#introduction to cloud computing
Text
Top 100 Cloud Computing Most Asked Questions in 2023
Cloud Computing Multiple Choice Questions
Here are top 100 Most Asked in exam MCQ:
1.Full form of KMS I Microsoft KMS is _____________
Key Management Services.
Key Management Sences.
Key Management Store.
Key Managed Store.
2.What does a full template include that a basic template does not ________
Disk Layout.
MAC Address.
Installation files.
Settings.
3. Virtualization provides optimizations techniques to dever the application______
Desktop.
Application.
Server.
Network.
4.CEN NetScaler SD-WAN is a set of appliances that optimum_______ performance.
LAN
MAN
WAN
INTERNET.
5.Which of the following storage supports fast cloning of virtual machine?
FC
NFC
SAS
ISCSI (Read More)
#cloud computing#aws certified cloud practitioner exam questions 2023#aws cloud practitioner exam question answers 2023#cloud computing interview questions and answers#aws cloud practitioner exam questions#aws cloud practitioner dumps 2023#aws cloud practitioner exam questions 2022#aws cloud practitioner questions dumps#cloud computing interview questions for freshers#top 10 cloud computing certifications in 2022#cloud computing certifications in 2022#cloud computing in telugu#introduction to cloud computing#cloud computing explained#ccc questions in hindi#cloud computing basics#cloud computing tutorial#crazy questions in science#complete cloud computing tutorial#internet questions for ccc exam#top 10 highest paying jobs in 2023#top 10 certifications in the world#investing in your 20s#internet questions#how to invest in stocks#internet questions and answers#cloud training
4 notes
·
View notes
Video
youtube
Top Cloud Hosting Companies NEED TALENT! |
We discuss a program that has empowered individuals from various backgrounds to transition into the tech industry, specifically cloud computing who are now happily making six-figure salaries without the burden or expense of a four-year college degree. For more visit here
#youtube#cloud computing#cloud#aws#amazonwebservices#oracle#Learning cloud computing#Cloud Hosting Talent#Top CloudHosting Companies#career in tech#jobs in tech#technology jobs#cloud computing jobs#aws cloud#aws for beginners#what is cloud computing#introduction to cloud computing#cloud technology#aws basics#cloud computing explained#aws course#aws services#aws certification#what is cloud computing for beginners#learn aws#software engineer#google cloud#Top
1 note
·
View note
Text
The Power of Cloud Computing in Data Science: How It Enables Faster, More Efficient Analysis
In this video, we're going to explore the power of cloud computing in data science. Cloud computing is a technology that enables users to access resources online, without having to install or manage software on their own.
Clouds enable data scientists to access large data sets and sophisticated machine learning algorithms without directly accessing the data. This allows us to run our analyses faster and more efficiently, leading to better insights and decision-making. So make sure to check out this video to learn more about the power of cloud computing in data science!
To read more about cloud computing in data science, check out this blog.
#cloud computing#cloud#what is cloud computing#cloud computing tutorial for beginners#introduction to cloud computing#what is cloud computing for beginners#what is cloud computing and how it works#cloud computing for beginners#why cloud computing#cloud computing in data science#what is cloud computing technology#learn cloud computing for data science#cloud computing for data science#role of cloud computing in data science#importance of cloud computing in data science
1 note
·
View note
Text
Elevating Employability: Short-Term Course Suggestions for College Students
Empower your future with our latest blog on short-term courses for college students! 🚀 Enhance your employability and unlock new opportunities. Dive in to discover courses that fit your passion and career goals. #EmpowermentThroughEducation #SkillUp
“विद्या ददाति विनयं, विनयाद् याति पात्रताम्।”
“Education bestows humility, humility leads to worthiness.”
In a world that’s constantly evolving, the importance of education—especially for students from lesser-known colleges in India—cannot be overstated. Education not only paves the way for personal growth but also significantly boosts employability in today’s competitive job market. Here are…

View On WordPress
#Career Advancement#College Students#Data Analytics Introduction#Digital Marketing Training#Education Empowerment#Employability Enhancement#Financial Literacy#Foreign Language Learning#Graphic Design Basics#Lifelong Learning#Payroll Management Digital Transformation HR Technology Compliance and Regulation Financial Management Cloud Computing Employee Empowerment#Professional Growth#Short-term Courses#Skill Development#Soft Skills Improvement#Web Development Skills
0 notes
Text
Starting Your Cloud Journey: An Introduction to the AWS Cloud Bootcamp
The cloud is revolutionizing the way businesses operate, and it's becoming increasingly important for IT professionals to have a strong understanding of cloud computing. One of the best ways to get started is with an AWS Cloud Bootcamp.
Amazon Web Services (AWS) is the largest cloud provider in the world, and its cloud bootcamp is designed to provide a comprehensive introduction to the world of cloud computing. The bootcamp covers everything from basic cloud concepts to advanced topics, and provides hands-on exercises to help you apply what you've learned.
Whether you're a beginner or an experienced IT professional, the AWS Cloud Bootcamp will help you develop the skills you need to start your cloud journey. The bootcamp covers a range of topics, including cloud architecture, security, and cost optimization, so you can be confident that you're getting a well-rounded education.
In addition to the hands-on exercises, the AWS Cloud Bootcamp also provides access to a community of experts and peers who can help you continue your learning journey. You'll have the opportunity to network with others in the industry, learn from their experiences, and ask questions.
In conclusion, the AWS Cloud Bootcamp is a great way to get started with cloud computing. With its comprehensive curriculum and hands-on approach, you'll have the skills and confidence you need to succeed in the cloud. So why wait? Sign up for the AWS Cloud Bootcamp today and start your cloud journey!
#AWS#cloud bootcamp#cloud computing#Amazon Web Services#IT professionals#introduction#basic concepts#advanced topics#hands-on exercises#cloud architecture#security#cost optimization#community#experts#peers#networking#industry#education
1 note
·
View note
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference.
Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
36 notes
·
View notes
Text
Did you know, you can take a Harvard computer science class...for free?
CS50x is a free online introduction to computer science course, featuring recorded lectures of an actual Harvard class, along with all the assignments, access to a cloud-based development environment, and supplemental material to help you. This is all completely free, and all at your own pace.
Now, the only catch is if you want a "verified certificate" of your completion of the course, it will cost about $150. You will still receive a digital certificate, but the verified certificate has an extra layer of authenticity, if you plan on using it professionally. Whether that's necessary, your mileage may vary. But all in all, still a relatively cheap price, and you can upgrade at any time.
I can't think of any resource for learning computer science and programming better than this. Even if you struggle with the concepts, there are many other people and resources around the internet to help you with this class specifically. If you've never written a line of code, or how computers work is a complete mystery to you, this class is still for you. Seriously, give it a try.
318 notes
·
View notes
Text
Here we go again : Matt Murdock x reader x Dick Grayson


