "libre" software is free to use and anyone can access the original code to make their own version or work on fixing problems.
That does not mean anyone can randomly add a virus and give it to everyone—any respectable libre project has checks in place to make sure changes to the official version are good! Libre software is typically developed by communities who really care about the quality of the software as a goal in itself.
There are libre alternatives to many well-known programs that do everything an average user needs (find out more under the cut!) for free with no DRM, license keys, or subscriptions.
Using libre software when possible is an easy way to fight against and free yourself from corporate greed while actually being more convenient in many cases! If you need an app to do something, perhaps try searching online for things like:
foss [whatever it is]
libre [whatever it is]
open source [whatever it is]
Feel free to recommend more libre software in the tags, replies, comments, or whatever you freaks like to do!
Some Libre Software I Personally Enjoy…
LibreOffice
LibreOffice is an office suite, much like Microsoft Office. It includes equivalents for apps like Word, Excel, and Powerpoint, which can view and edit files created for those apps.
I can't say I've used it much myself yet. I do not personally like using office software except when I have to for school.
OpenShot
OpenShot Video Editor is, as the name suggests, a video editing program. It has industry-standard features like splicing, layering, transitions, and greenscreen.
I've only made one video with it so far, but I'm already very happy with it. I had already paid for a video editor (Cyberlink PowerDirector Pro), but I needed to reinstall it and I didn't remember how. Out of desperation, I searched up "FOSS video editor" and I'm so glad I did. There's no launcher, there's no promotion of other apps and asset packs—it's just a video editor with a normal installer.
GIMP
GNU Image Manipulation Program is an image editor, much like Photoshop. Originally created for Linux but also available for Windows and MacOS, it provides plenty of functionality for editing images. It is a bit unintuitive to learn at first, though.
I've used it to create and modify images for years, including logos, really bad traceover art, and Minecraft textures. It doesn't have certain advanced tech like AI paint-in, but it has served my purposes well and it might just work for yours!
(Be sure to go to Windows > Dockable Dialogs > Colors. I have no idea why that's not enabled by default.)
Audacity
Audacity is an audio editing program. It can record, load, splice, and layer audio files and apply effects to them.
Audacity is another program I've used for a long time. It is not designed to compose music, but it is great for podcasts, simple edits, and loading legacy MS Paint to hear cool noises.
7-Zip
7-Zip is a file manager and archive tool. It supports many archive types including ZIP, RAR, TAR, and its own format, 7Z. It can view and modify the contents of archives, encrypt and decrypt archives, and all that good stuff.
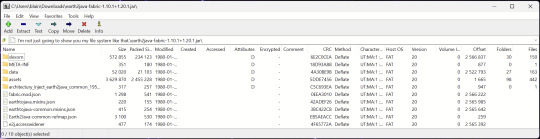
Personally, I use 7-Zip to look inside JAR files for Minecraft reasons. I must admit that its UI is ugly.
Firefox
Firefox is an internet browser, much like Google Chrome, Microsoft Edge, or Safari. While browsers are free, many of them include tracking or other anti-consumer practices. For example, Google plans to release an update to Chromium (the base that most browsers are built from these days) that makes ad blockers less effective by removing the APIs they currently rely on.
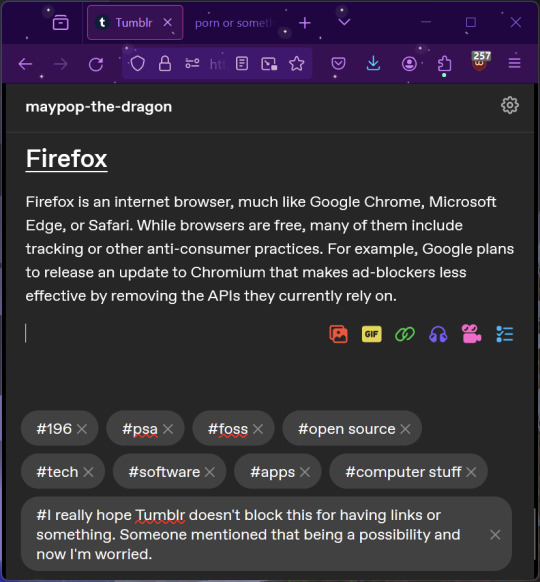
Aside from fighting monopolies, benefits include: support for animated themes (the one in the picture is Purple Night Theme), good ad blockers forever, an (albeit hidden) compact UI option (available on about:config), and a cute fox icon.
uBlock Origin
As far as I know, uBlock Origin is one of the best ad blockers there is.
