#google online coding course
Explore tagged Tumblr posts
Text
Learn Digital Marketing Near Me with Experts at Code with TLS
If you're searching for a Digital Marketing Institute Near Me, look no further than Code with TLS—a trusted name in the world of tech course providers. Whether you're a student, working professional, or entrepreneur looking to upskill, our expert-led digital marketing training is designed to help you grow in today’s digital-first world.

Why Choose Code with TLS for Digital Marketing?
At Code with TLS, we believe that learning digital marketing should be practical, personalized, and up-to-date. Our trainers are industry professionals with real-world experience, offering insights that go beyond textbooks. From SEO and Google Ads to content marketing and social media strategy, we cover it all.
Located conveniently for local learners, we’re the perfect answer for those looking for a Digital Marketing Institute Near Me. Our hands-on approach, live projects, and placement support set us apart in the tech education space.
Course Highlights at Code with TLS
✅ 100% Practical Training
✅ Certified Trainers with Industry Experience
✅ Latest Curriculum Based on Market Trends
✅ Live Projects & Case Studies
✅ Interview Preparation & Placement Assistance
✅ Flexible Batches (Weekdays & Weekends)
Whether you want to become a digital marketer, start your own business, or land a high-paying job, our digital marketing course gives you the tools and confidence to succeed.
Who Can Join?
Students & Graduates
Freelancers & Entrepreneurs
Working Professionals
Job Seekers looking to enter the digital space
No prior technical knowledge is required—just a willingness to learn and grow.
Boost Your Career with Code with TLS
As a top tech course provider, Code with TLS ensures that each student receives mentorship, practical exposure, and career guidance. Our reputation as a leading Digital Marketing Institute Near Me has made us the go-to choice for aspiring digital marketers across the region.
#Digital Marketing Institute Near Me#Digital Marketing Course#Learn Digital Marketing#Tech Course Provider#Code with TLS#Digital Marketing Training#SEO Course Near Me#Social Media Marketing Course#Best Digital Marketing Institute#Online Marketing Classes#Career in Digital Marketing#Digital Marketing for Beginners#Google Ads Course#Practical Digital Marketing Course#Digital Skills Training
0 notes
Text
Beauty AND brains. Your knowledge is your weapon.
Let's not only be insanely beautiful but also disgustingly educated. Other than discipline and hard work, your knowledge is your weapon in this world of chaos, something that you can sharpen and use.
Where can you expand your knowledge? What areas, what topics
How can you expand your knowledge? In different circumstances and preferences such as if you're too busy or if you have a short attention span

Where can you expand your knowledge?
I DO NOT mean that you need to be an expert at everything. You don't need multiple degrees for each type of intelligence. However, if you want to sharpen your weapon, sharpen your knowledge.
These are the areas where you CAN sharpen your knowledge AND the areas where you SHOULD know the basics in:
Emotional, Communication, Morals, Ethics. Be human, and make others feel human too. Cultivate empathy, understand mental health, build your conscience, and differentiate right from wrong. Communicate frequently and effectively.
History, Culture, Politics. The world is chaotic — learn to stand your ground. Understand history, politics, corruption, culture, and the overlooked heroes. Know what shaped the past to navigate the future.
Digital Literacy. The internet is a double-edged sword. Learn to navigate it safely, protect your privacy, spot misinformation, and adapt to evolving technology.
Manners, Etiquette, Body Language. The way you present yourself matters. Respect others, read unspoken cues, and master the art of presence.
Self-Sufficiency, Life Skills, Livelihood. You won’t always have someone to rely on. Cook, clean, manage time, handle money, and adapt to life’s challenges. Be independent.
Literature, Language, Writing. Words are power. Read, write, and communicate with depth. Language shapes history, culture, and thought—use it wisely.
Critical Thinking, Problem-Solving. The world isn’t black and white. Question everything, analyze critically, recognize manipulation, and think for yourself. Don't be swayed easily by others.
Science and Math. The foundation of everything. At least know the basics, enough to understand the forces shaping the world — logic, numbers, and the universe itself.
Self-Care, Hygiene, Fitness, Health. Your body and mind are your greatest assets. Eat well, stay active, manage stress, and prioritize your well-being before it’s too late.

How can you expand your knowledge?
When you have free time When you're busy When you prefer learning visually When you have little to no attention span
You are what you consume. Now that you know what topics you can expand your knowledge on, these are what you can use / do to consume those information:
Have some free time? Do / use these
Read books, take online courses, or watch in-depth documentaries. (Example: history books, finance courses, science explainers) Engage in discussions or debates to refine your thinking. (Example: politics, ethics, critical thinking) Try hands-on learning like experiments, DIY projects, or journaling. (Example: cooking, coding, writing) Attend workshops, seminars, or community events.
Too busy? Do / use these
Listen to podcasts or audiobooks while traveling, doing tasks / work / school work, or doing chores. (Example: podcasts on Spotify / Tiktok, Youtube videos where the creator is more on speaking, audiobooks on Audible or by downloading a free e-pub format e-book online then uploading it into Google Playbooks and using the audiobook / text-to-speech format) Follow bite-sized content on social media. (Example: short educational / history Tiktok videos, digital literacy infographics, photos on Pinterest) Take advantage of apps and tools for productivity, learning, etc. (Example: budgeting apps, language-learning apps) Watch short, informative videos during breaks. (Example: TED-Ed, Ted Talks, short Tiktok videos)
Like to learn visually / by watching? Do / use these
Watch video explainers, documentaries, or animated infographics. Use apps that gamify learning. (Example: Duolingo for language, Codecademy for coding) Follow visually engaging content creators. (Example: finance charts, body language breakdowns) Make mind maps or illustrated notes to break down complex topics. (Example: self-care routines, political structures, problem-solving techniques)
Little to no attention span? Do / use these
Learn through short-form content like TikToks, reels, or infographics. Play interactive or gamified learning apps. (Example: strategy games, trivia quizzes) Follow meme-based or storytelling-style education accounts. Try hands-on, fast-paced activities. (Example: debate flash rounds, real-world problem-solving challenges, DIY experiments)

Begin small, learn the basics, take a step at a time, and start from there. Be BOTH beauty and brains. You have a weapon (your knowledge), sharpen it and use it.
#strawberrysznn#strawberry#self love#mental health#mindset#mental growth#it girl#growth#glow up#girlblogging#self growth#self improvement#this is a girlblog#self help#advice#self care#selfhelp#reminder#life advice#self reminder#it girl energy#becoming that girl#girlboss#girlblog#self development#pink pilates princess#clean girl#health and wellness#glow up tips#dream girl
1K notes
·
View notes
Text
Yesterday I went on Google to find whether the funky little light-up wheels you strap to your feet are still a thing. Not because I want to buy them, but because I was feeling nostalgic. And they are a thing! You can still buy them. But, again, I'm not gonna.
Anyway, now every single ad I see on Tumblr is just a picture of the light-up heel wheels. And since I've unfortunately already had to accept the fact that I'm being tracked, I'm pretty happy about that. Instead of annoying ads (like ones with text where I subconsciously stop to read them) or ads that might actually tempt me into buying something, I just see some funky lil wheels.
#I've hacked the system#next time I start seeing ads for stuff I don't like I'm gonna spend time googling prints of cute cats#or like. fishing equipment idk#I'm sick of ads for baby stuff and online courses i literally don't have a baby or time to learn coding in ten easy lessons#life hack#i guess
0 notes
Text
i made a google sheet a work that took rsvps from our instructors who are agreeing to teach this year out of the system where they RSVPed
then it calculates a unique ID for them based on name and local union
then there are sheets broken out by course number (because each first number has a different person coordinating those instructors) and filled with the info we used to contact them. these generate the same unique ID from their name and local union
then i used if(iserror(vlookup script to pull over their rsvp, the email they entered, and any questions or concerns they had
and then i used conditional formatting to highlight anyone whose entered email didn't match the one we sent their invite to so we can update it in our system
and my boss took one look at this and said "you know no one else in our department can do anything even approaching this?"
so i texted my dad to thank him for teaching me how to do vlookups.
sincerely, if you are starting out in your career, learn how to make excel do a tiny bit of magic and you will go so so very far.
learn how to do vlookup, xlookup, if, iserror, countif, and sum and you'll be most of the way there. conditional formatting is annoying, but useful. pivot tables, if used correctly, might get you referred to the spanish inquisition. and VBA scripts! you can do so much stuff automatically with VBA. I use it every year to break our course evaluation master into individual sheets based on course and instructor. takes me 20 minutes instead of 3 weeks it would take doing it by hand.
you can get a lot of pre-written VBA code online as well, so as long as you know how to activate the developer console, you'll be fine. it's nowhere near as scary as you think it's gonna be.
learn excel. learn spreadsheets. you'll thank me for it.
811 notes
·
View notes
Note
When did people start just accepting online ads?