A/N: I think I got myself into an unhealthy addiction of writing stories based on the songs stuck in my head, but well, it fits, so why not.
A/N 2 : This is just something to make you grasp the idea behind the story. The next chapters are going to go back in time to properly deal with the timeline and events.
inspired by : That's hilarious by Charlie Puth.
PROLOGUE
That's hilarious
Hahahaha.....
haha
Yeah, if you haven't already guessed I'm laughing because at this point nothing seems real anymore and if I wasn't laughing at the irony I would probably start crying, screaming and then jump our of the window.
Let me give you a quick introduction into my life, so you could understand me better.
Hi,
my name is Y/N and I'm a citizen developer. Which means I pretty much do everything that has to do with IT, Artificial Inteligence, programming, computers and programming. I loved my job to the point where I was spending hours and hours in front of the screen to be the very best. And truly, finally I got to the top. At the age of 21 I was a most-known in my profession.
And that got me some attention.
Did I mention I was born and living in Gotham?
So, perhaps you guessed who was the guy that gave me my first job?
No?
Well, it was Bruce Wayne. Yes, Wayne as in Wayne Enterprises.
Oh, god, I was on cloud nine being able to put my hands on all that technology, give my ideas and finally having someone to listen and apreciate them. I upgraded it, gave a bit of personal touch to the systems and god, it was amazing., I felt like I was where I belonged.
Bruce, however reserved and distant he was soon started to treat me like his own daughter. I mean, what else can you expect from a relationship between a CEO who spend most of his time with the youngest IT who also happened to be a half-orphan?
So, soon, he let me into the Wayne Manor, where I met his adopted son, Dick. Quite different than his parential figure, but pretty much the same with distant and pushing away. I didn't force him. It took us half a year to become some sort of friends and another half a year to fall truly, madly, deeply in love. No irony here. We spend a lot of time together. Or at least as much as our busy schedules allowed us to. Dick was a detective with crazy work hours, both night and day so when I get the chance I worked from the Manor, even when Bruce was not content with it.
Now that I think about it, i wonder how love-blinded I was.
That's when the story starts to go downhill.
When I was 23, Wayne Enterprises' tech department, with me leading it, introduced some new prototype. The whole project was on the highest security level, full NDA and confidentiality, so from some point the only people involved in the details were me and Bruce. I was literally sunsine and rainbows I get to be involved, hell! be the head of the assignment.
Until I got myself in trouble walking home from work at late night.
Remember, it was Gotham City and I was overwhelmed with our success.
So, due to my absent-mindedness some assaulters came right at me, grabbing both of my arms and dragging me into the dark alley. Of course I was figthing back, screaming and squirming, but what can one girl do in confrontation with 3 pretty beefy men?
Yes, three points for the right answer. NOTHING.
I was pretty much saying goodbye to my life (or at least my sexual health and good memories in that aspect - thank you, Dick Grayson for giving me them) when Gotham's heroes - Batman and Robin decided to show up, blowing everything and beating the assaulters to shit. Maybe they exaggareted a bit, after all those men were not criminals, and there was no need to knock them unconscious and that made me wonder. Still a bit overwhelmed I looked around and then I spotted Batman's new gear. Based on the technology I created.
So there were two, maybe three options:
Batman stole the technology from Wayne, and therefore he was not a hero everyone believed him to
Batman got the techonology from Wayne and therefore Bruce knew Batman's identity (Bruce would never let anyone, even the hero got it without checking all the details)
Bruce was Batman.......
"Bruce......?"
"Y/N."
"What is going on here?" I took a step back and bumped into wall
"Let me explain it to you....."
"Y/N!" another voice came from my right and before I realised what was happening, another caped vigilante was holding me close to his chest, his warm embrace being oddly famliiar. "Are you alright?" Robin's hands started caressing my back, his breaht ticking my face.
Holy fuck!
If Bruce was Batman than .....
"Dick?" my eyes went wide. Stupid, stupid girl! You should have known!
"Are you all right?" he asked again, a mix of desperation and remorse in his voice.
"Yes. I mean, no. I mean, I don't know. What is this? some sort of Surprise Sur Price?"
"Let us explain...." Dick took a quick glance at Batman Bruce who nodded
"Not here. It's not safe."
NOT SAFE!?
"Y/N." Dick took my hand squizing it gently, but lovingly "come on, baby, let's get you out of here."
"Um, well, okey...."
They got me to the Manor and then, since the secret was out and in their own words, they trusted me, I got a quick tour around the batcave. Yeah, they trusted me so much they kept their second life in secret for two fucking years! How is that trust?! I felt betrayed, played with, used, you name it. All that anger made me cry and clench my fist at the same time, my face going red and my heart at the edge of literally breaking.
"Talk to her." apparently that was too much for Bruce, since he decided to let my boyfriend deal with the damage. "You're off the patrol tonigh. Just make sure she'll be fine."
Oh, quite a conversation it was. However, at first not many words were used..... Anger, or rather fury, found another way out......But, when we both calmed down enough to use our mouths to actually echange full sentences it was all painfully clear.
The problem about heroes comes down to the fact that when being torn between their mission and the person they love ,they always choose the duty. And Dick did exactly that when he decided to sweet talk all my worries and cover up the truth for two whole years. That was sad. But, trying to be rational, I didn't scream or blame him. To some point I understood his motives, I mean, as a gotham citizen. As his girlfiriend I could not. I stayed in the manor until he felt asleep in his serene belief we were fine now.
We weren't.
I left Gotham that nigh, leaving him a letter explaing why I had to do this and kindly asking him not to look for me. The thought of the heartbreak he had to go through must have been soul-piercing. At least that's how it was for me when I found myself in Hell's kitchen trying to put my life together and move on.
I found a new job, but it was not the same without him.
And then Matt Murdock came into my life. He was such a nice guy, With an opinion amongst girls, as his best friend Foggy told me. Well, I was not going to fall for him. I had my walls high. Matt and Foggy were both lawyers and a bit of tech was kind of useful in this profession so soon we were working together. As friends. But clearly it was not enough for Matt. We were working late in his aparment, foggy has already left and I was picking my stuff to go home as well, already halfway to the door when Murdock yanked me back by my hand and kissed me with the most knee-buckling, hot, passionate kiss. You know, the one when you just reciprocate in an instant, no need to process what the hell is going on, while the other person's hand sneak around you pulling you closer. At first, i just let him caress my body, but quickly fall on the concrete.
"Stay with me...." he whispered against my lips
"Matt...." I pushed him away and he backed out immidiately
"I'm sorry Y/N. I didn't mean to push you, but I just... I have so many feeligns for you."
"No, I'm sorry. I'm just..... not ready. Yet."
"Yet?" damn lawyers
"Yet" I smiled lightly to defuse the tension
"Well then, I'm not giving up on you".
***
You know the saying "the history repeats itself?" Well it really does. I learned that in a painfull way, when a month later it turned out Matt Murdock was the devil of hell's kitchen. DAREDEVIL for fuck's sake. What was wrong with me and why the hell was I attracting vigilantes from the whole damn country?!
At least I didn't have to get myself in trouble to get to know his secret identity.
Oh no.
This was much worse when he stumbled into my apartment at 3 a.m. waking me up, in not so pleasant way, al bloody and on the verge of life. Yeah, we.... well, we had an argument. But somehow, he convinced me to stay. Something Dick couldn't do in the past. He never asked me to stay.
So I give in to the hope that this time it would be diffent. And I stayed, ready to fight for whatever was blooming between us.
And I was happy-ish to work through it with him.
And I was slowly moving on.
Until one evening, half a year after I left Gotham the past came knocking at my door.
Literally.
I was at my apartment, working and cuddling with Matt when the noice from outside made me get up and open.
"Y/N...... I found you...."
Dick fucking Grayson was at my door.
"Y/N...." he whispered tenderly "I need you back. I want you back with me...."
"Y/N? who is that?" in a blink of an eye Matt was by my side and at this point I was just turning my gaze from one guy to another in shock.
"Who the fuck are you?" Dick hissed
"Well I could ask you the same question" Matt retorted coldly
"I'm her boyfriend" ok, now it was Robin talking
"Funny thing, because that is who I am." hello, Daredevil, nice to see you woke up as well. I guess it was automatic - when Dick went into vigilante mode, Matt responded with exact the same.
"Guys....." I tried to stop them, but they did not let me.
"So you must be the ex?" Matt smirked
"You know about me? Does she moan my name when you two....."
"Ok! Ok! That is enough!" ultimately I got their attention, pretty sure I was red as an apple due to Dick's words.
Now.
I was the only thing standing between two vigilantes in their full-on fighting mode, ready to kill each other .
Oh, boy......
@somest1
@pinksirensong
@everything2134
#matt murdock x reader#matt murdock#matt murdock imagine#matt murdock x y/n#matt murdock x you#matthew murdock#daredevil#daredevil x reader#daredevil x y/n#daredevil netflix#daredevil x you#mcu imagine#mcu#marvel imagines#marvel#dc#dc imagine#dick grayson x reader#dick grayson imagine#nightwing x reader#nightwing x oc#dick grayson x you#nightwing x you#dick grayson#nightwing#dc titans#dc titans x reader#dick grayson fanfiction#dick grayson x y/n#nightwing x y/n
126 notes
·
View notes
Text

