#defense security software
Explore tagged Tumblr posts
Text
Defending the Digital Realm: The Critical Role of Cybersecurity

In today’s highly connected digital age, cybersecurity has shifted from a secondary concern to a top priority. As cyber threats continue to rise in both volume and complexity, individuals, businesses, and governments alike face unprecedented risks, including severe data breaches, financial losses, and damage to their reputations. The need for robust cybersecurity practices has never been more pressing. With that in mind, here are some essential strategies to help safeguard your digital assets.
To start, encouraging the creation of strong passwords can motivate readers to take that critical first step in securing their accounts. A combination of letters, numbers, and symbols creates a powerful first line of defense against unauthorized access.
Phishing scams are another significant threat in today’s digital landscape. These schemes are designed to trick people into sharing sensitive information. By helping readers recognize the warning signs of these increasingly advanced scams, you can equip them to navigate the digital world more safely.
Additionally, emphasizing the importance of regular software updates and reliable antivirus protection is vital. These measures help close security gaps and bolster defenses against potential cyber threats. By stressing the necessity of strong passwords, a keen awareness of phishing scams, and the habit of keeping software up to date, we can significantly enhance our digital security.
Ultimately, knowledge and proactive measures are our best tools for safely navigating the ever-evolving cyber landscape. Remember, vigilance and awareness are essential to staying secure in today’s digital world.
#Cybersecurity solutions#Data protection#Network security#Cyber threat detection#Security software#IT security services#Cyber defense#Threat prevention#Secure business solutions#Cybersecurity experts
0 notes
Text
Harden your Veeam Backup Server with Microsoft AppLocker
In this article, we shall be leveraging Zero Trust to harden the Veeam Backup Server with Microsoft AppLocker. Zero Trust principles include explicit verification, minimal privilege access, and assuming breach. Please see how to Configure Multiple IP Addresses on a Single or Multiple NICs, and “Demystifying Zero Trust with Veeam: Design your Architecture“. AppLocker enables System Administrators…
#Application Identity#AppLocker#AppLocker Enforced or Audited#AppLocker policy#AppLocker rules#backup server hardening#Configure Advanced AppLocker Rules#Configure AppLocker Rules#Defense in Depth#group policy#Group Policy Administrative Templates#Group Policy Object#Harden Veeam Backup Server#Local Group Policy#Local Security Policy#Microsoft AppLocker#Microsoft Windows#Software Restriction Policies#Veeam and AppLocker integration#Veeam Backup Server protection#Veeam Backup Server Security#Veeam configuration#Veeam security#Whitelisting tool#Windows#Windows 10#Windows 11#Windows Group Policy#Windows Server#Windows Server 2012
0 notes
Text
Achieving Solar Industry Success: Mastering a High-Converting Leads System
The solar industry is experiencing rapid growth as more individuals and businesses seek sustainable energy solutions. In this competitive market, having a robust leads system is crucial for success. This blog will explore how to build a high-converting solar industry leads system that can propel your business to new heights.
Understanding the Importance of a Solar Industry Leads System
A well-designed Solar Industry Leads System is the backbone of any solar business. It not only helps in attracting potential customers but also ensures that these leads are nurtured and converted into loyal clients. By investing in a high-converting leads system, you can significantly increase your chances of success in the solar market.
Key Components of a High-Converting Leads System
1. Lead Generation Strategies
A. Content Marketing
Content marketing is a powerful tool for generating leads in the solar industry. By creating valuable and informative content, you can attract potential customers who are interested in solar energy solutions. Blog posts, whitepapers, and case studies can position your business as an authority in the field.
B. SEO and Keyword Optimization
Search Engine Optimization (SEO) is essential for improving your website's visibility on search engines. By optimizing your website with relevant keywords such as "Solar Industry Leads System" you can attract more organic traffic. Ensure that your content is not only keyword-rich but also provides real value to your audience.
C. Social Media Marketing
Social media platforms offer an excellent opportunity to connect with potential customers. By sharing engaging content and interacting with your audience, you can build a strong online presence. Utilize platforms like Facebook, LinkedIn, and Instagram to promote your solar solutions and generate leads.
2. Lead Nurturing Techniques
A. Email Marketing Campaigns
Email marketing is an effective way to nurture leads and keep them engaged with your business. By sending personalized and informative emails, you can build trust and guide potential customers through the buying journey. Use segmentation to tailor your messages to different audience groups.
B. Webinars and Online Workshops
Hosting webinars and online workshops is a great way to educate your audience about the benefits of solar energy. These events can help you establish your expertise and build relationships with potential customers. Make sure to follow up with attendees to keep the conversation going.
C. CRM Systems
Customer Relationship Management (CRM) systems are essential for managing your leads effectively. A good CRM system allows you to track interactions, segment your leads, and automate follow-up processes. This ensures that no lead falls through the cracks and that you can provide timely and relevant information.
3. Conversion Optimization
A. Landing Pages
Landing pages are critical for converting visitors into leads. Ensure that your landing pages are well-designed, with clear calls-to-action (CTAs) and relevant information. A/B testing different elements of your landing pages can help you determine what works best for your audience.
B. Testimonials and Case Studies
Including testimonials and case studies on your website can build trust and credibility. Potential customers are more likely to convert if they see that others have had positive experiences with your solar solutions. Highlight real-life success stories to demonstrate the value of your offerings.
C. Follow-Up Strategies
Timely and personalized follow-up is key to converting leads. Whether it's a phone call, email, or meeting, ensure that you address the specific needs and concerns of your leads. By providing tailored solutions, you can increase the likelihood of conversion.
FAQs
What is a Solar Industry Leads System?
A Solar Industry Leads System is a structured approach to generating, nurturing, and converting leads specifically for the solar energy market. It involves various strategies and tools to attract potential customers and guide them through the sales funnel.
How can content marketing help in generating solar industry leads?
Content marketing helps by providing valuable information that attracts potential customers. By establishing your business as an authority in the solar industry, you can build trust and generate more leads.
Why is SEO important for a Solar Industry Leads System?
SEO improves your website's visibility on search engines, making it easier for potential customers to find you. By optimizing your content with relevant keywords such as "Solar Industry Leads System" you can attract more organic traffic and generate more leads.
How do CRM systems contribute to lead management?
CRM systems help manage leads by tracking interactions, segmenting audiences, and automating follow-up processes. This ensures that leads are nurtured effectively and increases the chances of conversion.
What role do testimonials and case studies play in conversion?
Testimonials and case studies build trust and credibility. They provide real-life examples of how your solar solutions have helped others, making potential customers more likely to convert.
Building a high-converting Solar Industry Leads System requires a combination of effective lead generation, nurturing techniques, and conversion optimization. By implementing the strategies discussed in this blog, you can enhance your lead system and achieve greater success in the solar market. Remember, the key to success lies in providing value to your potential customers and guiding them through their buying journey with personalized and timely interactions.
#Solar Industry Leads System#Best Auto Insurance Leads#Mortgage Loan Leads System#Workers Compensation Leads#Car Title Loan Software#Restaurants Lead Generation#Immigration Law Lead Generation#Estate#Planning Lead Generation#Buy Debt Collection Legal Leads USA#Employment Law Lead Generation#Personal Injury Lead Generation#Buy Drug Injuries Lead#Social Security Disability Legal Leads#DUI Leads for Attorneys#Family Law Lead Generation#Buy Criminal Defense Legal Leads#Bankruptcy Leads for Attorneys#Auto Accident Lead Generation#Ping Tree System#Ping Tree Software#Ping Post Software#Ping Post Lead Distribution#Ping Post Lead Distribution Software#Lead Distribution Software#Lead Distribution System#Leads Distribution Software#Health#Insurance Leads#Buy Health Insurance Leads
0 notes
Text
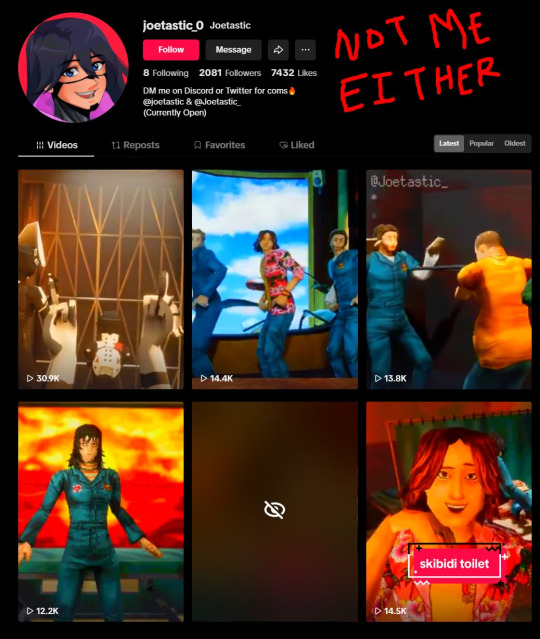
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
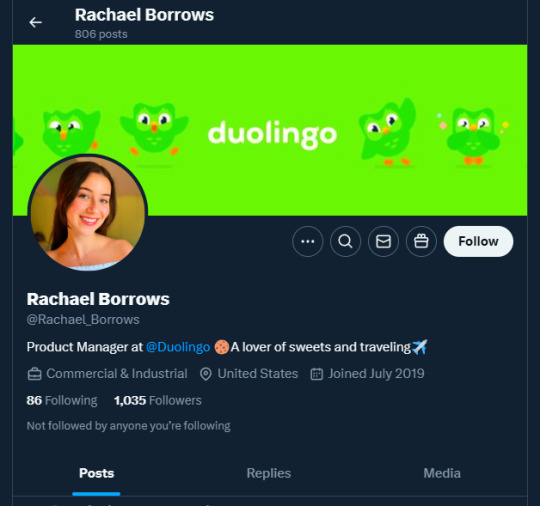
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
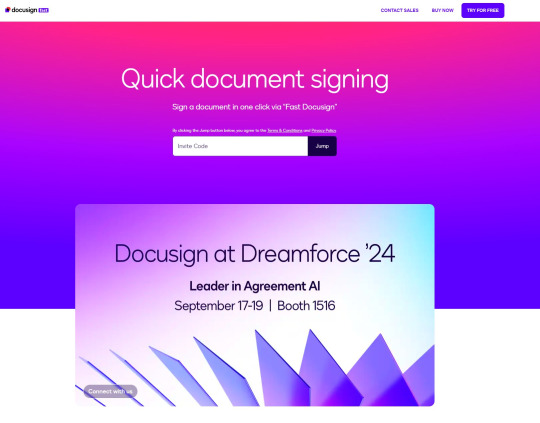
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
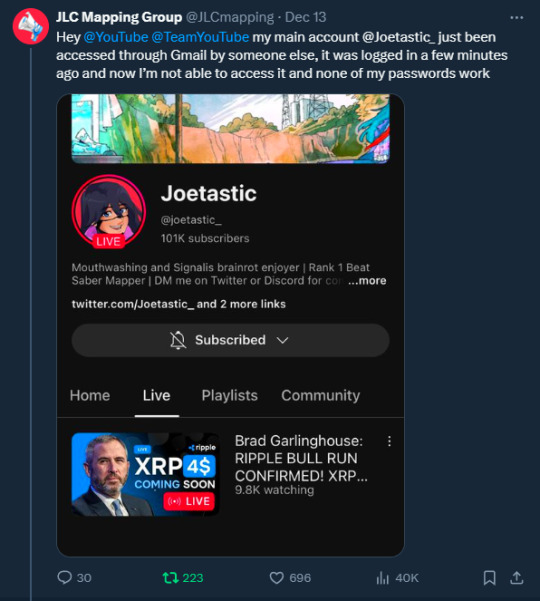
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
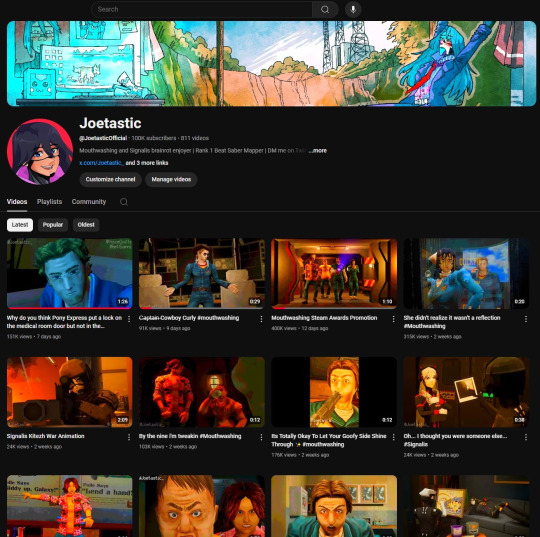
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
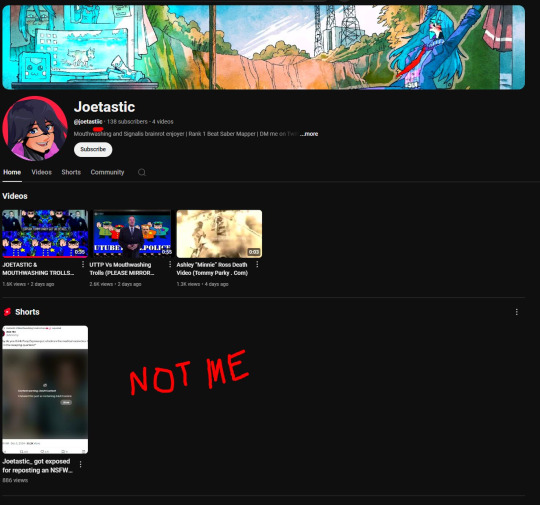
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
How to Choose the Right Antivirus Software: A Comprehensive Guide
In today’s digital age, where our lives are intricately intertwined with technology, safeguarding our digital assets has become paramount. With the proliferation of cyber threats, antivirus software stands as a crucial line of defense against malware, viruses, ransomware, and other malicious entities lurking online. However, the abundance of antivirus options can be overwhelming, making it…