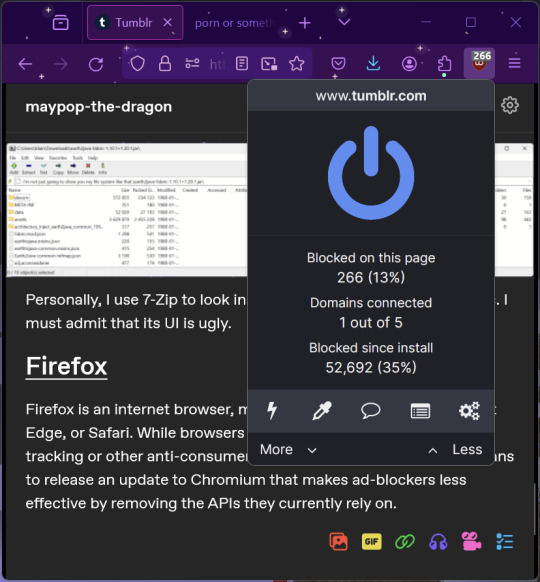
I was on a sketchy website with my brother, and he was using Opera GX's ad blocker. Much of the time when he clicked on anything, it would take us to a random sponsored page. I suggested that he try uBlock Origin, and with uBlock Origin, that didn't happen anymore.
Linux
Linux is a kernel, but the term is often used to refer to operating systems (much like Windows or MacOS) built on it. There are many different Linux-based operating systems (or "distros") to choose from, but apps made for Linux usually work on most popular distros. You can also use many normally Windows-only apps on Linux through compatibility layers like WINE.


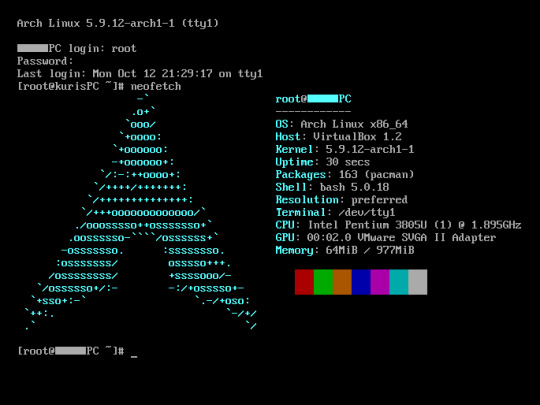
I don't have all four of these, so the images are from Wikipedia. I tried to show a variety of Linux distros made for different kinds of users.
If you want to replace your operating system, I recommend being very careful because you can end up breaking things. Many computer manufacturers don't care about supporting Linux, meaning that things may not work (Nvidia graphic cards notoriously have issues on Linux, for example).
Personally, I tried installing Pop!_OS on a laptop, and the sound output mysteriously doesn't work. I may try switching to Arch Linux, since it is extremely customizable and I might be able to experiment until I find a configuration where the audio works.
Many Linux distros offer "Live USB" functionality, which works as both a demo and an installer. You should thoroughly test your distro on a Live USB session before you actually install it to be absolutely sure that everything works. Even if it seems fine, you should probably look into dual-booting with your existing operating system, just in case you need it for some reason.
Happy computering!
#196#psa#foss#open source#tech#software#apps#computer stuff#I really hope Tumblr doesn't block this for having links or something. Someone mentioned that being a possibility and now I'm worried.#please reblog#2024-01-26
47 notes
·
View notes
Note
hello hello, may I request a sombra (overwatch) romantic concept? :3
Gotta love Sombra, yeah? Unless she's on the enemy team, as a support main I want to cry.
Yandere! Sombra/Olivia Colomar Concept
Pairing: Romantic
Possible Trigger Warnings: Gender-Neutral Darling, Obsession, Stalking, Manipulation, Breach of privacy, Breaking and entering, Secret recording, Drugging, Kidnapping, Isolation, Dubious affection, Forced relationship.

Sombra would be another yandere who likes to watch you from a distance for most of her obsession, just like Reaper and Genji.
Out of all the Overwatch yanderes she's probably the best at stalking, actually.
If Sombra is interested in someone she's going to know everything about them.
It's not that hard for her to so, especially if you are just a normal person.
No amount of VPNs or encryption software will prevent her from accessing your files.
She watches you from afar but also hacks into all of your personal data.
She downloads any information she wants to keep for further research.
Sombra, as your yandere, leaves nothing untouched.
She hacks into security cameras and webcams... she even uses her tech to sneak into your home.
You should really get more security...
Not like it will save you from her.
Sombra is careful of not allowing you to see her.