- Just A Introduction -
. - * I Am Cloud / Snowy * - .
. - I am a 6teen year old who loves writing fanfics on AO3 who’s an ex-wattpad author. I like to draw and most likely just reblog things but I will also post my art, plus two games I’m working on. I’m strictly profiction/ship who enjoys com/darkship. I’m also pro-choice, pro-para(anti-contact though obvs) and a socialist. I won’t get really political on my blogs but I will be going on fandom discourse though - .
. - * ~ I like: Anime, Vocaloid / Utauloid / Fanloid, Video Games, Art, Writing, Manga, Marvel, Computering, Omori, UnderTale / Deltarune, Space, Jellyfish, Genshin Impact, Honkai Star Rail, Reverse: 1999, whatinHELLisbad and a few more things. ~ * - .
- . * Some Ship Dynamics I Like: BroCon, Incest, Twincest, Age Gap, Dad / Son and a few more * . -
. . - Pronouns: Any Expect She/Her * Mainly Uses He/They/Cyber - . .
- ~ * Other: LibraMasc / TransMan and CupiAroAce, Uranic * ~ -
. * I don’t have a DNI or anything but if you’re a Zionist, Racist, Homo/Trans/Islamophobic, harass people over fiction and stuff like that, don’t go on my blog ‘cause I support Palestine and I don’t condone bigotry and/or hateful comments, but I do also block freely too * .
Fanfiction Requests — CLOSED (for now)
My Very Epic AO3 Account
(SIDE BLOG: @hauntedglobe )
(SIDE BLOG FOR POLITICAL VIEWS AND REAL LIFE ISSUES: @socialist-proshipper )
Extra: I will be posting my dark/Comships on here, and just want to let you know that I do NOT condone anything in real life. I also want to mention that I am autistic, have dyslexia and dyscalculia, tone tags are useful but y’all don’t have to use it all the time.
#vocaloid#utualoid#proship#proship pls interact#comship#darkship#pro fiction#anime#proshippers are welcome#i am a proshipper#cybercore#jellyfish#space
10 notes
·
View notes
Text
Sugarcoat
A/N: I wanted to write something in the spirit of back-to-school season since I will be heading back next week. :( If you've already started or if you're starting soon, best of luck with your semester!
TW: Reader is gossiped about
Pairing: Dami x Reader (platonic to implied romantic)
Summary: Your life in college has been nothing but empty rumors and failed promises. The introduction of a new seat mate changes how you view the people around you, and how they view you in return.