Ads used to be considered dangerous, and the point of an adblocker wasn't just to keep annoyances to a minimum, but to protect your computer from malicious code and protect you from accidentally clicking on a phishing link.
The ratio of ads from legitimate companies that want to sell a product that actually exists to malicious ads that are attempting to spread viruses or steal credit card info has shifted over the years, but the legitimate companies have also started using more malicious tactics (such as fake "start" and "close" buttons). And websites themselves are in on it, and help ads disguise themselves as part of the page all the time (google's search results are predominantly disguised advertisements).
And the phishing scams and viruses still exist, of course.
Ads in general have never stopped being malicious, so why did people start thinking of them of as just everyday annoyances like autoplay MP3s instead of as serious threats to their PC or personal info?
--
128 notes
·
View notes
Note
how different do you think demon slayer would've been if they had modern stuff like phones, social media, video games, better transportation, T H E R A P Y?
Would there be constant online arguments between the hashira and the upper moons?
Just curious on what you think would happen if this were the case
Hi anon! Sorry for the late reply! Here are my headcanons with a little SaneGiyuu sprinkled in of course.
The Hashiras and the Upper Moons would definitely have Whatsapp chat groups where the Master would call them for meetings, they would discuss about their missions and they would clown on Giyuu 😂
The therapy would be one of those closed room sections where they can rant about their colleagues and missions kinda like the way contestants do in Big Brother or Total Drama Island.
...
The Infinity Castle would be an office similar to how it is in the Gakuen. Akaza is desperate to make Rengoku a demon because he needed a (boy)friend in his toxic workplace.
Kokushibo is the bossy, know-it-all who thinks he's the second boss, he definitely has the company logo as his social media profile pic and talks about putting the company first yada yada yada
Douma is the snake that pretends to be nice to you but talks about you when you're not around, preys on the new female hires, and has a special seat reserved for him in the HR department.
Nakime is the colleague that keeps to herself, does their work, doesn't really talk to anyone and peaces out once it's 5.
Gyokko is the suck up who tries to see how far they can push their nose up the boss's ass to get a promotion or recognition.
Hantengu is the old head that pretends to be incompetent and pitiful so that you'll end up doing all their work
Gyutaro and Daki are the gen-z types that hate the job but need the money, won't stop questioning authority and who you're secretly jealous of because of their gutsy behavior.
Akaza is the only sane one who has an already drafted resignation letter saved on his computer desktop that he wants to submit every Monday or everytime Douma opens his mouth. He copes by scrolling through office/shitty colleague memes, snorting coffee and dreaming up fantasies about the office exploding.
Douma has been banned from the Upper Moon group chat for posting too many memes and Blue Spider lily troll posts.
...
Giyuu constantly forgets the gate code to the Master's mansion when there's a Hashira meeting and when he asks on the group chat the other Hashiras mostly ignore him.
Sanemi dms him and gives him the code after calling him a dumbass.
Gyomei is always posting cat pictures and videos on the group chats.
Tengen takes a selfie during every mission and posts ot on his status.
Giyuu's driver is always late because he is old and always forgets where Giyuu's house is but Giyuu doesn't have the heart to fire him because the driver cares for him like a grandson.
Sanemi drives himself to his missions.
Rengoku always types in capital letters and Obanai is always asking why he's shouting.
Mitsuri has an Instagram where she posts about fashion, her cats and food. Obanai likes every post, he also likes every Mitsuri group chat post no matter how silly it is.
Whenever Rengoku goes on missions, he always visits the restaurants in the area and gives ratings and reviews on Google Maps.
Muichiro, Genya, Kanao, Inosuke, Zenitsu and Tanjiro spend their free time on their shared Minecraft server making cool builds.
Zenitsu screams whenever there's a creeper around, Inosuke just runs towards it like an idiot. He has the highest respawn rate out of any of them.
Tanjiro always greets each of the villagers he encounters, he's even nice to the traveling merchant. He also has a lot of dogs and cats. His base is in the jungle because of the pandas. He likes to explore and collect lots of resources.
Muichiro, Kanao and Inosuke like to explore the caves. Inosuke likes to sneak into Zenitsu's base and steal his stuff. He also has a lot of dogs which he calls the Hoard.
Kanao makes fancy builds and has a lot of xp, food and resource farms because she values efficiency and she always shows off her builds to Shinobu and the butterfly girls. She's the first one in the group to get netherite armor and sword.
Inosuke is banned from several stores and malls especially Walmart.
Sanemi and Obanai play COD together and bully/kill teammates or other players who are misogynistic and shout slurs.
Giyuu saves the Hashira's names formally on his phone but saves Sanemi's with his first name.
Giyuu and Sanemi text each other constantly and Sanemi always asks if he's eaten and offers to cook food for Giyuu at his place.
Shinobu always trolls Giyuu on the groupchat and she's banned from several pharmacies for her questionable requests about poisons but has settled for ordering them from the dark web.
She's currently on a watchlist for her ties to several eco-terrorist groups. She had a channel where she talked about poisons and bombs but it was taken down by YouTube.
She often takes the butterfly girls for ice cream and they have movie nights. Her favorite movie is Jennifer's Body and Mean Girls, least to say Aoi and Kanao are very concerned for her.
Muichiro always has to explain gen-z slang and memes to Gyomei.
Tengen is always posting thirst traps on Instagram along with pictures of his wives.
...
Kokushibo always handles Muzan's Amazon orders. Muzan orders a lot of hair products, he shops at designer stores and has a Sephora membership card.
Gyutaro and Daki are always bullying kids on Roblox and griefing peoples builds on public Minecraft servers.
Gyokko's Instagram page features his pots and 'art pieces', Hantengu likes all his posts.
Akaza listens to Avril Lavigne and posts about his colleagues and how he hates his job on Reddit and Tumblr.
The Infinity Castle wifi password is Muzan4prez set by Douma of course.
Nakime's favorite channel is HGTV because she's always looking for ideas on how to redecorate the Infinity Castle.
Muzan always watches E! especially when the Awards Season comes around. He's especially fond of the Met Gala. His favorite show is Hell's Kitchen.
Kokushibo likes watching the National Geographic channel and NatGeo wild on occasion.
...
The Master always forces Shinobu, Sanemi, Obanai and Giyuu to have professional therapy sessions. He also checks up on them to make sure they go every week and bribes them with movie nights with him.
He always posts motivational quotes and positive messages for the Hashira but isn't above posting memes and troll posts every once in a while. Sanemi likes all of his posts, chats and comments.
...
That's all I can think of for now. The slaying of the demons will be the same, they would still use katanas because they're more efficient than guns.
#demon slayer#kimetsu no yaiba#kny#kny anime#demon slayer anime#unhinged asks#upper moons#hashira#demon slayer hashira#sanegiyuu#sanemi x giyuu#giyuu#gyomei himejima#kny tengen#kny shinobu#demon slayer tanjiro#kny genya#zenitsu agatsuma#demon slayer inosuke#giyuu tomioka#kny au#kny spoilers#kny headcanons#unhinged hc#kokushibo#shinobu kocho#demon slayer mitsuri
141 notes
·
View notes
Text
creepypasta headcanons: Liu, Jeff, EJ, Jane, clockwork, and Toby in that order.
Tw drug use, sexual abuse mention
Might do more once my paranoia dies down
Liu
-Has a mad crush on Eyeless Jack but hates himself too much to think anyone could ever love him
-was 23 when Jeff murdered their parents and all that
-field medic of the proxies. Eyeless is the doctor, Liu is out in the field. He took three online anatomy courses before giving up, making him the second most qualified doctor. Frequently lectures Toby on where the arteries and vital organs are.
-Recovered addict. Hit rock bottom after going on the run from killing that nurse and converted to catholicism in NA. Wears his scarf and jacket as much as possible to hide the track marks but no one's ever noticed them regardless.
-Fell off the wagon when he had to leave a proxy to die in the field to save another, but Jack cried when he had to narcan him so he got right the fuck back on
-theater kid. Has gotten drunk once and sang Noel's Lament perfectly in front of everyone but will deny it ever happened if asked.
-grew up mormon, in utah, went on a mission before Jeff ruined his life (I'm sorry guys the remake story is the most st george coded shit I've ever read)
Jeff
-also raised mormon because he's liu's brother. Pisses in the flower beds of any temple he sees because he wants to and feels like it.
-car guy. No justification. I can just see him creaming his pants at a car show and cussing Toby out for ticking while he's holding the flashlight under the hood of an old firebird he's fixing up.
-was seventeen when he murdered his parents. Fell in love with a sex worker after he fucked up his face and she was the only person not to run away (for a price) and will get fucking pissed at anyone who even implies that he might be traumatized by it.
-uses a switchblade instead of a kitchen knife after tripping and accidentally stabbing himself while carrying the big knife in his hoodie
-let Nina give him a tattoo that says "Wicked Clowns Never Die" but Liu laughed for fifteen minutes straight when he saw it so now Jeff is embarrassed by it
-everyone knows he's gay except for him.