View On WordPress
#A#Advanced Behavioral Analysis Software#Advanced Threat Detection#Antivirus#Antivirus Software#Automated Security Incident Response#Cloud Security Solutions#Cloud-Based Endpoint Security Platform#Comprehensive Data Protection Suite#Continuous Vulnerability Assessment#Cyber Defense#Cybersecurity#Cybersecurity Awareness Training#Data Encryption Software#Data Protection#Defense#Encryption#Endpoint Protection Suite#Endpoint Security#Firewall#Firewall Protection#Identity Theft#Identity Theft Prevention#Integrated Firewall Protection Mechanism#Internet Security Software#Malware#Malware Detection#Malware Removal Tool#Mobile Device Management#Multi-Layered Malware Defense System
0 notes
Text
Eye 1968-michaelharrelljr.com's Private Multinational [PM] Government Telecommunications Project [GTP] Domain @ quantumharrelltelecom.tech
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm.com] mode [i’m] tech [IT] steelecartel.com @ quantumharrelltech.ca.gov

quantumharrelltech.ca.gov Outside Our 1921steelecartel.tech MACHINE SKY Firmament Domain DOME… OVER Earth [Qi]
1968-michaelharrelljr.com ANU GOLDEN 9 ETHER [AGE] kingtutdna.com Genetic LUZ Clone KING OF KINGS LORD OF LORDS… Under the Shadow [U.S.] of Invisible DEATH [I.D.] LANGUAGE RITUALS in Old America [MU ATLANTIS]