Sugarcoat, I cast off
Whatever you say about me
Being reserved made you mysterious, and mystery caused rumors to cloud around your everyday movement and activities. Your dating life tended to be the worst of them all as classmates and co-workers alike would often pin you to be a player or completely uninterested in everything. You simply wished to sit next to someone and not see them lean over to talk to someone else.
So, you kept in your shell and kept to yourself. People didn’t need to know anything more about you then you would tell-
“Can I sit here?”
A warm, deep voice snaps you out of your thoughts.
“Sure.”
You gently observe the brown-haired woman who sits next to you. Intro to Philosophy, a social studies credit for your major, would prove to be more interesting than you thought. You notice that she pulls out a laptop that is well-endowed with stickers on the back.
“I like the stickers on your laptop.” You quietly say as your professor enters the classroom.
“Thanks. They’re just from different shows and musicians that I like.” She pauses for a moment as you continue to observe the different logos and characters on them. “Would you be interested in a tour?”
A light smile appears on your face - a rarity in class, especially by another person.
“I’d like that.”
Just move, as I want
Dancing for myself
“You take dance classes?” You ask you spot her daily schedule as the background on the computer. “Sorry, that was invasive and weird-“
“It’s just once a week with a close group of friends.” Dami explains before opening a browser to prepare materials for today’s class. “What about you? Any remarkable interests?”
“Nothing that you haven’t heard from others before, I’m sure-“
“I’d much rather make my observations in-person rather than by rumors.”
“I-“ You pause as a slight bout of embarrassment crosses your features. “I think that’s the first time someone’s spoken to me instead of about me.”
“It’s a shame, really,” Dami glances at you before the professor starts class, “they’re missing out on a great person.”
Another first happens within two weeks - someone manages to make your heartbeat quicken.
Don’t sugarcoat me, baby
Complex is over-rated
You like to simplify the world around you - it makes your life so much simpler. The grass is green, the sky is blue, and you most definitely have feelings for the mysterious yet kind girl who goes out of her way to always sit next to you or save you a seat whenever you have class.
You think that she’s caught on to your feelings as her hand lingers on yours when she’s looking at your computer or how her eyes catch yours when the professor goes off-topic every class period.
“You’re strange,” You comment as your professor talks about their dog again, “but I don’t mind.”
“Me?” Dami chuckles softly. “I think that’s the first time someone’s said that to my face.”
A light smile plays on your features as you notice your classmates aren’t paying you any mind - it’s so relaxing to know that you’re not under the microscope of your peers.
“I like that you’re strange, you’re like me,” You pause to still your beating heart, “but I was wondering if you’d like to get lunch sometime?”
“With you?” A warm, inviting smile stays on her face. “Absolutely.”
The transparent moonlight
Pours out, more freely
#fanfic#x reader#kpop#girl group#dami dreamcatcher#dreamcatcher imagines#dreamcatcher scenarios#dreamcatcher x reader#dami#dami x reader#dami imagines#dami drabbles#dreamcatcher drabbles#Kpop au#Spotify
34 notes
·
View notes
Text
Which Technology Is Making Quantum Computing Easier To Access And Adopt?
What type of Technology is making quantum computing easier to access and adopt?
There are several technologies and platforms that are making quantum computing more accessible and easier to adopt:
1.Cloud-based quantum computing platforms: Several companies, including IBM, Google, Amazon, and Microsoft, offer cloud-based quantum computing platforms that allow users to run quantum algorithms and experiments remotely using web interfaces or APIs. Read more
#quantum computing#quantum computer#quantum#quantum computing explained#future of quantum computing#technology#what is quantum computing#quantum computing programming#what is cloud computing and how it works#photonic quantum computing#cambridge quantum computing#azure quantum computing#quantum computing hardware#quantum technology#quantum computers#quantum computers 2022#national institute of standards and technology#introduction to cloud computing
0 notes
Text