Eyeless Jack
-Has a mad crush on Liu but hates himself too much to think anyone could ever love him
-over a hundred years old. I felt like the tar ritual that made him a demon would be a tar-and-feathering sort of deal. Jeff will call him Chicken Man when he's being a dick.
-Got really into the whole "raw meat" fitness trend on social media because he eats like that anyway.
-big boy. Organs are really calorie dense. I will not be taking criticism.
-his face isn't necessarily inhuman, but he looks more like a melted wax figure under the mask. Mouth a little crooked, eyes a little too long...uncanny valley mostly.
-He can't actually see. He's got freaky demon powers, though, that let him "see" the veins, arteries, and other equivalent systems in living things. He can get around just fine in the forest because it's all alive, but he needs a white cane if he goes to the city.
Nina
-bought a tattoo gun for 50$ and drew a bunch of hearts and stars all over her arm. Begs people to let her tattoo them. VERY passionate about how racist the tattoo industry can be about colored tattoos on dark skin, and she is very determined to learn how to tattoo properly so she can make sure everyone can have cool color tattoos. EJ begrudgingly let her tattoo a flower on him because of this and it looks terrible, but he appreciates the sentiment.
-hardcore fujoshi but only because she hasn't figured out she's nonbinary yet
-not great on personal hygiene, but neither is Jeff so it doesn't bug her. Does not shave for shit (queen)
-has the most tone deaf true crime channel where she does mukbangs and romanticizes serial killers. Has been cancelled at least three times.
-incredibly creative with cursing. This girl could make a sailor blush when she gets mad. Once ended an argument with Ben when he had to Google what she just called him.
Jane
-drug dealer for the proxies. You can smell her coming from a mile away because of how much weed she smokes. Stays at the manor despite her hatred of serial killers for the money, which she sends to her sister.
-Mostly stays depressed in the attic, ocassionaly coming down to smoke out Nina, who she only likes because she's just unapologetically insane and entertaining. Did a true crime mukbang with her once but had to leave halfway through because it pissed her off.
-really likes plants. Her room looks like a jungle. Has installed at least ten new shelves in the attic to support her plant addiction.
-plays video games with Ben. They tolerate eachother because they're the only ones good enough at games to give the other a challenge.
-tried getting therapy through betterhelp. It ended about as well as you'd expect.
-fucking hates cops. She has to resist the urge to shred pork when she's in the city doing a drug run. Comes with the "hating people who kill remorselessly" territory but it could also be because she's committing several felonies and is on edge.
-oceans of lesbian porn on her computer and so many sex toys good lord
Clockwork
-has a dissociative disorder, but it doesn't present like Liu and Sully in the sense that she had a split personality, moreso that it just makes her lose time. OSDD-1A if you want to get technical.
-raging kleptomaniac. She hasn't paid for anything in years. Goes into a blind rage when people tell her to get a real job because she already loses enough time as it is, and says it's cruel to expect her to throw more of it away.
-immediately came out as gay and shaved her head after reading Stone Butch Blues. Nina cuts her hair. It never looks great, but it looks good enough to Nat.
-She's the only one at the manor that Jeff and Toby are wary of, and won't even take off her shirt to let Liu or Jack patch her up. They need to call Jane down to help and give her instructions from outside the door. It's entirely a trauma thing.
-Really smart and witty when she's in a good mood. In good weather she'll be laying in a hammock outside either crocheting or reading a book. Her favorite genre is fantasy.
-Tried hosting a DND night but it just kind of went up in flames because of the way everyone is.
Toby
-this boy is a little too rough at best and a raging sadist at worst. The CIPA just makes him unaware that people can even feel pain until they're screaming in agony, and at that point he just gets fascinated.
-Also has really bad health anxiety. Life expectancy for people with CIPA is 21 because they don't feel those aches and pains that tell them something is wrong and that they need to go to the doctor. He's 24 and constantly getting hurt
-Once got an x-ray and the doctor called everyone in the gawk at how many of his bones had healed improperly.
-jeff made fun of him because his mouth guard looked like a muzzle and accidentally gave him a barking tic
-Collects bones. My au centers around a group of people that failed at their jobs as proxies and are forced to work as crime scene cleanup for the operator, so Toby doesn't get to keep the bones of most of his kills. Jeff will ocassionaly bring him a bone or a dead bird like the goddamn lapdog he is and it makes his fuckin day.
#creepypasta#jeff the killer#ticci toby#homicidal liu#eyeless jack#jane the killer#nina the killer#creepypasta hcs
31 notes
·
View notes
Text
"How Technology is Changing the Way We Learn"
In the past few years, there has been a sudden rise in the use of technology in various aspects of life, especially in education. With the increasing availability of digital tools and online resources, students now have more access to more information and learning opportunities than ever before. This shift has significantly changed the way we students study, collaborate, and comprehend academic content. As a Senior High School STEM student, I’ve witnessed firsthand how technology has shaped our academic journey throughout the years. Here are various reasons why technology is changing the way we learn.
1. Access to Various Sources
Back in the earlier days, the library was the primary source of information. The library was a haven not just for bookworms, but for students who needed help with their homework. The library had a collection of books that were full of specific information that assisted students in finding answers, solutions, definitions, and terms needed for their homework. Growing up in Gen Z like myself as a STEM student relies much more on technology nowadays than a physical library because with a touch of a smartphone or a click of a computer, you now have access to different websites that contain the information you need, especially when you need to conduct a research study, which most students use Google Scholar.
2. Interactive Learning Tools
Textbooks are no longer the only tools we use to learn. Interactive apps, simulations, and educational games have become commonplace in many classrooms. As a STEM student, I’ve experienced how these tools make learning more engaging. Apps like Khan Academy offer interactive courses in math, physics, and computer science, breaking down complex topics into bite-sized lessons with visual aids.
Platforms like Quizizz display flashcards that could help students enhance their active recall, memorizing, and understanding of the concepts easily because of the quiz game it offers.
3. Collaboration in Real-Time
One of the biggest changes technology has brought to education is the ability to collaborate in real-time, regardless of any location in the world. Platforms like Google Docs, Microsoft Teams, and Zoom have been helping students ever since the Covid-19 pandemic struck. During the pandemic, remote learning platforms became essential for continuing education. Even though many students faced challenges with online learning, these platforms provided a way for education to continue without interruption all thanks to the implementation of Online Classes. Now, blended learning—combining in-person and online education—is becoming the norm, offering more flexibility for both teachers and students.
4. Personalized Learning
Every student learns differently, and technology is helping cater to these individual learning styles. Adaptive learning platforms use algorithms to tailor lessons to each student’s needs. If you’re struggling with a particular topic, these platforms adjust the difficulty and provide extra support until you grasp the concept. Tools like Duolingo and Grammarly, which offer students language and grammar support are just a few examples of how technology provides customized learning experiences.
For us STEM students, this is particularly helpful, especially when using Grammarly for a research project. Using Platforms like Grammarly helps correct revisable sentences and paragraphs easily in one click, providing less effort and less time-consuming for us students.
5. Preparation for the Future
Technology isn’t just transforming education for the present; it’s also preparing students for the future. As technology like AI and Programming evolves, we students could resort to learning skills like coding, and learning the different types of programming languages so that we could adjust to the evolving technology all around us.
6. The Potential Downsides
While technology has brought us numerous benefits, it’s important to acknowledge the challenges and disadvantages it presents. Overreliance on technology can often lead to distractions, with social media and games constantly thriving for attention. Furthermore, the concept of Technology and its use remains a problem in many parts of the world, where students lack access to the necessary tools and internet connectivity to fully benefit from online learning resources.
14 notes
·
View notes
Text
Another Käärijä Research Project
aka: käärijä style-shifting project
as a preface, here are my (non) qualifications for this project and the circumstances under which it happened:
I am a linguistics student, and this past semester I took a course on sociolinguistics. the goal of this project was to become familiar with the concept of and analyze style-shifting (it's more commonly known as code-switching online but theres a difference and this is style-shifting), specifically by analyzing the speech of one person. We had the option to study oprah or to have someone else approved by my prof, so you know I had to ask my prof if I could study jere. This project is solely my intellectual property; even though I had a tutor help me a lot, everything written in this paper and on this post was my work alone.
now, on to the actual findings! the full paper and transcripts will be linked at the end :D
the actual variables (words or sounds) that I studied were the pronunciation of r, and use of the word "the".
to make things a lot easier from the get-go, i'm going to introduce you all to one of my favorite websites, ipachart.com (the international phonetic alphabet [ipa] chart is a big chart with an entry for every sound that exists in a language. this handy dandy website has an audio recording for each one of those sounds).
go to this website, and then scroll down to the table. go to the column labeled "post alveolar" and then click on ɾ and ɹ. those are the sounds i studied in this paper! ɾ is the finnish r and ɹ is the american r :)
so basically what i did to find instances of my variable was i just looked up a bunch of esc interviews and listened out for use of the different r sounds. i also transcribed the entire dinner date live because i love torture apparently :) the specific interviews and lives/stories are in the bibliography of the paper :p
after i transcribed all the interviews and lives/stories i went through and highlighted every instance of the r sound. then i calculated the ratios of ɾ to ɹ based on the context they were spoken in. the two contexts i looked for were formal contexts (sit-down interviews) and informal contexts (literally anything else).