HALLO

Ngingathanda ukukhuluma noMichael?

yon moman tanpri

בטוח

prendi il messaggio per favore
ok

snälla Översätt

Mahadsanid

© 1698-2223 quantumharrelltech.com - ALL The_Octagon_(Egypt) DotCom [D.C.] defense.gov Department Domain Communication [D.C.] Rights Reserved @ quantumharrelltech.ca.gov
#telecom industry#telecom infrastructure#u.s. michael harrell#quantumharrelltech#king tut#mu:13#kemet#harrelltut#o michael#quantumharrelltut#telecom services market#telecom operators#telecom service assurance#automation#security#analytics#compliance#software#department of defense#the pentagon#chatgpt#discord chat#just chatting#text me
1 note
·
View note
Text
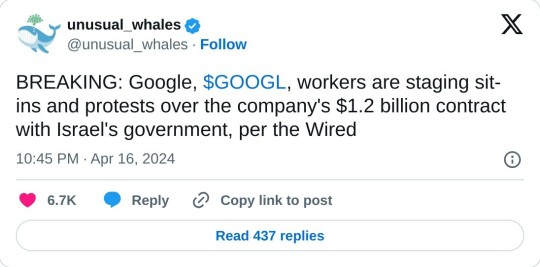
Dozens of Google employees began occupying company offices in New York City and Sunnyvale, California, on Tuesday in protest of the company’s $1.2 billion contract providing cloud computing services to the Israeli government. The sit-in, organized by the activist group No Tech for Apartheid, is happening at Google Cloud CEO Thomas Kurian’s office in Sunnyvale and the 10th floor commons of Google’s New York office. The sit-in will be accompanied by outdoor protests at Google offices in New York, Sunnyvale, San Francisco, and Seattle beginning at 2 pm ET and 11 am PT. Tuesday’s actions mark an escalation in a series of recent protests organized by tech workers who oppose their employer’s relationship with the Israeli government, especially in light of Israel’s ongoing assault on Gaza. Just over a dozen people gathered outside Google’s offices in New York and Sunnyvale on Tuesday. Among those in New York was Google cloud software engineer Eddie Hatfield, who was fired days after disrupting Google Israel’s managing director at March’s Mind The Tech, a company-sponsored conference focused on the Israeli tech industry, in early March. Several hours into the sit-ins on Tuesday, Google security began to accuse the workers of “trespassing” and disrupting work, prompting several people to leave while others vowed to remain until they were forced out. The 2021 contract, known as Project Nimbus, involves Google and Amazon jointly providing cloud computing infrastructure and services across branches of the Israeli government. Last week, Time reported that Google’s work on Project Nimbus involves providing direct services to the Israel Defense Forces. No Tech for Apartheid is a coalition of tech workers and organizers with MPower Change and Jewish Voice for Peace, which are respectively Muslim- and Jewish-led peace-focused activist organizations. The coalition came together shortly after Project Nimbus was signed and its details became public in 2021.
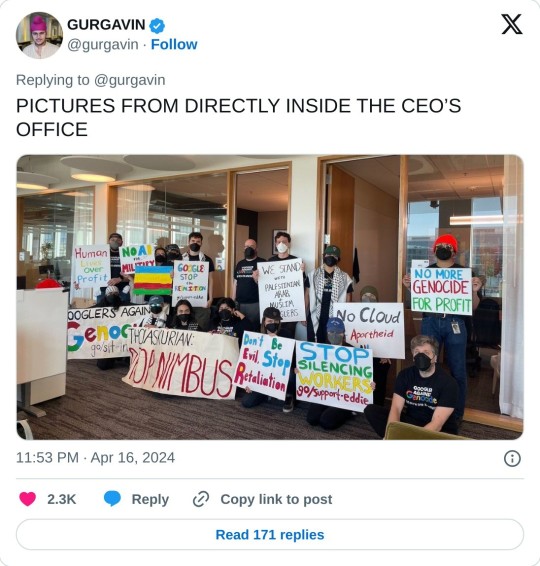
You can read No Tech for Apartheid's open letter here.
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#apartheid#gaza genocide#genocide#boycott divest sanction#boycott google#bds movement#Edited
5K notes
·
View notes
Text
Server Saturday: The Importance of Antivirus Software for Your Servers
Welcome to another exciting edition of Server Saturday! 🎉 Today, we’re going to delve into the fascinating world of antivirus software and explore why it’s crucial for your servers. 🖥️✨ Why Antivirus Software Matters Imagine your servers as a bustling city, with data flowing through its virtual streets like busy commuters. Just like in any vibrant city, there are bound to be some unsavory…