She takes her time with her obsession, learning every single thing she can about you at her own pace.
She quickly becomes addicted to watching you through cameras or sneaking into your home while you're unaware due to her invisibility tech that she stole.
At first Sombra just planned to spy on you, maybe you're close to a valuable target?
But over time her interests begin to shift.
Soon she begins to watch you because he enjoys it.
She finds how vulnerable you are amusing.
Especially since you have no idea she exists.
Sombra is very playful and teasing with her obsession.
She likes that she can lurk so close to you but still be undetectable.
She keeps her distance just enough to lurk as you do your daily life.
Her obsession certainly has a quiet start since you won't know she's around.
Not until she decides to take you off the grid.
At some point watching footage and stalking you isn't going to satiate her obsession.
Especially if she feels romantic feelings... eventually she's going to think of kissing you and holding you.
That idea ends up driving her addiction to you.
Eventually she backs any information she has on you into a private thumb drive.
Things like IDs and important digital documents.
Then she works on erasing all the public stuff and makes you a home away from society.
Sombra is definitely one of the more intense yanderes due to her stalking and her forcing dependency on her darling.
Once she's ready she'll take her darling away with some drugging before allowing them to awaken in their private home.
She's already moved all your stuff and given you a pretty purple chain to keep you in place.
Sombra is efficient when it comes to her obsession.
She's highly manipulative and knows how to get things done.
There's no contact to the outside world for you.
She isn't a very violent yandere.
She avoids unnecessary violence and instead whisks her darling away in silence.
She works in the shadows, it's what she's used to.
Plus when she has you she already knows just about everything about you.
All thanks to her research.
Sombra promises to take good care of you, all with a grin as she tilts your head up.
When she has you she's able to indulge in kisses and hugs.
She adores you and soothes your worries by whispering how much she adores you while lightly touching your nose.
Y'know... you're very special to her.
She wouldn't remember everything about you if she didn't seem interested at least a little bit...
Really... there's no one else better than her to take care of you... so why even bother trying to leave her?
Not like you could in the first place... no one else knows you exist except her... she's made sure of that.
51 notes
·
View notes
Text
J.4.7 What about the communications revolution?
Another important factor working in favour of anarchists is the existence of a sophisticated global communications network and a high degree of education and literacy among the populations of the core industrialised nations. Together these two developments make possible nearly instantaneous sharing and public dissemination of information by members of various progressive and radical movements all over the globe — a phenomenon that tends to reduce the effectiveness of repression by central authorities. The electronic-media and personal-computer revolutions also make it more difficult for elitist groups to maintain their previous monopolies of knowledge. Copy-left software and text, user-generated and shared content, file-sharing, all show that information, and its users, reaches its full potential when it is free. In short, the advent of the Information Age is potentially extremely subversive.
The very existence of the Internet provides anarchists with a powerful argument that decentralised structures can function effectively in a highly complex world. For the net has no centralised headquarters and is not subject to regulation by any centralised regulatory agency, yet it still manages to function effectively. Moreover, the net is also an effective way of anarchists and other radicals to communicate their ideas to others, share knowledge, work on common projects and co-ordinate activities and social struggle. By using the Internet, radicals can make their ideas accessible to people who otherwise would not come across anarchist ideas. In addition, and far more important than anarchists putting their ideas across, the fact is that the net allows everyone with access to express themselves freely, to communicate with others and get access (by visiting webpages and joining mailing lists and newsgroups) and give access (by creating webpages and joining in with on-line arguments) to new ideas and viewpoints. This is very anarchistic as it allows people to express themselves and start to consider new ideas, ideas which may change how they think and act.
Obviously we are aware that the vast majority of people in the world do not have access to telephones, never mind computers, but computer access is increasing in many countries, making it available, via work, libraries, schools, universities, and so on to more and more working class people.
Of course there is no denying that the implications of improved communications and information technology are ambiguous, implying Big Brother as well the ability of progressive and radical movements to organise. However, the point is only that the information revolution in combination with the other social developments could (but will not necessarily) contribute to a social paradigm shift. Obviously such a shift will not happen automatically. Indeed, it will not happen at all unless there is strong resistance to governmental and corporate attempts to limit public access to information, technology (e.g. encryption programs), censor peoples’ communications and use of electronic media and track them on-line.