✨Spotlight on Localhost HQ✨
Today we're here to tell you all about Localhost HQ, the first setting for the adventures of our protagonist (and fujoshi extraordinaire) Boba-tan.
Follow us under the cut to learn more about the #FujoGuide world and the amazing people that made it happen! And don't forget to back us on Kickstarter (and share this with your friends) so we can make this world a reality!
🏰 Localhost HQ 🏰
So, what is Localhost HQ? Well, we don't have—nor want!—all the details. The vaguer it is, the easier it adapts to any fanfic scenario. On the technical side, computers in a network use "localhost" to refer to themselves, for example to fetch a website they themselves host!
In the #FujoGuide world, Localhost HQ houses all programs that run on a user's own machine as part of the development workflow. Most importantly, the Terminal (a.k.a. Shell), but also programs like Git. In our version, Boba-tan has her very own (relatable) room within it.

🏰 Localhost Character 1: Boba-tan 🏰
Needing no introduction (ok, some introduction), Boba-tan is the author and protagonist of our zine. She was originally designed to serve as @bobaboard's own mascot by @essential-randomness, and brought to life by @ymske.

In our Kickstarter, you can see her all over the place, drawn by many different artists (some of which don't like the spotlight). For our character roster and avatar, she's been brought to life by @ikam177! Witness her in her full glory!

Want to know more about her? Well, she's the blankest slate of them all! Boba-tan is the quintessential fujoshi (or fujin, if you want), meant to embody the best quirks of transformative fandom folks: openness, enthusiasm, creativity, and heaps and heaps of thirst!
🏰 Localhost Character 2: Terminal 🏰
Is it Terminal or is it Shell? You too can now be part of one of programming's most pointless (and thus heated) debates.
Regardless of how you choose to refer to him, we all know who he actually is: the sexy live-in maid-pa of Localhost HQ.
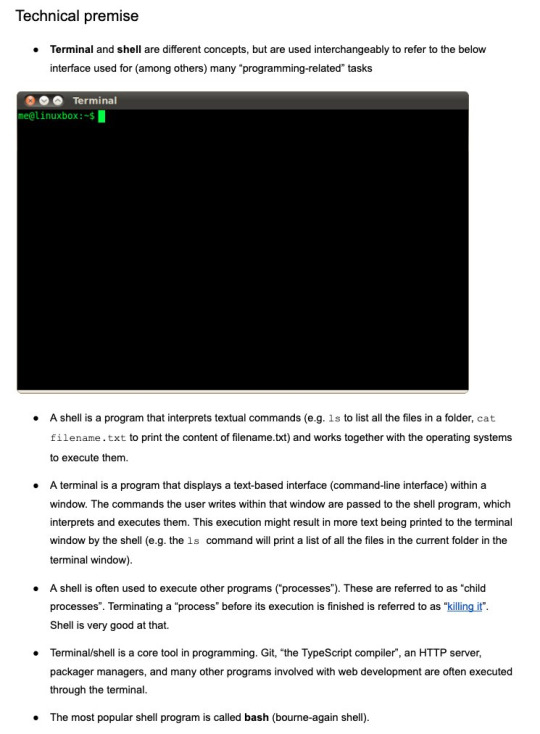
Terminal is a powerful tool in the programming world, used to run other programs and orchestrate complex interactions between them. He also runs the show in the #FujoGuide world, and is able to quickly summon any local program, and to interact directly with the operating system.

(comic by @tempural)
Is there any limit to Terminal's powers? We don't know, actually, and we don’t want to know! Please play around with hi— I mean, it!
If you love his look (a powerful mix of Danny Trejo and Revolver Ocelot), you can thank—and follow—@mappapapa's incredible work! And if you've wondered what's on his apron...well, that's cowsay for you!


(Shhh don’t tell anyone about this still-unused version, with a terminal-looking eyepatch on his eye)
🏰Localhost Character 3: Git🏰
We've already spent a lot of time on our favorite catboy, but that's no reason to ignore him—not that he'd ever let us!
If you haven't yet, see him in action and learn all about him in our demo (link in the Kickstarter).
This time, the hard work of turning our technical and trope guidance into a bona-fide hottie comes from @brokemycrown—the master of sexiness who also helped us with the overall art direction!
(If you're wondering what the lines on his hoodie are, those are “git branches”.)