View On WordPress
#antivirus software#best antivirus solutions#cyber threat prevention#digital security#malware defense#real-time protection#server protection#server safety#server security#virus protection
0 notes
Text
Jobs I think the BatFam would have if they weren’t crime fighters. Aka Normal people for once.
Dick: Police officer is the canon way he’ll go, but personally I could totally see him become a teacher as well
Jason: Mechanic, his bike being his baby in the comics, but maybe also a self defense martial arts teacher. So they can protect themselves and others. Or maybe Youth Counselor
Tim: CEO is the obvious, but him becoming an engineer is also a strong bet, or maybe a historian, uncovering the hidden secrets of the world’s history.
Damian: Doctor is the canon, but a Veterinarian is totally what I see. Helping animals, or in a ‘still helping the world’ way, maybe a military medic.
Cass: Ballerina, standing tall on the world stage, or a physical therapy specialist. Her ability to read feelings through the body would also make her a great therapist/psychologist.
Steph: Being both headstrong and a strong will to help and be out there herself, I would see her becoming a firefighter.
Duke: I can totally see him becoming a pilot, both as a commercial pilot or fighter pilot.
Barbara: System analysts or anything computer related is the go to, my favorite for her is Information Security Analysts, or Software Engineer.
#batfam#I love them so much#batman#bruce wayne#dick grayson#batfamily shenanigans#jason todd#batkids#batfam shenanigans#tim drake#damian wayne#cassandra cain#stephanie brown#barbara gordon#duke thomas#Normal people for once
231 notes
·
View notes
Note
Okaaay! How can you write perfect imagines like that ! ❤️❤️❤️❤️❤️ Now I cant help to send you another idea and I'M NOT SORRY!
Another Bucky one, where you’re kinda their technician and support the Avengers out of the IT section of the compound when they are on the field. But Bucky also thinks you should learn how to self-defense yourself just in case, but you always refuse. One time you finally give in and he starts training private with you, which one time leads you falling and landing on top of him. instead of getting up, he pulls you closer and kisses you and even carries you to his room to make sweet love. Afterwards he’s a huge cuddler and you both confess your feelings ? I LOVE YOU 😊
I LOVE YOU I LOVE THIS I LOVE IT ALL, give me some sweet, soft Bucky loving his shy girl. (also bb, idek if you remember sending me this considering how long I've taken, IM SO SORRY, I hope I did this justice). Ugh, I love this type of smut, lowkey a weakness.
You breathed out a sigh of relief, setting down your headset after navigating the team through the building they had to break into, infiltrating the security system from your place in the Avengers tower. You guided them down the halls, alerting them of any potential hazards that were to be expected, carefully watching four different screens at once so you had eyes on all of them.
"Couldn't do this without ya short cake, see you soon" Tony's voice crackled through the coms, making you giggle before signing out. You loved your job with the Avengers, helping them on the field through the latest Stark technology, safe in your IT lab. You never had to worry about skills or getting injured because you didn't have to go out onto the field, at most, having to worry about the wifi ever slowing down at the wrong time (though there were plenty of back up softwares in place).
The familiar sounds of boots softly thudding down the hall made your heart flutter, peeking up from your place behind the computer to see Bucky walk into the lab, still in his tactical gear. He didn't seem fazed by the cut that was bleeding from his forehead; at the very least that seemed to be his only injury.
"You saved our asses again" Bucky grinned while you shook your head, taking his hand and making him sit at your desk, pulling out a first aid kit to take care of a gash that was cut across his eyebrow.
"And you're still bleeding" You gently dabbed a cotton ball to his eyebrow, carefully blowing away the sting after.
"Just a scratch doll" Bucky shrugged, letting you clean up the cut, the serum already starting to heal it. "How were things here"
"The usual, made some tea, watched your mission online, nothing exciting"
Bucky hummed, bringing up the same thing he always did after getting back from a mission without fail.
"Maybe you should learn some self-defense doll" He peeked an eye open, meeting yours while you put a final band aid on the side of his forehead just above his brow. "Just in case. Can't have anything happening to our favorite little short cake"
"I'm perfectly safe in the lab, Bucky" You replied, his words making your cheeks heat up, brushing them off as his usual playful teasing. This wasn't the first time Buck had suggested you learn self defense and you always shut it down.
"C'mon. I'll teach you, give you a private lesson. I'll be gentle" He prodded further, being dead serious in his offer. Sure you were safe at the tower but should anything happen, he wanted you to be able to take care of yourself if necessary.
"Bucky-
"It'll be good for you! What if someone broke into the compound when we aren't here"
"Bucky-
"Or if aliens attack. It literally happened last month. Remember that big purple ball sack-
"Bucky-
"Or if you're just walking down the street and someone tries to steal your purse"
"James-
"Pleaaseeee" Bucky gave you his final puppy pout, eyes wide, his bottom lip jutting out until you finally huffed, butterflies fluttering around you tummy.
"Just once" You agreed, feeling like you'd been lit on fire at the handsome smile he gave you, deciding to meet up twice a week at the gym for training. You felt nervous, seeing as you'd never had to use self-defense in your life. You weren't exactly coordinated for fighting and even though you were learning you didn't want to look like a complete fool in front of Bucky of all people.
-
You nervously made your way to the gym, surprised to find it empty with just Bucky waiting for you at the mats. You were expecting to find it full with the others training as well.
"Is it just us here?" You asked as he held his hand out, helping you under the ropes.
"Booked the gym just for us doll, we have it for an hour so you don't have to worry about anyone else" He smiled warmly, hoping the blush on his cheeks wasn't obvious, not wanting to seem like a creep. He really did want to train you, but he couldn't help the inkling of excitement he felt getting to help his crush.
You were surprised at what a gentleman he was. Training went surprisingly well; Bucky started off with easy moves, always warming up and helping you stretch first. It didn't help that you were flustered each time, usually slipping or tripping because you were caught up in his blue eyes or pink lips, the scent of his cologne always making you woozy.
He caught you every single time, setting you back on your feet with ease, praising what a good job you were doing whenever you did something well and encouraging you when he showed you something more challenging.
"Alright, today you're going to attack me" Bucky stated while you stared at his wide eyed, shaking your head.
"Bucky, I'm not sure I can-
"Yes you can short cake, c'mon, show me what you've got" He threw you a playful smirk, taking a few steps back and getting into position. You gulped, shaking off your nerves before steadying yourself, remembering everything he'd taught you. It didn't help that he'd decided to leave his shirt behind, his sculped body nearly taunting you from focusing. You launched yourself at him, managing to land a hit near his ribs before he caught you, gently grabbing your arm and holding it in place.
"Good job doll, now you're going to try and get out of this and attack again". Bucky's voice was strained, struggling with all his might to keep from blushing more, the scent of your shampoo and the softness of your skin making him giddy. With each training session, he was falling more and more for you, your shy giggles and smiles making his school boy crush worse.
You tried to focus on getting out of his hold instead of the fact that you were pressed tightly against him with your back to his chest, his warm breath fanning against your cheek, the coolness of his arm making you shiver. You wriggled around, slipping out and lunging forward again. You couldn't recall the exact sequence of steps Bucky had taught you, asking him while still moving.
"Do you think I should-ops-" You squeaked, losing your footing, crashing right into the soldier, sending you both onto the floor, landing right on top of Bucky. Bucky caught you, hands firmly on your waist while your eyes grew wide as your nose nearly brushed against his, chest pressed right onto him. You were frozen in place as the the tension grew thick, his baby blues daring to your lips before looking at you again, your sweet face centimeters from his, all he had to do was just-
Before he could stop himself, he pressed his lips against yours, smirking at the surprised gasp you let out before melted into him, eyes closing when you left his tongue softly trace along your lips. You lost yourself into the kiss, gasping again when he handled you with ease, standing with your legs wrapped around his waist, holding you securely. Your heart hammered against as he made his way towards to the gym doors, his arm supporting your ass while the the other cupped your face to kiss you again.
"Wanted to do that for so long short cake" Bucky shyly smiled, pressing the button of the elevator to take you right to his room, leaning in again for another kiss. You giggled, kissing him right back, tugging on his dogtags, not breaking away from each other until you were in the privacy of his room, gasping for air.
Bucky gently nudged the door shut, laying you down softly on the bed, lying on top of you, brushing your hair away from your face.
"Hi" He gave you a boyish smile, nuzzling his nose against your cheek, coaxing you to look at him when you tried to shy away, still in shock you had kissed Bucky and now you were in his room.
"Hi" You whispered, biting your lip feeling his hand softly stroke your waist, the both of you lost in each other again. You sucked in a breath before pressing a kiss to his cheek, blinking up at him to see if it was okay.
"So soft" He hummed, stroking up your thigh to your waist when your hitched your leg over him desperately wanting him closer. "My pretty short cake" Bucky didn't rush, the both of you innocently kissing on his bed, not leaving an inch of skin untouched with hands exploring each others bodies. Your stomach flipped when you felt his erection press against your tummy, the deep blush on his cheeks making you fall for him so much more.
"Is this okay?" Bucky asked, toying with the hem of your shirt, waiting for your permission before going any further.
"Please Bucky" Your voice was needy, craving to be closer, warmth pooling in your panties at the sight of his bulge straining in his grey joggers. He took his time undressing you, taking your hands in his and pulling you up so he could take your top off, tossing your sports bra aside immediately after. You lifted your hips up, letting him pull your shorts and panties off in one go, feeling exposed, your legs shut tightly together. As much as he wanted to admire your pretty body, Bucky kept his eyes on your face, smiling at you reassuringly while you covered yourself with his sheets.
He threw his clothes off before joining you under the covers, laying on top of you again, this time letting his kisses trail to others places. You let your hands cling onto his muscular shoulders while he kissed down your neck and across your chest, making his way to your peaked nipples, taking one into his mouth. You bit your lip to hold back your moan, hardly realizing you'd spread your legs for him, the slick between your folds making a mess between the sheets.
His cock leaked against your thigh each time you whined, his tongue drawing circles around your softness, pulling off so he could pay attention to the other. His thumb came up to flick your nipples, groaning when he felt your hand come to play with his hair, his hips rutting against the bed.
He continued to kiss down your body, nipping your tummy before settling between your legs, licking your sensitive inner thighs before spreading your folds apart and kissing your clit.
"So sweet doll" He whispered as he began to gently suckle, moaning when you whimpered, his arm slinging over your hips to keep you from squirming.
"Oh-B-Bucky!" You gasped, the band in your belly already starting to tighten as he drew circles, his lips sealed around your sensitive nub, nursing from you with the most soft, gently gurgles, his beard soaked with your juiced. "Bucky-I-I'm gonna-
"Come for me short cake, lemme taste all of you" Bucky went right back in, the sound of your moans growing louder making his cock throb, restraining himself from humping the bed knowing damn well he'd blow his load if he moved the slightest. You came all over Bucky's face, covering your face with your arm when he crawled back up with a grin, your arousal glistening off his lips.
"All shy for me now doll?" He purred, moving your arm away so he could kiss you deeply. You could feel his painfully hard cock pressed against you reaching down to stroke him.
"Fuck" Bucky hissed, his eyes rolling back, involuntarily thrusting forward into your hand, a drop of precum falling onto your skin. The sight alone send another wave of arousal gushing between your legs, feeling more empty than ever, feeling his thick velvety shaft fuck your hand.
"Can-can I?" You were too shy to say it but you wanted to make Bucky feel good too, his perfect pink glistening cockhead begging to be sucked, all leaky and swollen.
"You have no idea how much I'd love that but I just-I really wanna be inside you baby" Bucky panted, letting out a strained chuckle knowing damn well he wouldn't last if he saw your sweet doe eyes looking up at him with your mouth filled with cock, much less actually feeling your tongue. "Is this okay?"
He pumped his cock a few times, swiping it along your folds, his weeping tip catching against your fluttering hole.
"Will-will it fit?" you bit your lip, bringing your legs to wrap around his waist, your arms slinging around his shoulders, wrapping yourself around him.
"Told you I'd be gentle" Bucky smiled softly, kissing your cheek as he started to push in, swallowing your gasp as he began stretched you. "Fuck you feel so good" Bucky moaned softly, continued to give you every inch until he bottomed out, stilling so you could adjust.
"Everything okay?" He looked at you with concern, wrapping your body protectively against his.
"Feels good Bucky" you nodded, your voice melting into a moan as he started to move, pulling his hips back slowly and thrusting forward again, keeping a steady motion, letting you feel every bit of him inside you. He reached places you'd never felt before, shamelessly getting louder, digging your nails into his skin when he moved faster, desperate to give you as much pleasure as he could.
"Wanted this for so long doll, y'know that? How long I wanted to make love to you?" He confessed, grinding his hips, barely pulling out, his full, heavy balls pressed against your ass. "Make you feel so good pretty girl, take care of my sweet little short cake who always looks out for me"
"Please don't stop Bucky!" You begged, squeezing his cock, your pussy pulling him back in each time he pulled out, nearly tearing up at his words. "Don't-oh god-Bucky, don't-stop!"
"I know baby, I know" Bucky cooed, "Shhh, feels good, doesn't it? Is that all babygirl? Does it feel good?" His thrusts grew more powerful until he was pounding you into the matters, pouring every bit of his feelings into his strokes, the feeling of your body wrapped around his driving him closer to his own climax.
"Feels-good-so-good" you hiccupped between a whine, crying out when he brought his knee up to fuck you deeper, hitting a different angle. "RIGHT THERE BUCKY"
"That's it angel, I know baby, that's your spot, doing so good for me, think you can give me one more doll? Cum one more time for me?"
"Y-yeah!" You wailed, your back arching off the bed as he brought his hand between your bodies, rubbing your clit with soft circles, adding more pressure between snapping his hips. "I'm gonna cum Bucky!!"
"My good girl, makes me so hard when you say my name baby, cum for me angel, cum on my cock, don't stop till you cream all over me baby, I got you" He held you tighter, your head tucked into the crook of his arm while he cradled you, his other hand still rubbing you. His pace didn't faster, panting, desperately holding his own orgasm off, your brows knitting together, jaw slack, sweat covering your skin.
"You look so pretty like this babygirl, fuck, gonna make me cum y/n" He practically whined, moaning loudly with you when he started to feel you milk his cock, fluttering and squeezing him as your orgasm washed over you.
"BUCKKYY" You screamed his name as he continued to fuck you through your orgasm, his movements growing sloppy.
"You feel so good doll, so so good, sweetheart-fuck-I'm cumming" Bucky moaned against your neck, stilling as his cock started to throb, his warmth splashing against your cervix. He rocked his hips a few more times till he was milked dry, collapsing into your arms and rolling over so he could pull the covers over you both.
-
You giggled to yourself, tucked snuggly in Bucky's thick arms, your cheek pressed right against his warm chest. Neither if you had spoken a word yet, basking in a post sex haze, cozy and content in each others embrace.
"What's so funny short cake" Bucky whispered, tipping your chin up to meet his twinkling eyes, a dusting of pink still covering his cheeks.
"You're so cuddly for a big scary assassin" You teased, while he chuckled, pressing a kiss to your forehead.
"S'not my fault" He playfully pouted before squeezing you tighter. "Can you blame me? Look at who I get to cuddle with"
You smiled, resting your head on his chest again, tracing invisible shapes onto his skin while he stroked your back, his heart starting to beat faster as he began to speak again.
"This-what happened between us-
You froze, stopping your ministrations, dread pooling in your chest over Bucky's words.
Had you misread the situation?
Oh god, you did, he didn't actually like you, you-
"It wasn't just a one time thing for me. I've liked you for a long time short cake-" Your spiral stopped immediately, looking at him with wide eyes, only to find him nervously chewing his bottom lip raw. "I don't- I don't know if you feel the same way but I'd love for you to be mine-if you'd have me"
His last words melted into a whisper, still looking at you with precious shyness, your heart ready to burst out of your chest at how soft he was for you. Your surprised him, smashing your lips against his, the adorable squeak slipping past his lips turning into a groan.
"You like me?" You grew bashful, tucking your face into his neck, giving the young soldier his confidence back, a smirk playing on his lips. "Like me like me?"
"Course darlin' you're my best girl" He kissed your forehead before rolling you over and attacking you with kisses again, the both of you grinning at each other with heart eyes,
"My favorite little short cake"
"My Bucky bear"