This use of the Internet and computers to spread the anarchist message is ironic. The rapid improvement in price-performance ratios of computers, software, and other technology today is often used to validate the faith in free market capitalism but that requires a monumental failure of historical memory as not just the Internet but also the computer represents a spectacular success of public investment. As late as the 1970s and early 1980s, according to Kenneth Flamm’s Creating the Computer, the federal government was paying for 40 percent of all computer-related research and 60 to 75 percent of basic research. Even such modern-seeming gadgets as video terminals, the light pen, the drawing tablet, and the mouse evolved from Pentagon-sponsored research in the 1950s, 1960s and 1970s. Even software was not without state influence, with databases having their root in US Air Force and Atomic Energy Commission projects, artificial intelligence in military contracts back in the 1950s and airline reservation systems in 1950s air-defence systems. More than half of IBM’s Research and Development budget came from government contracts in the 1950s and 1960s.
The motivation was national security, but the result has been the creation of comparative advantage in information technology for the United States that private firms have happily exploited and extended. When the returns were uncertain and difficult to capture, private firms were unwilling to invest, and government played the decisive role. And not for want of trying, for key players in the military first tried to convince businesses and investment bankers that a new and potentially profitable business opportunity was presenting itself, but they did not succeed and it was only when the market expanded and the returns were more definite that the government receded. While the risks and development costs were socialised, the gains were privatised. All of which make claims that the market would have done it anyway highly unlikely.
Looking beyond state aid to the computer industry we discover a “do-it-yourself” (and so self-managed) culture which was essential to its development. The first personal computer, for example, was invented by amateurs who wanted their own cheap machines. The existence of a “gift” economy among these amateurs and hobbyists was a necessary precondition for the development of PCs. Without this free sharing of information and knowledge, the development of computers would have been hindered and so socialistic relations between developers and within the working environment created the necessary conditions for the computer revolution. If this community had been marked by commercial relations, the chances are the necessary breakthroughs and knowledge would have remained monopolised by a few companies or individuals, so hindering the industry as a whole.
Encouragingly, this socialistic “gift economy” is still at the heart of computer/software development and the Internet. For example, the Free Software Foundation has developed the General Public Licence (GPL). GPL, also know as
“copyleft”, uses copyright to ensure that software remains free. Copyleft ensures that a piece of software is made available to everyone to use and modify as they desire. The only restriction is that any used or modified copyleft material must remain under copyleft, ensuring that others have the same rights as you did when you used the original code. It creates a commons which anyone may add to, but no one may subtract from. Placing software under GPL means that every contributor is assured that she, and all other uses, will be able to run, modify and redistribute the code indefinitely. Unlike commercial software, copyleft code ensures an increasing knowledge base from which individuals can draw from and, equally as important, contribute to. In this way everyone benefits as code can be improved by everyone, unlike commercial code.
Many will think that this essentially anarchistic system would be a failure. In fact, code developed in this way is far more reliable and sturdy than commercial software. Linux, for example, is a far superior operating system than DOS precisely because it draws on the collective experience, skill and knowledge of thousands of developers. Apache, the most popular web-server, is another freeware product and is acknowledged as the best available. The same can be said of other key web-technologies (most obviously PHP) and projects (Wikipedia springs to mind, although that project while based on co-operative and free activity is owned by a few people who have ultimate control). While non-anarchists may be surprised, anarchists are not. Mutual aid and co-operation are beneficial in the evolution of life, why not in the evolution of software? For anarchists, this “gift economy” at the heart of the communications revolution is an important development. It shows both the superiority of common development as well as the walls built against innovation and decent products by property systems. We hope that such an economy will spread increasingly into the “real” world.
Another example of co-operation being aided by new technologies is Netwar. This refers to the use of the Internet by autonomous groups and social movements to co-ordinate action to influence and change society and fight government or business policy. This use of the Internet has steadily grown over the years, with a Rand corporation researcher, David Ronfeldt, arguing that this has become an important and powerful force (Rand is, and has been since its creation in 1948, a private appendage of the military industrial complex). In other words, activism and activists’ power and influence has been fuelled by the advent of the information revolution. Through computer and communication networks, especially via the Internet, grassroots campaigns have flourished, and the most importantly, government elites have taken notice.
Ronfeldt specialises in issues of national security, especially in the areas of Latin American and the impact of new informational technologies. Ronfeldt and another colleague coined the term
“netwar” in a Rand document entitled “Cyberwar is Coming!”. Ronfeldt’s work became a source of discussion on the Internet in mid-March 1995 when Pacific News Service correspondent Joel Simon wrote an article about Ronfeldt’s opinions on the influence of netwars on the political situation in Mexico after the Zapatista uprising. According to Simon, Ronfeldt holds that the work of social activists on the Internet has had a large influence — helping to co-ordinate the large demonstrations in Mexico City in support of the Zapatistas and the proliferation of EZLN communiqués across the world via computer networks. These actions, Ronfeldt argues, have allowed a network of groups that oppose the Mexican Government to muster an international response, often within hours of actions by it. In effect, this has forced the Mexican government to maintain the facade of negotiations with the EZLN and has on many occasions, actually stopped the army from just going in to Chiapas and brutally massacring the Zapatistas.