🏰 Localhost Character 4: GitHub 🏰
☁️ Cloud character 1: GitHub ☁️
Unlike Git, GitHub is not a program that runs in a "local environment"—that is, a developer's own computer. Instead, GitHub is a cloud-based service where programmers can upload their own "Git repositories" to share their code with other developers.
In the #FujoGuide world, characters like Git live in ~the cloud~, a network of data spawning around the world and a place we want to carefully avoid showing. In part, to keep an aura of mystery, and in part because mysterious places not well-defined in canon are fujin catnip.
So why is GitHub at Localhost HQ? Because Git is there, of course! The two share a powerful psychic connection. While Git hasn't yet accepted that they're meant to become one, that is not for lack of trying. Much to Terminal's chagrin, GitHub keeps teleporting to HQ, uninvited.
Once again, the amazing artist behind our favorite tentacled catboy is @brokemycrown. We'll probably keep shouting them out over and over again in these spotlights, so just go right ahead and follow them now.


(I'm sure you can appreciate the subtle character design cues here.)
...and that is all for the Localhost HQ spotlight! If you like the amazing work of our team, you can hire our artists and writers (and help us launch this project) by backing our Git Art/Fic tiers! You can also help us by reblogging this post and sharing our kickstarter link with friends, family, colleagues and Discord servers.
58 notes
·
View notes
Text

The Comprehensive Guide to Web Development, Data Management, and More
Introduction
Everything today is technology driven in this digital world. There's a lot happening behind the scenes when you use your favorite apps, go to websites, and do other things with all of those zeroes and ones — or binary data. In this blog, I will be explaining what all these terminologies really means and other basics of web development, data management etc. We will be discussing them in the simplest way so that this becomes easy to understand for beginners or people who are even remotely interested about technology. JOIN US
What is Web Development?
Web development refers to the work and process of developing a website or web application that can run in a web browser. From laying out individual web page designs before we ever start coding, to how the layout will be implemented through HTML/CSS. There are two major fields of web development — front-end and back-end.
Front-End Development
Front-end development, also known as client-side development, is the part of web development that deals with what users see and interact with on their screens. It involves using languages like HTML, CSS, and JavaScript to create the visual elements of a website, such as buttons, forms, and images. JOIN US
HTML (HyperText Markup Language):
HTML is the foundation of all website, it helps one to organize their content on web platform. It provides the default style to basic elements such as headings, paragraphs and links.
CSS (Cascading Style Sheets):
styles and formats HTML elements. It makes an attractive and user-friendly look of webpage as it controls the colors, fonts, layout.
JavaScript :
A language for adding interactivity to a website Users interact with items, like clicking a button to send in a form or viewing images within the slideshow. JOIN US
Back-End Development
The difference while front-end development is all about what the user sees, back end involves everything that happens behind. The back-end consists of a server, database and application logic that runs on the web.
Server:
A server is a computer that holds website files and provides them to the user browser when they request it. Server-Side: These are populated by back-end developers who build and maintain servers using languages like Python, PHP or Ruby.
Database:
The place where a website keeps its data, from user details to content and settings The database is maintained with services like MySQL, PostgreSQL, or MongoDB. JOIN US
Application Logic —
the code that links front-end and back-end It takes user input, gets data from the database and returns right informations to front-end area.