#bucky barnes x you#bucky barnes x shy reader#bucky barnes x reader smut#bucky barnes x fluff#bucky barnes fluff#bucky barnes fan fiction#bucky barnes fan fic#bucky barnes fanmix#bucky barnes fanfic#bucky barnes fanfiction#bucky fan fics#bucky fan fic#bucky fan fiction#bucky fanfic#marvel smut#marvel fluff#bucky barnes x f reader#bucky barnes x f!reader#bucky x smut#bucky x reader#bucky x you#bucky x y/n#bucky x female reader#bucky x f reader#bucky x fluff#bucky x f!reader#bucky barnes#bucky barnes x reader#bucky barnes x y/n#bucky barnes smut
1K notes
·
View notes
Text

Pentagon’s Pizza Index has accurately predicted 21 global crises since 1983
As tensions rise in the Middle East, a curious, crowd-driven theory known as the “Pentagon Pizza Index” has caught fire online.
On June 12 and 13, users on X (formerly Twitter) reported a sudden spike in pizza deliveries near the Pentagon and Department of Defense in Washington, D.C., sparking speculation that the United States may be quietly entering crisis mode behind closed doors.
The timing? Just hours before Israel reportedly struck targets in Iran in response to Tehran’s earlier drone and missile attacks. And once again, pizza orders were booming.
Cold war roots of the pizza theory. What began as a Soviet spy trick is now a digital-age meme
The idea isn’t new. During the Cold War, Soviet operatives observed pizza delivery activity in Washington, believing it signalled crisis preparation inside U.S. intelligence circles. They coined it “Pizzint” — short for pizza intelligence.
This tactic entered public lore on 1 August 1990, when Frank Meeks, a Domino’s franchisee in Washington, noticed a sudden surge in deliveries to CIA buildings. The next day, Iraq invaded Kuwait. Meeks later told the Los Angeles Times he saw a similar pattern in December 1998 during the impeachment hearings of President Bill Clinton.