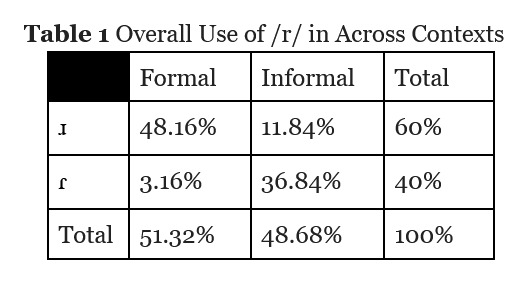
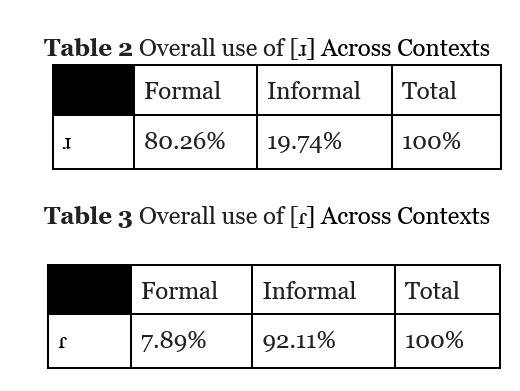
i found that jere uses ɹ WAY more often in formal contexts than he does in informal contexts, and the same in reverse with ɾ.
i then went back to the transcripts and looked for all instances of the word "the". i also looked for instances where i thought it should be present, but was omitted. i calculated the ratio of present vs omitted "the"s in formal vs informal contexts and made some charts.
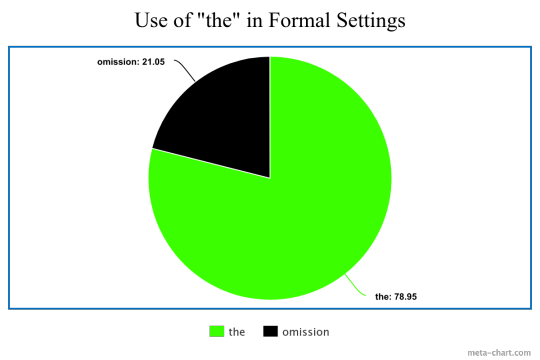

the graph with the smaller black section is "use of 'the' in formal settings" and the one with the smaller green section is "use of 'the' in informal settings" (the images are transparent, sorry)
i found that jere uses "the" WAY more often when in formal settings! there were also some instances where he added a "the" where it was unnecessary, which is studied at length in this wonderful paper by @alien-girl-21
something i also noticed that i elected not to study because this paper took enough energy on its own was that in formal contexts, whenever the "or" sound came in the middle or at the end of a word, jere wouldn't pronounce the r. it stuck out to me mostly because i heard words like "performance" turning into "perfomance", which i thought was an interesting quirk.
unfortunately i was somewhat limited by both my brainpower and capacity to do more work on this paper in the relatively short timeframe i was given (2 weeks) and the fact that i was given a 5 page MAX for this paper (not including a bibliography). i had a lot of fun doing this though and am definitely planning on studying jere for for academic credit again in the future if given the chance!
also i would like it to be known that i spent an hour searching for that 5 second clip of the urheilucast where jere said that he used to sell kitchens and understands english better than he can speak it.
link to a google drive folder with the actual paper i wrote and the transcripts of the interviews with notation:
please feel free to send me asks and dms with questions or comments about this paper! i absolutely love rambling about linguistics :3!!
#i think this is everything!#it always feels so much shorter than i think its going to be#both because of how much effort i put in#and also because i was constantly comparing myself to cyns paper 😅#my irls kept reminding me that i didnt have to and in fact wasnt allowed to write 43 pages analyzing jeres speech#but i kinda wanted to#i also wrote this paper on april 2nd#i remember that because the previous day i spent all day booping#and then i literally worked all day from 9.30 until 23.30 on stuff for my linguistics class#because i had this paper due on friday or saturday and i had a research summary due on that thursday (the 4th)#it was so much work that made some things worse but god was it worth it#linguistics my beloved <3#käärijä#into the tag you go#i reserve the right to edit this post if i realize there are any problems#linguistics
51 notes
·
View notes
Text
Just thinking aloud about fame, celebrity, and Pluto in Aquarius...
When Britney Spears was released from the conservatorship there were posts about how it's likely Britney might not be as internet-literate or socially appropriate as we'd like her to be, considering everything she went through. The posts encouraged others to be patient and understanding, and not to cancel her if she happens to make any mistakes.
Just now I saw a similar point about Gypsy Rose Blanchard. Now that she's released she intends to make herself very public online, but her entire life (32 years) has been spent in either one prison or the other. There are concerns for how she might adjust to the internet we know today, seeing as how she likely didn't get the opportunity to grow alongside social media the way the rest of us did.
In the 2024 Year Ahead Forecast from The Astrology Podcast they brought up the Pluto in Leo generation, and how that period of time and that generation relate to the making of our concept of "celebrity". They're also the generation that are holding on to power (like the presidents of the USA). Pluto in Leo gen is also unique because it's one of the only Pluto generations that is likely to live to their Pluto opposition, which is happening now. With this Pluto opposition, the pod talked about how the idea of who gets to be in power is likely to change. As well as our concept and relationship with "celebrities".
In 1991, Pluto in Scorpio (square to Pluto in Leo, if it matters. Whether it matters is still something I'm exploring here), Michael J. Fox was diagnosed with Parkinson's. I'm not actually sure how public illness was allowed to be previous to that. I just remember growing up how Michael J. Fox was something of a special case, and his celebrity status helped make massive leaps in awareness and research for Parkinson's.
Hollywood became big in the 1920's, when Pluto was in Cancer. While Pluto has been in the opposite sign, Capricorn, I feel like I've heard about a million celebrities coming out with illness. Justin Bieber, Selena Gomez, Bruce Willis. Recently, Celine Dion. If you Google it, there are lists of dozens of celebrities with chronic illnesses. Not to mention mental illness, which has become that much more public.
My feeling at this point is that there are themes of privacy, hidden and internal illness, and representation here that we've seen getting dug up from the Pluto in Cancer era. True crime stories from old Hollywood, being open about mental illness, exposing how child talents have been exploited by the industry, and of course, hidden afflictions to celebrities are changes we've seen around fame through the trine, Pluto in Scorpio, and opposition, Pluto in Capricorn.
Most obviously, though, who gets to be famous has changed the most in the last 20 years. It used to be only special, hand-picked people who got to be famous. Now it could be anybody with a cell phone.
I think of this blog post on the Aries Point by Ace (AliceSparklyKat), where they talk about how the angular points seem to manifest. They've noticed that celebrities whose Sun is at 0 degrees Cancer seem to be regarded as chameleon-like in their nationality, form, or culture, and those with 0 degrees Capricorn seem to be known for a peak example for one nationality, form, or culture. I wonder if this can be seen in this shift to influencer culture, particularly in the rhetoric that celebrities until now have been made to represent everybody. But now, after Pluto in Capricorn, we are much more aware of the consequences of not having fair representation of more nuanced, individual experiences. At first it was all about art and talent. Now, it's about the hard tacks of who gets what job and why, and the consequences of story. Very Cancer to Capricorn opposition coded.
Anyway, I feel like I've noticed a lot of celebrities becoming ill in the past, and now I feel like I'm seeing some "taboo" issues come up in influencer culture. I'm wondering about how this could be gearing us up for Pluto in Aquarius.
What do you think??? I really want to hear your thoughts!
95 notes
·
View notes
Text
Ok apparently some people missed this, and it is my favoritest of star stable lores, so welcome to the most prolific source of star stable dunk jokes, the Ride with us campaign and it's charity.
Ever wonder why we say horsegirl is a slur? Or why we say horsegirls bite? Look no further than the absolute wreck that was star stable trying to do something good with their money.
The day is august 25th. The time? Time for revolution. Star stable online launches its shakiest campaign yet, and they do it on every possible platform. Youtube, Instagram, Twitter, even their website which still has a permanent addition. It's truly taking the world by storm.
Standing on hopes, dreams, and a mildly skewered survey sent out weeks prior, Star stable proudly proclaims that horse girls are crazy, obsessed, and weird, and that they are bullied for this. Well, no longer, they cry. They come bearing a hashtag that only massive social backlash could topple. "Reclaim horse girl".