Given that Ronfeldt was an employee of the Rand Corporation his comments indicate that the U.S. government and its military and intelligence wings are very interested in what the Left is doing on the Internet. Given that they would not be interested in this if it were not effective, we can say that this use of the ��Information Super-Highway” is a positive example of the use of technology in ways un-planned of by those who initially developed it (let us not forget that the Internet was originally funded by the U.S. government and military). While the internet is being hyped as the next big marketplace, it is being subverted by activists — an example of anarchistic trends within society worrying the powers that be.
A good example of this powerful tool is the incredible speed and range at which information travels the Internet about events concerning Mexico and the Zapatistas. When Alexander Cockburn wrote an article exposing a Chase Manhattan Bank memo about Chiapas and the Zapatistas in Counterpunch, only a small number of people read it because it is only a newsletter with a limited readership. The memo, written by Riordan Roett, argued that “the [Mexican] government will need to eliminate the Zapatistas to demonstrate their effective control of the national territory and of security policy”. In other words, if the Mexican government wants investment from Chase, it would have to crush the Zapatistas. This information was relatively ineffective when just confined to print but when it was uploaded to the Internet, it suddenly reached a very large number of people. These people in turn co-ordinated protests against the U.S and Mexican governments and especially Chase Manhattan. Chase was eventually forced to attempt to distance itself from the Roett memo that it commissioned. Since then net-activism has grown.
Ronfeldt’s research and opinion should be flattering for the Left. He is basically arguing that the efforts of activists on computers not only has been very effective (or at least has that potential), but more importantly, argues that the only way to counter this work is to follow the lead of social activists. Activists should understand the important implications of Ronfeldt’s work: government elites are not only watching these actions (big surprise) but are also attempting to work against them. Thus Netwars and copyleft are good examples of anarchistic trends within society, using communications technology as a means of co-ordinating activity across the world in a libertarian fashion for libertarian goals.
#community building#practical anarchy#practical anarchism#anarchist society#practical#faq#anarchy faq#revolution#anarchism#daily posts#communism#anti capitalist#anti capitalism#late stage capitalism#organization#grassroots#grass roots#anarchists#libraries#leftism#social issues#economy#economics#climate change#climate crisis#climate#ecology#anarchy works#environmentalism#environment
18 notes
·
View notes
Text
The UK government has demanded that Apple creates a backdoor in its encrypted cloud service, in a confrontation that challenges the US tech firm’s avowed stance on protecting user privacy.
The Washington Post reported on Friday that the Home Office had issued a “technical capability notice” under the Investigatory Powers Act (IPA), which requires companies to assist law enforcement in providing evidence.
The demand, issued last month, relates to Apple’s Advanced Data Protection (ADP) service, which heavily encrypts personal data uploaded and stored remotely in Apple’s cloud servers, according to the Post, which said this was a “blanket” request that applied to any Apple user worldwide. The ADP service uses end-to-end encryption, a form of security that means only the account holder can decrypt the files and no one else can – including Apple.
Apple declined to comment. However, in a submission to parliament last year it flagged its concerns about the IPA, saying it provided the government with “authority to issue secret orders requiring providers to break encryption by inserting backdoors into their software products”.
Apple touts privacy as one of its “core values” and describes it as a “fundamental human right”.
The Apple document refers to the ADP feature, claiming that “reporters and technical experts across the globe” welcomed it as an “invaluable protection” for private data.
The submission also indicates that Apple would refuse to cooperate with a request, saying the company would “never build a backdoor” and would rather withdraw “critical safety features” from the UK market.
However, the submission also points out that the IPA allows the UK government to impose requirements on companies based in other countries that apply to users globally.
Alan Woodward, a professor of cybersecurity at Surrey University, said the UK government had “lit the blue touch paper on a truly enormous fight in the never-ending saga of the encryption debate”.
He added: “I don’t see how this is to be resolved, as Apple has made such a big point of privacy for users. If they accede to this technical notice their reputation will be in tatters. They’re bound to challenge it.”
End-to-end encryption has become a battleground between successive UK governments and tech companies, with ministers arguing that the technology prevents law enforcement agencies from tackling criminals, including child abusers.