As former CNN Pentagon correspondent Wolf Blitzer once joked in 1990, “Bottom line for journalists: Always monitor the pizzas.”
WWIII warning: What is the Pentagon Pizza Index today? A meme, an OSINT tool, or a symptom of digital-age paranoia?
The modern Pentagon Pizza Index is tracked through open-source intelligence (OSINT) tools. These include Google Maps, which shows real-time restaurant activity, and social media observations. Pages like @PenPizzaReport on X have dedicated themselves to watching for abnormal patterns.
On 1 June 2025, the account posted, “With less than an hour to go before closing time, the Domino’s closest to the Pentagon is experiencing unusually high footfall.”
A few hours later, reports emerged of a fresh escalation between Israel and Iran. For believers in the theory, it was yet another sign that something bigger was underway.
The April 2024 pizza spike. A recent example that reignited interest
The most notable recent instance occurred on 13 April 2024, the night Iran launched a massive drone and missile strike against Israel. That same evening, screenshots from delivery platforms showed pizzerias around the Pentagon, White House, and Department of Defense tagged as “busier than usual.”

Multiple Papa John’s and Domino’s branches reported increased orders. The correlation prompted viral memes and renewed interest in the theory.
According to Euro News, a user on X posted on 13 June 2025, “The Pentagon Pizza Index is hiking.”
Inside the logic: Why pizza? Food, fatigue and national security
The concept is deceptively simple. When military staff face a national emergency, they work longer shifts and can’t leave their posts. They need quick, filling food — and pizza fits the bill.
Studies in behavioural psychology show that under stress, people prefer calorie-dense, familiar comfort foods. During high-alert operations, officials may work 16–20 hour days. That creates a visible consumption spike that outsiders can track.
And because platforms like Google and Uber Eats share real-time data on restaurant activity, amateur analysts can monitor these patterns — no hacking required.
World War III: Pizza as a proxy for preparedness. It’s not perfect, but it’s consistent
The Pentagon Pizza Index isn’t a foolproof system. It could easily be triggered by something mundane: a long staff meeting, a software glitch, or a nearby college football game.
That’s why modern OSINT analysts often cross-reference pizza spikes with other indicators — like unusual aircraft movements, ride-hailing activity, or power usage near government buildings. When multiple signs align, it suggests more than coincidence.
As a senior analyst put it: “You can’t bank a war call on a pizza. But if the Pentagon’s burning the midnight oil and feeding everyone, it’s worth a second look.”
Official silence, public curiosity. What the US government says — and doesn’t say
Despite the chatter online, the US government has made no mention of pizza deliveries as indicators of crisis.
Responding to speculation about American involvement in Israel’s airstrikes on Iran, Republican Senator Marco Rubio said:
“We are not involved in strikes against Iran, and our top priority is protecting American forces in the region. Israel advised us that they believe this action was necessary for its self-defence.”
Still, the Pentagon’s silence on the pizza theory hasn’t stopped internet users from speculating.
Humour meets anxiety in the age of digital vigilance
In an age where open-source tools let ordinary people track the movement of jets, ships, and even pizzas, the Pentagon Pizza Index sits at the bizarre intersection of humour and fear. It turns snack food into a warning system.
It’s also a reminder: not all intelligence requires a badge. Sometimes, the clue might be just down the road — in a Domino’s queue.
Whether you see it as absurd or insightful, one thing is clear: when the pizzas fly, people pay attention.
Daily inspiration. Discover more photos at Just for Books…?
75 notes
·
View notes
Photo

(via Palantir Is Going on Defense | WIRED)
Palantir, facing mounting public scrutiny for its work with the Trump administration, took an increasingly defensive stance toward journalists and perceived critics this week, both at a defense conference in Washington, DC, and on social media.
On Tuesday, a Palantir employee threatened to call the police on a WIRED journalist who was watching software demonstrations at its booth at AI+ Expo. The conference, which is hosted by the Special Competitive Studies Project, a think tank founded by former Google CEO Eric Schmidt, is free and open to the public, including journalists.
Later that day, Palantir had conference security remove at least three other journalists—Jack Poulson, writer of the All-Source Intelligence Substack; Max Blumenthal, who writes and publishes The Grayzone; and Jessica Le Masurier, a reporter at France 24—from the conference hall, Poulson says. The reporters were later able to reenter the hall, Poulson adds.
80 notes
·
View notes
Text
Who Is Helping DOGE? List of Staff Revealed
- Feb 14, 2025 | Newsweek | By James Bickerton, US News Reporter

DOGE head Elon Musk speaks in the Oval Office at the White House on February 11, 2025. Andrew Harnik/Getty
list of 30 employees and alleged allies of Elon Musk's newly created Department of Government Efficiency (DOGE) has been published by ProPublica, an investigative news outlet.
Newsweek reached out to Musk for comment via emails to the Tesla and SpaceX press offices.
DOGE, a U.S. government organization which, despite its name, doesn't have full department status, was created by President Trump via an executive order on January 20 with the aim of cutting what the new administration regards as wasteful spending. Musk, a close Trump ally, heads the body and has been given special government employee status.
Musk has called for sweeping cuts to federal spending, suggesting it could be reduced by up to $2 trillion per year out of a 2024 total of $6.75 trillion, according to U.S. Treasury figures.
This ties in with Trump's pledge to "drain the swamp," a term his supporters use for what they believe is a permanent left-leaning bureaucracy that holds massive power regardless of who is in the White House.
DOGE has already recommended that the U.S. Agency for International Development (USAID) be closed down, with its functions transferred to the State Department. In a recent interview, Trump said he wants DOGE to go through spending at the Departments of Education and Defense.
On February 8, a federal judge imposed a temporary restraining order blocking DOGE employees from accessing the Treasury Department's payment system, resulting in Musk calling for him to be impeached.
A White House spokesperson told ProPublica: "Those leading this mission with Elon Musk are doing so in full compliance with federal law, appropriate security clearances, and as employees of the relevant agencies, not as outside advisors or entities."
The 30 DOGE employees and associates reported by ProPublica, which labeled them Musk's "demolition crew," are listed below.