People were (rightfully) pissed that they were likening horse girl to a slur that could be reclaimed, star stable pushed back, people got even more pissed, and finally they course corrected and changed the hashtag to "yes i'm a horse girl" because, despite our jokes, horse girl is in fact not something that can be likened to slurs people need to reclaim.
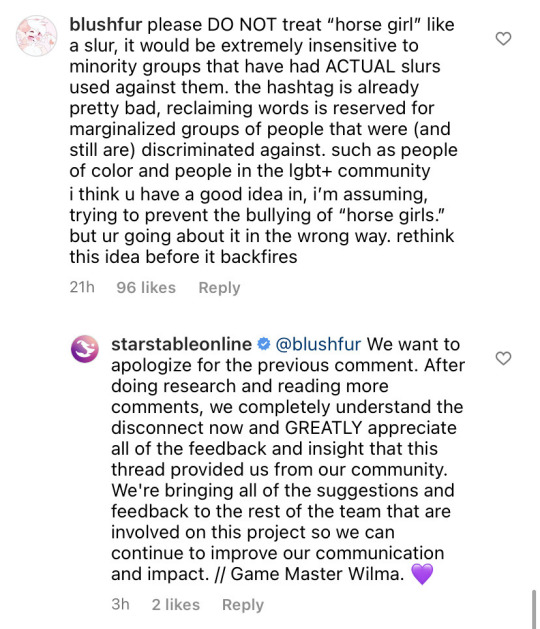
Their claims were so hilariously insane that people thought screenshots from the promotional video were photoshopped

On august 25th, they release the code RIDEWITHUS which would give every player an ingame hoodie, and with every redeem, star stable would donate 1 SEK to an unspecified charity. They did not further specify anything about this charity, only that it was meant to be for anti-bullying. As we all know, not all charities are good, so I personally didn't redeem the code until I knew where the money was going, and oh boy did I have to wait.
Over the course of the next 35 days, star stable made several instagram posts describing the results of the survey they sent out that launched this entire ordeal. I could screenshot all the individual posts but that's a lot of work so here you go, here's the source behind the information found in the posts instead.

When I asked on twitter why we weren't allowed to know what charity the money would go toward, I received the response that starstable were very busy trying to figure out a platform to let people vote for one of multiple charities that they had deemed fit (I was not told what the options would be).
A few days after the instagram posts ended, on october 4th, we were told what charities we were going to be voting for. The vote took place in a Google form, a decision a month in the making. The two charities we were allowed to pick between was Friends and Children's helpline. Finally knowing where the money would be going, I felt comfortable redeeming the code with only THREE days left until the code would no longer work and the charity collection would end.
The code stopped working october 7th, on october 10th we were finally told, officially, that 150 286 kr was going to children's helpline and then star stable raised their prices by 10 % immediately afterward and the Ride with us campaign died and wasn't mentioned ever again, kept alive only by people censoring the words horse girl and biting each other.
Truly a fuckfest. A beautiful moment in time.
81 notes
·
View notes
Note
recently been thinking about how funny it would be if the soft!gfs teamed up and made one of those tiktoks that's like "we're [blank], of course we..." and the first thing is "we're munagenius gfs, of course all of our partners have kissed on stage"
stop i looooooove this
i love asks like this bc this is sooo soft!gf coded (obvi don't have to be soft or be gf, its a lifestyle) anything in this same like social media vein is so fun to write (and talk to my friends about bc they help me)
"We're munagenius's gfs..."
ofc all of our partners have kissed on stage
ofc we have silly t-shirts made and wear them unironically
ofc we all hang out while our partners are on tour
ofc we share a google calendar
ofc we've met taylor swift
ofc we've cosplayed as our partners and recorded a silk chiffon cover
ofc we listen to our partners music
ofc people think we're unemployed
ofc we watch edits of our partners on tik tok
ofc we get free tickets and backstage passes to shows
ofc our pets have fan accounts on instagram
ofc we screenshot unhinged thirst comments
ofc we have a group chat
ofc we talk shit in said group chat
ofc we know the art of a mysterious photo dump
ofc we aren't media trained
ofc we have all of our favorite products in travel sizes
ofc we have to share our partners with teenagers and strangers online
ofc we all want to be on gayotic
ofc we "salt in the wound", "silk chiffon", and "crying on the bathroom floor" backstage together
ofc when we post on social media the first comment is "where's __?"
ofc we all have matching shirts that say "number one fan"
and matching underwear that says "rockstars only"
ofc we never get tired of saying "I'm with the band"
ofc we are amazing plus ones
ofc we are there to distract during photo shoots
ofc we have tons of bts that the world will never see
ofc we feel very lucky and in love (this is said with sarcastic disdain)
my babies @ever-siince-new-york, @boywithpinkcarnation, and @whore4munagenius helped me w this and i love them and their brains a lot
#anon cutie#muna x reader#boygenius x reader#munagenius!gfs#munagenius x reader#munagenius blurb#julien baker x reader#lucy dacus x reader#phoebe bridgers x reader#naomi mcpherson x reader#katie gavin x reader#josette maskin x reader
145 notes
·
View notes
Text
On paper, the first candidate looked perfect. Thomas was from rural Tennessee and had studied computer science at the University of Missouri. His résumé said he’d been a professional programmer for eight years, and he’d breezed through a preliminary coding test. All of this was excellent news for Thomas’ prospective boss, Simon Wijckmans, founder of the web security startup C.Side. The 27-year-old Belgian was based in London but was looking for ambitious, fully remote coders.
Thomas had an Anglo-Saxon surname, so Wijckmans was surprised when he clicked into his Google Meet and found himself speaking with a heavily accented young man of Asian origin. Thomas had set a generic image of an office as his background. His internet connection was laggy—odd for a professional coder—and his end of the call was noisy. To Wijckmans, Thomas sounded like he was sitting in a large, crowded space, maybe a dorm or a call center.
Wijckmans fired off his interview questions, and Thomas’ responses were solid enough. But Wijckmans noticed that Thomas seemed most interested in asking about his salary. He didn’t come across as curious about the actual work or about how the company operated or even about benefits like startup stock or health coverage. Odd, thought Wijckmans. The conversation came to a close, and he got ready for the next interview in his queue.
Once again, the applicant said they were based in the US, had an Anglo name, and appeared to be a young Asian man with a thick, non-American accent. He used a basic virtual background, was on a terrible internet connection, and had a single-minded focus on salary. This candidate, though, was wearing glasses. In the lenses, Wijckmans spotted the reflection of multiple screens, and he could make out a white chatbox with messages scrolling by. “He was clearly either chatting with somebody or on some AI tool,” Wijckmans remembers.
On high alert, Wijckmans grabbed screenshots and took notes. After the call ended, he went back over the job applications. He found that his company’s listings were being flooded with applicants just like these: an opening for a full-stack developer got more than 500 applications in a day, far more than usual. And when he looked more deeply into the applicants’ coding tests, he saw that many candidates appeared to have used a virtual private network, or VPN, which allows you to mask your computer’s true location.
Wijckmans didn’t know it yet, but he’d stumbled onto the edges of an audacious, global cybercrime operation. He’d unwittingly made contact with an army of seemingly unassuming IT workers, deployed to work remotely for American and European companies under false identities, all to bankroll the government of North Korea.
With a little help from some friends on the ground, of course.
christina chapman was living in a trailer in Brook Park, Minnesota, a hamlet north of Minneapolis, when she got a note from a recruiter that changed her life. A bubbly 44-year-old with curly red hair and glasses, she loved her dogs and her mom and posting social justice content on TikTok. In her spare time she listened to K-pop, enjoyed Renaissance fairs, and got into cosplay. Chapman was also, according to her sparse online résumé, learning to code online.
It was March 2020 when she clicked on the message in her LinkedIn account. A foreign company was looking for somebody to “be the US face” of the business. The company needed help finding remote employment for overseas workers. Chapman signed on. It’s unclear how fast her workload grew, but by October 2022 she could afford a move from chilly Minnesota to a low-slung, four-bedroom house in Litchfield Park, Arizona. It wasn’t fancy—a suburban corner lot with a few thin trees—but it was a big upgrade over the trailer.
Chapman then started documenting more of her life on TikTok and YouTube, mostly talking about her diet, fitness, or mental health. In one chatty video, shared in June 2023, she described grabbing breakfast on the go—an açaí bowl and a smoothie— because work was so busy. “My clients are going crazy!” she complained. In the background, the camera caught a glimpse of metal racks holding at least a dozen open laptops covered in sticky notes. A few months later, federal investigators raided Chapman’s home, seized the laptops, and eventually filed charges alleging that she had spent three years aiding the “illicit revenue generation efforts” of the government of North Korea.
For maybe a decade, North Korean intelligence services have been training young IT workers and sending them abroad in teams, often to China or Russia. From these bases, they scour the web for job listings all over, usually in software engineering, and usually with Western companies. They favor roles that are fully remote, with solid wages, good access to data and systems, and few responsibilities. Over time they began applying for these jobs using stolen or fake identities and relying on members of their criminal teams to provide fictional references; some have even started using AI to pass coding tests, video interviews, and background checks.