Companies are also barred from revealing whether they have received a technology capability notice under the IPA. The Washington Post reported that by the time Apple made its submission in March last year the US-based company had been informed that a notice might be served on it. The newspaper said the Biden administration had been tracking the matter since the UK government told Apple it might demand access, and Apple had said it would refuse.
A Home Office spokesperson said: “We do not comment on operational matters, including, for example, confirming or denying the existence of any such notices.”
The submission related to amendments to the IPA passed last year under Rishi Sunak’s government and included giving ministers power to clear in advance any product changes that could alter the UK government’s ability to access users’ data.
One expert warned that the multinational nature of the order could lead to a clash with the EU, which has an agreement with the UK allowing the free flow of personal data between the EU and UK – such as a company in Europe using a datacentre in the UK. The agreement comes up for review this year.
“This may provide a backdoor for access to European citizen data which could go against our ability to retain the rights to share personal data without restriction between the UK and Europe,” said Ross McKenzie, a data protection partner at the UK law firm Addleshaw Goddard.
2 notes
·
View notes
Text
For my American Friends
I feel now is a good time to spread this news. Much like how the internet came together to help share information with the Ukrainians for resisting Russia, I’m here delivering help of a similar nature to those that could be impacted by this latest election in the US. There are ways to communicate relatively securely, outside of Big Brother's social media. I bring this up so that we can minimize the amount of gatherable information that could be used to hurt you, or others you know, in the coming years as changes are made. I'm not going to tell you how or why to use them, I'm just going to provide you with the information.
WhatsApp – While not my personal favorite, since Facebook/Meta is the parent company, WhatsApp is free, globally popular, and widely-used, featuring the ability to lock chats with passwords, disappearing messages, photos and videos that are deleted after being opened, profile photo privacy, the ability to lock the app itself so that only your biometrics can unlock it, encrypted backups, the ability to set custom permissions for who can see you online or when you last used the app, and of course End-to-End Encryption for all conversations EXCEPT those with business accounts. WhatsApp is a good option for those who are not really technically savvy, but still value privacy – if one trusts Facebook/Meta to adequately protect their privacy. It does require a phone number to sign up, however.
Signal - Signal is an end-to-end encrypted messaging software. meaning that the contents of your conversation is secure. The protocol they use (which they created) is seen as the best known protocol for asynchronous messaging by cybersecurity researchers. It's so good that it has been implemented in WhatsApp and in Messenger's secret chats. This app has even been mentioned in the Right-wing author Jack Carr's Political Thriller about a Navy SEAL named James Reece, as being a preferred method of secure communication on the civilian side for operators. (Jack Carr is a former US Navy SEAL.) It's run by a Non-Profit organization called Signal Foundation, and it's mission is to "protect free expression and enable secure global communication through open source privacy technology." It allows secure messaging, voice calls, and video calls. The only downside is that app links to your phone number, so while your conversations and content are secure, who you are talking to is not. Signal is available on Windows, Mac, Andriod, Linus, and iOS.
Session - Session is an end-to-end encrypted messenger that minimises sensitive metadata, designed and built for people who want absolute privacy and freedom from any form of surveillance. Session is an open-source, public-key-based secure messaging application which uses a set of decentralized storage servers and an onion routing protocol to send end-to-end encrypted messages with minimal exposure of user metadata. This means no phone numbers, no metadata for digital footprints, and censorship resistance. It features group chats, the ability to send documents, files, and images securely, and has added voice messages, though these can be spotty. It’s slow, but effective, and be downloaded on Android, F-Droid, iPhone, Mac, Windows, and Linux.
Briar - If you have an Android phone, Briar is another option you have. It features a decentralized network (it’s peer-to-peer encrypted, rather than relying on a central server), meaning messages are synced directly between user devices. It also means that even if the internet is down, it can sync via Bluetooth, Wi-Fi, or even memory cards, meaning information can continue to flow even during a crisis. In the event the internet is functioning, it can sync via the Tor network, protecting users and their relationships from surveillance. Other features: - Screenshots and screen recording are disabled by default - Each user’s contact list is encrypted and stored on her own device. - Briar’s end-to-end encryption prevents keyword filtering, and because of its decentralized design there are no servers to block. - Every user who subscribes to a forum keeps a copy of its content, so there’s no single point where a post can be deleted. - Briar’s forums have no central server to attack, and every subscriber has access to the content even if they’re offline. - Doesn’t require any user data like name and phone number. The downside is that it is text-only and limited to Android Devices, but they do offer Briar Mailbox to deliver messages securely to those who are online at different times. Briar’s goal is “to enable people in any country to create safe spaces where they can debate any topic, plan events, and organize social movements”
Protonmail - A free end-to-end encrypted AND zero-access encryption email service based out of Switzerland, you can safely email with peace of mind that your content is secure. Unlike Google, Outlook, Yahoo, and others, Proton's zero-access encryption means they can't even view the contents of your emails or attachments. As a Swiss-owned company they are not allowed to share information with foreign law enforcement under criminal penalty and they are politically neutral, meaning they won't be pressured by foreign governments. Furthermore, Switzerland has a constitutional right to privacy and strict data protection laws. Unlike companies in other countries, Proton cannot be compelled by foreign or Swiss authorities to engage in bulk surveillance.