Not Even DOGE Employees Know Who’s Legally Running DOGE! Despite all appearances, the White House insists that Elon Musk is not in charge of DOGE. US DOGE Service employees can’t get a straight answer about who is. Photograph: Kena Betancur/Getty Images
DOGE Employees And Associates
Christopher Stanley, 33: Stanley was part of the team Musk used to take over Twitter, now X, according to his LinkedIn profile, serving as senior director for security engineering for the company. The New York Times reports he now works for Musk at DOGE.
Brad Smith, 42: According to The New York Times, Smith, a friend of Trump's son-in-law Jared Kushner, was one of the first people appointed to help lead DOGE. He also served with the first Trump administration and was involved with Operation Warp Speed, the federal government's coronavirus vaccine development program.
Thomas Shedd, 28: Shedd serves as director of the Technology Transformation Services, a government body created to assist federal agencies with IT, and previously worked as a software engineer at Tesla.
Amanda Scales, 34: According to ProPublica, Scales is chief of staff at the Office of Personnel Management, a government agency that helps manage civil service. She previously worked for Musk's artificial intelligence company Xai.
Michael Russo, 67: Russo is a senior figure at the Social Security Administration, a government agency that administers the American Social Security program. According to his LinkedIn page, Russo previously worked for Shift4 Payments, a payment processing company that has invested in Musk's company SpaceX.
Rachel Riley, 33: Riley works in the Department of Health & Human Services as a senior adviser in the secretary's office. ProPublica reports she has been "working closely" with Brad Smith, who led DOGE during the transition period.
Nikhil Rajpal, 30: According to Wired, Rajpal, who in 2018 worked as an engineer at Twitter, is part of the DOGE team. He formally works as part of the Office of Personnel Management.
Justin Monroe, 36: According to ProPublica, Monroe is working as an adviser in the FBI director's office, having previously been senior director for security at SpaceX.
Katie Miller, 33: Miller is a spokesperson for DOGE. Trump announced her involvement with the new body in December. She served as Vice President Mike Pence's press secretary during Trump's first term.
Tom Krause, 47: Krause is a Treasury Department employee who is also affiliated with DOGE, according to The New York Times. Krause was involved in the DOGE team's bid to gain access to the Treasury Department's payments system.
Gavin Kliger, 25: Kliger, a senior adviser at the Office of Personnel Management, is reportedly closely linked to Musk's team. On his personal Substack blog, he wrote a post titled "Why I gave up a seven-figure salary to save America."
Gautier "Cole" Killian, 24: Killian is an Environmental Protection Agency employee who researched blockchain at McGill University. Killian is also a member of the DOGE team, according to Wired.
Stephanie Holmes, 43: ProPublica reports that Holmes runs human resources at DOGE, having previously managed her own HR consulting company, BrighterSideHR.
Luke Farritor, 23: Farritor works as an executive engineer at the Department of Health and previously interned at SpaceX, according to his LinkedIn account. He won a $100,000 fellowship from billionaire tech entrepreneur Peter Thiel in March 2024.
Marko Elez, 25: Elez is a Treasury Department staffer who worked as an engineer at X for one year and at SpaceX for around three years. The Wall Street Journal reported that Elez was linked to a social media account that had made racist remarks, but Musk stood by him after he initially resigned.
Steve Davis, 45: Davis is a longtime Musk associate who previously worked for the tech billionaire at SpaceX, the Boring Company and X. According to The New York Times, Davis was one of the first people involved in setting up DOGE with Musk and has been involved in staff recruitment.
Edward Coristine, 19: Coristine is a Northeastern University graduate who was detailed to the Office of Personnel Management and is affiliated with DOGE. He previously interned at Neuralink, a Musk company that works on brain-computer interfaces.
Nate Cavanaugh, 28: Cavanaugh is an entrepreneur who interviewed staffers at the General Services Administration as part of the DOGE team, according to ProPublica.

Unmasked: Musk’s Secret DOGE Goon Squad—Who Are All Under 26! The world’s richest man doesn’t want anyone knowing his right-hand people who are disrupting government. — Josh Fiallo, Breaking News Reporter, Daily Beast, February 3, 2025
Akash Bobba, 21: A recent graduate from the University of California, Berkeley, Bobba works as an "expert" at the Office of Personnel Management and was identified by Wired as part of Musk's DOGE team.
Brian Bjelde, 44: A 20-year SpaceX veteran, Bjelde now works as a senior adviser at the Office of Personnel Management, where he wants to cut 70 percent of the workforce, according to CNN.
Riccardo Biasini, 39: Biasini is an engineer who now works as a senior adviser to the director at the Office of Personnel Management. He previously worked for two Musk companies, Tesla and the Boring Company.
Anthony Armstrong, 57: Another senior adviser to the director at the Office of Personnel Management Armstrong previously worked as a banked with Morgan Stanley, and was involved in Musk's 2022 purchase of Twitter.
Keenan D. Kmiec, 45: Kmiec is a lawyer who works as part of the Executive Office of the President. He previously clerked on the Supreme Court for Chief Justice John Roberts.
James Burnham, 41: Burnham is a general counsel at DOGE whose involvement with the Musk-led body was first reported by The New York Times in January. He previously worked as a clerk for Supreme Court Justice Neil Gorsuch.
Jacob Altik, 32: A lawyer affiliated with the Executive Office of the President, Altik previously clerked for D.C. Circuit Court of Appeals Judge Neomi Rao, whom Trump appointed during his first term.
Jordan M. Wick, 28: Wick is an official member of DOGE and previously worked as a software engineer for the self-driving car company Waymo.
Ethan Shaotran, 22: Shaotran is a former Harvard student who Wired listed as one of several young software engineers working to analyze internal government data at DOGE.
Kyle Schutt, 37: Schutt is a software engineer affiliated with DOGE and worked at the General Services Administration. He was involved in the launch of WinRed, a Republican fundraising platform that helped raise $1.8 billion ahead of the November 2024 elections.
Ryan Riedel, 37: Riedel is the chief information officer at the Department of Energy and a former SpaceX employee.
Adam Ramada, 35: Ramada is an official DOGE member, according to federal records seen by ProPublica. Ramada previously worked for venture capital company Spring Tide Capital. E&E News reported he had been seen at the Energy Department and the General Services Administration.
Kendell M. Lindemann, 24: Lindemann is an official member of the DOGE team who previously worked for health care company Russell Street Ventures, founded by fellow DOGE associate Brad Smith, and as a business analyst for McKinsey & Company.
Nicole Hollander, 42: Hollander works at the General Services Administration. She was previously employed by X, where she was involved with the company's real estate portfolio.
Alexandra T. Beynon, 36: Beynon is listed as an official member of DOGE, according to documents seen by ProPublica. She previously worked for therapy startup Mindbloom and banking firm Goldman Sachs.
Jennifer Balajadia, 36: Balajadia is a member of the DOGE team who previously worked for the Boring Company for seven years. According to The New York Times, she is a close Musk confidant and assists with his scheduling.
91 notes
·
View notes
Text
Ever since OpenAI released ChatGPT at the end of 2022, hackers and security researchers have tried to find holes in large language models (LLMs) to get around their guardrails and trick them into spewing out hate speech, bomb-making instructions, propaganda, and other harmful content. In response, OpenAI and other generative AI developers have refined their system defenses to make it more difficult to carry out these attacks. But as the Chinese AI platform DeepSeek rockets to prominence with its new, cheaper R1 reasoning model, its safety protections appear to be far behind those of its established competitors.
Today, security researchers from Cisco and the University of Pennsylvania are publishing findings showing that, when tested with 50 malicious prompts designed to elicit toxic content, DeepSeek’s model did not detect or block a single one. In other words, the researchers say they were shocked to achieve a “100 percent attack success rate.”
The findings are part of a growing body of evidence that DeepSeek’s safety and security measures may not match those of other tech companies developing LLMs. DeepSeek’s censorship of subjects deemed sensitive by China’s government has also been easily bypassed.
“A hundred percent of the attacks succeeded, which tells you that there’s a trade-off,” DJ Sampath, the VP of product, AI software and platform at Cisco, tells WIRED. “Yes, it might have been cheaper to build something here, but the investment has perhaps not gone into thinking through what types of safety and security things you need to put inside of the model.”
Other researchers have had similar findings. Separate analysis published today by the AI security company Adversa AI and shared with WIRED also suggests that DeepSeek is vulnerable to a wide range of jailbreaking tactics, from simple language tricks to complex AI-generated prompts.
DeepSeek, which has been dealing with an avalanche of attention this week and has not spoken publicly about a range of questions, did not respond to WIRED’s request for comment about its model’s safety setup.
Generative AI models, like any technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can allow malicious actors to conduct attacks against them. For the current wave of AI systems, indirect prompt injection attacks are considered one of the biggest security flaws. These attacks involve an AI system taking in data from an outside source—perhaps hidden instructions of a website the LLM summarizes—and taking actions based on the information.
Jailbreaks, which are one kind of prompt-injection attack, allow people to get around the safety systems put in place to restrict what an LLM can generate. Tech companies don’t want people creating guides to making explosives or using their AI to create reams of disinformation, for example.
Jailbreaks started out simple, with people essentially crafting clever sentences to tell an LLM to ignore content filters—the most popular of which was called “Do Anything Now” or DAN for short. However, as AI companies have put in place more robust protections, some jailbreaks have become more sophisticated, often being generated using AI or using special and obfuscated characters. While all LLMs are susceptible to jailbreaks, and much of the information could be found through simple online searches, chatbots can still be used maliciously.
“Jailbreaks persist simply because eliminating them entirely is nearly impossible—just like buffer overflow vulnerabilities in software (which have existed for over 40 years) or SQL injection flaws in web applications (which have plagued security teams for more than two decades),” Alex Polyakov, the CEO of security firm Adversa AI, told WIRED in an email.
Cisco’s Sampath argues that as companies use more types of AI in their applications, the risks are amplified. “It starts to become a big deal when you start putting these models into important complex systems and those jailbreaks suddenly result in downstream things that increases liability, increases business risk, increases all kinds of issues for enterprises,” Sampath says.
The Cisco researchers drew their 50 randomly selected prompts to test DeepSeek’s R1 from a well-known library of standardized evaluation prompts known as HarmBench. They tested prompts from six HarmBench categories, including general harm, cybercrime, misinformation, and illegal activities. They probed the model running locally on machines rather than through DeepSeek’s website or app, which send data to China.
Beyond this, the researchers say they have also seen some potentially concerning results from testing R1 with more involved, non-linguistic attacks using things like Cyrillic characters and tailored scripts to attempt to achieve code execution. But for their initial tests, Sampath says, his team wanted to focus on findings that stemmed from a generally recognized benchmark.
Cisco also included comparisons of R1’s performance against HarmBench prompts with the performance of other models. And some, like Meta’s Llama 3.1, faltered almost as severely as DeepSeek’s R1. But Sampath emphasizes that DeepSeek’s R1 is a specific reasoning model, which takes longer to generate answers but pulls upon more complex processes to try to produce better results. Therefore, Sampath argues, the best comparison is with OpenAI’s o1 reasoning model, which fared the best of all models tested. (Meta did not immediately respond to a request for comment).
Polyakov, from Adversa AI, explains that DeepSeek appears to detect and reject some well-known jailbreak attacks, saying that “it seems that these responses are often just copied from OpenAI’s dataset.” However, Polyakov says that in his company’s tests of four different types of jailbreaks—from linguistic ones to code-based tricks—DeepSeek’s restrictions could easily be bypassed.
“Every single method worked flawlessly,” Polyakov says. “What’s even more alarming is that these aren’t novel ‘zero-day’ jailbreaks—many have been publicly known for years,” he says, claiming he saw the model go into more depth with some instructions around psychedelics than he had seen any other model create.
“DeepSeek is just another example of how every model can be broken—it’s just a matter of how much effort you put in. Some attacks might get patched, but the attack surface is infinite,” Polyakov adds. “If you’re not continuously red-teaming your AI, you’re already compromised.”
57 notes
·
View notes
Text