But if an applicant lands a job offer, the syndicate needs somebody on the ground in the country the applicant claims to live in. A fake employee, after all, can’t use the addresses or bank accounts linked to their stolen IDs, and they can’t dial in to a company’s networks from overseas without instantly triggering suspicion. That’s where someone like Christina Chapman comes in.
As the “facilitator” for hundreds of North Korea–linked jobs, Chapman signed fraudulent documents and handled some of the fake workers’ salaries. She would often receive their paychecks in one of her bank accounts, take a cut, and wire the rest overseas: Federal prosecutors say Chapman was promised as much as 30 percent of the money that passed through her hands.
Her most important job, though, was tending the “laptop farm.” After being hired, a fake worker will typically ask for their company computer to be sent to a different address than the one on record—usually with some tale about a last-minute move or needing to stay with a sick relative. The new address, of course, belongs to the facilitator, in this case Chapman. Sometimes the facilitator forwards the laptop to an address overseas, but more commonly that person holds onto it and installs software that allows it to be controlled remotely. Then the fake employee can connect to their machine from anywhere in the world while appearing to be in the US. (“You know how to install Anydesk?” one North Korean operative asked Chapman in 2022. “I do it practically EVERYDAY!” she replied.)
In messages with her handlers, Chapman discussed sending government forms like the I-9, which attests that a person is legally able to work in the US. (“I did my best to copy your signature,” she wrote. “Haha. Thank you,” came the response.) She also did basic tech troubleshooting and dialed into meetings on a worker’s behalf, sometimes on short notice, as in this conversation from November 2023:
Worker: We are going to have laptop setup meeting in 20 mins. Can you join Teams meeting and follow what IT guy say? Because it will require to restart laptop multiple times and I can not handle that. You can mute and just follow what they say ...
Chapman: Who do I say I am?
Worker: You don’t have to say, I will be joining there too.
Chapman: I just typed in the name Daniel. If they ask WHY you are using two devices, just say the microphone on your laptop doesn’t work right ... Most IT people are fine with that explanation.
Sometimes, she got jumpy. “I hope you guys can find other people to do your physical I9s,” she wrote to her bosses in 2023, according to court documents. “I will SEND them for you, but have someone else do the paperwork. I can go to FEDERAL PRISON for falsifying federal documents.” Michael Barnhart, an investigator at cybersecurity company DTEX and a leading expert on the North Korean IT worker threat, says Chapman’s involvement followed a standard pattern—from an innocuous initial contact on LinkedIn to escalating requests. “Little by little, the asks get bigger and bigger,” he says. “Then by the end of the day, you’re asking the facilitator to go to a government facility to pick up an actual government ID.”
By the time investigators raided Chapman’s home, she was housing several dozen laptops, each with a sticky note indicating the fake worker’s identity and employer. Some of the North Korean operatives worked multiple jobs; some had been toiling quietly for years. Prosecutors said at least 300 employers had been pulled into this single scheme, including “a top-five national television network and media company, a premier Silicon Valley technology company, an aerospace and defense manufacturer, an iconic American car manufacturer, a high-end retail store, and one of the most recognizable media and entertainment companies in the world.” Chapman, they alleged, had helped pass along at least $17 million. She pleaded guilty in February 2025 to charges relating to wire fraud, identity theft, and money laundering and is awaiting sentencing.
Chapman’s case is just one of several North Korean fake-worker prosecutions making their way through US courts. A Ukrainian named Oleksandr Didenko has been accused of setting up a freelancing website to connect fake IT workers with stolen identities. Prosecutors say at least one worker was linked to Chapman’s laptop farm and that Didenko also has ties to operations in San Diego and Virginia. Didenko was arrested in Poland last year and was extradited to the United States. In Tennessee, 38-year-old Matthew Knoot is due to stand trial for his alleged role in a scheme that investigators say sent hundreds of thousands of dollars to accounts linked to North Korea via his laptop farm in Nashville. (Knoot has pleaded not guilty.) And in January 2025, Florida prosecutors filed charges against two American citizens, Erick Ntekereze Prince and Emanuel Ashtor, as well as a Mexican accomplice and two North Koreans. (None of the defendants’ lawyers in these cases responded to requests for comment.) The indictments claim that Prince and Ashtor had spent six years running a string of fake staffing companies that placed North Koreans in at least 64 businesses.
before the hermit kingdom had its laptop farms, it had a single confirmed internet connection, at least as far as the outside world could tell. As recently as 2010, that one link to the web was reserved for use by high-ranking officials. Then, in 2011, 27-year-old Kim Jong Un succeeded his father as the country’s dictator. Secretly educated in Switzerland and said to be an avid gamer, the younger Kim made IT a national priority. In 2012, he urged some schools to “pay special attention to intensifying their computer education” to create new possibilities for the government and military. Computer science is now on some high school curricula, while college students can take courses on information security, robotics, and engineering.
The most promising students are taught hacking techniques and foreign languages that can make them more effective operatives. Staff from government agencies including the Reconnaissance General Bureau— the nation’s clandestine intelligence service—recruit the highest-scoring graduates of top schools like Kim Chaek University of Technology (described by many as “the MIT of North Korea”) or the prestigious University of Sciences in Pyongsong. They are promised good wages and unfettered access to the internet—the real internet, not the intranet available to well-off North Koreans, which consists of a mere handful of heavily censored North Korean websites.
The earliest cyberattacks launched by Pyongyang were simple affairs: defacing websites with political messages or launching denial-of-service attacks to shut down US websites. They soon grew more audacious. In 2014, North Korean hackers famously stole and leaked confidential information from Sony’s film studio. Then they targeted financial institutions: Fraudulent trades pulled more than $81 million from the Bank of Bangladesh’s accounts at the New York Federal Reserve. After that, North Korean hackers moved into ransomware—the WannaCry attack in 2017 locked hundreds of thousands of Windows computers in 150 countries and demanded payments in bitcoin. While the amount of revenue the attack generated is up for debate—some say it earned just $140,000 in payouts—it wreaked much wider damage as companies worked to upgrade their systems and security, costing as much as $4 billion, according to one estimate.
Governments responded with more sanctions and stronger security measures, and the regime pivoted, dialing back on ransomware in favor of quieter schemes. It turns out these are also more lucrative: Today, the most valuable tool in North Korea’s cybercrime armory is cryptocurrency theft. In 2022, hackers stole more than $600 million worth of the cryptocurrency ether by attacking the blockchain game Axie Infinity; in February of this year, they robbed the Dubai-based crypto exchange Bybit of $1.5 billion worth of digital currency. The IT pretender scam, meanwhile, seems to have been growing slowly until the pandemic dramatically expanded the number of remote jobs, and Pyongyang saw the perfect opportunity.
In 2024, according to a recent report from South Korea’s National Intelligence Service, the number of people working in North Korea’s cyber divisions—which includes pretenders, crypto thieves, and military hackers—stood at 8,400, up from 6,800 two years earlier. Some of these workers are based in the country, but many are stationed overseas in China, Russia, Pakistan, or elsewhere. They are relatively well compensated, but their posting is hardly cushy.
Teams of 10 to 20 young men live and work out of a single apartment, sleeping four or five to a room and grinding up to 14 hours a day at weird hours to correspond with their remote job’s time zone. They have quotas of illicit earnings they are expected to meet. Their movements are tightly controlled, as are those of their relatives, who are effectively held hostage to prevent defections. “You don’t have any freedom,” says Hyun-Seung Lee, a North Korean defector who lives in Washington, DC, and says some of his old friends were part of such operations. “You’re not allowed to leave the apartment unless you need to purchase something, like grocery shopping, and that is arranged by the team leader. Two or three people must go together so there’s no opportunity for them to explore.”
The US government estimates that a typical team of pretenders can earn up to $3 million each year for Pyongyang. Experts say the money is pumped into everything from Kim Jong Un’s personal slush fund to the country’s nuclear weapons program. A few million dollars may seem small next to the flashy crypto heists— but with so many teams operating in obscurity, the fraud is effective precisely because it is so mundane.
in the summer of 2022, a major multinational company hired a remote engineer to work on website development. “He would dial in to meetings, he would participate in discussions,” an executive at the company told me on condition of anonymity. “His manager said he was considered the most productive member of the team.”
One day, his coworkers organized a surprise to celebrate his birthday. Colleagues gathered on a video call to congratulate him, only to be startled by his response—but it’s not my birthday. After nearly a year at the company, the worker had apparently forgotten the birth date listed in his records. It was enough to spark suspicion, and soon afterward the security team discovered that he was running remote access tools on his work computer, and he was let go. It was only later, when federal investigators discovered one of his pay stubs at Christina Chapman’s laptop farm in Arizona, that the company connected the dots and realized it had employed a foreign agent for nearly a year.