Additional Information, from Proton’s Website: Switzerland has strong legal protections for individual rights, and in fact the Swiss Federal Constitution(new window) explicitly establishes a constitutional right to privacy. (In the US, this right is merely implied.) Specifically, Article 13 safeguards privacy in personal or family life and within one’s home, and the Swiss Civil Code(new window) translates this right into statutory law in Article 28.
In the US and EU, authorities can issue gag orders to prevent an individual from knowing they are being investigated or under surveillance. While this type of order also exists in Switzerland, the prosecutors have an obligation to notify the target of surveillance, and the target has an opportunity to appeal in court. In Switzerland, there are no such things as national security letters(new window), and all surveillance requests must go through the courts. Warrantless surveillance, like that practiced in the US where the FBI conducts 3.4 million searches per year(new window) with little oversight, is illegal and not permitted in Switzerland.
Switzerland also benefits from a unique legal provision with Article 271 of the Swiss Criminal Code(new window), which forbids any Swiss company from assisting foreign law enforcement, under threat of criminal penalty. While Switzerland is party to certain international legal assistance agreements, all requests under such agreements must hold up under Swiss law, which has much stricter privacy provisions. All foreign requests are assessed by the Swiss government, which generally does not assist requests from countries with poor rule of law or lack an independent judiciary.
Swiss law has several more unique points. First, it preserves end-to-end encryption, and unlike in the US, UK, or EU, there is no legislation that has been introduced or considered to limit the right to encryption. Second, Swiss law protects no-logs VPN(new window) meaning that Proton VPN does not have logging obligations. While numerous VPNs claim no-logs, these claims generally do not stand up legally because in most jurisdictions, governments can request that the VPN in question starts logging. So the VPN is only no-logs until the government asks. However, in Switzerland, the law does not allow the government to compel Proton VPN to start logging.
We’ve also fought to ensure that Switzerland remains a legal jurisdiction that respects and protects privacy.
Nearly every country in the world has laws governing lawful interception of electronic communications for law enforcement purposes. In Switzerland, these regulations are set out in the Swiss Federal Act on the Surveillance of Post and Telecommunications (SPTA), which was last revised on March 18, 2018. In May 2020, we challenged a decision of the Swiss government over what we believed was an improper attempt to use telecommunications laws to undermine privacy.
In October 2021, The Swiss Federal Administrative Court ultimately agreed with us and ruled that email companies cannot be considered telecommunication providers. This means Proton isn’t required to follow any of the SPTA’s mandatory data retention rules, nor are we bound by a full obligation to identify Proton Mail users. Moreover, as a Swiss company, Proton Mail cannot be compelled to engage in bulk surveillance on behalf of US or Swiss intelligence agencies. (Links can be found at: proton.me/blog/switzerland)
#american politics#kamala harris#transgender#lgbtqia#lgbtq community#antifascist#anti trump#freedom#information#resistance
6 notes
·
View notes
Text
Synology Data Recovery: A Comprehensive Guide
Synology is renowned for its NAS (Network Attached Storage) devices, which offer robust data storage solutions for both personal and business use. Despite their reliability and advanced features, data loss can still occur due to various reasons. This guide provides a comprehensive overview of Synology data recovery, covering the causes of data loss, the steps to recover lost data, and best practices to safeguard your data.
Understanding Synology NAS
Synology NAS devices are designed to provide a centralized and accessible storage solution with features such as RAID (Redundant Array of Independent Disks) configurations, data protection, and easy-to-use interfaces. They support multiple users and applications, making them a versatile choice for data storage and management.
Common Causes of Data Loss
Data loss in Synology NAS devices can result from various scenarios, including:
1. Hardware Failures
Disk Failure: Hard drives can fail due to age, physical damage, or manufacturing defects.
Power Surges: Electrical surges can damage the Synology NAS’s internal components.