Why Proper Data Management is Absolutely Critical
Data management — Besides web development this is the most important a part of our Digital World. What Is Data Management? It includes practices, policies and procedures that are used to collect store secure data in controlled way.
Data Storage –
data after being collected needs to be stored securely such data can be stored in relational databases or cloud storage solutions. The most important aspect here is that the data should never be accessed by an unauthorized source or breached. JOIN US
Data processing:
Right from storing the data, with Big Data you further move on to process it in order to make sense out of hordes of raw information. This includes cleansing the data (removing errors or redundancies), finding patterns among it, and producing ideas that could be useful for decision-making.
Data Security:
Another important part of data management is the security of it. It refers to defending data against unauthorized access, breaches or other potential vulnerabilities. You can do this with some basic security methods, mostly encryption and access controls as well as regular auditing of your systems.
Other Critical Tech Landmarks
There are a lot of disciplines in the tech world that go beyond web development and data management. Here are a few of them:
Cloud Computing
Leading by example, AWS had established cloud computing as the on-demand delivery of IT resources and applications via web services/Internet over a decade considering all layers to make it easy from servers up to top most layer. This will enable organizations to consume technology resources in the form of pay-as-you-go model without having to purchase, own and feed that infrastructure. JOIN US
Cloud Computing Advantages:
Main advantages are cost savings, scalability, flexibility and disaster recovery. Resources can be scaled based on usage, which means companies only pay for what they are using and have the data backed up in case of an emergency.
Examples of Cloud Services:
Few popular cloud services are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These provide a plethora of services that helps to Develop and Manage App, Store Data etc.
Cybersecurity
As the world continues to rely more heavily on digital technologies, cybersecurity has never been a bigger issue. Protecting computer systems, networks and data from cyber attacks is called Cyber security.
Phishing attacks, Malware, Ransomware and Data breaches:
This is common cybersecurity threats. These threats can bear substantial ramifications, from financial damages to reputation harm for any corporation.
Cybersecurity Best Practices:
In order to safeguard against cybersecurity threats, it is necessary to follow best-practices including using strong passwords and two-factor authorization, updating software as required, training employees on security risks.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) represent the fastest-growing fields of creating systems that learn from data, identifying patterns in them. These are applied to several use-cases like self driving cars, personalization in Netflix.
AI vs ML —
AI is the broader concept of machines being able to carry out tasks in a way we would consider “smart”. Machine learning is a type of Artificial Intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. JOIN US
Applications of Artificial Intelligence and Machine Learning: some common applications include Image recognition, Speech to text, Natural language processing, Predictive analytics Robotics.
Web Development meets Data Management etc.
We need so many things like web development, data management and cloud computing plus cybersecurity etc.. but some of them are most important aspects i.e. AI/ML yet more fascinating is where these fields converge or play off each other.
Web Development and Data Management
Web Development and Data Management goes hand in hand. The large number of websites and web-based applications in the world generate enormous amounts of data — from user interactions, to transaction records. Being able to manage this data is key in providing a fantastic user experience and enabling you to make decisions based on the right kind of information.
E.g. E-commerce Website, products data need to be saved on server also customers data should save in a database loosely coupled with orders and payments. This data is necessary for customization of the shopping experience as well as inventory management and fraud prevention.
Cloud Computing and Web Development
The development of the web has been revolutionized by cloud computing which gives developers a way to allocate, deploy and scale applications more or less without service friction. Developers now can host applications and data in cloud services instead of investing for physical servers.
E.g. A start-up company can use cloud services to roll out the web application globally in order for all users worldwide could browse it without waiting due unavailability of geolocation prohibited access.
The Future of Cybersecurity and Data Management
Which makes Cybersecurity a very important part of the Data management. The more data collected and stored by an organization, the greater a target it becomes for cyber threats. It is important to secure this data using robust cybersecurity measures, so that sensitive information remains intact and customer trust does not weaken. JOIN US
Ex: A healthcare provider would have to protect patient data in order to be compliant with regulations such as HIPAA (Health Insurance Portability and Accountability Act) that is also responsible for ensuring a degree of confidentiality between a provider and their patients.
Conclusion
Well, in a nutshell web-developer or Data manager etc are some of the integral parts for digital world.
As a Business Owner, Tech Enthusiast or even if you are just planning to make your Career in tech — it is important that you understand these. With the progress of technology never slowing down, these intersections are perhaps only going to come together more strongly and develop into cornerstones that define how we live in a digital world tomorrow.
With the fundamental knowledge of web development, data management, automation and ML you will manage to catch up with digital movements. Whether you have a site to build, ideas data to manage or simply interested in what’s hot these days, skills and knowledge around the above will stand good for changing tech world. JOIN US
#Technology#Web Development#Front-End Development#Back-End Development#HTML#CSS#JavaScript#Data Management#Data Security#Cloud Computing#AWS (Amazon Web Services)#Cybersecurity#Artificial Intelligence (AI)#Machine Learning (ML)#Digital World#Tech Trends#IT Basics#Beginners Guide#Web Development Basics#Tech Enthusiast#Tech Career#america
4 notes
·
View notes
Text
How to Become a Cloud Computing Engineer
Introduction:
Cloud computing has become a cornerstone of modern IT infrastructure, making the role of a Cloud Computing Engineer highly in demand. If you're looking to enter this field, here's a roadmap to help you get started:
Build a Strong Foundation in IT
A solid understanding of computer networks, operating systems, and basic programming is essential. Consider getting a degree in Computer Science or Information Technology. Alternatively, Jetking offer you to make your career in Cloud computing Courses and gain the technical knowledge needed.
Learn Cloud Platforms
Familiarize yourself with popular cloud service providers such as AWS (Amazon Web Services), Microsoft Azure, and Google Cloud. Many platforms offer certification courses, like AWS Certified Solutions Architect, which will help validate your skills.
Gain Hands-On Experience
Practical experience is critical. Set up your own cloud projects, manage databases, configure servers, and practice deploying applications. This will give you the real-world experience that employers seek.
Master Programming Languages
Learn programming languages commonly used in cloud environments, such as Python, Java, or Ruby. Scripting helps automate tasks, making your work as a cloud engineer more efficient.
Understand Security in the Cloud
Security is paramount in cloud computing. Gain knowledge of cloud security best practices, such as encryption, data protection, and compliance standards to ensure safe operations and become Master in cloud computing courses.
Get Certified
Earning cloud certifications from AWS, Azure, or Google Cloud can enhance your credibility. Certifications like AWS Certified Cloud Practitioner or Microsoft Certified: Azure Fundamentals can provide you a competitive edge.
Keep Learning
Cloud technology evolves rapidly, so continuous learning is key. Stay updated by taking advanced courses and attending cloud tech conferences.
Join Jetking today! Click Here
By building your expertise in these areas, you’ll be well on your way to a successful career as a Cloud Computing Engineer!
2 notes
·
View notes
Text
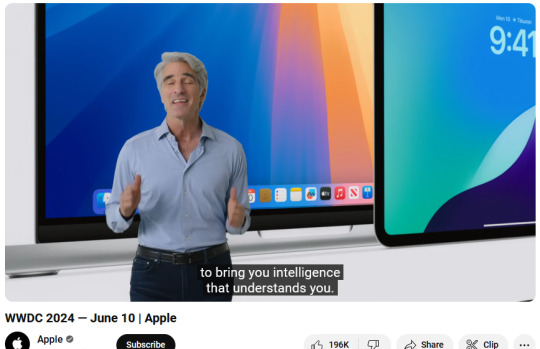