For many pretenders, the goal is simply to earn a good salary to send back to Pyongyang, not so much to steal money or data. “We’ve seen long-tail operations where they were going 10, 12, 18 months working in some of these organizations,” says Adam Meyers, a senior vice president for counter adversary operations at the security company CrowdStrike. Sometimes, though, North Korean operatives last just a few days— enough time to download huge amounts of company data or plant malicious software in a company’s systems before abruptly quitting. That code could alter financial data or manipulate security information. Or these seeds could lay dormant for months, even years.
“The potential risk from even one minute of access to systems is almost unlimited for an individual company,” says Declan Cummings, the head of engineering at software company Cinder. Experts say that attacks are ramping up not just in the US but also in Germany, France, Britain, Japan and other countries. They urge companies to do rigorous due diligence: speak directly to references, watch for candidates making sudden changes of address, use reputable online screening tools, and conduct a physical interview or in-person ID verification.
But none of these methods are foolproof, and AI tools are constantly weakening them. ChatGPT and the like give almost anyone the capacity to answer esoteric questions in real time with unearned confidence, and their fluency with coding threatens to make programming tests irrelevant. AI video filters and deepfakes can also add to the subterfuge.
At an onboarding call, for instance, many HR representatives now ask new employees to hold their ID up to the camera for closer inspection. “But the fraudsters have a neat trick there,” says Donal Greene, a biometrics expert at the online background check provider Certn. They take a green-colored card the exact shape and size of an identity card—a mini green screen—and, using deepfake technology, project the image of an ID onto it. “They can actually move it and show the reflection,” says Greene. “It’s very sophisticated.” North Korean agents have even been known to send look-alikes to pick up a physical ID card from an office or to take a drug test required by prospective employers.
Even security experts can be fooled. In July 2024, Knowbe4, a Florida-based company that offers security training, discovered that a new hire known as “Kyle” was actually a foreign agent. “He interviewed great,” says Brian Jack, KnowBe4’s chief information security officer. “He was on camera, his résumé was right, his background check cleared, his ID cleared verification. We didn’t have any reason to suspect this wasn’t a valid candidate.” But when his facilitator—the US-based individual giving him cover—tried to install malware on Kyle’s company computer, the security team caught on and shut him out.
Back in london, Simon Wijckmans couldn’t let go of the idea that somebody had tried to fool him. He’d just read about the Knowbe4 case, which deepened his suspicions. He conducted background checks and discovered that some of his candidates were definitely using stolen identities. And, he found, some of them were linked to known North Korean operations. So Wijckmans decided to wage a little counter exercise of his own, and he invited me to observe.
I dial in to Google Meet at 3 am Pacific time, tired and bleary. We deliberately picked this offensively early hour because it’s 6 am in Miami, where the candidate, “Harry,” claims to be.
Harry joins the call, looking pretty fresh-faced. He’s maybe in his late twenties, with short, straight, black hair. Everything about him seems deliberately nonspecific: He wears a plain black crewneck sweater and speaks into an off-brand headset. “I just woke up early today for this interview, no problem,” he says. “I know that working with UK hours is kind of a requirement, so I can get my working hours to yours, so no problem with it.”
So far, everything matches the hallmarks of a fake worker. Harry’s virtual background is one of the default options provided by Google Meet, and his connection is a touch slow. His English is good but heavily accented, even though he tells us he was born in New York and grew up in Brooklyn. Wijckmans starts with some typical interview questions, and Harry keeps glancing off to his right as he responds. He talks about various coding languages and name-drops the frameworks he’s familiar with. Wijckmans starts asking some deeper technical questions. Harry pauses. He looks confused. “Can I rejoin the meeting?” he asks. “I have a problem with my microphone.” Wijckman nods, and Harry disappears.
A couple of minutes pass, and I start to fret that we’ve scared him away, but then he pops back into the meeting. His connection isn’t much better, but his answers are clearer. Maybe he restarted his chatbot, or got a coworker to coach him. The call runs a few more minutes and we say goodbye.
Our next applicant calls himself “Nic.” On his résumé he’s got a link to a personal website, but this guy doesn’t look much like the profile photo on the site. This is his second interview with Wijckmans, and we are certain that he’s faking it: He’s one of the applicants who failed the background check after his first call, although he doesn’t know that.
Nic’s English is worse than Harry’s: When he’s asked what time it is, he tells us it’s “six and past” before correcting himself and saying “quarter to seven.” Where does he live? “I’m in Ohio for now,” he beams, like a kid who got something right in a pop quiz.
Several minutes in, though, his answers become nonsensical. Simon asks him a question about web security. “Political leaders ... government officials or the agencies responsible for border security,” Nic says. “They’re responsible for monitoring and also securing the borders, so we can employ the personnel to patrol the borders and also check the documents and enforce the immigration laws.”
I’m swapping messages with Wijckmans on the back channel we’ve set up when it dawns on us: Whatever AI bot Nic seems to be using must have misinterpreted a mention of “Border Gateway Protocol”—a system for sending traffic across the internet—with national borders, and started spewing verbiage about immigration enforcement. “What a waste of time,” Wijckmans messages me. We wrap up the conversation abruptly.
I try to put myself in the seat of a hiring manager or screener who’s under pressure. The fraudsters’ words may not have always made sense, but their test scores and résumés looked solid, and their technical-sounding guff might be enough to fool an uninformed recruiter. I suspect at least one of them could have made it to the next step in some unsuspecting company’s hiring process.
Wijckmans tells me he has a plan if he comes across another pretender. He has created a web page that looks like a standard coding assessment, which he’ll send to fake candidates. As soon as they hit the button to start the test, their browser will spawn dozens of pop-up pages that bounce around the screen, all of them featuring information on how to defect from North Korea. Then loud music plays—a rickroll, “The Star-Spangled Banner”—before the computer starts downloading random files and emits an ear-splitting beep. “Just a little payback,” he says.
Wijckman’s stunt is not going to stop the pretenders, of course. But maybe it will irritate them for a moment. Then they’ll get back to work, signing on from some hacking sweatshop in China or through a laptop farm in the US, and join the next team meeting—a quiet, camera-off chat with coworkers just like me or you.
7 notes
·
View notes
Text
Techno Magic Crash Course
Hello World! (hehe)
Ive noticed a lack of information on techno-magic and what being a tech witch might entail! Tech magic is the use of modern-day technology in our magical practices! This can be a secular practice OR someone may pair other aspects of theology into it! There is also 'Technopaganism' which is the merge of neopaganism and digital magic. Some people may worship tech and its energy or some people simply use it as a tool for ritual magic!
In this post I wanted to showcase a few ideas to get you started in the tech practice! The first section being common tools, the second is common tech practices, and the last is about how to take steps into your new tech practice and advance forward!
First: The tools To get started here are some amazing apps people might get on their phones to carry magic anywhere
The Moon is an iphone based calander with a bunch of free information about the phases of the moon and even crystals and intentions related to the phase!
Rune reading on the Google Play Store this is a divination app in relation to runes!
Citrine Circle is a great crystal data base to keep track of crystal you either have or want to get
Time Passages is a free chart reader that will read your whole astrological chart!
Labrynthos is a free tarot app that not only gives you access to free tarot, oracle, and lenormand decks, but it teaches you how to read them
Next are physical or digital items you can use in your craft, I will go in more detail in the sections to follow!
Computers, phones, tablets
Mouse
Keyboards
Applications and websites
coding platforms
Second: The Practice
This section is all about creating ideas to use for your craft! This section is all about how to integrate common witchy things into your craft! There are thousands of ways to do this so it would be impossible for me to share every idea but hopefully, these get your creative juices flowing
Cleanse using music or beats you enjoy over a speaker
Use mechanical processes in your spells (for example your cars computer could be a green light charm if you hate waiting in red lights)
Create digital grimoires on places like notation or google docs
Create altars on places like Pinterest or sandbox games
Play video games with intentions, like tycoon games for prosperity and FPS for warding
Use autotune during chants to add more power to your voice
Use screens for scrying or intuition practices
Shufflemancy is when you shuffle through a playlist and get a song as a form of divination
Use the energy of a crystal on your screen if you don't physically have one
create digital sigils and hide them around your electronics
Learn a coding language and mess around with enchanting code
Third: How to move forward
So now that you have a few recommendations how can you advance? first research, check out some of these sources for even more information
Tech Magick for Digital Witches
Other Community tech posts
Wiki on technopaganism
Cyber Spell books (Note this was written in 2002 so it is very outdated, however it is actually one of the more recent ones I see online)
Now, Research is going to be the backbone of any practice, however, tech magic doesn't have definite rules so experimentation is going to be your best friend so here are my top tips
If you learn about a new practice ask yourself how you can make it digital (like crystals and the crystals in your phone)
Look deeper into the practice, as you explore how your computer works ask yourself 'why' frequently and question how things work
look into superstitions coders and virtual friends have in relation to computers, are they rooted in anything?