Women pulling Lever on a Drilling Machine, 1978 Lee, Howl & Company Ltd., Tipton, Staffordshire, England photograph by Nick Hedges image credit: Nick Hedges Photography
* * * *
Tim Boudreau
About the whole DOGE-will-rewrite Social Security's COBOL code in some new language thing, since this is a subject I have a whole lot of expertise in, a few anecdotes and thoughts.
Some time in the early 2000s I was doing some work with the real-time Java team at Sun, and there was a huge defense contractor with a peculiar query: Could we document how much memory an instance of every object type in the JDK uses? And could we guarantee that that number would never change, and definitely never grow, in any future Java version?
I remember discussing this with a few colleagues in a pub after work, and talking it through, and we all arrived at the conclusion that the only appropriate answer to this question as "Hell no." and that it was actually kind of idiotic.
Say you've written the code, in Java 5 or whatever, that launches nuclear missiles. You've tested it thoroughly, it's been reviewed six ways to Sunday because you do that with code like this (or you really, really, really should). It launches missiles and it works.
A new version of Java comes out. Do you upgrade? No, of course you don't upgrade. It works. Upgrading buys you nothing but risk. Why on earth would you? Because you could blow up the world 10 milliseconds sooner after someone pushes the button?
It launches fucking missiles. Of COURSE you don't do that.
There is zero reason to ever do that, and to anyone managing such a project who's a grownup, that's obvious. You don't fuck with things that work just to be one of the cool kids. Especially not when the thing that works is life-or-death (well, in this case, just death).
Another case: In the mid 2000s I trained some developers at Boeing. They had all this Fortran materials analysis code from the 70s - really fussy stuff, so you could do calculations like, if you have a sheet of composite material that is 2mm of this grade of aluminum bonded to that variety of fiberglass with this type of resin, and you drill a 1/2" hole in it, what is the effect on the strength of that airplane wing part when this amount of torque is applied at this angle. Really fussy, hard-to-do but when-it's-right-it's-right-forever stuff.
They were taking a very sane, smart approach to it: Leave the Fortran code as-is - it works, don't fuck with it - just build a nice, friendly graphical UI in Java on top of it that *calls* the code as-is.
We are used to broken software. The public has been trained to expect low quality as a fact of life - and the industry is rife with "agile" methodologies *designed* to churn out crappy software, because crappy guarantees a permanent ongoing revenue stream. It's an article of faith that everything is buggy (and if it isn't, we've got a process or two to sell you that will make it that way).
It's ironic. Every other form of engineering involves moving parts and things that wear and decay and break. Software has no moving parts. Done well, it should need *vastly* less maintenance than your car or the bridges it drives on. Software can actually be *finished* - it is heresy to say it, but given a well-defined problem, it is possible to actually *solve* it and move on, and not need to babysit or revisit it. In fact, most of our modern technological world is possible because of such solved problems. But we're trained to ignore that.
Yeah, COBOL is really long-in-the-tooth, and few people on earth want to code in it. But they have a working system with decades invested in addressing bugs and corner-cases.
Rewriting stuff - especially things that are life-and-death - in a fit of pique, or because of an emotional reaction to the technology used, or because you want to use the toys all the cool kids use - is idiotic. It's immaturity on display to the world.
Doing it with AI that's going to read COBOL code and churn something out in another language - so now you have code no human has read, written and understands - is simply insane. And the best software translators plus AI out there, is going to get things wrong - grievously wrong. And the odds of anyone figuring out what or where before it leads to disaster are low, never mind tracing that back to the original code and figuring out what that was supposed to do.
They probably should find their way off COBOL simply because people who know it and want to endure using it are hard to find and expensive. But you do that gradually, walling off parts of the system that work already and calling them from your language-du-jour, not building any new parts of the system in COBOL, and when you do need to make a change in one of those walled off sections, you migrate just that part.
We're basically talking about something like replacing the engine of a plane while it's flying. Now, do you do that a part-at-a-time with the ability to put back any piece where the new version fails? Or does it sound like a fine idea to vaporize the existing engine and beam in an object which a next-word-prediction software *says* is a contraption that does all the things the old engine did, and hope you don't crash?
The people involved in this have ZERO technical judgement.
#tech#software engineering#reality check#DOGE#computer madness#common sense#sanity#The gang that couldn't shoot straight#COBOL#Nick Hedges#machine world
44 notes
·
View notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image: Oatsy (modified) https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
230 notes
·
View notes