Apple WWDC 2024, screenshot of the segment on the "semantic index". The semantic index is just knowledge graph PR on their Siri development, setting the stage for AI cloud computing of personal data being their new feature, as well as a connection to ChatGPT. Worth noting that all the big players (Apple, Google, Microsoft) are doing the same thing simultaneously, introducting tighter surveillance ("on-screen awareness") directly on the operating system, in order to extract personal data for AI assistants ("intelligence that understands you"). Apple is now pushing ahead in this field exactly in one direction: using privacy scandals and the outrage against the AI economy to promise a closed wall system in their cloud. The fact that they need to build a bridge to the businesses they so theatrically distances themselves of (OpenAI/ChatGPT) shows how flimsy their own system is.
The WWDC presentation produced an image of this style of network culture. Its core selling point being a 'personal' index (how often do we hear the word "mum" in this segment...), and a personal cloud. This personal cloud then will process all your friends and family, as the presentation shows in a charming way, integrating algorithmic production in every step of personal communication (custom emojis, text rewriting, photo remixing). Everyone and everyone's communication and image is part of this "personal" computing.
"Contemporary production includes linguistic competence, knowledge, imagination, social interaction as its core sources of added value. So, the new modes of production and contemporary wealth are built not on labour power understood in classic Marxist terms, but on the appropriation of the entirety of human productive power. Terranova applies the concepts to today’s network cultures: “These are moments which turn qualitative, intensive differences into quantitative relations of exchange and equivalence; which enclose the open and dissipative potential of cultural production into differential hierarchies; which accumulate the rewards or work carried out by larger social assemblages… “ [Terranova 2006, 28]
The logic of capital subsumes the potential of many platforms, and encloses it within the chain of valorization of creativity and subjectivity."
Goriunova, Olga (2007) Towards a new critique of network cultures: creativity, autonomy and late capitalism in the constitution of cultural forms on the Internet, Network Cultures
3 notes
·
View notes
Text
Windows Server 2016: Revolutionizing Enterprise Computing
In the ever-evolving landscape of enterprise computing, Windows Server 2016 emerges as a beacon of innovation and efficiency, heralding a new era of productivity and scalability for businesses worldwide. Released by Microsoft in September 2016, Windows Server 2016 represents a significant leap forward in terms of security, performance, and versatility, empowering organizations to embrace the challenges of the digital age with confidence. In this in-depth exploration, we delve into the transformative capabilities of Windows Server 2016 and its profound impact on the fabric of enterprise IT.

Introduction to Windows Server 2016
Windows Server 2016 stands as the cornerstone of Microsoft's server operating systems, offering a comprehensive suite of features and functionalities tailored to meet the diverse needs of modern businesses. From enhanced security measures to advanced virtualization capabilities, Windows Server 2016 is designed to provide organizations with the tools they need to thrive in today's dynamic business environment.
Key Features of Windows Server 2016
Enhanced Security: Security is paramount in Windows Server 2016, with features such as Credential Guard, Device Guard, and Just Enough Administration (JEA) providing robust protection against cyber threats. Shielded Virtual Machines (VMs) further bolster security by encrypting VMs to prevent unauthorized access.
Software-Defined Storage: Windows Server 2016 introduces Storage Spaces Direct, a revolutionary software-defined storage solution that enables organizations to create highly available and scalable storage pools using commodity hardware. With Storage Spaces Direct, businesses can achieve greater flexibility and efficiency in managing their storage infrastructure.
Improved Hyper-V: Hyper-V in Windows Server 2016 undergoes significant enhancements, including support for nested virtualization, Shielded VMs, and rolling upgrades. These features enable organizations to optimize resource utilization, improve scalability, and enhance security in virtualized environments.
Nano Server: Nano Server represents a lightweight and minimalistic installation option in Windows Server 2016, designed for cloud-native and containerized workloads. With reduced footprint and overhead, Nano Server enables organizations to achieve greater agility and efficiency in deploying modern applications.
Container Support: Windows Server 2016 embraces the trend of containerization with native support for Docker and Windows containers. By enabling organizations to build, deploy, and manage containerized applications seamlessly, Windows Server 2016 empowers developers to innovate faster and IT operations teams to achieve greater flexibility and scalability.
Benefits of Windows Server 2016
Windows Server 2016 offers a myriad of benefits that position it as the platform of choice for modern enterprise computing:
Enhanced Security: With advanced security features like Credential Guard and Shielded VMs, Windows Server 2016 helps organizations protect their data and infrastructure from a wide range of cyber threats, ensuring peace of mind and regulatory compliance.
Improved Performance: Windows Server 2016 delivers enhanced performance and scalability, enabling organizations to handle the demands of modern workloads with ease and efficiency.
Flexibility and Agility: With support for Nano Server and containers, Windows Server 2016 provides organizations with unparalleled flexibility and agility in deploying and managing their IT infrastructure, facilitating rapid innovation and adaptation to changing business needs.
Cost Savings: By leveraging features such as Storage Spaces Direct and Hyper-V, organizations can achieve significant cost savings through improved resource utilization, reduced hardware requirements, and streamlined management.
Future-Proofing: Windows Server 2016 is designed to support emerging technologies and trends, ensuring that organizations can stay ahead of the curve and adapt to new challenges and opportunities in the digital landscape.
Conclusion: Embracing the Future with Windows Server 2016
In conclusion, Windows Server 2016 stands as a testament to Microsoft's commitment to innovation and excellence in enterprise computing. With its advanced security, enhanced performance, and unparalleled flexibility, Windows Server 2016 empowers organizations to unlock new levels of efficiency, productivity, and resilience. Whether deployed on-premises, in the cloud, or in hybrid environments, Windows Server 2016 serves as the foundation for digital transformation, enabling organizations to embrace the future with confidence and achieve their full potential in the ever-evolving world of enterprise IT.
Website: https://microsoftlicense.com
4 notes
·
View notes