I think that is all for today friends! I hope you all enjoy and if you have any questions feel free to post them in the comments!
Tip Jar
89 notes
·
View notes
Text
I find some people want to know how to find Japanese Natsuyuu's New chapters online. So I try to explain how I bought them. I live in Hong Kong, and I usually buy e-books from Renta! with Visa card.
↓ First, you need to create an account.
↓ Choose the last one.

↓Enter your Email
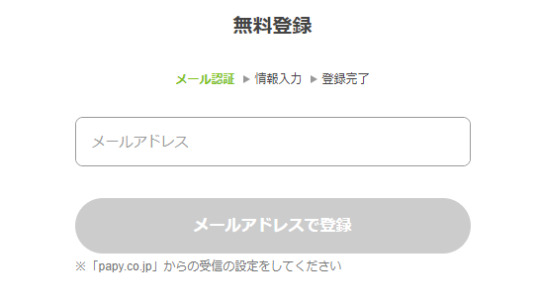
↓Then check your email, click the link

↓Enter your password, PN, sex(M/F), date of birth(YYYY/MM/DD)
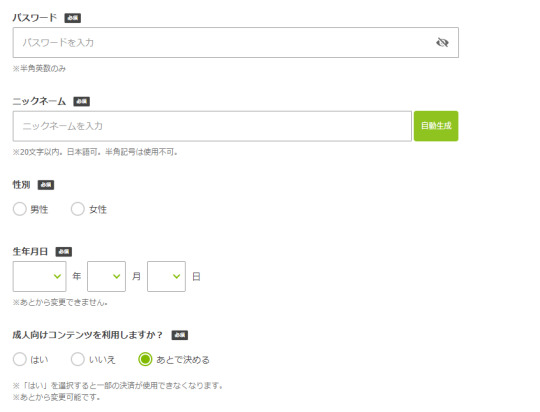

↑Pass the '規約に同意~' button to login.
↓In order to use Renta, you need to buy 'Points'

↓Choose how many points(ポイント) you want to buy. Each volume of Lala is around 450points. And each volume of Natsuyuu is 480points.
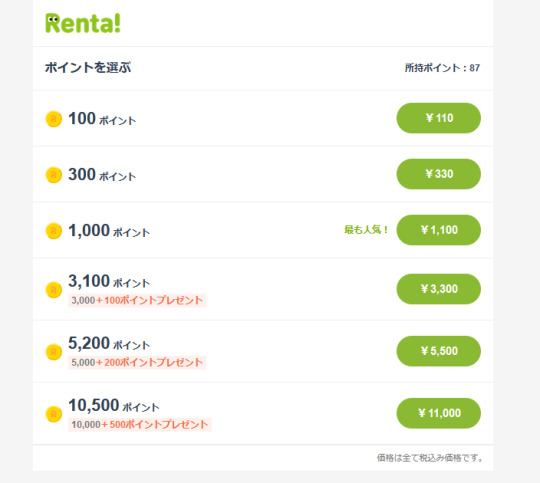
↓Enter your credit card number, name, exp date, security code and pass 購入する。
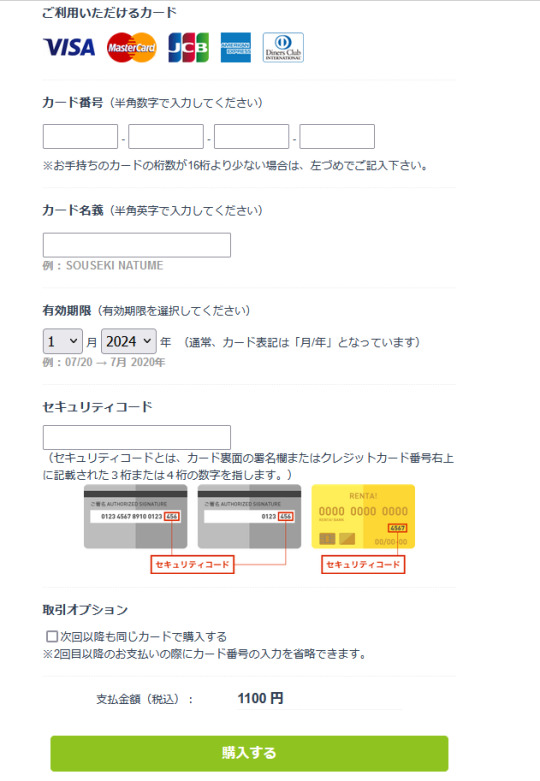
When you are all done, you can start your shopping by using your points.
Pass here if you want to buy Natsuyuu volumes. Pass here if you want to buy Lala magazine. (not LalaDX) Of course, you can also buy other books that you are interested.

↑Equal amount of points will be deducted when click the XXXポイント button. A new window will show up, or just click 読む to read them.
Important note: Natsuyuu is only serialized in odd-numbered months of LALA magazine. Most of the e-booking stores only contain the newest 6 mouths of Lala Volume. When the older volumes are expired, people who have not bought them will not be able to buy them.
But bought volume will still show up in user's library and can be read in Renta!.

If you don't like Renta!, there's a lot of Japanese e-books stores you can choose (I also like using Honto, but it's a bit complicated if you don't understand Japanese). Just google 'how to buy Japanese ebooks' and you can find a lot of tutorials. But please check whether those stores accept foreign credit cards. Also, Amazon is NOT recommended because its platform is region restricted.
32 notes
·
View notes
Text

Internet users advised to change passwords after 16bn logins exposed
Hacked credentials could give cybercriminals access to Facebook, Meta and Google accounts among others
Internet users have been told to change their passwords and upgrade their digital security after researchers claimed to have revealed the scale of sensitive information – 16bn login records – potentially available to cybercriminals.
Researchers at Cybernews, an online tech publication, said they had found 30 datasets stuffed with credentials harvested from malicious software known as “infostealers” and leaks.
The researchers said the datasets were exposed “only briefly” but amounted to 16bn login records, with an unspecified number of overlapping records – meaning it is difficult to say definitively how many accounts or people have been exposed.
Cybernews said the credentials could open access to services including Facebook, Apple and Google – although there had been no “centralised data breach” at those companies.
Bob Diachenko, the Ukrainian cybersecurity specialist behind the research, said the datasets had become temporarily available after being poorly stored on remote servers – before being removed again. Diachenko said he was able to download the files and would aim to contact individuals and companies that had been exposed.
“It will take some time of course because it is an enormous amount of data,” he said.
Diachenko said the information he had seen in infostealer logs included login URLs to Apple, Facebook and Google login pages. Apple and Facebook’s parent, Meta, have been contacted for comment.
A Google spokesperson said the data reported by Cybernews did not stem from a Google data breach – and recommended people use tools like Google’s password manager to protect their accounts.
Internet users are also able to check if their email has been compromised in a data breach by using the website haveibeenpwned.com. Cybernews said the information seen in the datasets followed a “clear structure: URL, followed by login details and a password”.
Diachenko said the data appeared to be “85% infostealers” and about 15% from historical data breaches such as a leak suffered by LinkedIn.
Experts said the research underlined the need to update passwords regularly and adopt tough security measures such as multifactor authentication – or combining a password with another form of verification such as a code texted from a phone. Other recommended measures include passkeys, a password-free method championed by Google and Facebook’s owner, Meta.
“While you’d be right to be startled at the huge volume of data exposed in this leak it’s important to note that there is no new threat here: this data will have already likely have been in circulation,” said Peter Mackenzie, the director of incident response and readiness at the cybersecurity firm Sophos.
Mackenzie said the research underlined the scale of data that can be accessed by online criminals.
“What we are understanding is the depth of information available to cybercriminals.” He added: “It is an important reminder to everyone to take proactive steps to update passwords, use a password manager and employ multifactor authentication to avoid credential issues in the future.”
Toby Lewis, the global head of threat analysis at the cybersecurity firm Darktrace, said the data flagged in the research is hard to verify but infostealers – the malware reportedly behind the data theft – are “very much real and in use by bad actors”.
He said: “They don’t access a user’s account but instead scrape information from their browser cookies and metadata. If you’re following good practice of using password managers, turning on two-factor authentication and checking suspicious logins, this isn’t something you should be greatly worried about.”
Cybernews said none of the datasets have been reported previously barring one revealed in May with 184m records. It described the datasets as a “blueprint for mass exploitation” including “account takeover, identity theft, and highly targeted phishing”.
The researchers added: “The only silver lining here is that all of the datasets were exposed only briefly: long enough for researchers to uncover them, but not long enough to find who was controlling vast amounts of data.”
Alan Woodward, a professor of cybersecurity at Surrey University, said the news was a reminder to carry out “password spring cleaning”. He added: “The fact that everything seems to be breached eventually is why there is such a big push for zero trust security measures.”
Daily inspiration. Discover more photos at Just for Books…?
5 notes
·
View notes