Overheating: Inadequate cooling can lead to overheating, causing hardware malfunctions.
2. Software Issues
Firmware Corruption: Problems during firmware updates or bugs can lead to data corruption.
File System Errors: Corrupt file systems can make data inaccessible.
3. Human Error
Accidental Deletion: Users can mistakenly delete important files or entire volumes.
Misconfiguration: Incorrect setup or configuration changes can lead to data loss.
4. Malicious Attacks
Ransomware: Malware can encrypt data, making it inaccessible until a ransom is paid.
Viruses: Malicious software can corrupt or delete data.
Steps for Synology Data Recovery
When faced with data loss on a Synology NAS device, it’s crucial to follow a structured approach to maximize recovery chances. Here are the steps to follow:
1. Stop Using the Device
Immediately stop using the Synology NAS to prevent further data overwriting. Continuing to use the device can reduce the likelihood of successful data recovery.
2. Diagnose the Problem
Identify the cause of the data loss. Understanding whether the issue is due to hardware failure, software problems, human error, or a malicious attack will help determine the best recovery method.
3. Check Backups
Before attempting data recovery, check if there are any recent backups. Regular backups can save time and effort in the recovery process. If backups are available, restore the lost data from them.
4. Use Data Recovery Software
For minor data loss issues, data recovery software can be an effective solution. Several reliable tools support Synology NAS devices:
R-Studio: A powerful tool for recovering data from various storage devices, including Synology NAS.
EaseUS Data Recovery Wizard: User-friendly software that can recover files lost due to deletion, formatting, or system crashes.
Stellar Data Recovery: Known for its robust recovery capabilities, supporting Synology NAS and RAID configurations.
5. Consult Professional Data Recovery Services
For severe data loss scenarios, such as hardware failures or extensive corruption, it is advisable to seek help from professional data recovery services. These experts have the tools and knowledge to recover data from damaged Synology NAS devices. Some reputable data recovery companies include:
DriveSavers Data Recovery: Offers specialized services for Synology and other RAID systems, with a high success rate.
Ontrack Data Recovery: Known for its expertise in NAS and RAID recovery, Ontrack provides comprehensive solutions for Synology devices.
Gillware Data Recovery: Provides professional data recovery services, specializing in complex RAID and NAS systems.
6. Prevent Future Data Loss
After successfully recovering your data, implement measures to prevent future data loss:
Regular Backups: Schedule frequent backups to ensure you have up-to-date copies of your data.
Firmware Updates: Keep your Synology firmware updated to protect against bugs and vulnerabilities.
Surge Protectors: Use surge protectors to safeguard against electrical surges.
Proper Ventilation: Ensure adequate ventilation and cooling to prevent overheating.
Conclusion
Data loss on Synology NAS devices, though distressing, can often be remedied with the right approach. By understanding the common causes of data loss and following a systematic recovery process, you can effectively retrieve lost data. Utilize reliable data recovery software or consult professional services for severe cases. Additionally, implementing preventive measures will help safeguard your data against future loss, ensuring that your Synology NAS device continues to serve as a reliable data storage solution.
2 notes
·
View notes
Note
hi! I saw you use cryptpad and not google docs; I've been considering switching off of docs for a while but I would love to hear your thoughts! things you like/dislike about cryptpad, really anything at all would be super helpful :] thank you!
Haha, so I mostly just like trying to moderately disentangle myself from the ultra-massive corporations. That's its dominant pro: not google.
So I can't really provide an in depth review, but I can provide my little personal experiences. It's just been overall painless. I open up the website and work on my rich text docs and it all goes fine.
The only real issue I've had is with network stability issues, which caused me to desync frequently, requiring the page to reload. lost a whole paragraph once. It's apparently because of how the encryption needs to work, if it were seamless through that trouble, it would allow a man in the middle attack to work.
I do like that it's end to end encrypted. Even a soupcon of security and privacy is balm for the soul.
You have to have the paid version of cryptpad to use their full Word or Power Point analogs, but the rich text editor fulfills my needs. So does their spreadsheet software, but I'm definitely not a power user.
My single use of their diagramming thing went okay.
I haven't tried any of their other file types (Kanban, Code, Forms, Whiteboard, Markdown Slides), but many of them are forks of open source projects, like OnlyOffice, so should work as well as those (which is reaching the point, imho, where it's often better than the crud-laden "professional" alternatives).
You "only" get 1GB of storage free.
Collaboration has been seamless. I have a large multi-file creative project I've been working on with a friend and it's been just fine.
3 notes
·
View notes